具有安全記憶體保護區的 Always Encrypted
適用於:SQL Server 2019 (15.x) 和更新版本 - 僅限 Windows
Azure SQL Database
具有安全記憶體保護區的 Always Encrypted 透過啟用就地加密和更豐富的機密查詢,來擴充 Always Encrypted 的機密運算功能。 SQL Server 2019 (15.x) 和更新版本以及 Azure SQL Database 均提供具有安全記憶體保護區的 Always Encrypted。
Always Encrypted 是在 Azure SQL Database 2015 和 SQL Server 2016 (13.x) 中引進,旨在保護敏感性資料的機密性免受惡意程式碼和高權限的「未經授權」使用者威脅,這些使用者包括資料庫管理員 (DBA)、電腦系統管理員、雲端系統管理員,或是對伺服器執行個體、硬體等具有合法存取權,但不應該存取部分或所有實際資料的其他人。
若沒有本文所述的增強功能,Always Encrypted 保護資料的方式是透過在用戶端將資料加密,且「絕不」允許資料或對應的密碼編譯金鑰以純文字形式出現在資料庫引擎內部。 因此,資料庫內部的加密資料行功能受到嚴格限制。 資料庫引擎唯一能對加密資料執行的作業是相等比較 (僅適用於確定性加密)。 資料庫內部不支援所有其他作業,包括密碼編譯作業 (初始資料加密或金鑰輪替) 及更豐富的查詢 (例如模式比對)。 使用者需要將資料移出資料庫以在用戶端執行這些作業。
「具有安全記憶體保護區」的 Always Encrypted 允許在伺服器端對安全記憶體保護區內的純文字資料進行一些計算,藉以因應這些限制。 安全記憶體保護區是資料庫引擎處理序內受保護的記憶體區域。 安全記憶體保護區對於資料庫引擎的其餘部分,以及主控電腦上的其他處理序,會顯示為不透明方塊。 即使使用偵錯工具,也無法從外部檢視記憶體保護區內部的任何資料或程式碼。 這些屬性會讓安全記憶體保護區成為「信任的執行環境」,可安全存取純文字的密碼編譯金鑰和機密資料,卻不會破壞資料機密性。
Always Encrypted 會使用安全記憶體保護區,如下圖所示:
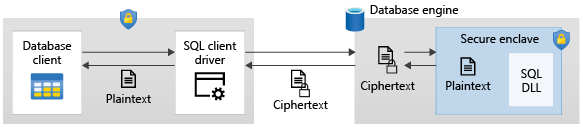
剖析應用程式提交的 Transact-SQL 陳述式時,資料庫引擎會判斷陳述式是否包含任何需要使用安全記憶體保護區的加密資料作業。 針對這類陳述式:
用戶端驅動程式會將作業所需的資料行加密金鑰 (透過安全通道) 傳送至安全記憶體保護區,並提交陳述式以供執行。
處理陳述式時,資料庫引擎會將密碼編譯作業或加密資料行計算委派給安全記憶體保護區。 如有需要,記憶體保護區會解密資料,並對純文字執行計算。
在陳述式處理期間,資料和資料行加密金鑰都不會以純文字形式公開在安全記憶體保護區外的資料庫引擎中。
支援的用戶端驅動程式
若要使用具有安全記憶體保護區的 Always Encrypted,應用程式必須使用支援此功能的用戶端驅動程式。 設定應用程式和用戶端驅動程式,以啟用記憶體保護區計算和記憶體保護區證明 (請參閱下面的安全記憶體保護區證明一節)。 如需詳細資料 (包括支援的用戶端驅動程式清單),請參閱使用 Always Encrypted 開發應用程式。
支援的記憶體保護區技術
Always Encrypted 支援下列記憶體保護區技術 (或記憶體保護區類型):
- 虛擬化型安全性 (VBS) 記憶體保護區 (也稱為虛擬安全模式或 VSM 記憶體保護區) - 依賴 Windows Hypervisor 且不需要任何特殊硬體的軟體型技術。
- Intel Software Guard Extensions (Intel SGX) 記憶體保護區 - 值得信任的硬體型執行環境技術。
資料庫可用的記憶體保護區類型取決於裝載它的 SQL 產品 (Azure SQL Database 或 SQL Server),在 Azure SQL Database 的情況下,還取決於您的資料庫組態。
在 SQL Server 2019 (15.x) 和更新版本中,Always Encrypted 支援 VBS 記憶體保護區 (不支援 Intel SGX 記憶體保護區)。
在 Azure SQL Database 中,資料庫可以使用 Intel SGX 記憶體保護區或 VBS 記憶體保護區,視設定執行資料庫的硬體而定:
- 使用 DC 系列硬體組態 (適用於虛擬核心購買模型) 的資料庫會使用 Intel SGX 記憶體保護區。
- 使用虛擬核心購買模型 DC 系列以外組態的資料庫,以及使用 DTU 購買模型的資料庫,可以設定為使用 VBS 記憶體保護區。
注意
VBS 記憶體保護區目前適用於所有 Azure SQL 資料庫區域,但 Jio 印度中部除外。
如需每個記憶體保護區類型所提供保護層級的重要資訊,請參閱安全性考量一節。
安全記憶體保護區證明
記憶體保護區證明是一項深度防禦機制,可協助偵測涉及惡意系統管理員竄改記憶體保護區程式碼或其環境的攻擊。
記憶體保護區證明可讓用戶端應用程式先與應用程式所連線資料庫的安全記憶體保護區建立信任,再讓應用程式使用該記憶體保護區來處理敏感性資料。 證明工作流程會驗證記憶體保護區是正版 VBS 或 Intel SGX 記憶體保護區,且其內部執行的程式碼是經由 Microsoft 簽署適用於 Always Encrypted 的正版記憶體保護區程式庫。 在證明期間,應用程式和資料庫引擎內的用戶端驅動程式都會使用用戶端指定的端點來與外部證明服務通訊。
Always Encrypted 可以使用下列兩項證明服務的其中一項:
- Microsoft Azure 證明 - 雲端式證明解決方案。
- 實作 Windows Defender 系統防護執行階段證明的主機守護者服務 (HGS)。
若要為應用程式啟用具有安全記憶體保護區的 Always Encrypted,您必須在應用程式的用戶端驅動程式組態中設定證明通訊協定。 證明通訊協定值會 1) 判斷用戶端應用程式是否會使用證明,如果是的話,則會 2) 指定要使用的證明服務類型。 下表擷取有效 SQL 產品和記憶體保護區類型組合支援的證明通訊協定:
| 裝載的產品 | 記憶體保護區類型 | 支援的證明通訊協定 |
|---|---|---|
| SQL Server 2019 (15.x) 和更新版本 | VBS 記憶體保護區 | HGS、無證明 |
| Azure SQL Database | SGX 記憶體保護區 (DC 系列資料庫) | Microsoft Azure 證明 |
| Azure SQL Database | VBS 記憶體保護區 | 無證明 |
請注意下列幾個重點:
- 在 SQL Server 2019 (15.x) 和更新版本中證明 VBS 記憶體保護區需要 HGS。 您也可以在沒有證明的情況下使用 VBS 記憶體保護區 (需要最新的用戶端驅動程式)。
- 在 Azure SQL Database 中使用 Intel SGX 記憶體保護區 (在 DC 系列資料庫中) 時,證明為必要,且需要 Microsoft Azure 證明。
- Azure SQL 資料庫中的 VBS 記憶體保護區不支援證明。
如需詳細資訊,請參閱
術語
已啟用記憶體保護區的金鑰
具有安全記憶體保護區的 Always Encrypted 引入了已啟用記憶體保護區的金鑰概念:
- 已啟用記憶體保護區的資料行主要金鑰 - 在資料庫內部資料行主要金鑰中繼資料物件中指定
ENCLAVE_COMPUTATIONS屬性的資料行主要金鑰。 資料行主要金鑰中繼資料物件也必須包含中繼資料屬性的有效簽章。 如需詳細資訊,請參閱 CREATE COLUMN MASTER KEY (Transact-SQL) - 已啟用記憶體保護區的資料行加密金鑰 - 以已啟用記憶體保護區的資料行主要金鑰進行加密的資料行加密金鑰。 安全記憶體保護區內只能使用已啟用記憶體保護區的資料行加密金鑰執行計算。
如需詳細資訊,請參閱為具有安全記憶體保護區的 Always Encrypted 管理金鑰。
已啟用記憶體保護區的資料行
已啟用記憶體保護區的資料行是以已啟用記憶體保護區資料行加密金鑰進行加密的資料庫資料行。
已啟用記憶體保護區的資料行機密計算功能
具有安全記憶體保護區的 Always Encrypted 其兩大優點為就地加密和豐富機密查詢。
就地加密
就地加密允許對安全記憶體保護區內的資料庫資料行進行密碼編譯作業,而無需將資料移出資料庫。 就地加密可提升密碼編譯作業的效能和可靠性。 您可使用 ALTER TABLE (Transact-SQL) 陳述式執行就地加密。
可就地執行的密碼編譯作業如下:
- 使用已啟用記憶體保護區的資料行加密金鑰加密純文字資料行。
- 重新加密已啟用記憶體保護區的加密資料行,以:
- 輪替資料行加密金鑰 - 使用已啟用記憶體保護區的新資料行加密金鑰重新加密資料行。
- 例如,將已啟用記憶體保護區的資料行加密類型從確定性變更為隨機。
- 解密儲存在加密資料行中的資料 (將資料行轉換成純文字資料行)。
只要與密碼編譯作業有關的資料行加密金鑰已啟用記憶體保護區,確定性和隨機加密就都可以就地加密。
機密查詢
注意
SQL Server 2022 (16.x) 為機密查詢新增在加密資料行上執行 JOIN、GROUP BY 和 ORDER BY 作業的額外支援。
機密查詢是在安全記憶體保護區內對已啟用記憶體保護區資料行執行作業的 DML 查詢。
安全記憶體保護區內支援的作業包括:
| 作業 | Azure SQL Database | SQL Server 2022 (16.x) | SQL Server 2019 (15.x) |
|---|---|---|---|
| 比較運算子 | 支援 | 支援 | 支援 |
| BETWEEN (Transact-SQL) | 支援 | 支援 | 支援 |
| IN (Transact-SQL) | 支援 | 支援 | 支援 |
| LIKE (Transact-SQL) | 支援 | 支援 | 支援 |
| DISTINCT | 支援 | 支援 | 支援 |
| 聯結 | 支援 | 支援 | 僅支援巢狀的迴圈聯結 |
| SELECT - ORDER BY 子句 (Transact-SQL) | 支援 | 已支援 | 不支援 |
| SELECT - GROUP BY- Transact-SQL | 支援 | 已支援 | 不支援 |
注意
安全記憶體保護區內部的上述作業需要隨機加密。 不支援確定性加密。 相等比較仍是使用確定性加密的資料行可用的作業。
資料庫的相容性層級應設定為 SQL Server 2022 (160) 或更高版本。
在 Azure SQL Database 和 SQL Server 2022 (16.x) 中,對字元字串資料行 (char、nchar) 使用記憶體保護區的機密查詢,會要求資料行使用二進位字碼指標 (_BIN2) 定序或 UTF-8 定序。 在 SQL Server 2019 (15.x) 中,需要 a_BIN2 定序。
如需詳細資訊,請參閱使用安全記憶體保護區執行 Transact-SQL 陳述式。
已啟用記憶體保護區的資料行上索引
您可在使用隨機加密的已啟用記憶體保護區資料行中建立非叢集索引,讓使用安全記憶體保護區的機密 DML 查詢執行得更快。
為確保使用隨機加密所加密資料行上索引不會外洩機密資料,索引資料結構 (B 型樹狀結構) 中的索引鍵值會加密,並根據其純文字值排序。 按純文字值排序也適用於在記憶體保護區內處理查詢。 當資料庫引擎中的查詢執行程式使用加密資料行上的索引,於記憶體保護區內部進行計算時,它會搜尋索引來查閱儲存在資料行中的特定值。 每個搜尋都可能會涉及多次比較。 查詢執行程式會將每一次的比較委派給記憶體保護區,記憶體保護區則會解密儲存在資料行中的值,以及要比較的加密索引鍵值;它接著會在純文字上執行比較,然後將比較的結果傳回執行程式。
目前仍不支援在使用隨機加密,但沒有啟用記憶體保護區的資料行上建立索引。
使用確定性加密的資料行上索引,會根據加密文字 (而非純文字) 排序,無論資料行是否啟用記憶體保護區。
如需詳細資訊,請參閱使用具有安全記憶體保護區的 Always Encrypted 在資料行上建立及使用索引。 如需資料庫引擎中索引運作方式的一般資訊,請參閱叢集與非叢集索引說明一文。
資料庫復原
若 SQL Server 的執行個體失敗,其資料庫可能會處於資料檔案仍包含交易中修改項目未完成的狀態。 執行個體啟動時,它會執行稱為資料庫復原的處理序,該處理序會涉及復原交易記錄中所找到的每個未完成交易,確保資料庫的完整性能獲得保留。 若未完成的交易更動了索引,那些變更也必須要復原。 例如,索引中的某些索引鍵值可能需要移除或重新插入。
重要
Microsoft 強烈建議先為您的資料庫啟用高速資料庫復原 (ADR),再使用隨機加密進行加密,以在啟用記憶體保護區的資料行上建立第一個索引。 預設會在 Azure SQL Database 中啟用 ADR,但不會在 SQL Server 2019 (15.x) 和更新版本中啟用。
若透過傳統式資料庫復原處理序 (遵循 ARIES) 復原對索引進行的變更,SQL Server 必須等待應用程式將資料行的資料行加密金鑰提供給記憶體保護區,這可能會花費很長的時間。 加速資料庫復原 (ADR) 可大幅減少因為無法在記憶體保護區內快取中取得資料行加密金鑰,而必須延遲的復原作業數目。 因此,它可以透過將封鎖新交易的機會降至最低,來大幅增加資料庫的可用性。 啟用 ADR 後,雖然 SQL Server 仍需要資料行加密金鑰來完成清理舊的資料版本,但它會以背景工作的形式進行,不會影響資料庫的可用性或使用者交易。 您可能會在錯誤記錄檔中看到錯誤訊息,指出因缺少資料行加密金鑰而無法完成清理作業。
安全性考量
下列安全性考量事項適用於具備安全記憶體保護區的 Always Encrypted。
- VBS 記憶體保護區有助於保護資料免受 VM 內部的攻擊。 不過,它們不會使用來自主機的特殊權限系統帳戶來提供任何保護以免受攻擊。 Intel SGX 記憶體保護區可保護資料免受來自客體 OS 和主機 OS 的攻擊。
- 建議在下列情況下使用記憶體保護區證明:如果您的環境可以使用,且您想要在具有裝載您資料庫之電腦 OS 層級系統管理員存取權的使用者發動攻擊時,保護資料免受攻擊。 如果您使用證明,您必須確定證明服務及其組態是由受信任的系統管理員所管理。 此外,這兩項支援的證明服務提供不同的原則和證明模式,其中一些會對記憶體保護區及其環境執行基本驗證,且旨在用於測試及開發。 請仔細遵循您證明服務特定的指導方針,確保您針對生產環境部署使用建議的組態和原則。
- 以啟用記憶體保護區資料行加密金鑰的隨機加密來加密資料行,可能會因為這類資料行支援範圍比較,而造成資料行中的資料儲存順序外洩。 例如,如果包含員工薪資的加密資料行中具有索引,則惡意的 DBA 可能會掃描索引來尋找最大加密薪資值,並識別薪資最高的人員 (假設該人員的姓名未加密)。
- 如果您使用 Always Encrypted 來保護敏感性資料,使其不受未獲授權的 DBA 存取,請不要與 DBA 共用資料行主要金鑰或資料行加密金鑰。 DBA 可以透過使用記憶體保護區內的資料行加密金鑰快取,在無需直接存取金鑰的情況下管理加密資料行上的索引。
商務持續性、災害復原和資料移轉的考量
為使用具有安全記憶體保護區之 Always Encrypted 的資料庫設定高可用性或災害復原解決方案時,請確定所有資料庫複本都可以使用安全的記憶體保護區。 如果記憶體保護區適用於主要複本,但不適用於次要複本,則嘗試使用具有安全記憶體保護區的 Always Encrypted 功能其所有陳述式在容錯移轉後都會失敗。
當使用具有安全記憶體保護區的 Always Encrypted 複製或遷移資料庫時,請確定目標環境一律支援記憶體保護區。 否則,使用記憶體保護區的陳述式將無法在複本或所移轉資料庫上運作。
請務必牢記下列特定考量:
SQL Server
- 設定 Always On 可用性群組時,請確保可用性群組中裝載資料庫的每個 SQL Server 執行個體都支援具有安全記憶體保護區的 Always Encrypted,並設定了記憶體保護區和證明。
- 當將使用具有安全記憶體保護區 Always Encrypted 功能的資料庫備份檔案還原到未設定記憶體保護區上 SQL Server 執行個體時,還原作業會成功,並可使用所有不依賴記憶體保護區的功能。 但是,所有使用記憶體保護區功能的後續陳述式都會失敗,且使用隨機加密的已啟用記憶體保護區資料行上索引都會失效。 當將使用資料庫 (其具有安全記憶體保護區 Always Encrypted) 連結到未設定記憶體保護區的執行個體時,也會發生相同情況。
- 如果資料庫在使用隨機加密的啟用記憶體保護區資料行上包含索引,請務必先在資料庫中啟用加速資料庫復原 (ADR),再建立資料庫備份。 ADR 將會確保資料庫 (包含索引) 在還原資料庫後立即開放使用。 如需詳細資訊,請參閱資料庫復原。
Azure SQL Database
- 設定主動式異地複寫時,如果主要資料庫支援安全記憶體保護區,請確定次要資料庫也支援。
在 SQL Server 和 Azure SQL Database 中,當使用 bacpac 檔案遷移資料庫時,您必須確定在建立 bacpac 檔案前,已卸除所有使用隨機加密的啟用索引記憶體保護區資料行其索引。
已知的限制
具有安全記憶體保護區的 Always Encrypted 可利用索引支援就地加密和更豐富機密查詢,因應 Always Encrypted 的一些限制,如已啟用記憶體保護區的資料行機密計算功能所述。
限制中所列 Always Encrypted 的所有其他限制,也適用於具有安全記憶體保護區的 Always Encrypted。
下列限制僅適用於具備安全記憶體保護區的 Always Encrypted:
- 無法在使用隨機加密啟用記憶體保護區的資料行上建立叢集索引。
- 使用隨機加密的已啟用記憶體保護區資料行不能作為主索引鍵資料行,且無法由外部索引鍵條件約束或唯一索引鍵條件約束參考。
- 在 SQL Server 2019 (15.x) 中 (此限制不適用於 Azure SQL Database 或 SQL Server 2022 (16.x)),使用隨機加密的已啟用記憶體保護區資料行僅支援巢狀迴圈聯結 (使用索引,如果有的話)。 如需不同產品間其他差異的資訊,請參閱機密查詢。
- 除了變更相同字碼頁中的定序和可 NULL 性外,就地密碼編譯作業無法與資料行中繼資料的任何其他變更合併。 例如,您無法加密、重新加密或解密資料行,同時在單一
ALTER TABLE/ALTER COLUMNTransact-SQL 陳述式中變更資料行的資料類型。 請使用兩個個別的陳述式。 - 不支援對記憶體內部資料表中的資料行使用已啟用記憶體保護區的金鑰。
- 定義計算資料行的運算式,無法對使用隨機加密的已啟用記憶體保護區資料行執行任何計算 (即使是機密查詢中所列支援作業中的計算也不行)。
- 在使用隨機加密的已啟用記憶體保護區資料行上,不支援 LIKE 運算子參數中的逸出字元。
- 透過使用 LIKE 運算子或具有使用下列任一資料類型 (在加密之後會成為大型物件) 查詢參數的比較運算子所進行的查詢會忽略索引,並執行資料表掃描。
nchar[n]和nvarchar[n],如果 n 大於 3967。char[n]、varchar[n]、binary[n]、varbinary[n],如果 n 大於 7935。
- 工具限制:
- 若要儲存已啟用記憶體保護區的資料行主要金鑰,唯一支援的金鑰存放區是 Windows 憑證存放區和 Azure Key Vault。
- 若要透過
ALTER TABLE/ALTER COLUMN觸發就地密碼編譯作業,您必須使用 SSMS 中的查詢視窗或 Azure Data Studio 發出陳述式,也可以撰寫自己的程式來發出陳述式。 目前,SqlServer PowerShell 模組中的Set-SqlColumnEncryptionCmdlet 和 SQL Server Management Studio 中的 [Always Encrypted 精靈] 不支援就地加密。 將資料移出資料庫以進行密碼編譯作業,即使用於作業的資料行加密金鑰為已啟用記憶體保護區也一樣。
- 當您還原已啟用 VBS 記憶體保護區的資料庫時,請務必再次重新設定 VBS 記憶體保護區設定。
下一步
- 教學課程:開始使用具有安全記憶體保護區的 Always Encrypted
- 設定和使用具有安全記憶體保護區的 Always Encrypted
- 執行 SQL Server 範例 GitHub 存放庫中具有安全記憶體保護區的 Always Encrypted 示範/範例
- 深入了解 Azure 機密運算
另請參閱
意見反應
即將登場:在 2024 年,我們將逐步淘汰 GitHub 問題作為內容的意見反應機制,並將它取代為新的意見反應系統。 如需詳細資訊,請參閱:https://aka.ms/ContentUserFeedback。
提交並檢視相關的意見反應