為其他組織的使用者提供您的宣告感知應用程式與服務的存取權
如果您是 Active Directory 同盟服務 (AD FS) 中資源夥伴組織中的系統管理員,而且您的部署目標是將另一個組織 (帳戶夥伴組織) 中使用者的同盟存取權,提供給您的組織 (資源夥伴組織) 中的宣告感知應用程式或 Web 型服務:
您的組織,和已設定同盟信任您組織 (帳戶夥伴組織) 的組織中的同盟使用者,都可以存取您組織所裝載的 AD FS 保護應用程式或服務。 如需詳細資訊,請參閱 Federated Web SSO Design。
例如,Fabrikam 可能想要其公司網路員工對於裝載於 Contoso 的 Web 服務具有同盟存取權。
當與受信任的組織 (例如個別客戶) 沒有直接關聯的同盟使用者登入您周邊網路上裝載的屬性存放區,則也可以存取您的周邊網路所裝載的多個 AD FS 保護應用程式,而且只要從網際網路的用戶端電腦中登入一次即可。 換句話說,當您裝載客戶帳戶以存取周邊網路中的應用程式或服務時,您在屬性存放區中裝載的客戶只要登入一次,就可以存取周邊網路中的一或多個應用程式或服務。 如需詳細資訊,請參閱 Web SSO Design。
例如,Fabrikam 可能會想讓客戶利用單一登入 (SSO),存取其周邊網路中裝載的多個應用程式或服務。
此部署目標需要下列元件:
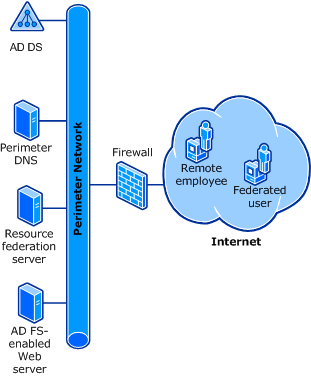
Active Directory 網域服務 (AD DS): 資源夥伴同盟伺服器必須加入 Active Directory 網域。
周邊網路 DNS: 網域名稱系統 (DNS) 應該包含簡單的主機 (A) 資源記錄,讓用戶端電腦可以找到資源夥伴同盟伺服器和 Web 伺服器。 DNS 伺服器可以裝載周邊網路也需要的其他 DNS 記錄。 如需詳細資訊,請參閱 Name Resolution Requirements for Federation Servers。
資源夥伴同盟伺服器: 資源夥伴同盟伺服器會驗證帳戶夥伴所傳送的 AD FS 權杖。 帳戶夥伴探索是透過此同盟伺服器執行。 如需詳細資訊,請參閱 Review the Role of the Federation Server in the Resource Partner。
Web 伺服器:Web 伺服器可以裝載 Web 應用程式或 Web 服務。 Web 伺服器會先確認它從同盟使用者接收有效的 AD FS 權杖,才允許存取受保護的 Web 應用程式或 Web 服務。
藉由使用 Windows Identity Foundation (WIF),您可以開發 Web 應用程式或服務,讓它接受使用任何標準登入方法 (例如使用者名稱和密碼) 所提出的同盟使用者登入要求。
檢閱連結主題中的資訊之後,您可以遵循 Checklist: Implementing a Federated Web SSO Design 及 Checklist: Implementing a Web SSO Design 中的步驟,開始部署此目標。
下圖顯示這個 AD FS 部署目標的每個必要元件。