使用 Reporting Services 來驗證擴充保護
「擴充保護」是 Microsoft Windows 作業系統最新版本的一組增強功能。 擴充保護會增強應用程式保護認證與驗證的方式。 此功能本身並不會針對認證轉送這類特定攻擊直接提供保護,但會為 Reporting Services 這類應用程式提供基礎結構,以增強驗證擴充保護。
屬於擴充保護一部分的主要驗證增強功能為服務繫結與通道繫結。 通道繫結使用通道繫結 Token (CBT) 驗證兩點端點之間建立的通道是否未受到危害。 服務繫結使用服務主要名稱 (SPN) 驗證預期的驗證 Token 目的地。 如需擴充保護的詳細背景資訊,請參閱具有擴充保護的整合式 Windows 驗證。
SQL Server Reporting Services (SSRS) 會支援並強制執行已在作業系統中啟用,且在 Reporting Services 中設定的擴充保護。 依預設,Reporting Services 會接受指定交涉或 NTLM 驗證的要求,因此可以在作業系統與 Reporting Services 擴充保護功能中獲得擴充保護支援。
重要
Windows 預設不會啟用 [擴充保護]。 如需如何在 Windows 中啟用「擴充保護」的資訊,請參閱驗證擴充保護。 作業系統與用戶端驗證堆疊必須同時支援擴充保護,驗證才會成功。 對於舊版作業系統,您可能需要針對完整具備擴充保護的電腦安裝多個更新。 如需擴充保護之最近開發狀況的詳細資訊,請參閱擴充保護的更新資訊。
Reporting Services 擴充保護概觀
SSRS 支援並強制執行已在作業系統中啟用的擴充保護。 如果作業系統不支援擴充保護,或者尚未啟用作業系統中的功能,則 Reporting Services 擴充保護功能將會無法驗證。 Reporting Services 擴充保護也需要 TLS/SSL 憑證。 如需詳細資訊,請參閱在原生模式報表伺服器上設定 TLS 連線
重要
Reporting Services 預設不會啟用 [擴充保護]。 修改 rsreportserver.config 組態檔或使用 WMI API 更新組態檔,即可啟用該功能。 SSRS 未提供可修改或檢視擴充保護設定的使用者介面。 如需詳細資訊,請參閱本主題中的 組態設定 一節。
因為擴充保護設定變更或進行之設定錯誤所造成的常見問題,不會以明顯的錯誤訊息或對話方塊視窗公開。 與擴充保護設定和相容性相關的問題會導致驗證失敗,並將錯誤記錄在 Reporting Services 追蹤記錄中。
重要
某些資料存取技術可能不支援擴充保護。 資料存取技術可用於連接 SQL Server 資料來源與 Reporting Services 目錄資料庫。 無法支援擴充保護的資料存取技術會以下列方式對 Reporting Services 造成影響:
- 執行 Reporting Services 目錄資料庫的 SQL Server 無法啟用擴充功能,否則報表伺服器將無法成功連線至目錄資料庫,並傳回驗證錯誤。
- 用作 Reporting Services 報表資料來源的 SQL Server 執行個體無法啟用擴充保護,否則報表伺服器為連線至報表資料來源所做的嘗試將會失敗,並傳回驗證錯誤。
資料存取技術的文件應具有支援擴充保護的資訊。
升級
將 Reporting Services 伺服器升級至 SQL Server 2016 時,會將具有預設值的組態設定新增至 rsreportserver.config 檔案。 如果這些設定已經存在,SQL Server 2016 安裝會將它們保留在 rsreportserver.config 檔案中。
將組態設定新增至 rsreportserver.config 組態檔時,預設行為是關閉 Reporting Services 擴充保護功能,因此您必須按照這篇文章中的描述,啟用該功能。 如需詳細資訊,請參閱本文中的組態設定一節。
設定
RSWindowsExtendedProtectionLevel的預設值為Off。設定
RSWindowsExtendedProtectionScenario的預設值為Proxy。Upgrade Advisor 不會驗證作業系統或目前安裝的 Reporting Services 是否已啟用擴充保護支援。
Reporting Services 擴充保護不涵蓋的功能
Reporting Services 擴充保護功能不支援下列功能區和案例:
Reporting Services 自訂安全性延伸模組的作者必須將擴充保護的支援新增至其自訂安全性延伸模組。
協力廠商必須更新新增至 Reporting Services 或由 Reporting Services 安裝所使用的協力廠商元件,才能支援擴充保護。 如需詳細資訊,請連絡協力廠商。
部署案例與建議
下列情節說明不同的部署和拓撲,以及使用 Reporting Services 擴充保護來保護其安全的建議設定。
直接
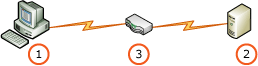
此案例描述直接連接至報表伺服器,例如內部網路環境。
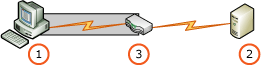
Proxy 與網路負載平衡
用戶端應用程式所連線的裝置或軟體會執行 TLS,並向伺服器傳遞認證以進行驗證,例如外部網路、網際網路或安全的內部網路。 用戶端連接至 Proxy 或所有用戶端都使用 Proxy。
這個情況與您使用網路負載平衡 (NLB) 裝置相同。
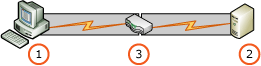
閘道
此案例描述連線至會執行 TLS 並驗證使用者之裝置或軟體的用戶端應用程式。 接著,裝置或軟體會模擬使用者內容或不同的使用者內容,之後才對報表伺服器發出要求。
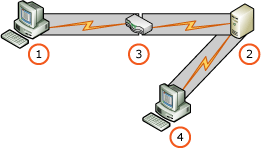
合併
此案例描述用戶端連線至 Proxy 的外部網路或網際網路環境,以及用戶端連線至報表伺服器的內部網路環境。
設定 Reporting Services 擴充保護
rsreportserver.config 檔案包含的設定值可以控制 Reporting Services 擴充保護的行為。
如需有關如何使用和編輯 rsreportserver.config 檔案的詳細資訊,請參閱 RsReportServer.config 組態檔。 擴充保護設定也可以透過 WMI API 變更與檢查。 如需詳細資訊,請參閱 SetExtendedProtectionSettings 方法 (WMI MSReportServer_ConfigurationSetting)。
當組態設定的驗證失敗時,報表伺服器上會停用驗證類型 RSWindowsNTLM、RSWindowsKerberos 和 RSWindowsNegotiate。
Reporting Services 擴充保護的組態設定
下表提供在 rsreportserver.config 中顯示之擴充保護的組態設定相關資訊。
| 設定 | 描述 |
|---|---|
RSWindowsExtendedProtectionLevel |
指定擴充保護的強制執行程度。 有效值為:Off:預設。 不會指定通道繫結或服務繫結驗證。Allow 支援擴充保護,但不需要擴充保護。 指定:- 擴充保護將會針對在支援擴充保護之作業系統上執行的用戶端應用程式強制執行。 如何強制執行保護,取決於設定 RsWindowsExtendedProtectionScenario- 對於在不支援擴充保護之作業系統上執行的應用程式,允許執行驗證。 Require 會指定:- 擴充保護將會針對在支援擴充保護之作業系統上執行的用戶端應用程式強制執行。 - 對於在不支援擴充保護之作業系統上執行的應用程式,不允許執行驗證。 |
RsWindowsExtendedProtectionScenario |
指定要驗證的擴充保護形式:通道繫結、服務繫結或兩者。 有效值為:Proxy:預設。 指定:\- Windows NTLM、Kerberos 和交涉驗證 (當通道繫結權杖存在時)。 \- 服務繫結會強制執行。 Any 會指定:- Windows NTLM、Kerberos 和交涉驗證,而不需要通道繫結。 \- 服務繫結會強制執行。 Direct 會指定:\- Windows NTLM、Kerberos 和交涉驗證 (當 CBT 存在、目前服務的 TLS 連線存在,而且 TLS 連線的 CBT 與 NTLM、Kerberos 或交涉權杖的 CBT 相符時)。 - 服務繫結會強制執行。 備註:如果系統將 RsWindowsExtendedProtectionLevel 設定為 OFF,則會忽略 RsWindowsExtendedProtectionScenario 設定。 |
rsreportserver.config 組態檔中的範例項目︰
<Authentication>
<RSWindowsExtendedProtectionLevel>Allow</RSWindowsExtendedProtectionLevel>
<RSWindowsExtendedProtectionScenario>Proxy</RSWindowsExtendedProtectionLevel>
</Authentication>
服務繫結與隨附的 SPN
服務繫結使用服務主要名稱或 SPN 驗證預期的驗證 Token 目的地。 Reporting Services 使用現有 URL 保留資訊來建立視為有效的 SPN 清單。 URL 保留資訊同時驗證保留的 SPN 和 URL,讓系統管理員從單一位置同時進行管理。
發生下列其中一個動作時,會更新有效的 SPN 清單:
- 報表伺服器隨即啟動。
- 擴充保護的組態設定已變更。
- 應用程式定義域已回收。
有效的 SPN 清單專屬於每個應用程式。 例如,報表管理員和報表伺服器會各自計算一份不同的有效 SPN 清單。
下列因素可決定針對應用程式計算的有效 SPN:
每個保留的 URL。
從 Reporting Services 服務帳戶之網域控制站擷取的每個 SPN。
如果保留的 URL 包括萬用字元 ('*' 或 '+'),則報表伺服器將會從主機集合加入每個項目。
主機集合來源。
下表列出主機集合的潛在來源。
| 來源類型 | 描述 |
|---|---|
| ComputerNameDnsDomain | 指派給本機電腦之 DNS 網域的名稱。 如果本機電腦是叢集中的一個節點,則會使用叢集虛擬伺服器的 DNS 網域名稱。 |
| ComputerNameDnsFullyQualified | 唯一識別本機電腦的完整 DNS 名稱。 此名稱結合 DNS 主機名稱與 DNS 網域名稱,其格式為 HostName.DomainName。 如果本機電腦是叢集中的一個節點,則會使用叢集虛擬伺服器的完整 DNS 名稱。 |
| ComputerNameDnsHostname | 本機電腦的 DNS 主機名稱。 如果本機電腦是叢集中的一個節點,則會使用叢集虛擬伺服器的 DNS 主機名稱。 |
| ComputerNameNetBIOS | 本機電腦的 NetBIOS 名稱。 如果本機電腦是叢集中的一個節點,則會使用叢集虛擬伺服器的 NetBIOS 名稱。 |
| ComputerNamePhysicalDnsDomain | 指派給本機電腦之 DNS 網域的名稱。 如果本機電腦是叢集中的一個節點,則會使用本機電腦的 DNS 網域名稱,而非叢集虛擬伺服器的名稱。 |
| ComputerNamePhysicalDnsFullyQualified | 唯一識別電腦的完整 DNS 名稱。 如果本機電腦是叢集中的一個節點,則會使用本機電腦的完整 DNS 名稱,而非叢集虛擬伺服器的名稱。 完整的 DNS 名稱結合 DNS 主機名稱與 DNS 網域名稱,其格式為 HostName.DomainName。 |
| ComputerNamePhysicalDnsHostname | 本機電腦的 DNS 主機名稱。 如果本機電腦是叢集中的一個節點,則會使用本機電腦的 DNS 主機名稱,而非叢集虛擬伺服器的名稱。 |
| ComputerNamePhysicalNetBIOS | 本機電腦的 NetBIOS 名稱。 如果本機電腦是叢集中的一個節點,則此來源為本機電腦的 NetBIOS 名稱,而非叢集虛擬伺服器的名稱。 |
如需詳細資訊,請參閱為報表伺服器註冊服務主體名稱 (SPN) 和關於 URL 保留項目和註冊 (報表伺服器組態管理員)。
相關內容
使用擴充保護連線至資料庫引擎
驗證擴充保護概觀
具有擴充保護的整合式 Windows 驗證
Microsoft 資訊安全諮詢:驗證延伸保護
報表伺服器服務追蹤記錄
RsReportServer.config 組態檔
SetExtendedProtectionSettings 方法 (WMI MSReportServer_ConfigurationSetting)
更多問題嗎? 請嘗試詢問 Reporting Services 論壇
意見反應
即將登場:在 2024 年,我們將逐步淘汰 GitHub 問題作為內容的意見反應機制,並將它取代為新的意見反應系統。 如需詳細資訊,請參閱:https://aka.ms/ContentUserFeedback。
提交並檢視相關的意見反應