步驟 2: 可遠端存取內部部署應用程式和服務
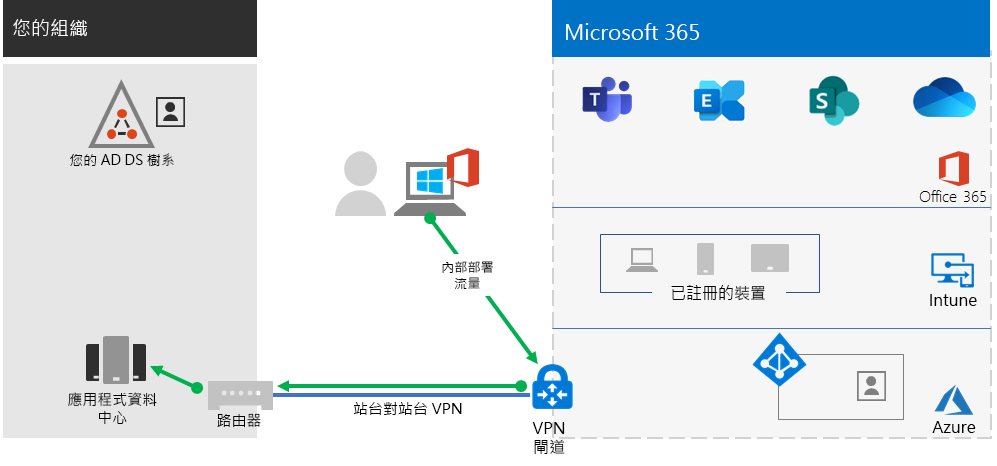
如果貴組織使用遠端存取 VPN 解決方案 (通常 VPN 伺服器安裝在網路的邊緣,而 VPN 用戶端則安裝在使用者的裝置上),您的使用者就可以使用遠端存取 VPN 連線存取內部部署應用程式和伺服器。 但您可能需要將 Microsoft 365 雲端服務的流量最佳化。
如果您的使用者未使用 VPN 解決方案,您可以使用 Microsoft Entra 應用程式 Proxy 和 Azure 點對站 (P2S) VPN 來提供存取權,視您的所有應用程式是否為 Web 為基礎而定。
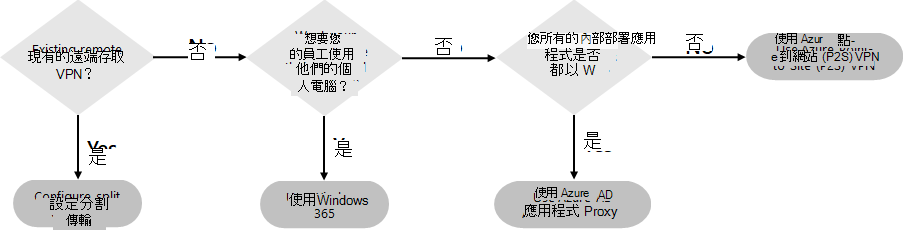
以下是用於遠端存取的主要設定:
- 您已經在使用遠端存取 VPN 解決方案。
- 您未使用遠端存取 VPN 解決方案,且希望您的遠端工作者使用其個人電腦。
- 您沒有使用遠端存取 VPN 解決方案、您有混合式身分識別,而且您只需要遠端存取內部部署的 Web 架構應用程式。
- 您沒有使用遠端存取 VPN 解決方案、您需要存取內部部署應用程式,而且其中部分應用程式並非 Web 架構。
請參閱此流程圖,了解本文所述的遠端存取設定選項。
使用遠端存取連線時,您也可以使用遠端桌面,將您的使用者連線到內部部署電腦。 例如,遠端工作者可以從其 Windows、iOS 或 Android 裝置,使用遠端桌面連線到其辦公室中的電腦。 從遠端連線之後,他們就可以像坐在電腦前面一樣使用電腦。
針對 Microsoft 365 雲端服務,將遠端存取 VPN 用戶端的效能最佳化
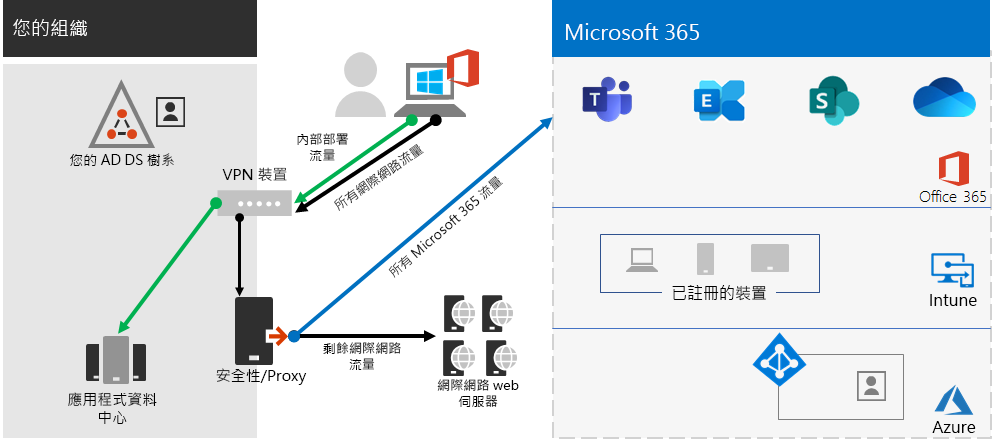
如果您的遠端工作者使用傳統的 VPN 用戶端取得貴組織網路的遠端存取權,請確認 VPN 用戶端支援分割通道。
如果沒有分割通道,您所有的遠端工作流量都會透過 VPN 連線傳送,其中必須先將流量轉送給貴組織的邊緣裝置、進行處理,然後透過網際網路傳送。
Microsoft 365 流量必須透過貴組織進行間接路由,這可能是從距離 VPN 用戶端實體位置很遠的位置轉送到 Microsoft 網路進入點。 這種間接路徑可增加網路流量的延遲,並降低整體效能。
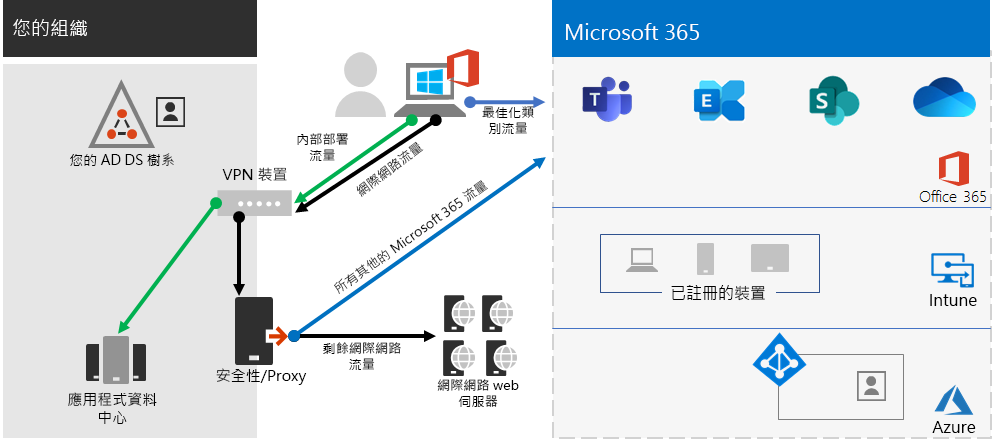
您可以利用分割通道設定 VPN 用戶端,以排除透過 VPN 連線傳送到組織網路的特定類型流量。
若要將 Microsoft 365 雲端資源的存取最佳化,請設定分割通道 VPN 用戶端,排除透過 VPN 連線到最佳化類別 Microsoft 365 端點的流量。 如需詳細資訊,請參閱 Office 365 端點類別 (部分機器翻譯)。 請參閱本清單,以了解最佳化類別端點。
以下是產生的流量,其中連至 Microsoft 365 雲端應用程式的大部分流量會略過 VPN 連線。
如此可讓 VPN 用戶端直接透過網際網路傳送和接收重要的 Microsoft 365 雲端服務流量,並透過最接近的進入點到 Microsoft 網路。
如需詳細資訊和指導方針,請參閱使用 VPN 分割通道將遠端使用者的 Office 365 連線能力最佳化。
當您的所有應用程式都為 Web 應用程式且您擁有混合式身分識別時,部署遠端存取
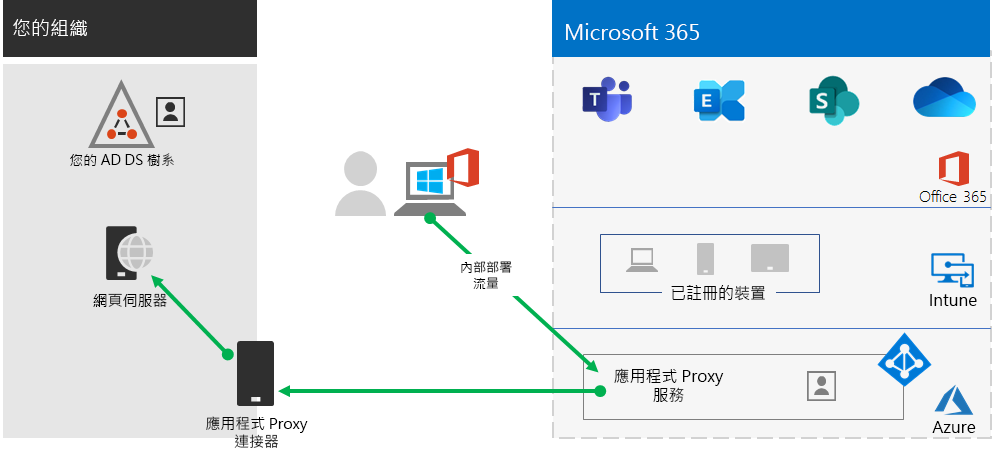
如果您的遠端工作者未使用傳統的 VPN 用戶端,且內部部署使用者帳戶和群組已與 Microsoft Entra 標識符同步,您可以使用 Microsoft Entra 應用程式 Proxy,為裝載於內部部署伺服器上的 Web 應用程式提供安全的遠端訪問。 Web 架構應用程式包括 SharePoint 伺服器網站、Outlook Web Access 伺服器或其他任何 Web 架構企業營運應用程式。
以下是 Microsoft Entra 應用程式 Proxy 的元件。
如需詳細資訊,請參閱此 Microsoft Entra 應用程式 Proxy 概觀。
注意事項
Microsoft Entra 應用程式 Proxy 不包含在 Microsoft 365 訂閱中。 您必須購買單獨的 Azure 訂閱才能使用。
並非所有應用程式都是 Web 應用程式時,部署遠端存取
如果您的遠端工作者並未使用傳統的 VPN 用戶端,且您有非 Web 架構的應用程式,則可以使用 Azure 點對站台 (P2S) VPN。
P2S VPN 連線會透過 Azure 虛擬網路,建立遠端工作者裝置到貴組織網路的安全連線。
如需詳細資訊,請參閱這個 P2S VPN 概觀 (部分機器翻譯)。
注意事項
Azure P2S VPN 不包含在 Microsoft 365 訂閱中。 您必須購買單獨的 Azure 訂閱才能使用。
部署 Windows 365 以提供使用個人裝置的遠端工作者遠端存取
若要支援僅可使用其個人和非受控裝置的遠端工作者,請使用 Windows 365,為您的使用者建立和配置虛擬桌面以供在家使用。 使用內部部署網路連線 (OPNC),Windows 365 雲端電腦可以像是連接至您的組織網路電腦那樣運作。
如需詳細資訊,請參閱Windows 365 概觀。
注意事項
Windows 365 並未包括在 Microsoft 365 訂閱中。 您必須使用單獨的訂閱來支付使用款項。
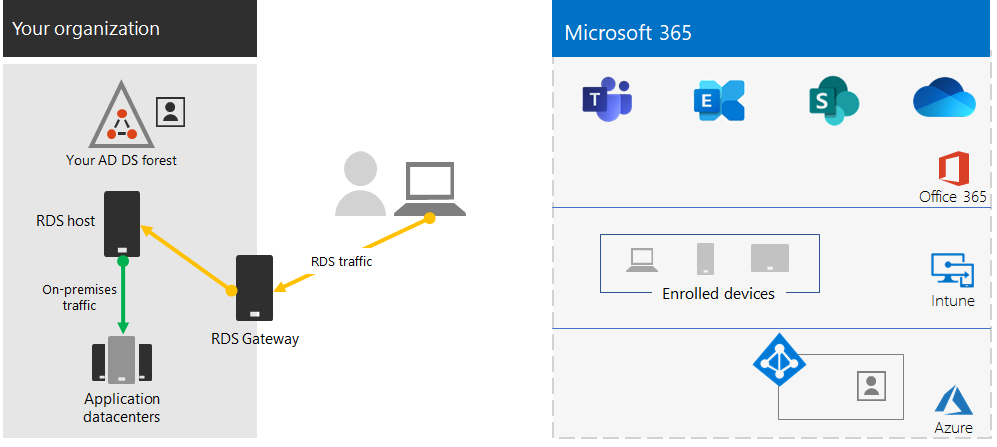
使用遠端桌面服務閘道保護您的遠端桌面服務連線
如果您使用遠端桌面服務 (RDS) 來允許員工連線到內部部署網路上的 Windows 電腦,您應在邊緣網路中使用 Microsoft 遠端桌面服務閘道。 閘道會使用傳輸層安全性 (TLS) 來加密流量,並防止直接將主控 RDS 的內部部署電腦暴露到網際網路上。
如需詳細資訊,請參閱這篇文章。
適用於遠端存取的系統管理技術資源
步驟 2 的結果
為您的遠端工作者部署遠端存取解決方案之後:
| 遠端存取設定 | 結果 |
|---|---|
| 遠端存取 VPN 解決方案已就緒 | 您已經針對分割通道以及 Microsoft 365 端點的最佳化類別,設定您的遠端存取 VPN 用戶端。 |
| 沒有遠端存取 VPN 解決方案,而且您只需要遠端存取內部部署的 Web 架構應用程式 | 您已經設定 Azure 應用程式 Proxy。 |
| 沒有遠端存取 VPN 解決方案、您需要存取內部部署應用程式,而且其中部分應用程式並非 Web 架構 | 您已經設定 Azure P2S VPN。 |
| 遠端工作者正在家中使用其個人裝置 | 您已設定 Windows 365。 |
| 遠端工作者正在使用 RDS 連線到內部部署系統 | 您已在邊緣網路中部署遠端桌面服務閘道。 |
下一步
繼續進行步驟 3 部署 Microsoft 365 安全性與合規性服務,以保護您的應用程式、資料和裝置。
意見反應
即將登場:在 2024 年,我們將逐步淘汰 GitHub 問題作為內容的意見反應機制,並將它取代為新的意見反應系統。 如需詳細資訊,請參閱:https://aka.ms/ContentUserFeedback。
提交並檢視相關的意見反應