附錄 D:保護 Active Directory 中內建的 Administrator 帳戶
適用於:Windows Server 2022、Windows Server 2019、Windows Server 2016、Windows Server 2012 R2、Windows Server 2012
附錄 D:保護 Active Directory 中內建的 Administrator 帳戶
在 Active Directory 的每個網域中,會在建立網域時建立 Administrator 帳戶。 預設情況下,此帳戶是網域中 Domain Admins 和 Administrators 群組的成員。 如果網域是樹系根網域,帳戶也是 Enterprise Admins 群組的成員。
網域 Administrator 帳戶的使用應該只保留給初始建置活動,也可能是災害復原案例。 若要確保可以在未使用任何其他帳戶的情況下使用 Administrator 帳戶來進行修復,您不應該變更樹系內任何網域中 Administrator 帳戶的預設成員資格。 相反地,您應該如下節所述以及如後續逐步指示中詳述來保護樹系內每個網域中的 Administrator 帳戶。
注意
本指南用來建議停用帳戶。 這已予以移除,因為樹系復原白皮書會利用預設 Administrator 帳戶。 原因是,這是唯一允許在沒有通用類別目錄伺服器的情況下登入的帳戶。
內建 Administrator 帳戶的控制項
針對樹系內每個網域中內建的 Administrator 帳戶,您應該設定下列設定:
啟用帳戶上的 [這是機密帳戶,無法委派] 旗標。
啟用帳戶上的 [互動式登入必須使用智慧卡] 旗標。
設定 GPO,以限制在已加入網域的系統上使用 Administrator 帳戶:
在每個網域中建立並連結至工作站和成員伺服器 OU 的一或多個 GPO 中,將每個網域的 Administrator 帳戶新增至 [電腦設定\原則\Windows 設定\安全性設定\本機原則\使用者權限指派] 中的下列使用者權限:
拒絕從網路存取這台電腦
拒絕以批次工作登入
拒絕以服務方式登入
拒絕透過遠端桌面服務登入
注意
當您將帳戶新增至此設定時,必須指定您要設定本機 Administrator 帳戶還是網域 Administrator 帳戶。 例如,若要將 TAILSPINTOYS 網域的 Administrator 帳戶新增到這些拒絕權利中,則必須將該帳戶輸入為 TAILSPINTOYS\Administrator,或瀏覽到 TAILSPINTOYS 網域的 Administrator 帳戶。 如果您在群組原則物件編輯器內的這些使用者權限設定中輸入 "Administrator",則將會限制每部套用 GPO 之電腦上的本機 Administrator 帳戶。
建議使用與網域型 Administrator 帳戶相同的方式,來限制成員伺服器和工作站上的本機 Administrator 帳戶。 因此,您一般應該會將樹系內每個網域的 Administrator 帳戶以及本機電腦的 Administrator 帳戶新增至這些使用者權限設定。 下列螢幕擷取畫面所顯示的範例是有關設定這些使用者權限以封鎖本機 Administrator 帳戶和網域 Administrator 帳戶執行這些帳戶不應該需要的登入。
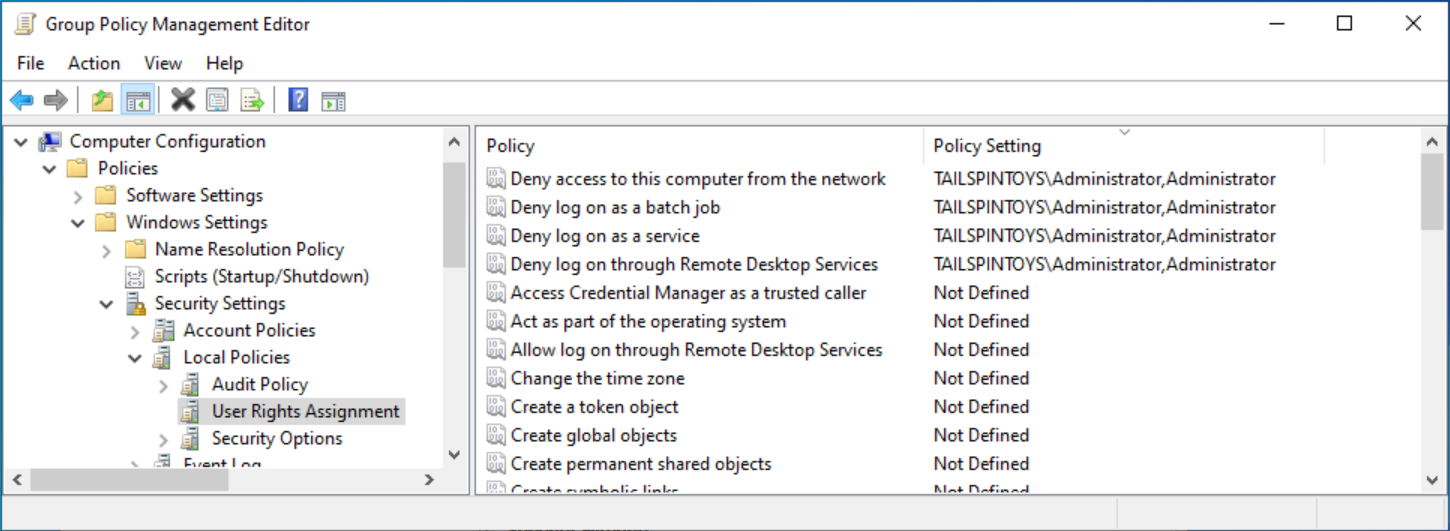
- 設定 GPO 以限制網域控制站上的 Administrator 帳戶
在樹系的每個網域中,應修改預設網域控制器 GPO 或連結到網域控制器 OU 的原則,以將每個網域的 Administrator 帳戶新增到 Computer Configuration\Policies\Windows Settings\Security Settings\Local Policies\User Rights Assignments 中的以下使用者權限:
拒絕從網路存取這台電腦
拒絕以批次工作登入
拒絕以服務方式登入
拒絕透過遠端桌面服務登入
注意
這些設定將確保無法使用網域內建的 Administrator 帳戶來連線至網域控制站,不過此帳戶可以在本機登入至網域控制站。 因為此帳戶只應該用於災害復原案例,所以預期至少可以使用一個網域控制站的實體存取,或者可以使用具有遠端存取網域控制站權限的其他帳戶。
設定 Administrator 帳戶的稽核
當每個網域的 Administrator 帳戶安全時,您應設定稽核以監視帳戶的使用方式或變更。 如果帳戶已登入、重設其密碼,或對帳戶進行任何其他修改,則除了組織中的事件回應小組之外,應該還會將警示傳送給負責 Active Directory 系統管理的使用者或小組。
保護 Active Directory 中內建 Administrator 帳戶的逐步指示
在 [伺服器管理員] 中,選取 [工具],然後選取 [Active Directory 使用者和電腦]。
若要防止利用委派在其他系統上使用帳戶憑證的攻擊,請執行下列步驟:
以滑鼠右鍵按選 Administrator 帳戶,然後選擇 [屬性]。
選取 [帳戶] 索引標籤。
在 [帳戶選項] 」下下,選取 [帳戶是敏感性帳戶,無法委派] 旗標,如以下螢幕擷取畫面所示,然後選取 [確定]。
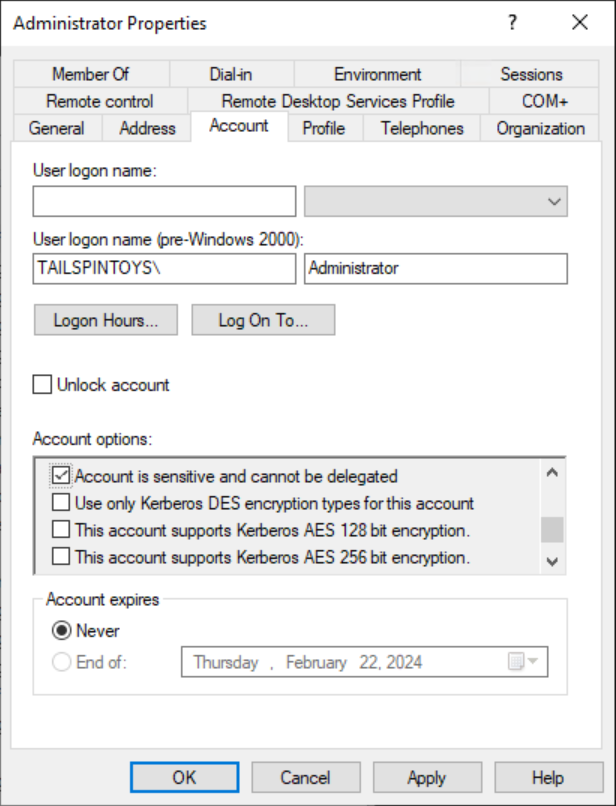
若要啟用帳戶上的 [互動式登入必須使用智慧卡] 旗標,請執行下列步驟:
以滑鼠右鍵按選 Administrator 帳戶,然後選擇 [屬性]。
選取 [帳戶] 索引標籤。
在 [帳戶] 選項下選取 [互動式登入必須使用智慧卡] 旗標,如以下螢幕擷取畫面所示,然後選取 [確定]。
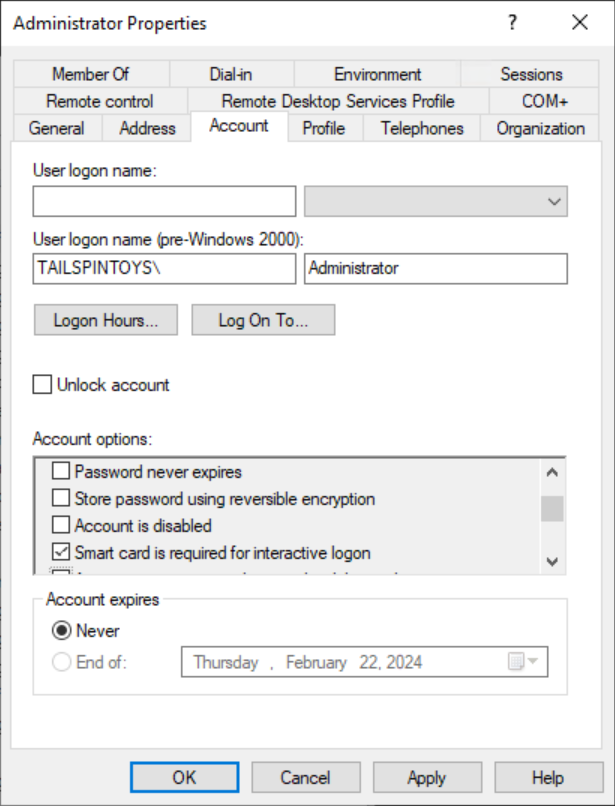
設定 GPO 以限制網域層級的 Administrator 帳戶
警告
此 GPO 絕不應該在網域層級進行連結,因為它會讓內建的 Administrator 帳戶無法使用,即使在災害復原案例中也是如此。
在 [伺服器管理員] 中,選取 [工具],然後選取 [群組原則管理]。
在主控台樹狀目錄中,展開 [<Forest>\網域\<Domain>],然後展開 [群組原則物件] (其中 <Forest> 是樹系的名稱,而 <Domain> 是您想要在其中建立群組原則的網域名稱)。
在主控台樹系中,以右鍵按一下 [群組原則物件],然後選取 [ 新建]。
在 [新 GPO] ] 對話方塊中,輸入 [<GPO 名稱>],然後選取[確定] (其中 [<GPO 名稱>] 是此 GPO 的名稱)。
在詳細資訊窗格中,以右鍵按一下 [<GPO 名稱>],然後選取 [編輯]。
瀏覽至 Computer Configuration\Policies\Windows Settings\Security Settings\Local Policies,然後選取 [使用者權限指派]。
透過執行以下步驟,設定使用者權限以防止 Administrator 帳戶透過網路存取成員伺服器和工作站:
按選拒絕從網路存取這台電腦] 兩次並選取 [定義這些原則設定]。
選取 [新增使用者或群組],然後選取 [瀏覽]。
輸入 管理員,選取 [檢查名稱],然後選取 [確定]。 確認以 <DomainName>\Username 格式顯示帳戶,如下列螢幕擷取畫面所指出。
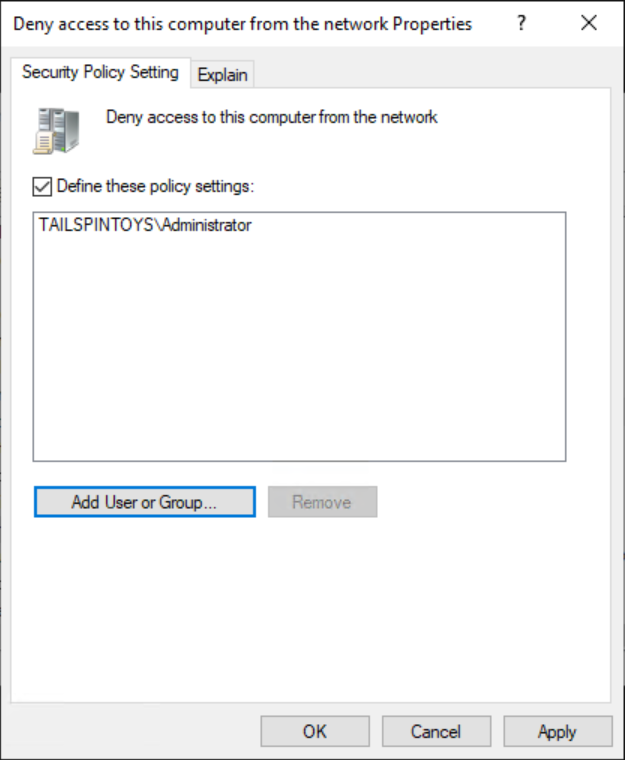
選取 [確定],然後再次選取 [確定]。
透過執行以下步驟,設定使用者權限以防止 Administrator 帳戶以分批處理作業方式登入:
按兩下 [拒絕以批次工作登入],然後選取 [定義這些原則設定]。
選取 [新增使用者或群組],然後選取 [瀏覽]。
輸入 管理員,選取 [檢查名稱],然後選取 [確定]。 確認以 <DomainName>\Username 格式顯示帳戶,如下列螢幕擷取畫面所指出。
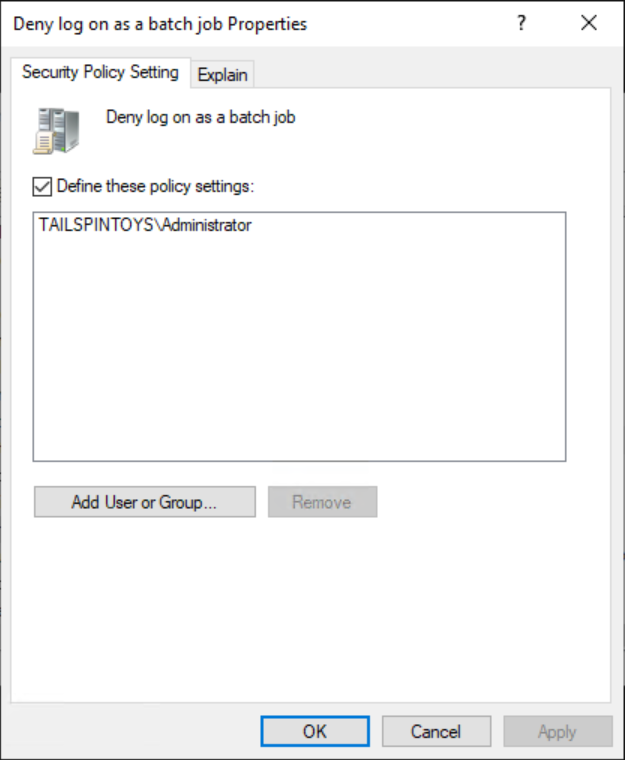
選取 [確定],然後再次選取 [確定]。
透過執行以下步驟,設定使用者權限以防止 Administrator 帳戶以服務方式登入:
按兩下 [拒絕以服務方式登入],然後選取 [定義這些原則設定]。
選取 [新增使用者或群組],然後選取 [瀏覽]。
輸入 管理員,選取 [檢查名稱],然後選取 [確定]。 確認以 <DomainName>\Username 格式顯示帳戶,如下列螢幕擷取畫面所指出。
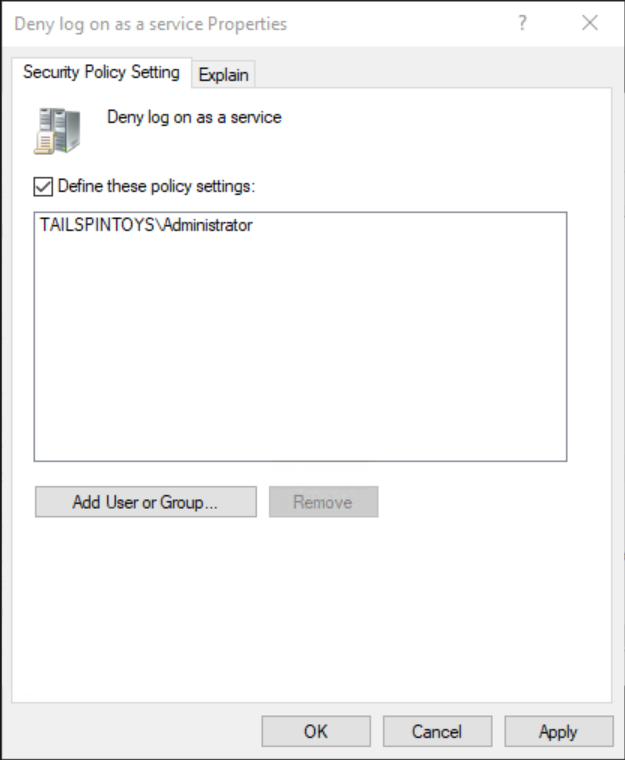
選取 [確定],然後再次選取 [確定]。
透過執行以下步驟,設定使用者權限以防止 Administrator 帳戶透過遠端桌面服務存取成員伺服器和工作站:
按兩下 [拒絕透過遠端桌面服務登入],然後選取 [定義這些原則設定]。
選取 [新增使用者或群組],然後選取 [瀏覽]。
輸入 管理員,選取 [檢查名稱],然後選取 [確定]。 確認以 <DomainName>\Username 格式顯示帳戶,如下列螢幕擷取畫面所指出。
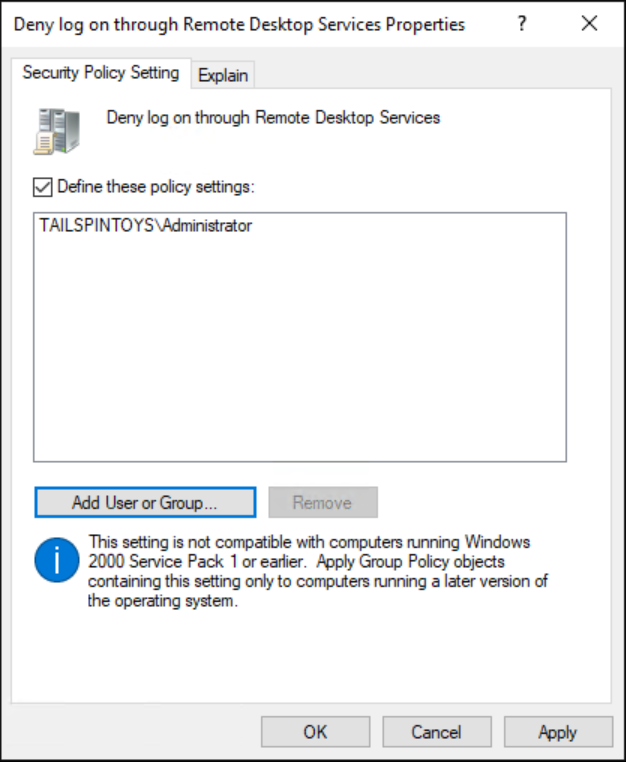
選取 [確定],然後再次選取 [確定]。
若要退出 [群組原則管理編輯器] ,請選取 [檔案],然後選取 [結束]。
在 [群組原則管理]中,執行以下步驟以將 GPO 連結到成員伺服器和工作站 OU:
導覽至 [<Forest>\網域\<Domain>] (其中 <Forest> 是樹系的名稱,而 <Domain> 是您想要在其中設定群組原則的網域名稱)。
以右鍵按一下要套用 GPO 的 OU,然後選取 [連結現有 GPO]。
選取您建立的 GPO,並選取 [確定]。
針對包含工作站的其他所有 OU 建立連結。
針對包含成員伺服器的其他所有 OU 建立連結。
重要
當您將 Administrator 帳戶新增至這些設定時,可以指定您要如何標記本機 Administrator 帳戶或網域 Administrator 帳戶來設定帳戶。 例如,若要將 TAILSPINTOYS 網域的 Administrator 帳戶新增至這些拒絕權限,您將會瀏覽至 TAILSPINTOYS 網域的 Administrator 帳戶,而這會顯示為 TAILSPINTOYS\Administrator。 如果您在群組原則物件編輯器內的這些使用者權限設定中輸入 "Administrator",則將會限制每部套用 GPO 之電腦上的本機 Administrator 帳戶,如先前所述。
驗證步驟
此處所概述的驗證步驟專屬於 Windows 8 和 Windows Server 2012。
驗證 [互動式登入必須使用智慧卡] 帳戶選項
- 從 GPO 變更所影響的任何成員伺服器或工作站中,嘗試使用網域內建的 Administrator 帳戶以互動方式登入至網域。 嘗試登入之後,會出現對話方塊,通知您需要智慧卡才能登入。
驗證 [拒絕從網路存取這台電腦] GPO 設定
嘗試從不受 GPO 變更影響的成員伺服器或工作站,透過網路存取受 GPO 變更影響的成員伺服器或工作站。 若要驗證 GPO 設定,請使用 NET USE 命令來嘗試對應系統磁碟機:
使用網域內建的 Administrator 帳戶登入至網域。
以右鍵按選 [開始] 提示和選擇 [Windows PowerShell (管理員)]。
系統提示核准提高權限時,選取 [是]。
在 PowerShell 視窗中,輸入 net use \\<Server Name>\c$,其中 <Server Name> 是指嘗試透過網路存取的成員伺服器或工作站的名稱。
您應該會收到訊息,其中指出使用者尚未獲得要求的登入類型。
確認「拒絕以批次工作登入」GPO 設定
透過受 GPO 變更影響的任何成員伺服器或工作站,在本機登入。
建立批次檔
選取 [開始],提示並輸入 [記事本]。
在結果清單中,選取 [記事本]。
在[記事本]中,輸入[dir c:]。
選取 [檔案],並選取 [另存新檔]。
在 [檔案名稱] 欄位中,輸入 <Filename>.bat (其中 <Filename> 是新批次檔的名稱)。
排程工作
選取 [ 開始] 提示,輸入工作排程器,然後選取 [工作排程器]。
在 [工作排程器] 上選取 [動作],然後選取 [建立工作] 。
在[建立工作]對話方塊中,輸入工作名稱<> (其中<工作名稱>是新工作的名稱)。
選取 [動作] 索引標籤,並選取 [新增]。
在 [動作:] 下方,選取 [啟動程式]。
在 [程式/指令碼] 下,選取 [瀏覽],找到並選取 [建立批次檔] 區段中建立批次檔,然後選取 [開啟]。
選取 [確定]。
選取一般索引標籤。
在 [安全性] 選項」下,選取 [變更使用者或群組]。
在網域層級輸入 Administrator 帳戶的名稱,選取 [檢查名稱],然後選取 [確定]。
選取 [不論使用者是否登入皆執行] 和 [不要儲存密碼]。 此工作只能存取本機電腦資源。
選取 [確定]。
應該會出現對話方塊,要求取得使用者帳戶認證來執行工作。
輸入認證後,請選取 [確定]。
您會看到一個對話方塊,通知您工作需要具有以批次作業權限登入的帳戶。
確認「拒絕以服務方式登入」GPO 設定
透過受 GPO 變更影響的任何成員伺服器或工作站,在本機登入。
選取 [開始] 提示,輸入服務,然後選取 [服務]。
找到並按兩下 [列印多工緩衝處理器]。
選取 [登入] 索引標籤。
在 [登入身分:] 下方,選取 [此帳戶]。
選取 [瀏覽],在網域層級輸入 Administrator 帳戶的名稱,選取 [檢查名稱],然後選取 [確定]。
在 [密碼:] 和 [確認密碼] 下,輸入 Administrator 帳戶的密碼,然後選擇 [確定]。
選取 [確定] 三次。
以右鍵按選 [列印多工緩衝處理器服務] ,並選取 [重新啟動]。
重新啟動服務時,對話方塊會通知您無法啟動 [列印多工緩衝處理器服務]。
將變更還原為「列印多工緩衝處理器服務」
透過受 GPO 變更影響的任何成員伺服器或工作站,在本機登入。
選取 [開始] 提示,輸入服務,然後選取 [服務]。
找到並按兩下 [列印多工緩衝處理器]。
選取 [登入] 索引標籤。
在 [登入為] ,選取 [本機系統],然後選取 [確定]。
確認「拒絕透過遠端桌面服務登入」GPO 設定
選取 [開始],然後輸入遠端桌面連線,然後選取 [遠端桌面連線]。
在 [電腦] 欄位中,輸入要連接的電腦名稱,然後選取 [連線]。 (您也可以輸入 IP 位址,而不輸入電腦名稱。)
出現提示時,請提供網域層級之 Administrator 帳戶名稱的認證。
遠端桌面連線遭到拒絕。