Windows Server 2012 R2 和 Windows Server 2012 AD FS 中的存取控制原則
本文所述的原則會使用兩種宣告
根據 AD FS 和 Web 應用程式 Proxy 可以檢查和驗證的資訊 (例如直接連線到 AD FS 或 WAP 的用戶端 IP 位址) 建立宣告 AD FS。
根據用戶端轉送至 AD FS 的資訊建立宣告 AD FS 做為 HTTP 標頭
重要事項:以下所記載的原則會封鎖需要存取下列其他端點的 Windows 10 網域加入和登入案例
Windows 10 網域加入和登入所需的 AD FS 端點
- [同盟服務名稱]/adfs/services/trust/2005/windowstransport
- [同盟服務名稱]/adfs/services/trust/13/windowstransport
- [同盟服務名稱]/adfs/services/trust/2005/usernamemixed
- [同盟服務名稱]/adfs/services/trust/13/usernamemixed
- [同盟服務名稱]/adfs/services/trust/2005/certificatemixed
- [同盟服務名稱]/adfs/services/trust/13/certificatemixed
重要事項:/adfs/services/trust/2005/windowstransport 和 /adfs/services/trust/13/windowstransport 端點應該只啟用內部網路存取,因為它們是要做為在 HTTPS 上使用 WIA 繫結的內部網路面向端點。 將其公開至外部網路可能會允許對這些端點的要求略過鎖定保護。 這些端點應該在 Proxy 上停用 (也就是從外部網路停用),以保護 AD 帳戶鎖定。
若要解決,請更新會根據端點宣告拒絕的任何原則,以允許上述端點的例外狀況。
例如,下列規則:
c1:[Type == "http://custom/ipoutsiderange", Value == "true"] && c2:[Type == "https://schemas.microsoft.com/2012/01/requestcontext/claims/x-ms-endpoint-absolute-path", Value != "/adfs/ls/"] => issue(Type = "https://schemas.microsoft.com/authorization/claims/deny", Value = " DenyUsersWithClaim");
會更新為:
c1:[Type == "http://custom/ipoutsiderange", Value == "true"] && c2:[Type == "https://schemas.microsoft.com/2012/01/requestcontext/claims/x-ms-endpoint-absolute-path", Value != "(/adfs/ls/)|(/adfs/services/trust/2005/windowstransport)|(/adfs/services/trust/13/windowstransport)|(/adfs/services/trust/2005/usernamemixed)|(/adfs/services/trust/13/usernamemixed)|(/adfs/services/trust/2005/certificatemixed)|(/adfs/services/trust/13/certificatemixed)"] => issue(Type = "https://schemas.microsoft.com/authorization/claims/deny", Value = " DenyUsersWithClaim");
注意
此類別的宣告只應該用來實作商務原則,而不是作為安全性原則來保護對您網路的存取。 未經授權的用戶端可以傳送具有虛假資訊的標頭,做為取得存取權的方式。
本文所述的原則應該一律與其他驗證方法搭配使用,例如使用者名稱和密碼或多重要素驗證。
用戶端存取原則案例
| 案例 | 說明 |
|---|---|
| 案例 1:封鎖對 Office 365 的所有外部存取 | 允許從內部公司網路上的所有用戶端存取 Office 365,但來自外部用戶端的要求會根據外部用戶端的 IP 位址拒絕。 |
| 案例 2:封鎖對 Office 365 的所有外部存取,Exchange ActiveSync 除外 | 允許從內部公司網路上的所有用戶端,以及使用 Exchange ActiveSync 的任何外部用戶端裝置 (例如智慧型手機) 存取 Office 365。 會封鎖所有其他外部用戶端,例如使用 Outlook 的外部用戶端。 |
| 案例 3:封鎖對 Office 365 的所有外部存取,瀏覽器型應用程式除外 | 封鎖對 Office 365 的外部存取,除了被動式 (瀏覽器型) 應用程式,例如 Outlook Web Access 或 SharePoint Online。 |
| 案例 4:封鎖對 Office 365 的所有外部存取,但指定的 Active Directory 群組除外 | 此案例用於測試和驗證用戶端存取原則部署。 它只會針對一或多個 Active Directory 群組的成員封鎖對 Office 365 的外部存取。 它也可以用來僅提供群組成員的外部存取。 |
啟用用戶端存取原則
若要在 Windows Server 2012 R2 的 AD FS 中啟用用戶端存取原則,您必須更新 Microsoft Office 365 身分識別平台信賴憑證者信任。 選擇下列其中一個範例案例,在最符合組織需求的 Microsoft Office 365 身分識別平台信賴憑證者信任上設定宣告規則。
案例 1:封鎖對 Office 365 的所有外部存取
此用戶端存取原則案例會允許從所有內部用戶端存取,並根據外部用戶端的 IP 位址封鎖所有外部用戶端。 您可以使用下列程序,將正確的發佈授權規則新增至所選案例的 Office 365 信賴憑證者信任。
建立規則以封鎖對 Office 365 的所有外部存取
從 [伺服器管理員],按一下 [工具],然後按一下 [AD FS 管理]。
在主控台樹狀目錄的 [AD FS\信任關係] 底下,按一下 [信賴憑證者信任],以滑鼠右鍵按一下 [Microsoft Office 365 身分識別平台] 信任,然後按一下 [編輯宣告規則]。
在 [編輯宣告規則] 對話方塊中,選取 [發佈授權規則] 索引標籤,然後按一下 [新增規則] 以啟動宣告規則精靈。
在 [選取規則範本] 頁面上的 [宣告規則範本] 底下,選取 [傳送使用自訂規則的宣告],然後按 [下一步]。
在 [設定規則] 頁面上的 [宣告規則名稱] 底下,輸入此規則的顯示名稱,例如「如果有任何 IP 宣告超出所需範圍,則拒絕」。 在 [自訂規則] 底下,輸入或貼上下列宣告規則語言語法 (以有效的 IP 運算式取代上述 “x-ms-forwarded-client-ip” 的值):
c1:[Type == "https://schemas.microsoft.com/ws/2012/01/insidecorporatenetwork", Value == "false"] && c2:[Type == "https://schemas.microsoft.com/2012/01/requestcontext/claims/x-ms-forwarded-client-ip", Value =~ "^(?!192\.168\.1\.77|10\.83\.118\.23)"] => issue(Type = "https://schemas.microsoft.com/authorization/claims/deny", Value = " DenyUsersWithClaim");按一下完成。 驗證新規則出現在 [發佈授權規則] 清單的預設 [允許所有使用者存取] 規則之前 (即使它出現在清單中較早的位置,拒絕規則仍會優先)。 如果沒有預設的允許存取規則,可以使用宣告規則語言在清單尾端新增一個,如下所示:
c:[] => issue(Type = "https://schemas.microsoft.com/authorization/claims/permit", Value = "true");若要儲存新規則,請在 [編輯宣告規則] 對話方塊中,按一下 [確定]。 產生的清單看起來應該如下所示。
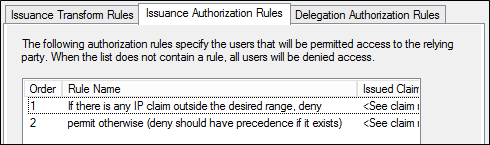
案例 2:封鎖對 Office 365 的所有外部存取,Exchange ActiveSync 除外
下列範例會允許從內部用戶端 (包括 Outlook ) 存取所有 Office 365 應用程式 (包括 Exchange Online)。 它會封鎖來自位於公司網路外部用戶端的存取,如用戶端 IP 位址所指出,但 Exchange ActiveSync 用戶端 (例如智慧型手機) 除外。
建立規則來封鎖對 Office 365 的所有外部存取,Exchange ActiveSync 除外
從 [伺服器管理員],按一下 [工具],然後按一下 [AD FS 管理]。
在主控台樹狀目錄的 [AD FS\信任關係] 底下,按一下 [信賴憑證者信任],以滑鼠右鍵按一下 [Microsoft Office 365 身分識別平台] 信任,然後按一下 [編輯宣告規則]。
在 [編輯宣告規則] 對話方塊中,選取 [發佈授權規則] 索引標籤,然後按一下 [新增規則] 以啟動宣告規則精靈。
在 [選取規則範本] 頁面上的 [宣告規則範本] 底下,選取 [傳送使用自訂規則的宣告],然後按 [下一步]。
在 [設定規則] 頁面上的 [宣告規則名稱] 底下,輸入此規則的顯示名稱,例如「如果有任何 IP 宣告超出所需範圍,則發出 ipoutsiderange 宣告」。 在 [自訂規則] 底下,輸入或貼上下列宣告規則語言語法 (以有效的 IP 運算式取代上述 “x-ms-forwarded-client-ip” 的值):
c1:[Type == "https://schemas.microsoft.com/ws/2012/01/insidecorporatenetwork", Value == "false"] && c2:[Type == "https://schemas.microsoft.com/2012/01/requestcontext/claims/x-ms-forwarded-client-ip", Value =~ "^(?!192\.168\.1\.77|10\.83\.118\.23)"] => issue(Type = "http://custom/ipoutsiderange", Value = "true");按一下完成。 驗證新規則出現在 [發佈授權規則] 清單中。
下一步,在 [編輯宣告規則] 對話方塊的 [發佈授權規則] 索引標籤上,按一下 [新增規則] 再次啟動宣告規則精靈。
在 [選取規則範本] 頁面上的 [宣告規則範本] 底下,選取 [傳送使用自訂規則的宣告],然後按 [下一步]。
在 [設定規則] 頁面上的 [宣告規則名稱] 底下,輸入此規則的顯示名稱,例如「如果 IP 超出所需的範圍,且有非 EAS x-ms-client-application 宣告,則拒絕」。 在 [自訂規則] 底下,輸入或貼上下列宣告規則語言語法:
c1:[Type == "http://custom/ipoutsiderange", Value == "true"] && c2:[Type == "https://schemas.microsoft.com/2012/01/requestcontext/claims/x-ms-client-application", Value != "Microsoft.Exchange.ActiveSync"] => issue(Type = "https://schemas.microsoft.com/authorization/claims/deny", Value = "DenyUsersWithClaim");按一下完成。 驗證新規則出現在 [發佈授權規則] 清單中。
下一步,在 [編輯宣告規則] 對話方塊的 [發佈授權規則] 索引標籤上,按一下 [新增規則] 再次啟動宣告規則精靈。
在 [選取規則範本] 頁面上的 [宣告規則範本] 底下,從清單中選取 [傳送使用自訂規則的宣告],然後按 [下一步]。
在 [設定規則] 頁面上的 [宣告規則名稱] 底下,輸入此規則的顯示名稱,例如「檢查應用程式宣告是否存在」。 在 [自訂規則] 底下,輸入或貼上下列宣告規則語言語法:
NOT EXISTS([Type == "https://schemas.microsoft.com/2012/01/requestcontext/claims/x-ms-client-application"]) => add(Type = "http://custom/xmsapplication", Value = "fail");按一下完成。 驗證新規則出現在 [發佈授權規則] 清單中。
下一步,在 [編輯宣告規則] 對話方塊的 [發佈授權規則] 索引標籤上,按一下 [新增規則] 再次啟動宣告規則精靈。
在 [選取規則範本] 頁面上的 [宣告規則範本] 底下,從清單中選取 [傳送使用自訂規則的宣告],然後按 [下一步]。
在 [設定規則] 頁面上的 [宣告規則名稱] 底下,輸入此規則的顯示名稱,例如「拒絕 ipoutsiderange 為 true 且應用程式失敗的使用者」。 在 [自訂規則] 底下,輸入或貼上下列宣告規則語言語法:
c1:[Type == "http://custom/ipoutsiderange", Value == "true"] && c2:[Type == "http://custom/xmsapplication", Value == "fail"] => issue(Type = "https://schemas.microsoft.com/authorization/claims/deny", Value = "DenyUsersWithClaim");按一下完成。 驗證新規則出現在緊接著上一個規則下方並在 [發佈授權規則] 清單中的預設 [允許所有使用者存取] 規則之前 (即使它出現在清單中較早的位置,拒絕規則仍會優先)。
如果沒有預設的允許存取規則,可以使用宣告規則語言在清單尾端新增一個,如下所示:
c:[] => issue(Type = "https://schemas.microsoft.com/authorization/claims/permit", Value = "true");若要儲存新規則,請在 [編輯宣告規則] 對話方塊中,按一下 [確定]。 產生的清單看起來應該如下所示。
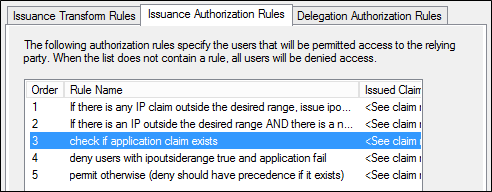
案例 3:封鎖對 Office 365 的所有外部存取,瀏覽器型應用程式除外
建立規則以封鎖對 Office 365 的所有外部存取,瀏覽器型應用程式除外
從 [伺服器管理員],按一下 [工具],然後按一下 [AD FS 管理]。
在主控台樹狀目錄的 [AD FS\信任關係] 底下,按一下 [信賴憑證者信任],以滑鼠右鍵按一下 [Microsoft Office 365 身分識別平台] 信任,然後按一下 [編輯宣告規則]。
在 [編輯宣告規則] 對話方塊中,選取 [發佈授權規則] 索引標籤,然後按一下 [新增規則] 以啟動宣告規則精靈。
在 [選取規則範本] 頁面上的 [宣告規則範本] 底下,選取 [傳送使用自訂規則的宣告],然後按 [下一步]。
在 [設定規則] 頁面上的 [宣告規則名稱] 底下,輸入此規則的顯示名稱,例如「如果有任何 IP 宣告超出所需範圍,則發出 ipoutsiderange 宣告」。 在 [自訂規則] 底下,輸入或貼上下列宣告規則語言語法 (以有效的 IP 運算式取代上述 “x-ms-forwarded-client-ip” 的值):
c1:[Type == "https://schemas.microsoft.com/ws/2012/01/insidecorporatenetwork", Value == "false"] && c2:[Type == "https://schemas.microsoft.com/2012/01/requestcontext/claims/x-ms-forwarded-client-ip", Value =~ "^(?!192\.168\.1\.77|10\.83\.118\.23)"] => issue(Type = "http://custom/ipoutsiderange", Value = "true");
按一下完成。 驗證新規則出現在 [發佈授權規則] 清單中。
下一步,在 [編輯宣告規則] 對話方塊的 [發佈授權規則] 索引標籤上,按一下 [新增規則] 再次啟動宣告規則精靈。
在 [選取規則範本] 頁面上的 [宣告規則範本] 底下,從清單中選取 [傳送使用自訂規則的宣告],然後按 [下一步]。
在 [設定規則] 頁面上的 [宣告規則名稱] 底下,輸入此規則的顯示名稱,例如「如果有任何 IP 超出所需範圍且端點不是 /adfs/ls,則拒絕」。 在 [自訂規則] 底下,輸入或貼上下列宣告規則語言語法:
c1:[Type == "http://custom/ipoutsiderange", Value == "true"] && c2:[Type == "https://schemas.microsoft.com/2012/01/requestcontext/claims/x-ms-endpoint-absolute-path", Value != "/adfs/ls/"] => issue(Type = "https://schemas.microsoft.com/authorization/claims/deny", Value = " DenyUsersWithClaim");`按一下完成。 驗證新規則出現在 [發佈授權規則] 清單的預設 [允許所有使用者存取] 規則之前 (即使它出現在清單中較早的位置,拒絕規則仍會優先)。 如果沒有預設的允許存取規則,可以使用宣告規則語言在清單尾端新增一個,如下所示:
c:[] => issue(Type = "https://schemas.microsoft.com/authorization/claims/permit", Value = "true");
若要儲存新規則,請在 [編輯宣告規則] 對話方塊中,按一下 [確定]。 產生的清單看起來應該如下所示。
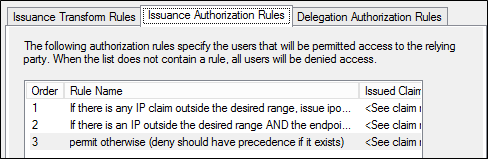
案例 4:封鎖對 Office 365 的所有外部存取,但指定的 Active Directory 群組除外
下列範例會根據 IP 位址,從內部用戶端啟用存取。 它會封鎖從位於具有外部用戶端 IP 位址的公司網路外部的用戶端存取,但指定 Active Directory 群組中的個人除外。使用下列步驟,使用下列步驟,使用宣告規則精靈將正確的發佈授權規則新增至 Microsoft Office 365 身分識別平台信賴憑證者信任:
建立規則以封鎖對 Office 365 的所有外部存取,但指定的 Active Directory 群組除外
從 [伺服器管理員],按一下 [工具],然後按一下 [AD FS 管理]。
在主控台樹狀目錄的 [AD FS\信任關係] 底下,按一下 [信賴憑證者信任],以滑鼠右鍵按一下 [Microsoft Office 365 身分識別平台] 信任,然後按一下 [編輯宣告規則]。
在 [編輯宣告規則] 對話方塊中,選取 [發佈授權規則] 索引標籤,然後按一下 [新增規則] 以啟動宣告規則精靈。
在 [選取規則範本] 頁面上的 [宣告規則範本] 底下,選取 [傳送使用自訂規則的宣告],然後按 [下一步]。
在 [設定規則] 頁面上的 [宣告規則名稱] 底下,輸入此規則的顯示名稱,例如「如果有任何 IP 宣告超出所需範圍,則發出 ipoutsiderange 宣告」。 在 [自訂規則] 底下,輸入或貼上下列宣告規則語言語法 (以有效的 IP 運算式取代上述 “x-ms-forwarded-client-ip” 的值):
`c1:[Type == "https://schemas.microsoft.com/2012/01/requestcontext/claims/x-ms-forwarded-client-ip", Value =~ "^(?!192\.168\.1\.77|10\.83\.118\.23)"] && c2:[Type == "https://schemas.microsoft.com/ws/2012/01/insidecorporatenetwork", Value == "false"] => issue(Type = "http://custom/ipoutsiderange", Value = "true");`按一下完成。 驗證新規則出現在 [發佈授權規則] 清單中。
下一步,在 [編輯宣告規則] 對話方塊的 [發佈授權規則] 索引標籤上,按一下 [新增規則] 再次啟動宣告規則精靈。
在 [選取規則範本] 頁面上的 [宣告規則範本] 底下,從清單中選取 [傳送使用自訂規則的宣告],然後按 [下一步]。
在 [設定規則] 頁面上的 [宣告規則名稱] 底下,輸入此規則的顯示名稱,例如「檢查群組 SID」。 在 [自訂規則] 底下,輸入或貼上下列宣告規則語言語法 (以您所使用的 AD 群組的實際 SID 取代 "groupsid"):
NOT EXISTS([Type == "https://schemas.microsoft.com/ws/2008/06/identity/claims/groupsid", Value == "S-1-5-32-100"]) => add(Type = "http://custom/groupsid", Value = "fail");按一下完成。 驗證新規則出現在 [發佈授權規則] 清單中。
下一步,在 [編輯宣告規則] 對話方塊的 [發佈授權規則] 索引標籤上,按一下 [新增規則] 再次啟動宣告規則精靈。
在 [選取規則範本] 頁面上的 [宣告規則範本] 底下,從清單中選取 [傳送使用自訂規則的宣告],然後按 [下一步]。
在 [設定規則] 頁面上的 [宣告規則名稱] 底下,輸入此規則的顯示名稱,例如「拒絕 ipoutsiderange 為 true 且 groupsid 失敗的使用者」。 在 [自訂規則] 底下,輸入或貼上下列宣告規則語言語法:
c1:[Type == "http://custom/ipoutsiderange", Value == "true"] && c2:[Type == "http://custom/groupsid", Value == "fail"] => issue(Type = "https://schemas.microsoft.com/authorization/claims/deny", Value = "DenyUsersWithClaim");
- 按一下完成。 驗證新規則出現在緊接著上一個規則下方並在 [發佈授權規則] 清單中的預設 [允許所有使用者存取] 規則之前 (即使它出現在清單中較早的位置,拒絕規則仍會優先)。 如果沒有預設的允許存取規則,可以使用宣告規則語言在清單尾端新增一個,如下所示:
c:[] => issue(Type = "https://schemas.microsoft.com/authorization/claims/permit", Value = "true");
若要儲存新規則,請在 [編輯宣告規則] 對話方塊中,按一下 [確定]。 產生的清單看起來應該如下所示。
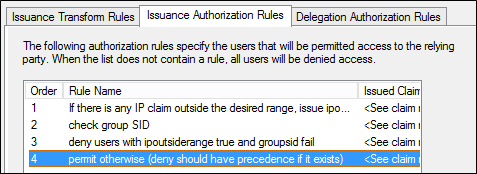
建立 IP 位址範圍運算式
x-ms-forwarded-client-ip 宣告會從目前僅由 Exchange Online 設定的 HTTP 標頭填入,這會在將驗證要求傳遞至 AD FS 時填入標頭。 宣告的值可能是下列其中一項:
注意
Exchange Online 目前僅支援 IPV4 而非 IPV6 位址。
- 單一 IP 位址:直接連線至 Exchange Online 的用戶端的 IP 位址
注意
- 公司網路上用戶端的 IP 位址會顯示為組織輸出 Proxy 或閘道的外部介面 IP 位址。
- 透過 VPN 或 Microsoft DirectAccess (DA) 連線到公司網路的用戶端,可能會根據 VPN 或 DA 的設定,顯示為內部公司用戶端或外部用戶端。
- 一或多個 IP 位址:當 Exchange Online 無法判斷連線用戶端的 IP 位址時,它會根據 x-forwarded-for 標頭的值來設定值,這是可包含在 HTTP 型要求中的非標準標頭,且受到市場上許多用戶端、負載平衡器和 Proxy 支援。
注意
- 多個 IP 位址,指出用戶端 IP 位址和傳遞要求的每個 Proxy 的位址將會以逗號分隔。
- 與 Exchange Online 基礎結構相關的 IP 位址將不會列在清單上。
[規則運算式]
當您必須比對某個範圍的 IP 位址時,必須建構規則運算式來執行比較。 在接下來的一系列步驟中,我們將提供如何建構這類運算式以比對下列位址範圍的範例 (請注意,您必須變更這些範例以比對您的公用 IP 範圍):
192.168.1.1 - 192.168.1.25
10.0.0.1 - 10.0.0.14
首先,比對單一 IP 位址的基本模式如下所示:\b###\.###\.###\.###\b
為此,我們可以使用 OR 運算式比對兩個不同的 IP 位址,如下所示:\b###\.#\.##\b|\b#\.##\.###\b
因此,只比對兩個位址 (例如 192.168.1.1 或 10.0.0.1) 的範例會是:\b192\.168\.1\.1\b|\b10\.0\.0\.1\b
這可提供您輸入任意數目位址的技術。 必須允許某個位址範圍時,例如 192.168.1.1 - 192.168.1.25,比對必須逐字元完成:\b192\.168\.1\.([1-9]|1[0-9]|2[0-5])\b
請注意以下事項:
將 IP 位址視為字串,而不是數字。
規則劃分如下:\b192\.168\.1\。
這會比對以 192.168.1 開頭的任何值。
以下會比對最後的小數點之後位址部分所需的範圍:
([1-9] 比對結尾為 1-9 的位址
|1[0-9] 比對結尾為 10-19 的位址
|2[0-5]) 比對結尾為 20-25 的位址
請注意,必須正確放置括弧,使得您不會開始比對 IP 位址的其他部分。
比對到 192 區塊之後,我們可以為 10 區塊撰寫類似的運算式:\b10\.0\.0\.([1-9]|1[0-4])\b
並將它們放在一起,下列運算式應該會比對 “192.168.1.1~25” 和 “10.0.0.1~14” 的所有位址:\b192\.168\.1\.([1-9]|1[0-9]|2[0-5])\b|\b10\.0\.0\.([1-9]|1[0-4])\b
測試運算式
Regex 運算式可能會變得相當棘手,因此強烈建議您使用 RegEx 驗證工具。 如果您在網際網路上搜尋 “online regex expression builder”,您會發現數個良好的線上公用程式,可讓您針對範例資料試用您的運算式。
測試運算式時,請務必了解預期要比對的項目。 Exchange Online 系統可能會傳送許多 IP 位址,並以逗號分隔。 上述提供的運算式將適用於此作業。 不過,在測試 RegEx 運算式時,請務必考慮這個問題。 例如,其中一個可能會使用下列範例輸入來驗證上述範例:
192.168.1.1、192.168.1.2、192.169.1.1。 192.168.12.1、192.168.1.10、192.168.1.25、192.168.1.26、192.168.1.30、1192.168.1.20
10.0.0.1、10.0.0.5、10.0.0.10、10.0.1.0、10.0.1.1、110.0.0.1、10.0.0.14、10.0.0.15、10.0.0.10、10,0.0.1
宣告類型
Windows Server 2012 R2 中的 AD FS 會使用下列宣告類型提供要求內容資訊:
X-MS-Forwarded-Client-IP
宣告類型:https://schemas.microsoft.com/2012/01/requestcontext/claims/x-ms-forwarded-client-ip
此 AD FS 宣告代表確定提出要求的使用者 IP 位址 (例如 Outlook 用戶端) 的「最佳嘗試」。 此宣告可以包含多個 IP 位址,包括轉送要求的每個 Proxy 的位址。 此宣告會從 HTTP 填入。 宣告的值可以是下列其中一項:
- 單一 IP 位址 - 直接連線至 Exchange Online 的用戶端的 IP 位址
注意
公司網路上用戶端的 IP 位址會顯示為組織輸出 Proxy 或閘道的外部介面 IP 位址。
一或多個 IP 位址
如果 Exchange Online 無法判斷連線用戶端的 IP 位址,它會根據 x-forwarded-for 標頭的值來設定值,這是可包含在 HTTP 型要求中的非標準標頭,且受到市場上許多用戶端、負載平衡器和 Proxy 支援。
多個 IP 位址,指出用戶端 IP 位址和傳遞要求的每個 Proxy 的位址將會以逗號分隔。
注意
與 Exchange Online 基礎結構相關的 IP 位址將不會出現在清單中。
警告
Exchange Online 目前僅支援 IPV4 位址;它不支援 IPV6 位址。
X-MS-Client-Application
宣告類型:https://schemas.microsoft.com/2012/01/requestcontext/claims/x-ms-client-application
此 AD FS 宣告代表終端用戶端所使用的通訊協定,其會與要使用的應用程式鬆散對應。 此宣告會從目前僅由 Exchange Online 設定的 HTTP 標頭填入,這會在將驗證要求傳遞至 AD FS 時填入標頭。 視應用程式而定,此宣告的值會是下列其中一項:
在使用 Exchange Active Sync 的裝置中,值為 Microsoft.Exchange.ActiveSync。
使用 Microsoft Outlook 用戶端可能會導致下列任何值:
Microsoft.Exchange.Autodiscover
Microsoft.Exchange.OfflineAddressBook
Microsoft.Exchange.RPCMicrosoft.Exchange.WebServices
Microsoft.Exchange.RPCMicrosoft.Exchange.WebServices
此標頭的其他可能值包括下列各項:
Microsoft.Exchange.Powershell
Microsoft.Exchange.SMTP
Microsoft.Exchange.Pop
Microsoft.Exchange.Imap
X-MS-Client-User-Agent
宣告類型:https://schemas.microsoft.com/2012/01/requestcontext/claims/x-ms-client-user-agent
此 AD FS 宣告提供字串來表示用戶端用來存取服務的裝置類型。 當客戶想要防止存取特定裝置時 (例如特定類型的智慧型手機),可以使用此選項。 此宣告的範例值包括 (但不限於) 下列值。
以下是 x-ms-user-agent 值對於 x-ms-client-application 為 “Microsoft.Exchange.ActiveSync” 的用戶端可能包含內容的範例
Vortex/1.0
Apple-iPad1C1/812.1
Apple-iPhone3C1/811.2
Apple-iPhone/704.11
Moto-DROID2/4.5.1
SAMSUNGSPHD700/100.202
Android/0.3
這個值也可能是空白。
X-MS-Proxy
宣告類型:https://schemas.microsoft.com/2012/01/requestcontext/claims/x-ms-proxy
此 AD FS 宣告指出要求已通過 Web 應用程式 Proxy。 此宣告會由 Web 應用程式 Proxy 填入,其會在將驗證要求傳遞至後端同盟服務時填入標頭。 AD FS 接著會將它轉換成宣告。
宣告的值是傳遞要求的 Web 應用程式 Proxy 的 DNS 名稱。
InsideCorporateNetwork
宣告類型:https://schemas.microsoft.com/ws/2012/01/insidecorporatenetwork
類似於上述 x-ms-proxy 宣告類型,此宣告類型會指出要求是否已通過 Web 應用程式 Proxy。 不同於 x-ms-proxy,insidecorporatenetwork 是布林值,其值為 True,指出從公司網路內直接向同盟服務提出要求。
X-MS-Endpoint-Absolute-Path (主動與被動)
宣告類型:https://schemas.microsoft.com/2012/01/requestcontext/claims/x-ms-endpoint-absolute-path
此宣告類型會用於判斷源自「主動」(豐富) 用戶端與「被動」(網頁瀏覽器型) 用戶端的要求。 這可允許來自瀏覽器型應用程式 (例如 Outlook Web Access、SharePoint Online 或 Office 365 入口網站) 的外部要求,同時封鎖來自 Microsoft Outlook 等豐富用戶端的要求。
宣告的值是接收要求的 AD FS 服務名稱。