在 SDN 基礎結構中於網路之間進行流量路由
重要
此版本的 Virtual Machine Manager (VMM) 已終止支援。 建議您 升級至 VMM 2022。
本文說明如何在 System Center Virtual Machine Manager (VMM) 網狀架構所設定的軟體定義網路 (SDN) 基礎結構中跨網路路由流量。
無論資源位於何處,您皆可透過 SDN RAS 閘道,在實體和虛擬網路之間進行網路流量的路由。 SDN RAS 閘道支援多重租用戶、邊界閘道協定 (BGP),及使用 IPsec 或 Generic Routing Encapsulation (GRE) 或 Layer 3 轉送的站對站虛擬私人網路 (VPN) 連線。 深入了解。
注意
- 從 VMM 2019 UR1 起,單一連線網路類型已變更為連線的網路。
- VMM 2019 UR2 和更新版本支援 IPv6。
- IPSec 通道、GRE 通道和 L3 層通道支援 IPv6。
注意
- IPSec 通道、GRE 通道和 L3 層通道支援 IPv6。
開始之前
確認下列事項:
部署 SDN 網路控制站、SDN 軟體 Load Balancer 和 SDN RAS 閘道。
建立具有網路虛擬化的 SDN VM 網路。
使用 VMM 設定站對站 VPN 連線
站對站 VPN 連線可讓您使用因特網,在不同的實體位置安全地連線兩個網路。
對於在其 Datacenter 中代管許多租用戶的雲端服務提供者 (CSP) 來說,SDN RAS 閘道提供一項多重租用戶閘道解決方案,讓您的租用戶能從遠端站台透過站對站 VPN 連線,存取及管理其資源,因而讓您 Datacenter 中虛擬資源與其實體網路之間能進行網路流量。
VMM 2022 支援 SDN 元件的雙堆疊 (Ipv4 + Ipv6) 。
若要啟用站對站 VPN 連線的 IPv6,路由子網路必須同時為 IPv4 和 IPv6。 若要讓閘道在 IPv6 中正常運作,請提供以分號 ( ; ) 分隔的 IPv4 和 IPv6 位址,並在遠端端點中提供 IPv6 位址。 例如,192.0.2.1/23;2001:0db8:85a3:0000:0000:8a2e:0370::/64。 若要指定VIP範圍,請勿使用IPv6位址的縮短格式;使用 '2001:db8:0:200:0:0:7' 格式,而不是 '2001:db8:0:200::7'。
設定 IPSec 連線
使用下列程序:
- 選取您要設定站對站IPSec連線的 VM 網路,然後選取 [連線]。
- 選取 [透過 VPN 通道連線至其他網路]。 或者,若要在資料中心啟用 BGP 對等互連,請選取 [啟用邊界閘道協定 (BGP)]。
- 選取閘道裝置的網路控制卡服務。
- 選取 [VPN 連線]>[新增]>[新增 IPSec 通道]。
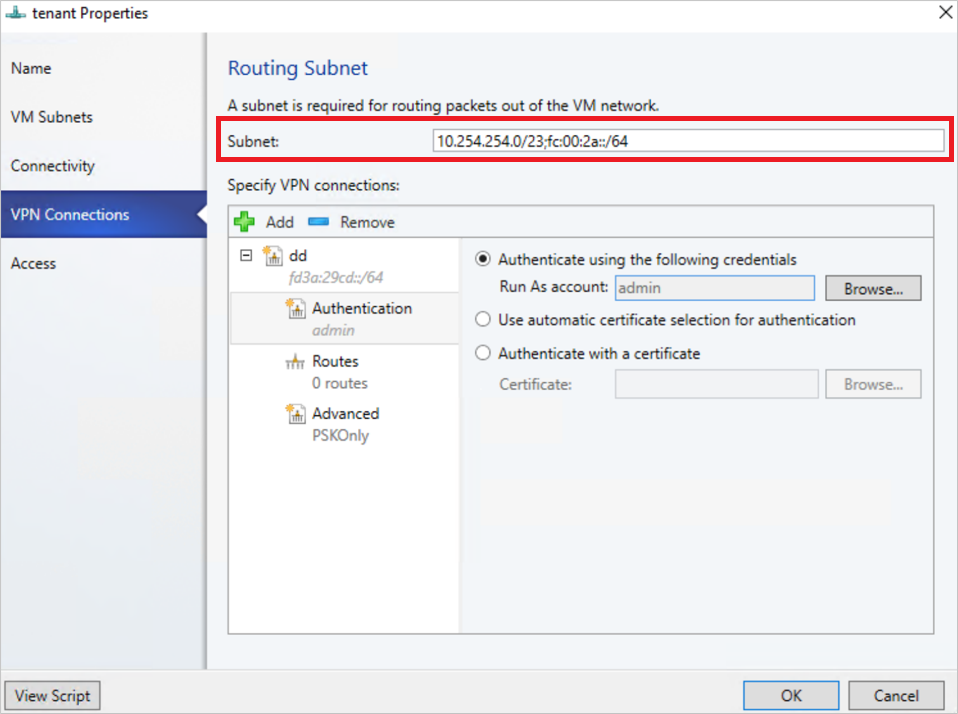
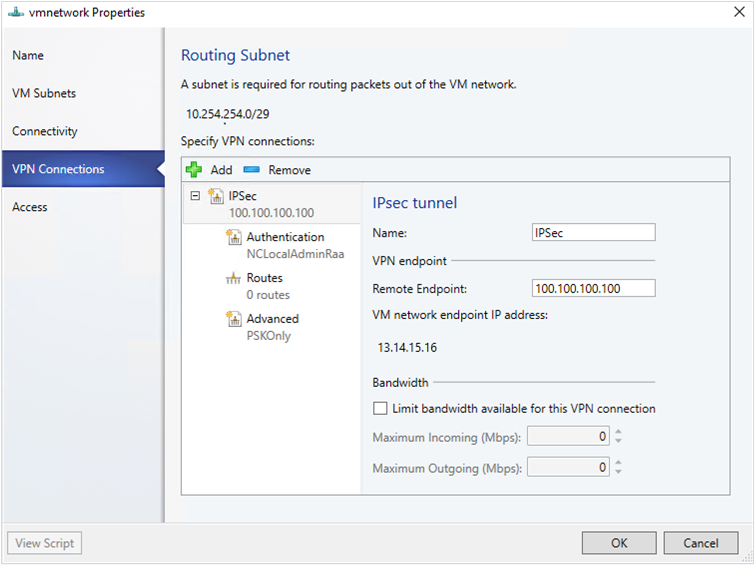
- 輸入子網路,如下圖所示。 這個子網路用來將封包路由傳送到 VM 網路外部。 您不需要在資料中心預先設定此子網。
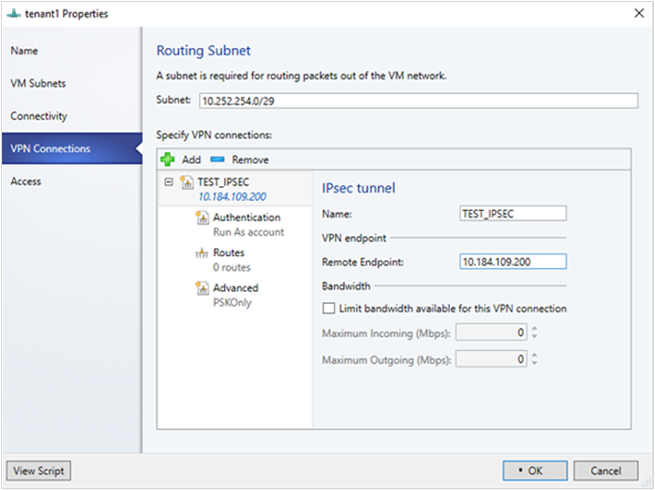
- 輸入連線的名稱,以及遠端端點的IP位址。 選擇性地設定頻寬。
- 在 [驗證] 中,選取您要使用的驗證類型。 如果您選擇使用執行身分帳戶進行驗證,請建立一個具有使用者名稱的使用者帳戶,並使用 IPSec 金鑰作為帳戶的密碼。
- 在 [路由] 中,輸入您要連線的所有遠端子網路。 如果您已在 [連線能力] 頁面中選取 [啟用邊界閘道通訊協定 (BGP) ,則不需要路由。
- 在 [進階] 索引標籤上,接受預設設定。
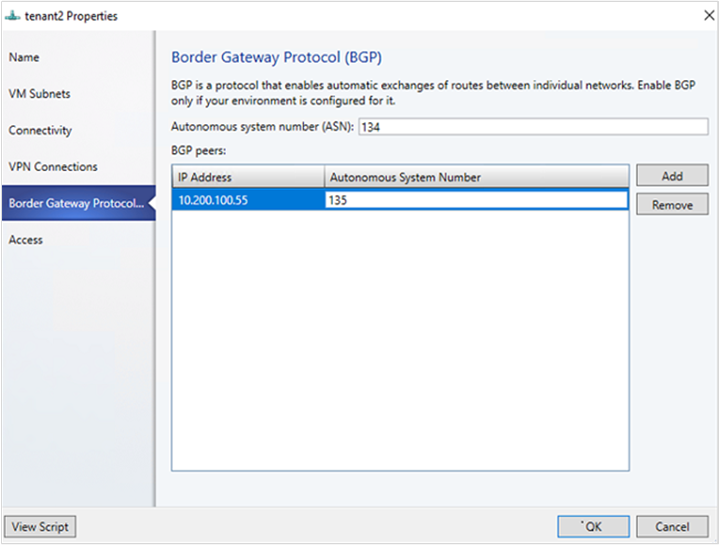
- 如果您已在 [連線能力] 頁面中選取 [啟用邊界網關通訊協定] (BGP) ,您可以在 [ 邊界網關通訊協定 精靈] 頁面上填寫 ASN、對等 BGP IP 及其 ASN,如下所示:
- 若要驗證連線,請嘗試從 VM 網路的其中一部虛擬機器,Ping 遠端端點 IP 位址。
設定 GRE 通道
GRE 通道能讓租用戶虛擬網路與外部網路之間能有連線。 由於 GRE 通訊協定是輕量型的,而且大部分的網路裝置都支援 GRE,因此成為不需要加密數據之通道的理想選擇。 站對站 (S2S) 通道中的 GRE 支援,有助於在租用戶虛擬網路與租用戶外部網路之間,傳遞流量。
使用下列程序:
- 選取您想要設定 S2S GRE 連線的 VM 網络,然後選取 [連線]。
- 選取 [透過 VPN 通道連線至其他網路]。 或者,若要在資料中心啟用 BGP 對等互連,請選取 [啟用邊界閘道協定 (BGP)]。
- 選取閘道裝置的網路控制站服務。
- 選取 [VPN 連線]>[新增]>[新增 GRE 通道]。
- 輸入子網路,如下圖所示。 這個子網路用來將封包路由傳送到 VM 網路外部。 您資料中心不需要預先設定此子網。
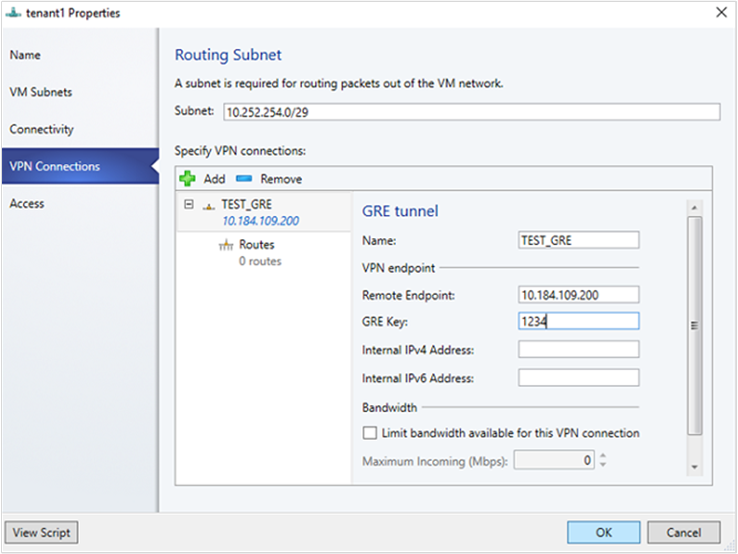
- 輸入連線名稱,並且指定遠端端點的 IP 位址。
- 鍵入 GRE 金鑰。
- 您可以選擇性地完成此畫面上的其他欄位;設定連線不需要這些值。
- 在 [路由] 中,新增您要連線的所有遠端子網路。 如果您在 [連線] 中選取 [啟用邊界閘道協定 (BGP)],則可以將此畫面保留空白,並改為在 [邊界閘道協定] 索引標籤上完成您的 ASN、對等 BGP IP 及 ASN 欄位。
- 其餘的設定可以使用預設值。
- 若要驗證連線,請嘗試從 VM 網路上的其中一部虛擬機器來 Ping 遠端端點的 IP 位址。
設定遠端站台上的 IPsec 與 GRE 連線
在遠端對等裝置上,使用 VMM UI 中的 VM 網路端點 IP 位址 作為目的地位址,同時設定 IPSec\GRE 連線。
設定 L3 轉寄
L3 轉送閘道能在 Datacenter 內的實體基礎結構與 Hyper-V 網路虛擬雲端中的虛擬基礎結構之間建立連線。
租用戶網路虛擬機器可以使用 L3 轉送,透過已在 SDN 環境中設定完成的 Windows Server 2016 SDN 閘道來連線到實體網路。 在這種情況下,SDN 閘道的作用是虛擬網路和實體網路之間的路由器。
若要深入了解,請參閱這些文章︰使用 Windows Server 閘道作為私人雲端環境的轉送閘道和 RAS Gateway High Availability (RAS 閘道高可用性)。
在嘗試設定 L3 之前,請確認下列事項:
- 請確保您是以 VMM 伺服器的系統管理員身分登入。
- 您必須為需要設定 L3 轉送的各個租用戶 VM 網路,設定具有唯一 VLAN 識別碼的唯一下一個躍點邏輯網路。 租用戶網路和對應的實體網路之間必須有 1:1 的對應 (具有唯一的 VLAN 識別碼)。
請使用下列步驟在 SCVMM 中建立下一個躍點邏輯網路:
在 VMM 控制臺上,選取 [ 邏輯網络],以滑鼠右鍵按兩下並選取 [ 建立邏輯網络]。
在 [設定] 頁面中,選擇 [一個連線網路] 並選取 [使用相同名稱建立 VM 網路以允許虛擬機器直接存取此邏輯網路] 及 [由 Microsoft 網路控制卡管理]
為這個新的邏輯網路建立 IP 集區。
用於設定 L3 轉送的指令碼會需要來自這個集區的 IP 位址。
下表提供動態和靜態 L3 連線的範例。
| 參數 | 詳細資料/範例值 |
|---|---|
| L3VPNConnectionName | L3 轉送網路連線的使用者定義名稱。 範例:Contoso_L3_GW |
| VmNetworkName | 可透過 L3 網路連線到達的租用戶虛擬網路名稱。 執行指令碼時,此網路必須存在。 範例:ContosoVMNetwork |
| NextHopVMNetworkName | 下一個躍點 VM 網路的使用者定義名稱,依必要條件而建立。 這代表想要與租用戶 VM 網路通訊的實體網路。 執行此指令碼時,此網路必須存在。 範例:Contoso_L3_Network |
| LocalIPAddresses | 要在 SDN 閘道 L3 網路介面上設定的 IP 位址。 此 IP 位址必須屬於您建立的下一個躍點邏輯網路。 您也必須提供子網路遮罩。 範例:10.127.134.55/25 |
| PeerIPAddresses | 可透過 L3 邏輯網路到達的實體網路閘道的 IP 位址。 此 IP 位址必須屬於您在必要條件中建立的下一個躍點邏輯網路。 當指定要流向實體網路的租用戶 VM 網路流量到達 SDN 閘道時,此 IP 就會充任下一個躍點。 範例:10.127.134.65 |
| GatewaySubnet | 用於在 HVN 閘道與租用戶虛擬網路之間進行路由的子網路。 您可以使用任何子網,確定它不會與下一個躍點邏輯網路重疊。 範例:192.168.2.0/24 |
| RoutingSubnets | 必須位於 HNV 閘道 L3 介面上的靜態路由。 這些路由適用於實體網路子網,這應該可從透過 L3 連線從租使用者 VM 網路連線。 |
| EnableBGP | 啟用 BGP 的選項。 預設:false。 |
| TenantASNRoutingSubnets | 租用戶閘道的 ASN 號碼 (僅限啟用 BGP 時)。 |
請執行下列指令碼以設定 L3 轉送。 並參閱上表,了解各個指令碼參數的意義。
param (
[Parameter(Mandatory=$true)]
# Name of the L3 VPN connection
$L3VPNConnectionName,
[Parameter(Mandatory=$true)]
# Name of the VM network to create gateway
$VmNetworkName,
[Parameter(Mandatory=$true)]
# Name of the Next Hop one connected VM network
# used for forwarding
$NextHopVmNetworkName,
[Parameter(Mandatory=$true)]
# IPAddresses on the local side that will be used
# for forwarding
# Format should be @("10.10.10.100/24")
$LocalIPAddresses,
[Parameter(Mandatory=$true)]
# IPAddresses on the remote side that will be used
# for forwarding
# Format should be @("10.10.10.200")
$PeerIPAddresses,
[Parameter(Mandatory=$false)]
# Subnet for the L3 gateway
# default value 10.254.254.0/29
$GatewaySubnet = "10.254.254.0/29",
[Parameter(Mandatory=$false)]
# List of subnets for remote tenants to add routes for static routing
# Format should be @("14.1.20.0/24","14.1.20.0/24");
$RoutingSubnets = @(),
[Parameter(Mandatory=$false)]
# Enable BGP in the tenant space
$EnableBGP = $false,
[Parameter(Mandatory=$false)]
# ASN number for the tenant gateway
# Only applicable when EnableBGP is true
$TenantASN = "0"
)
# Import SC-VMM PowerShell module
Import-Module virtualmachinemanager
# Retrieve Tenant VNET info and exit if VM Network not available
$vmNetwork = Get-SCVMNetwork -Name $VmNetworkName;
if ($vmNetwork -eq $null)
{
Write-Verbose "VM Network $VmNetworkName not found, quitting"
return
}
# Retrieve L3 Network info and exit if VM Network not available
$nextHopVmNetwork = Get-SCVMNetwork -Name $NextHopVmNetworkName;
if ($nextHopVmNetwork -eq $null)
{
Write-Verbose "Next Hop L3 VM Network $NextHopVmNetworkName not found, quitting"
return
}
# Retrieve gateway Service and exit if not available
$gatewayDevice = Get-SCNetworkGateway | Where {$_.Model -Match "Microsoft Network Controller"};
if ($gatewayDevice -eq $null)
{
Write-Verbose "Gateway Service not found, quitting"
return
}
# Retrieve Tenant Virtual Gateway info
$vmNetworkGatewayName = $VmNetwork.Name + "_Gateway";
$VmNetworkGateway = Get-SCVMNetworkGateway -Name $vmNetworkGatewayName -VMNetwork $vmNetwork
# Create a new Tenant Virtual Gateway if not configured
if($VmNetworkGateway -eq $null)
{
if($EnableBGP -eq $false)
{
# Create a new Virtual Gateway for tenant
$VmNetworkGateway = Add-SCVMNetworkGateway -Name $vmNetworkGatewayName -EnableBGP $false -NetworkGateway $gatewayDevice -VMNetwork $vmNetwork -RoutingIPSubnet $GatewaySubnet;
}
else
{
if($TenantASN -eq "0")
{
Write-Verbose "Please specify valid ASN when using BGP"
return
}
# Create a new Virtual Gateway for tenant
$VmNetworkGateway = Add-SCVMNetworkGateway -Name $vmNetworkGatewayName -EnableBGP $true -NetworkGateway $gatewayDevice -VMNetwork $vmNetwork -RoutingIPSubnet $GatewaySubnet -AutonomousSystemNumber $TenantASN;
}
}
if ($VmNetworkGateway -eq $null)
{
Write-Verbose "Could not Find / Create Virtual Gateway for $($VmNetwork.Name), quitting"
return
}
# Check if the network connection already exists
$vpnConnection = Get-SCVPNConnection -VMNetworkGateway $VmNetworkGateway -Name $L3VPNConnectionName
if ($vpnConnection -ne $null)
{
Write-Verbose "L3 Network Connection for $($VmNetwork.Name) already configured, skipping"
}
else
{
# Create a new L3 Network connection for tenant
$vpnConnection = Add-SCVPNConnection -NextHopNetwork $nexthopvmNetwork -Name $L3VPNConnectionName -IPAddresses $LocalIPAddresses -PeerIPAddresses $PeerIPAddresses -VMNetworkGateway $VmNetworkGateway -protocol L3;
if ($vpnConnection -eq $null)
{
Write-Verbose "Could not add network connection for $($VmNetwork.Name), quitting"
return
}
Write-Output "Created VPN Connection " $vpnConnection;
}
# Add all the required static routes to the newly created network connection interface
foreach($route in $RoutingSubnets)
{
Add-SCNetworkRoute -IPSubnet $route -RunAsynchronously -VPNConnection $vpnConnection -VMNetworkGateway $VmNetworkGateway
}
設定 L3 轉寄
L3 轉送閘道能在 Datacenter 內的實體基礎結構與 Hyper-V 網路虛擬雲端中的虛擬基礎結構之間建立連線。
租用戶網路虛擬機器可以使用 L3 轉送連線,透過已在 SDN 環境中設定完成的 Windows Server 2016/2019 SDN 閘道來連線到實體網路。 在這種情況下,SDN 閘道的作用是虛擬網路和實體網路之間的路由器。
使用 L3 轉送連線,租使用者網路虛擬機可以透過已在 SDN 環境中設定的 Windows Server 2016/2019/2022 SDN 網關聯機到實體網路。 在這種情況下,SDN 閘道的作用是虛擬網路和實體網路之間的路由器。
若要深入了解,請參閱這些文章︰使用 Windows Server 閘道作為私人雲端環境的轉送閘道和 RAS Gateway High Availability (RAS 閘道高可用性)。
在嘗試設定 L3 連線之前,請確認下列事項:
- 請確保您是以 VMM 伺服器的系統管理員身分登入。
- 您必須為需要設定 L3 轉送的各個租用戶 VM 網路,設定具有唯一 VLAN 識別碼的唯一下一個躍點邏輯網路。 租用戶網路和對應的實體網路之間必須有 1:1 的對應 (具有唯一的 VLAN 識別碼)。
請使用下列步驟在 VMM 中建立下一個躍點邏輯網路:
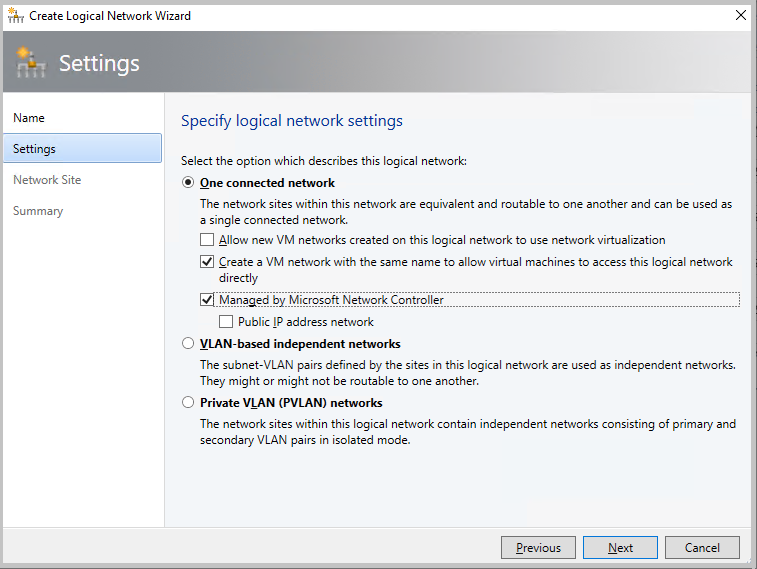
在 VMM 控制臺上,選取 [ 邏輯網络],以滑鼠右鍵按兩下並選取 [ 建立邏輯網络]。
在 [ 設定 ] 頁面中,選擇 [一個連線的網络 ],然後選取 [ 建立具有相同名稱的 VM 網络],以允許虛擬機直接存取此邏輯網络 ,並由 Microsoft 網络控制站管理。
注意
從 VMM 2019 UR1 起,單一連線網路類型已變更為連線的網路。
- 為這個新的邏輯網路建立 IP 集區。 設定 L3 轉送時會需要來自這個集區的 IP 位址。
請使用下列步驟來設定 L3 轉送:
注意
您無法限制 L3 VPN 連線中的頻寬。
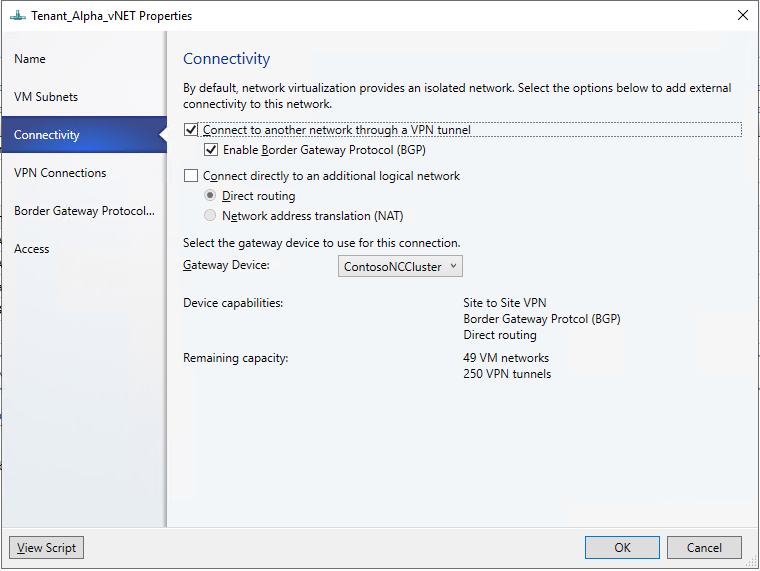
在 VMM 控制台中,選取您想要透過 L3 網關聯機到實體網路的租使用者虛擬網路。
以滑鼠右鍵按下選取的租使用者虛擬網路,然後選取 [屬性>連線]。
選取 [透過 VPN 通道連線至其他網路]。 或者,若要在資料中心啟用 BGP 對等互連,請選取 [啟用邊界閘道協定 (BGP)]。
選取閘道裝置的網路控制卡服務。
在 [VPN Connections] 頁面中,選取 [新增新增>第 3 層通道]。
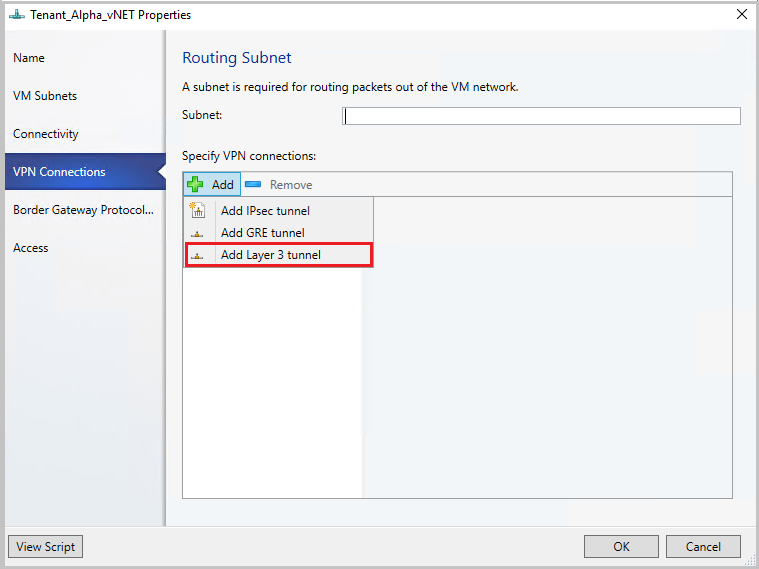
為路由子網路提供 CIDR 標記法格式的子網路。 這個子網路用來將封包路由傳送到 VM 網路外部。 您不需要在資料中心預先設定此子網。
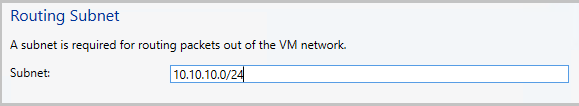
使用下列資訊,並設定 L3 連線:
| 參數 | 詳細資料 |
|---|---|
| 名稱 | L3 轉送網路連線的使用者定義名稱。 |
| VM 網路 (NextHop) | 下一個躍點 VM 網路的使用者定義名稱,依必要條件而建立。 這代表想要與租用戶 VM 網路通訊的實體網路。 當您選取 [瀏覽] 時,只能選取 [由網络服務管理的 一個已連線的 VM 網络 ]。 |
| 對等 IP 位址 | 可透過 L3 邏輯網路到達的實體網路閘道的 IP 位址。 此 IP 位址必須屬於您在必要條件中建立的下一個躍點邏輯網路。 當指定要流向實體網路的租用戶 VM 網路流量到達 SDN 閘道時,此 IP 就會充任下一個躍點。 此值必須是 IPv4 位址。 可以有多個對等 IP 位址,必須以逗號分隔。 |
| 本機 IP 位址 | 要在 SDN 閘道 L3 網路介面上設定的 IP 位址。 這些IP位址必須屬於您建立為必要條件的下一個躍點邏輯網路。 您也必須提供子網路遮罩。 範例:10.127.134.55/25. 這必須是 IPv4 位址,且應是 CIDR 標記法格式。 對等 IP 位址和本機 IP 位址應是來自相同的集區。 這些 IP 位址應屬於 VM 網路的邏輯網路定義中定義的子網路。 |
如果您使用靜態路由,請在 [路由] 中輸入您想要連線的所有遠端子網。
注意
您必須使用與 SDN 閘道上 L3 介面 IP 位址 (在建立 L3 連線時所用的本機 IP 位址) 相同的下一個躍點,在實體網路中為租用戶虛擬網路子網路設定路由。 這是為了確保傳回租用戶虛擬網路的流量會正確地透過 SDN 閘道路由。
如果您使用 BGP,請確定在 SDN 閘道內部介面 IP 位址之間建立 BGP 對等互連,其存在於閘道 VM 的不同區間中, (不是實體網路上的預設區間) 和對等裝置。
為了讓 BGP 運作,您必須執行下列步驟:
新增 L3 連線的 BGP 對等體。 在 [邊界閘道通訊協定 ] 頁面上輸入您的 ASN、對等 BGP IP 及其 ASN。
判斷 SDN 閘道內部位址,如 下一節所述。
在遠端 (實體網路閘道) 建立 BGP 對等。 建立 BGP 對等互連時,請使用 SDN 閘道內部位址 (,如上一個步驟) 判斷為對等 IP 位址。
在實體網路上設定路由,並將目的地設定為 SDN 閘道內部位址,並將下一個躍點設定為 L3 介面 IP 位址, (建立 L3 連線時使用的本機 IP 位址值) 。
注意
設定 L3 連線之後,您必須在租使用者虛擬網路子網的實體網路中設定路由,下一個躍點作為 SDN 閘道上 L3 介面的 IP 位址, (腳本中的 LocalIpAddresses 參數 localIpAddresses) 。 這是為了確保傳回租用戶虛擬網路的流量會正確地透過 SDN 閘道路由。
您可以選擇設定靜態路由或搭配 L3 連線的動態路由 (透過 BGP)。 如果您使用靜態路由,您可以使用 Add-SCNetworkRoute 來 新增它們,如下列腳本所述。
如果您搭配 L3 通道連線使用 BGP,就必須在 SDN 閘道內部介面 IP 位址 (出現於閘道 VM 上的不同區間,而非預設區間) 與實體網路上的對等裝置之間建立 BGP 對等互連。
若要讓 BGP 運作,您必須使用下列步驟:
使用 Add-SCBGPPeer Cmdlet,為 L3 連線新增 BGP 對等。
範例:Add-SCBGPPeer -Name "peer1" -PeerIPAddress "12.13.14.15" -PeerASN 15 -VMNetworkGateway $VmNetworkGateway
依照下一節的說明,判斷 SDN 閘道內部位址。
在遠端 (實體網路閘道) 建立 BGP 對等。 建立 BGP 對等互連時,請使用在上述步驟 2 中決定的 SDN 閘道內部位址 () 作為對等 IP 位址。
在實體網路上設定路由,其目的地為 SDN 閘道內部位址,下一個躍點為 L3 介面 IP 位址 (指令碼中的 LocalIPAddresses)。
判斷 SDN 閘道內部位址
請使用下列程序:
在已安裝網路控制卡的電腦或已設為網路控制卡用戶端的電腦上,執行下列 PowerShell Cmdlet:
$gateway = Get-NetworkControllerVirtualGateway -ConnectionUri <REST uri of your deployment>
$gateway.Properties.NetworkConnections.Properties.IPAddresses
此命令的結果可以根據有多少租用戶已設定網關聯機,顯示多個虛擬閘道。 每個虛擬閘道都可以有多個連線 (IPSec、GRE、L3)。
由於您已經知道連線的 L3 介面 IP 位址 (LocalIPAddresses),因此可以依據該 IP 位址找出正確的連線。 完成正確的網路連線之後,請在對應的虛擬閘道上執行下列命令 () ,以取得虛擬網關的 BGP 路由器 IP 位址。
$gateway.Properties.BgpRouters.Properties.RouterIp
此命令的結果會提供您必須在遠端路由器設為對等 IP 位址的 IP 位址。
從 VMM PowerShell 設定流量選取器
使用下列程序:
注意
使用的值僅為範例。
使用下列參數建立流量選取器。
$t= new-object Microsoft.VirtualManager.Remoting.TrafficSelector $t.Type=7 // IPV4=7, IPV6=8 $t.ProtocolId=6 // TCP =6, reference: https://en.wikipedia.org/wiki/List_of_IP_protocol_numbers $t.PortEnd=5090 $t.PortStart=5080 $t.IpAddressStart=10.100.101.10 $t.IpAddressEnd=10.100.101.100使用 Add-SCVPNConnection 或 Set-SCVPNConnection 的 -LocalTrafficSelectors 參數設定上述流量選取器。
意見反應
即將登場:在 2024 年,我們將逐步淘汰 GitHub 問題作為內容的意見反應機制,並將它取代為新的意見反應系統。 如需詳細資訊,請參閱:https://aka.ms/ContentUserFeedback。
提交並檢視相關的意見反應