附錄 C︰Active Directory 中受保護的帳戶和群組
適用於:Windows Server 2022、Windows Server 2019、Windows Server 2016、Windows Server 2012 R2、Windows Server 2012
附錄 C︰Active Directory 中受保護的帳戶和群組
在 Active Directory 中,預設的一組高特許權限帳戶和群組會被視為受保護的帳戶和群組。 對於 Active Directory 中的大多數物件,委派管理 Active Directory 物件的權限的使用者可以變更對物件享有的權限,包括變更權限以允許自己修改特殊群組的成員身分。
受保護的帳戶和群組是特殊物件,其透過自動流程設定和強制執行權限,以確保對物件的權限保持一致。 即使將物件移至 Active Directory 中的不同位置,這些權限仍維持不變。 如果修改了受保護物件的權限,現有處理序可確保將權限快速恢復為預設值。
受保護的群組
下列安全性帳戶和群組會在 Active Directory 網域服務中受到保護:
- Account Operators
- 系統管理員
- 系統管理員
- Backup Operators
- 網域管理員
- 網域控制站
- 企業管理員
- Krbtgt
- Print Operators
- Read-only Domain Controllers
- 複製者
- 架構管理員
- 服務操作員
AdminSDHolder
AdminSDHolder 物件的用途是提供網域中受保護帳戶和群組的「範本」權限。 AdminSDHolder 會自動建立為每個 Active Directory 網域之系統容器中的物件。 其路徑為:CN=AdminSDHolder,CN=System、DC=<domain_component>、DC=<domain_component>?。
雖然 Administrators 群組擁有 Active Directory 網域中的大多數物件,但 Domain Admins 群組擁有 AdminSDHolder 物件。 預設情況下,企業管理員可以對任何網域的 AdminSDHolder 物件進行變更,網域的網域管理員和管理員群組也可以進行變更。 此外,雖然 AdminSDHolder 的預設擁有者是網域的 Domain Admins 群組,但 Administrators 或 Enterprise Admins 的成員可以取得物件的所有權。
SDProp
SDProp 是在保留網域 PDC 模擬器 (PDCE) 的網域控制站上每隔 60 分鐘執行一次程式。 SDProp 會將網域 AdminSDHolder 物件的權限與網域中受保護帳戶和群組的權限進行比較。 如果任何受保護帳戶和群組的權限與 AdminSDHolder 物件上的權限不相符,SDProp 會重設受保護帳戶和群組的權限,以和為網域的 AdminSDHolder 物件設定的權限相符。
受保護的群組和帳戶上會停用權限繼承功能。 即使將帳戶和群組移到目錄中的不同位置,帳戶和群組也不會從其新的父物件繼承權限。 AdminSDHolder 物件上已停用繼承,因此父物件的權限變更不會變更 AdminSDHolder 的權限。
變更 SDProp 間隔
一般而言,除了測試目的,您不應該變更 SDProp 執行間隔。 如果您需要變更 SDProp 間隔,請在網域的 PDCE 上使用 regedit,在 HKLM\SYSTEM\CurrentControlSet\Services\NTDS\Parameters 中新增或修改 AdminSDProtectFrequency DWORD 值。
值的範圍是從 60 到 7200 的秒數 (一分鐘到兩小時)。 若要移除變更,請刪除管理員 AdminSDProtectFrequency 金鑰。 刪除金鑰會導致 SDProp 還原回 60 分鐘間隔。 您通常不應該在生產網域中減少此間隔,因為它會增加網域控制站上的 LSASS 處理額外負荷。 此增加的影響取決於網域中的受保護物件數目。
手動執行 SDProp
測試 AdminSDHolder 變更的較佳方法是手動執行 SDProp,這會導致工作立即執行,但不會影響排程的執行。 您可以使用 Ldp.exe 或執行 LDAP 修改腳本,強制 SDProp 執行。 若要手動執行 SDProp,請執行下列步驟:
啟動 Ldp.exe。
在 [Ldp] 對話方塊中,按一下 [連線],然後按一下 [連線]。
在 [連線] 對話方塊中,輸入保存 PDC 模擬器 (PDCE) 角色之網域的網域控制站名稱,然後按一下 [確定]。

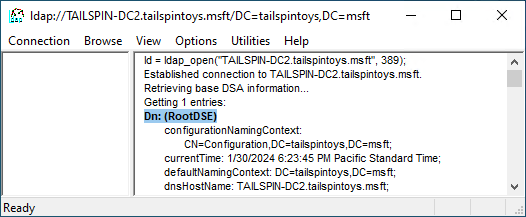
若要確認連線,請檢查 Dn: (RootDSE) 是否存在類似下列螢幕擷取畫面。 接著按一下 [連線],然後按一下 [繫結]。
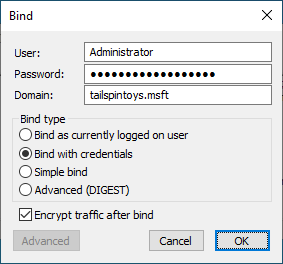
在 [繫結] 對話方塊中,輸入有權修改 rootDSE 物件的使用者帳號憑證。 (如果您是以該使用者身分登入,您可以選取繫結為目前登入的使用者。)按一下 [確定] 。
繫結作業完成後,按一下 [瀏覽],然後按一下 [修改]。
在 [修改] 對話方塊中,將 [DN] 欄位保留空白。 在 [編輯專案屬性] 欄位中,輸入 RunProtectAdminGroupsTask,然後在 [值] 欄位中輸入 1。 按一下 Enter 以填入專案清單,如下所示。

在填入的修改對話方塊中,按一下 [執行],並確認您對 AdminSDHolder 物件所做的變更已出現在該物件上。