Incident response in the Microsoft Defender portal
An incident in the Microsoft Defender portal is a collection of related alerts and associated data that make up the story of an attack. It's also a case file that your SOC can use to investigate that attack and manage, implement, and document the response to it.
The Microsoft Sentinel and Microsoft Defender services create alerts when they detect a suspicious or malicious event or activity. Individual alerts provide valuable evidence of a completed or ongoing attack. However, increasingly prevalent and sophisticated attacks typically employ a variety of techniques and vectors against different types of asset entities, such as devices, users, and mailboxes. The result is multiple alerts, from multiple sources, for multiple asset entities in your digital estate.
Because individual alerts each tell only part of the story, and because manually grouping individual alerts together to gain insight into an attack can be challenging and time-consuming, the unified security operations platform automatically identifies alerts that are related—from both Microsoft Sentinel and Microsoft Defender XDR—and aggregates them and their associated information into an incident.
Grouping related alerts into an incident gives you a comprehensive view of an attack. For example, you can see:
- Where the attack started.
- What tactics were used.
- How far the attack has gone into your digital estate.
- The scope of the attack, such as how many devices, users, and mailboxes were impacted.
- All of the data associated with the attack.
The unified security operations platform in the Microsoft Defender portal includes methods to automate and assist in the triage, investigation, and resolution of incidents.
Microsoft Copilot in Defender harnesses AI to support analysts with complex and time-consuming daily workflows, including end-to-end incident investigation and response with clearly described attack stories, step-by-step actionable remediation guidance and incident activity summarized reports, natural language KQL hunting, and expert code analysis—optimizing on SOC efficiency across Microsoft Sentinel and Defender XDR data.
This capability is in addition to the other AI-based functionality that Microsoft Sentinel brings to the unified platform, in the areas of user and entity behavior analytics, anomaly detection, multi-stage threat detection, and more.
Automated attack disruption uses high-confidence signals collected from Microsoft Defender XDR and Microsoft Sentinel to automatically disrupt active attacks at machine speed, containing the threat and limiting the impact.
If enabled, Microsoft Defender XDR can automatically investigate and resolve alerts from Microsoft 365 and Entra ID sources through automation and artificial intelligence. You can also perform additional remediation steps to resolve the attack.
Microsoft Sentinel automation rules can automate triage, assignment, and management of incidents, regardless of their source. They can apply tags to incidents based on their content, suppress noisy (false positive) incidents, and close resolved incidents that meet the appropriate criteria, specifying a reason and adding comments.
Important
Microsoft Sentinel is available as part of the public preview for the unified security operations platform in the Microsoft Defender portal. For more information, see Microsoft Sentinel in the Microsoft Defender portal.
Incidents and alerts in the Microsoft Defender portal
Tip
For a limited time during January 2024, when you visit the Incidents page, Defender Boxed appears. Defender Boxed highlights your organization's security successes, improvements, and response actions during 2023. To reopen Defender Boxed, in the Microsoft Defender portal, go to Incidents, and then select Your Defender Boxed.
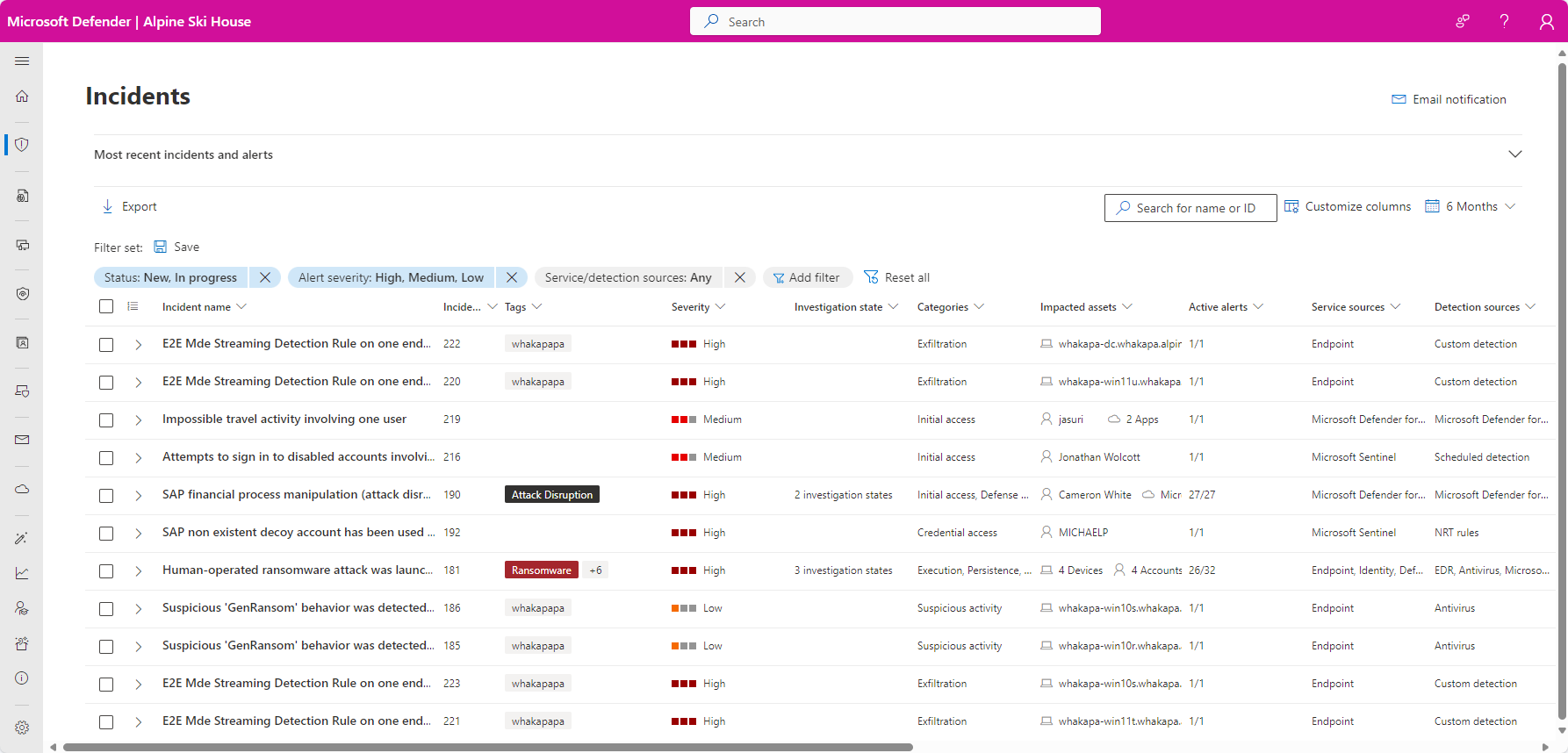
You manage incidents from Investigation & response > Incidents & alerts > Incidents on the quick launch of the Microsoft Defender portal. Here's an example:
Selecting an incident name displays the incident page, starting with the entire attack story of the incident, including:
Alert page within incident: The scope of alerts related to the incident and their information on the same tab.
Graph: A visual representation of the attack that connects the different suspicious entities that are part of the attack with the asset entities that make up the attack's targets, such as users, devices, apps, and mailboxes.
You can view the asset and other entity details directly from the graph and act on them with response options such as like disabling an account, deleting a file, or isolating a device.
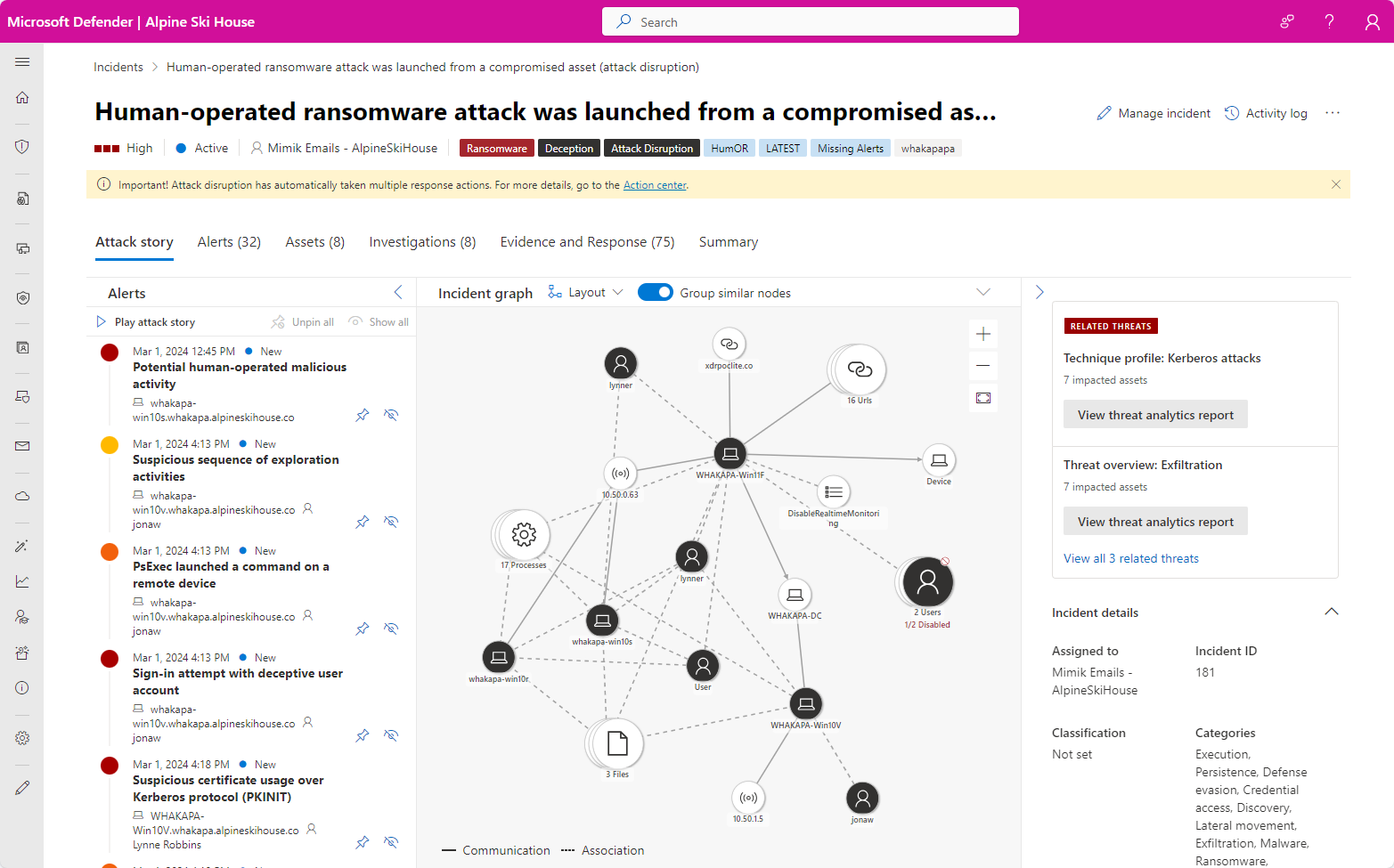
The incident page consists of the following tabs:
Attack story
Mentioned above, this tab includes the timeline of the attack, including all the alerts, asset entities, and remediation actions taken.
Alerts
All the alerts related to the incident, their sources, and information.
Assets
All the assets (protected entities such as devices, users, mailboxes, apps, and cloud resources) that have been identified to be part of or related to the incident.
Investigations
All the automated investigations triggered by alerts in the incident, including the status of the investigations and their results.
Evidence and Response
All the suspicious entities in the alerts of the incident, which constitute evidence supporting the attack story. These entities can include IP addresses, files, processes, URLs, registry keys and values, and more.
Summary
A quick overview of the impacted assets associated with alerts.
Note
If you see an Unsupported alert type alert status, it means that automated investigation capabilities cannot pick up that alert to run an automated investigation. However, you can investigate these alerts manually.
Incident response workflow example in the Microsoft Defender portal
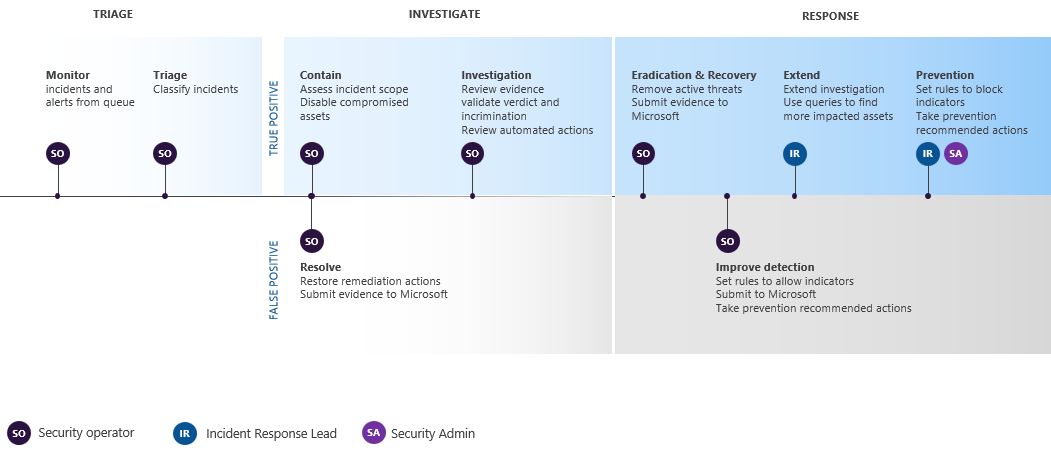
Here's a workflow example for responding to incidents in Microsoft 365 with the Microsoft Defender portal.
On an ongoing basis, identify the highest priority incidents for analysis and resolution in the incident queue and get them ready for response. This is a combination of:
- Triaging to determining the highest priority incidents through filtering and sorting of the incident queue.
- Managing incidents by modifying their title, assigning them to an analyst, and adding tags and comments.
You can use Microsoft Sentinel automation rules to automatically triage and manage (and even respond to) some incidents as they're created, removing the easiest-to-handle incidents from taking up space in your queue.
Consider these steps for your own incident response workflow:
| Stage | Steps |
|---|---|
| For each incident, begin an attack and alert investigation and analysis. |
|
| After or during your analysis, perform containment to reduce any additional impact of the attack and eradication of the security threat. | For example, |
| As much as possible, recover from the attack by restoring your tenant resources to the state they were in before the incident. | |
| Resolve the incident and document your findings. | Take time for post-incident learning to: |
If you're new to security analysis, see the introduction to responding to your first incident for additional information and to step through an example incident.
For more information about incident response across Microsoft products, see this article.
Integrating security operations in the Microsoft Defender portal
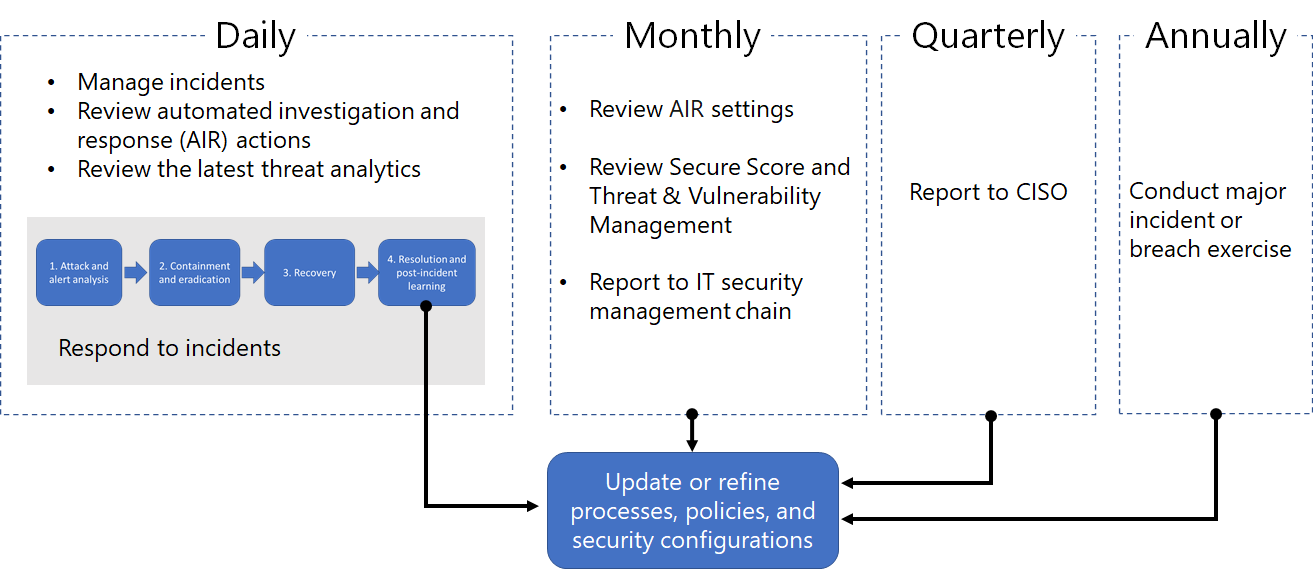
Here's an example of integrating security operations (SecOps) processes in the Microsoft Defender portal.
Daily tasks can include:
- Managing incidents
- Reviewing automated investigation and response (AIR) actions in the Action center
- Reviewing the latest Threat Analytics
- Responding to incidents
Monthly tasks can include:
- Reviewing AIR settings
- Reviewing Secure Score and Microsoft Defender Vulnerability Management
- Reporting to your IT security management chain
Quarterly tasks can include a report and briefing of security results to the Chief Information Security Officer (CISO).
Annual tasks can include conducting a major incident or breach exercise to test your staff, systems, and processes.
Daily, monthly, quarterly, and annual tasks can be used to update or refine processes, policies, and security configurations.
See Integrating Microsoft Defender XDR into your security operations for more details.
SecOps resources across Microsoft products
For more information about SecOps across Microsoft's products, see these resources:
Incident notifications by email
You can set up the Microsoft Defender portal to notify your staff with an email about new incidents or updates to existing incidents. You can choose to get notifications based on:
- Alert severity
- Alert sources
- Device group
To set up email notifications for incidents, see get email notifications on incidents.
Training for security analysts
Use this learning module from Microsoft Learn to understand how to use Microsoft Defender XDR to manage incidents and alerts.
| Training: | Investigate incidents with Microsoft Defender XDR |
|---|---|
 |
Microsoft Defender XDR unifies threat data from multiple services and uses AI to combine them into incidents and alerts. Learn how to minimize the time between an incident and its management for subsequent response and resolution. 27 min - 6 Units |
Next steps
Use the listed steps based on your experience level or role on your security team.
Experience level
Follow this table for your level of experience with security analysis and incident response.
| Level | Steps |
|---|---|
| New |
|
| Experienced |
|
Security team role
Follow this table based on your security team role.
| Role | Steps |
|---|---|
| Incident responder (Tier 1) | Get started with the incident queue from the Incidents page of the Microsoft Defender portal. From here you can:
|
| Security investigator or analyst (Tier 2) |
|
| Advanced security analyst or threat hunter (Tier 3) |
|
| SOC manager | See how to integrate Microsoft Defender XDR into your Security Operations Center (SOC). |
Tip
Do you want to learn more? Engage with the Microsoft Security community in our Tech Community: Microsoft Defender XDR Tech Community.
意見反應
即將登場:在 2024 年,我們將逐步淘汰 GitHub 問題作為內容的意見反應機制,並將它取代為新的意見反應系統。 如需詳細資訊,請參閱:https://aka.ms/ContentUserFeedback。
提交並檢視相關的意見反應