使用驗證原則
在 Windows Server 2012 R2 中的 AD FS 中,存取控制具有多種因素,包括使用者、裝置、位置和驗證資料。 這些增強功能可讓您藉由使用者介面或藉由 Windows PowerShell,透過多重要素存取控制和多重要素驗證來管理將存取權限授予 AD FS 保護應用程式的的風險,這些控制和驗證是根據使用者身分識別或群組成員資格、網路位置、加入工作場所的裝置資料,以及執行多重要素驗證 (MFA) 時的驗證狀態。
如需 Windows Server 2012 R2 中 Active Directory 同盟服務 (AD FS) 中 MFA 和多重要素存取控制的詳細資訊,請參閱下列主題:
透過 AD FS 管理嵌入式管理單元建立驗證原則
本機電腦上的系統管理員或對等的成員資格是完成這些程序的最低需求。 請檢閱在本機和網域預設群組使用適當帳戶和群組成員資格的詳細資料。
在 AD FS 中,在 Windows Server 2012 R2 中,您可以在全域範圍內指定驗證原則,該原則適用於 AD FS 保護的所有應用程式和服務。 您也可以為依賴合作物件信任且受 AD FS 保護的特定應用程式和服務設定驗證原則。 為每個信賴憑證者信任指定特定應用程式的驗證原則不會覆寫全域驗證原則。 如果全域或每個信賴憑證者信任驗證原則都需要 MFA,當使用者嘗試向此信賴憑證者信任進行驗證時,就會觸發 MFA。 全域驗證原則是信賴憑證者信任的後援,適用於沒有特定設定驗證原則的應用程式和服務。
在 Windows Server 2012 R2 中全域設定主要驗證
在 [伺服器管理員] 中,按一下[工具],然後選取 [AD FS 管理]。
在 AD FS 嵌入式管理單元中,按一下[驗證原則]。
在[主要驗證]區段中,按一下[全域設定]旁的[編輯]。 您也能夠以滑鼠右鍵按一下[驗證原則],然後選取[編輯全域主要驗證],或在[動作]窗格下方選取[編輯全域主要驗證]。
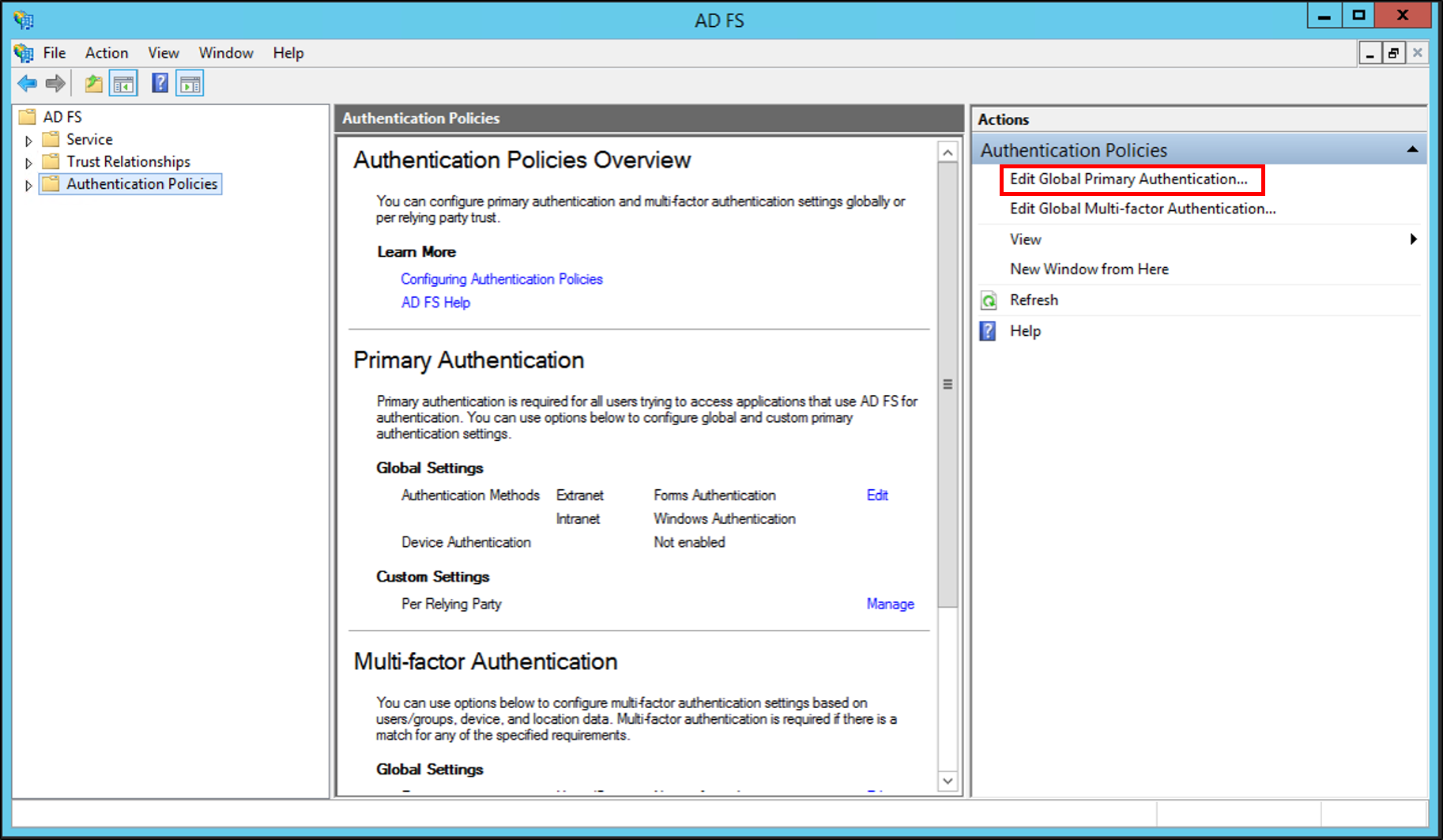
在[編輯全域驗證原則]視窗中,在[主要]索引標籤上,您可以設定下列設定,作為全域驗證原則的一部分:
要用於主要驗證的驗證方法。 您可以在[外部網路]和內部網路下方選取可用的驗證方法。
透過[啟用裝置驗證]核取方塊進行裝置驗證。 如需詳細資訊,請參閱 Join to Workplace from Any Device for SSO and Seamless Second Factor Authentication Across Company Applications。
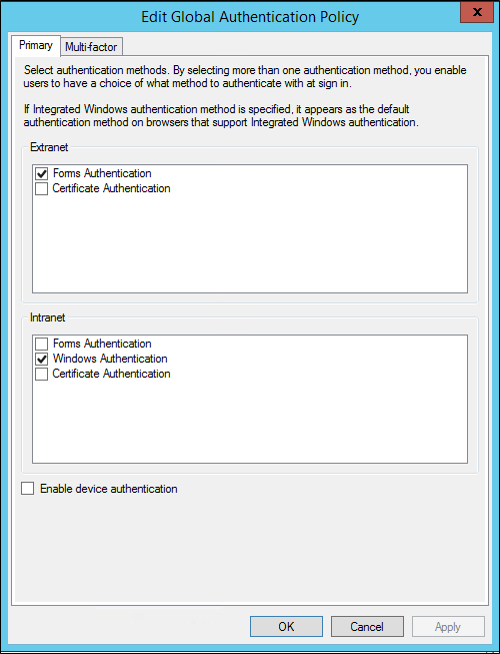
若要設定每個信賴憑證者信任的主要驗證
在 [伺服器管理員] 中,按一下[工具],然後選取 [AD FS 管理]。
在 AD FS 嵌入式管理單元中,按一下[驗證原則]\[依信賴憑證者信任],然後按一下您要設定驗證原則的信賴憑證者信任。
以滑鼠右鍵按一下您要設定驗證原則的信賴憑證者信任,然後選取[編輯自訂主要驗證],或在[動作]窗格下方選取[編輯自訂主要驗證]。
在[編輯驗證原則,適用於<relying_party_trust_name]>視窗中,在[主要]索引標籤底下,您可以設定下列設定,作為[每個信賴憑證者信任]驗證原則的一部分:
- 透過[使用者每次登入時需要提供其認證]核取方塊,指示使用者是否需要在每次登入時提供其認證。
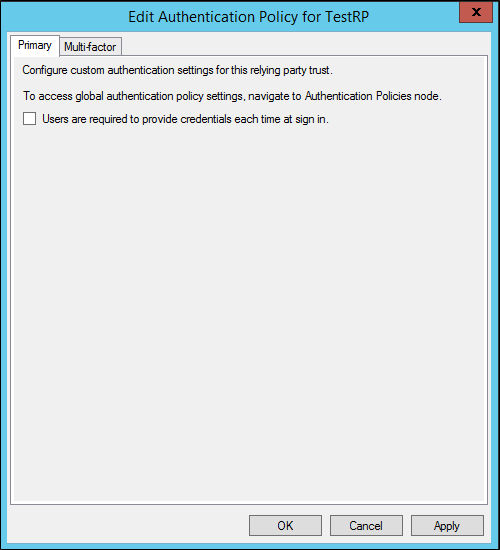
- 透過[使用者每次登入時需要提供其認證]核取方塊,指示使用者是否需要在每次登入時提供其認證。
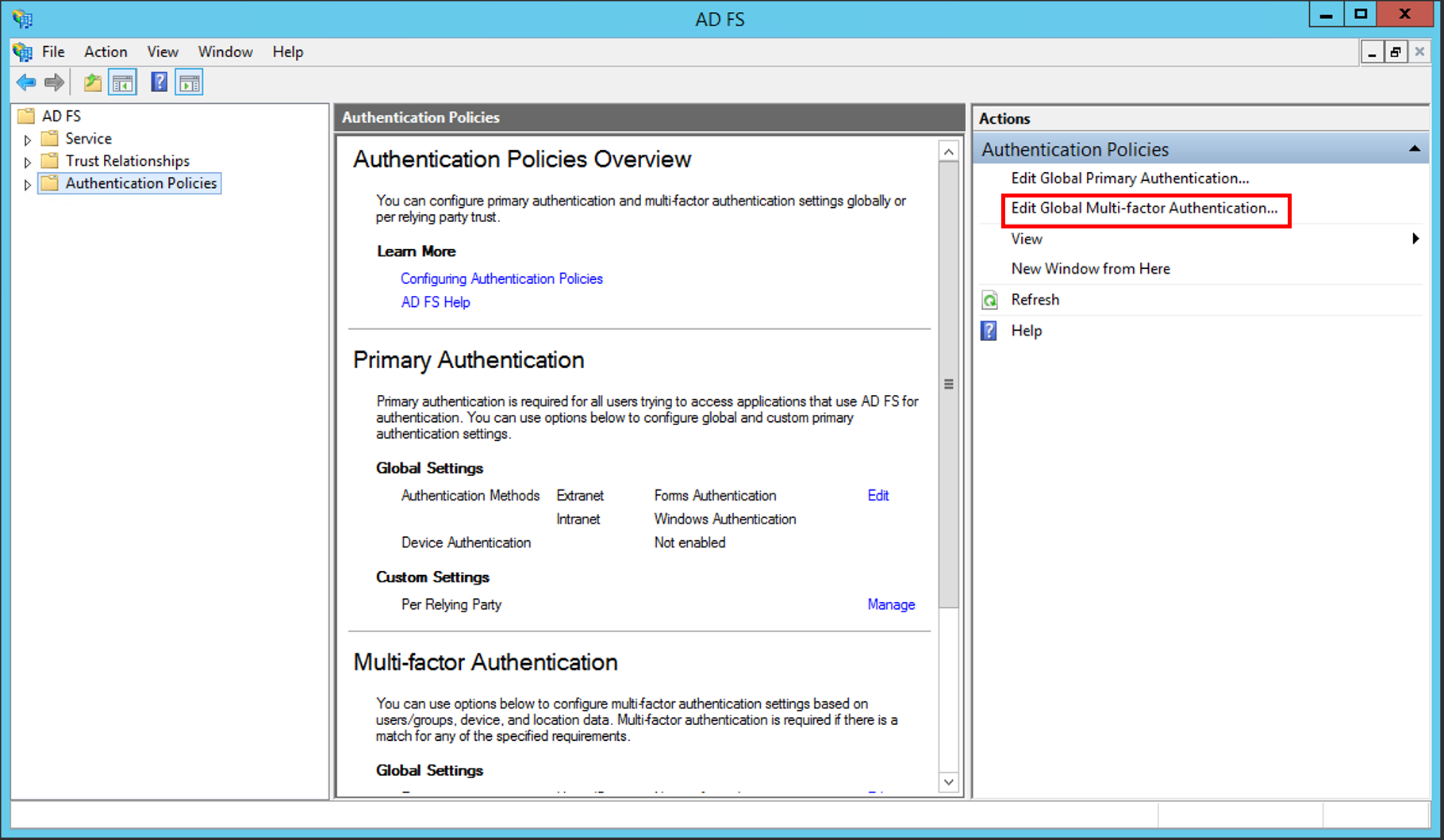
全域設定多重要素驗證
在 [伺服器管理員] 中,按一下[工具],然後選取 [AD FS 管理]。
在 AD FS 嵌入式管理單元中,按一下[驗證原則]。
在[多重要素驗證]區段中,按一下[全域設定]旁的[編輯]。 您也能夠以滑鼠右鍵按一下[驗證原則],然後選取[編輯全域多重要素驗證],或在[動作]窗格底下方選取[編輯全域多重要素驗證]。
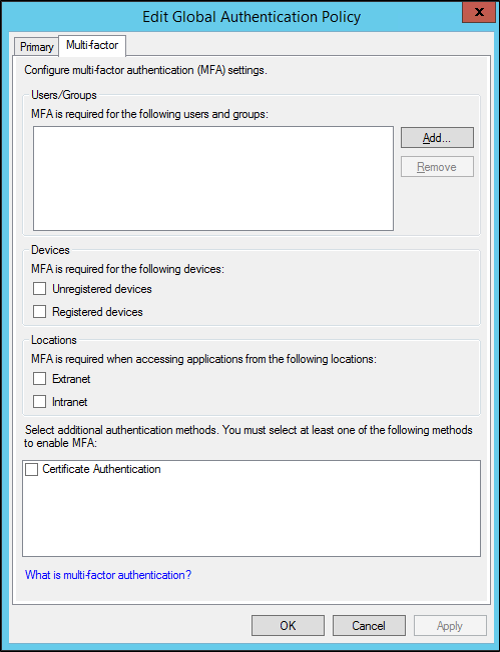
在[編輯全域驗證原則]視窗中,在[多重要素]索引標籤底下方,您可以設定下列設定,作為為全域多重要素驗證原則的一部分:
透過[使用者/群組]、[裝置]和[位置]區段下方的可用選項取得 MFA 的設定或條件。
若要針對任何這些設定啟用 MFA,您必須選取至少一個額外的驗證方法。 憑證驗證是預設可用的選項。 您也可以設定其他自訂的其他驗證方法,例如 Windows Azure Active Authentication。 如需詳細資訊,請參閱逐步解說指南:使用敏感性應用程式的其他多重要素驗證來管理風險。
警告
您只能全域設定其他驗證方法。
若要為每個信賴憑證者信任設定多重要素驗證
在 [伺服器管理員] 中,按一下[工具],然後選取 [AD FS 管理]。
在 AD FS 嵌入式管理單元中,按一下[驗證原則]\[依信賴憑證者信任],然後按一下您想要設定 MFA 的信賴憑證者信任。
以滑鼠右鍵按一下您要設定 MFA 的信賴憑證者信任,然後選取[編輯自訂多重要素驗證],或在[動作]窗格下方選取[編輯自訂多重要素驗證]。
在[編輯驗證原則,適用於 <relying_party_trust_name]>視窗中,在[多重要素]索引標籤下方,您可以設定下列設定,作為依信賴憑證者信任驗證原則的一部分:
- 透過[使用者/群組]、[裝置]和[位置]區段下方的可用選項取得 MFA 的設定或條件。
透過 Windows PowerShell 設定驗證原則
Windows PowerShell 可讓您使用各種存取控制因素和 Windows Server 2012 R2 AD FS 中提供的驗證機制,來設定驗證原則和授權規則,這些規則是針對 AD FS 保護的資源實作真正的條件式存取所需的。
本機電腦上的管理員或對等成員資格是完成這些程式的最低需求。 請檢閱在本機和網域預設群組使用適當帳戶和群組成員資格的詳細資料 (http://go.microsoft.com/fwlink/?LinkId=83477).
透過 Windows PowerShell 設定其他驗證方法
- 在您的同盟伺服器上,開啟 Windows PowerShell 命令視窗,然後執行下列命令。
`Set-AdfsGlobalAuthenticationPolicy –AdditionalAuthenticationProvider CertificateAuthentication `
警告
若要確認是否已順利執行此命令,可以執行 Get-AdfsGlobalAuthenticationPolicy 命令。
若要依信賴者信任 (依據使用者群組成員資格資料) 設定 MFA
- 在您的同盟伺服器上,開啟 Windows PowerShell 命令視窗,並執行下列命令:
`$rp = Get-AdfsRelyingPartyTrust –Name relying_party_trust`
警告
請務必將 <relying_party_trust> 取代為您的信賴憑證者信任的名稱。
- 在同一個 Windows PowerShell 命令視窗中,執行下列命令。
$MfaClaimRule = "c:[Type == '"https://schemas.microsoft.com/ws/2008/06/identity/claims/groupsid'", Value =~ '"^(?i) <group_SID>$'"] => issue(Type = '"https://schemas.microsoft.com/ws/2008/06/identity/claims/authenticationmethod'", Value '"https://schemas.microsoft.com/claims/multipleauthn'");"
Set-AdfsRelyingPartyTrust –TargetRelyingParty $rp –AdditionalAuthenticationRules $MfaClaimRule
注意
請務必將 <group_SID> 取代為您 Active Directory (AD) 群組的安全性識別碼 (SID) 值。
根據使用者的群組成員資格資料全域設定 MFA
- 在您的同盟伺服器上,開啟 Windows PowerShell 命令視窗,然後執行下列命令。
$MfaClaimRule = "c:[Type == '" https://schemas.microsoft.com/ws/2008/06/identity/claims/groupsid'", Value == '"group_SID'"]
=> issue(Type = '"https://schemas.microsoft.com/ws/2008/06/identity/claims/authenticationmethod'", Value = '"https://schemas.microsoft.com/claims/multipleauthn'");"
Set-AdfsAdditionalAuthenticationRule $MfaClaimRule
注意
請務必將 <group_SID> 取代為 AD 群組的 SID 值。
根據使用者的位置全域設定 MFA
- 在您的同盟伺服器上,開啟 Windows PowerShell 命令視窗,然後執行下列命令。
$MfaClaimRule = "c:[Type == '" https://schemas.microsoft.com/ws/2012/01/insidecorporatenetwork'", Value == '"true_or_false'"]
=> issue(Type = '"https://schemas.microsoft.com/ws/2008/06/identity/claims/authenticationmethod'", Value = '"https://schemas.microsoft.com/claims/multipleauthn'");"
Set-AdfsAdditionalAuthenticationRule $MfaClaimRule
注意
請務必將 <true_or_false> 取代為 true 或 false。 此值取決於您的特定規則條件,該條件是依據存取要求是否來自外部網路或內部網路而定。
根據使用者的裝置資料全域設定 MFA
- 在您的同盟伺服器上,開啟 Windows PowerShell 命令視窗,然後執行下列命令。
$MfaClaimRule = "c:[Type == '" https://schemas.microsoft.com/2012/01/devicecontext/claims/isregistereduser'", Value == '"true_or_false"']
=> issue(Type = '"https://schemas.microsoft.com/ws/2008/06/identity/claims/authenticationmethod'", Value = '"https://schemas.microsoft.com/claims/multipleauthn'");"
Set-AdfsAdditionalAuthenticationRule $MfaClaimRule
注意
請務必將 <true_or_false> 取代為 true 或 false。 此值取決於您的特定規則條件,該條件是根據裝置是否加入工作場所而定。
如果存取要求來自外部網路,以及來自未加入工作場所的裝置,請全域設定 MFA
- 在您的同盟伺服器上,開啟 Windows PowerShell 命令視窗,然後執行下列命令。
`Set-AdfsAdditionalAuthenticationRule "c:[Type == '"https://schemas.microsoft.com/2012/01/devicecontext/claims/isregistereduser'", Value == '"true_or_false'"] && c2:[Type == '"https://schemas.microsoft.com/ws/2012/01/insidecorporatenetwork'", Value == '" true_or_false '"] => issue(Type = '"https://schemas.microsoft.com/ws/2008/06/identity/claims/authenticationmethod'", Value ='"https://schemas.microsoft.com/claims/multipleauthn'");" `
注意
請確定將 <true_or_false> 的兩個實例取代為 true 或 false,這取決於您的特定規則條件。 規則條件是根據裝置是否加入工作場所,以及存取要求是否來自外部網路或內部網路而定。
存取來自屬於特定群組的外部網路使用者時,若要全域設定 MFA
- 在您的同盟伺服器上,開啟 Windows PowerShell 命令視窗,然後執行下列命令。
Set-AdfsAdditionalAuthenticationRule "c:[Type == `"https://schemas.microsoft.com/ws/2008/06/identity/claims/groupsid`", Value == `"group_SID`"] && c2:[Type == `"https://schemas.microsoft.com/ws/2012/01/insidecorporatenetwork`", Value== `"true_or_false`"] => issue(Type = `"https://schemas.microsoft.com/ws/2008/06/identity/claims/authenticationmethod`", Value =`"https://schemas.microsoft.com/claims/
注意
請確認將 <group_SID> 取代為群組 SID 的值,並將 <true_or_false> 取代為 true 或 false,這取決於您的特定規則條件,該條件是依據存取要求是否來自外部網路或內部網路而定。
若要透過 Windows PowerShell,依據使用者資料,授予對應用程式的存取權
在您的同盟伺服器上,開啟 Windows PowerShell 命令視窗,然後執行下列命令。
$rp = Get-AdfsRelyingPartyTrust –Name relying_party_trust
注意
請務必將 <relying_party_trust> 取代為信賴憑證者信任的值。
在同一個 Windows PowerShell 命令視窗中,執行下列命令。
$GroupAuthzRule = "@RuleTemplate = `"Authorization`" @RuleName = `"Foo`" c:[Type == `"https://schemas.microsoft.com/ws/2008/06/identity/claims/groupsid`", Value =~ `"^(?i)<group_SID>$`"] =>issue(Type = `"https://schemas.microsoft.com/authorization/claims/deny`", Value = `"DenyUsersWithClaim`");" Set-AdfsRelyingPartyTrust –TargetRelyingParty $rp –IssuanceAuthorizationRules $GroupAuthzRule
注意
請務必將 <group_SID> 取代為 AD 群組的 SID 值。
只有在使用 MFA 驗證此使用者的身分識別時,才授予對 AD FS 保護之應用程式的存取權
- 在您的同盟伺服器上,開啟 Windows PowerShell 命令視窗,然後執行下列命令。
`$rp = Get-AdfsRelyingPartyTrust –Name relying_party_trust `
注意
請務必將 <relying_party_trust> 取代為信賴憑證者信任的值。
在同一個 Windows PowerShell 命令視窗中,執行下列命令。
$GroupAuthzRule = "@RuleTemplate = `"Authorization`" @RuleName = `"PermitAccessWithMFA`" c:[Type == `"https://schemas.microsoft.com/claims/authnmethodsreferences`", Value =~ `"^(?i)https://schemas\.microsoft\.com/claims/multipleauthn$`"] => issue(Type = `"https://schemas.microsoft.com/authorization/claims/permit`", Value = '"PermitUsersWithClaim'");"
只有在存取要求來自已向使用者註冊的已加入工作場所的裝置時,才授予對 AD FS 保護之應用程式的存取權
在您的同盟伺服器上,開啟 Windows PowerShell 命令視窗,然後執行下列命令。
$rp = Get-AdfsRelyingPartyTrust –Name relying_party_trust
注意
請務必將 <relying_party_trust> 取代為信賴憑證者信任的值。
- 在同一個 Windows PowerShell 命令視窗中,執行下列命令。
$GroupAuthzRule = "@RuleTemplate = `"Authorization`"
@RuleName = `"PermitAccessFromRegisteredWorkplaceJoinedDevice`"
c:[Type == `"https://schemas.microsoft.com/2012/01/devicecontext/claims/isregistereduser`", Value =~ `"^(?i)true$`"] => issue(Type = `"https://schemas.microsoft.com/authorization/claims/permit`", Value = `"PermitUsersWithClaim`");
只有在存取要求來自已加入工作場所的裝置,且該裝置已向透過 MFA 驗證的使用者註冊時,才授予對 AD FS 所保護之應用程式的存取權
- 在您的同盟伺服器上,開啟 Windows PowerShell 命令視窗,然後執行下列命令。
`$rp = Get-AdfsRelyingPartyTrust –Name relying_party_trust `
注意
請務必將 <relying_party_trust> 取代為信賴憑證者信任的值。
在同一個 Windows PowerShell 命令視窗中,執行下列命令。
$GroupAuthzRule = '@RuleTemplate = "Authorization" @RuleName = "RequireMFAOnRegisteredWorkplaceJoinedDevice" c1:[Type == `"https://schemas.microsoft.com/claims/authnmethodsreferences`", Value =~ `"^(?i)http://schemas\.microsoft\.com/claims/multipleauthn$`"] && c2:[Type == `"https://schemas.microsoft.com/2012/01/devicecontext/claims/isregistereduser`", Value =~ `"^(?i)true$"] => issue(Type = "https://schemas.microsoft.com/authorization/claims/permit`", Value = `"PermitUsersWithClaim`");"
只有當存取要求來自已使用 MFA 驗證身分識別的使用者時,才能授予外部網路對 AD FS 所保護應用程式的存取權
- 在您的同盟伺服器上,開啟 Windows PowerShell 命令視窗,然後執行下列命令。
`$rp = Get-AdfsRelyingPartyTrust –Name relying_party_trust`
注意
請務必將 <relying_party_trust> 取代為信賴憑證者信任的值。
- 在同一個 Windows PowerShell 命令視窗中,執行下列命令。
$GroupAuthzRule = "@RuleTemplate = `"Authorization`"
@RuleName = `"RequireMFAForExtranetAccess`"
c1:[Type == `"https://schemas.microsoft.com/claims/authnmethodsreferences`", Value =~ `"^(?i)http://schemas\.microsoft\.com/claims/multipleauthn$`"] &&
c2:[Type == `"https://schemas.microsoft.com/ws/2012/01/insidecorporatenetwork`", Value =~ `"^(?i)false$`"] => issue(Type = `"https://schemas.microsoft.com/authorization/claims/permit`", Value = `"PermitUsersWithClaim`");"