搭配使用 AD DS 宣告與 AD FS
您可以使用 Active Directory Domain Services (AD DS) 發行的使用者和裝置宣告搭配 Active Directory 同盟服務 (AD FS),為同盟應用程式啟用更豐富的存取控制。
關於動態存取控制
在 Windows Server® 2012 中,動態存取控制功能可讓組織根據使用者宣告 (來源為使用者帳戶屬性) 和裝置宣告 (來源為電腦帳戶屬性) 授與檔案的存取權,而這些宣告是由 Active Directory Domain Services (AD DS) 所發出。 AD DS 發出的宣告會透過 Kerberos 驗證通訊協定整合到 Windows 整合式驗證中。
如需「動態存取控制」的詳細資訊,請參閱動態存取控制內容藍圖。
AD CS 的最新動向
作為動態存取控制案例的延伸模組,Windows Server 2012 中的 AD FS 現在可以:
除了 AD DS 內的使用者帳戶屬性之外,還可存取電腦帳戶屬性。 在舊版 AD FS 中,同盟服務完全無法從 AD DS 存取電腦帳戶屬性。
取用位於 Kerberos 驗證票證中 AD DS 發出的使用者或裝置宣告。 在舊版 AD FS 中,宣告引擎能夠從 Kerberos 讀取使用者和群組安全性識別碼 (SID),但無法讀取 Kerberos 票證內含的任何宣告資訊。
將 AD DS 發出的使用者或裝置宣告轉換成 SAML 權杖,以便信賴應用程式用來執行更豐富的存取控制。
使用 AD DS 宣告搭配 AD FS 的好處
這些 AD DS 發出的宣告可插入 Kerberos 驗證票證中,並搭配 AD FS 使用以提供下列優點:
需要更豐富存取控制原則的組織可以使用 AD DS 發出的宣告來啟用應用程式和資源的宣告式存取,而 AD DS 發出的宣告是以 AD DS 中針對指定使用者或電腦帳戶儲存的屬性值為基礎。 這可協助系統管理員減輕與建立和管理下列項目相關聯的額外負荷:
AD DS 安全性群組,用於控制可透過 Windows 整合式驗證存取之應用程式和資源的存取。
樹系信任,用來控制企業對企業 (B2B) / 網際網路可存取應用程式和資源的存取。
組織現在可以根據儲存在 AD DS 中的特定電腦帳戶屬性值 (例如電腦的 DNS 名稱) 是否符合資源的存取控制原則 (例如,已使用宣告進行 ACLd 的檔案伺服器) 或信賴憑證者原則 (例如宣告感知 Web 應用程),防止從用戶端電腦未經授權存取網路資源。 這可協助系統管理員針對下列資源或應用程式設定更精細的存取控制原則:
只能透過 Windows 整合式驗證存取。
可透過 AD FS 驗證機制存取網際網路。 AD FS 可用於將 AD DS 發出的裝置宣告轉換成 AD FS 宣告,這些宣告可以封裝成 SAML 權杖,而 SAML 權杖可由網際網路可存取的資源或信賴憑證者應用程式取用。
AD DS 與 AD FS 發出的宣告之間的差異
有兩個差異化因素對於瞭解從 AD DS 與 AD FS 發出的宣告而言很重要。 這些差異包括:
AD DS 只能發出封裝在 Kerberos 票證中的宣告,而不是 SAML 權杖。 如需 AD DS 如何發出宣告的詳細資訊,請參閱動態存取控制內容藍圖。
AD FS 只能發出封裝在 SAML 權杖中的宣告,而不是 Kerberos 票證。 如需 AD FS 如何發出宣告的詳細資訊,請參閱宣告引擎的角色。
已發出的 AD DS 宣告如何與 AD FS 搭配
AD DS 發出的宣告可以搭配 AD FS 使用,直接從使用者的驗證內容存取使用者和裝置宣告,而不是對 Active Directory 進行個別 LDAP 呼叫。 下圖和對應的步驟會討論此程序如何更詳細地運作,以針對動態存取控制案例啟用宣告式存取控制。
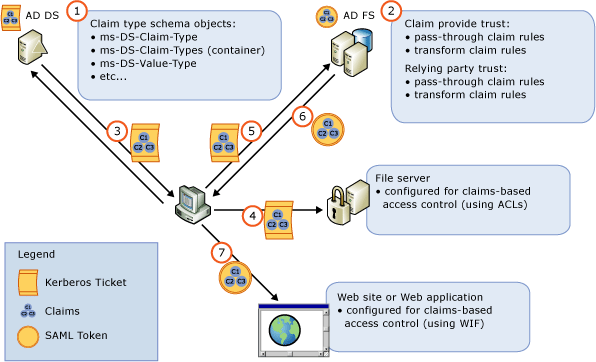
AD DS 系統管理員會使用 Active Directory 管理中心主控台或 PowerShell Cmdlet,在 AD DS 結構描述中啟用特定的宣告類型物件。
AD FS 系統管理員會使用 AD FS 管理主控台,建立及設定具有傳遞或轉換宣告規則的宣告提供者和信賴憑證者信任。
Windows 用戶端會嘗試存取網路。 在 Kerberos 驗證程序中,用戶端會向網域控制站出示尚未包含任何宣告的使用者和電腦票證授權票證 (TGT)。 然後網域控制站會在 AD DS 中尋找已啟用的宣告類型,並在傳回的 Kerberos 票證中包含任何產生的宣告。
當使用者/用戶端嘗試存取已進行 ACLd 來要求宣告的檔案資源時,他們可以存取此資源,因為從 Kerberos 呈現的複合識別碼具有這些宣告。
當相同的用戶端嘗試存取針對 AD FS 驗證設定的網站或 Web 應用程式時,使用者會重新導向至針對 Windows 整合式驗證設定的 AD FS 同盟伺服器。 用戶端會使用 Kerberos 將要求傳送至網域控制站。 網域控制站會發出 Kerberos 票證,其中包含用戶端可接著向同盟伺服器出示的要求宣告。
根據在系統管理員先前設定的宣告提供者和信賴憑證者信任上設定宣告規則的方式,AD FS 會從 Kerberos 票證讀取宣告並將其包含在針對用戶端發行的 SAML 權杖中。
用戶端會收到包含正確宣告的 SAML 權杖,然後重新導向至網站。
如需如何針對 AD DS 發出的宣告搭配 AD FS 運作建立所需的宣告規則詳細資訊,請參閱建立規則以轉換傳入宣告。