使用已註冊的裝置設定內部部署條件式存取
下列文件將引導您使用已註冊的裝置安裝並設定內部部署條件式存取。
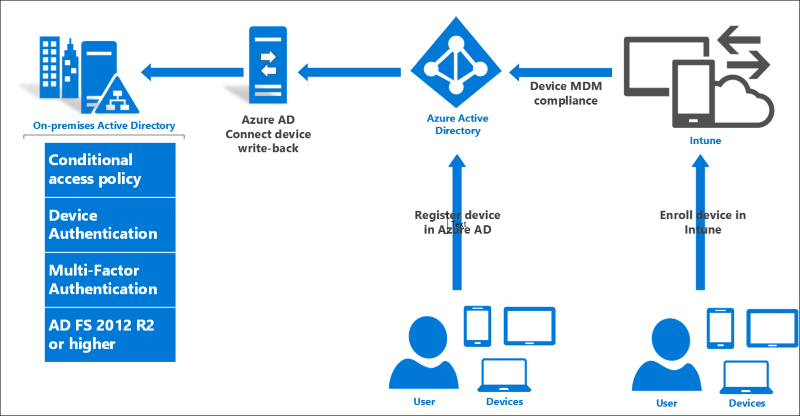
基礎結構必要條件
您必須先具備下列必要條件,才能開始使用內部部署條件式存取。
| 需求 | 描述 |
|---|---|
| 含有 Microsoft Entra ID P1 或 P2 的 Microsoft Entra 訂閱 | 若要啟用內部部署條件式存取的裝置回寫 - 歡迎免費試用 |
| Intune 訂用帳戶 | 僅對裝置合規性案例的 MDM 整合為必要 -歡迎免費試用 |
| Microsoft Entra Connect | 2015 年 11 月 QFE 或更新版本。 在此取得最新版本。 |
| Windows Server 2016 | AD FS 組建 10586 或更新版本 |
| Windows Server 2016 Active Directory 結構描述 | 需要結構描述層級 85 或更高版本。 |
| Windows Server 2016 網域控制站 | 只有 Hello 企業版金鑰信任部署才需要此條件。 如需詳細資訊,請參閱此處。 |
| Windows 10 用戶端 | 只有 Windows 10 網域加入和 Windows Hello 企業版案例,才需要使用組建 10586 或更新版本並加入上述網域 |
| 已指派 Microsoft Entra ID P1 或 P2 授權的 Microsoft Entra 使用者帳戶 | 針對註冊裝置 |
升級 Active Directory 結構描述
若要搭配已註冊的裝置使用內部部署條件式存取,您必須先升級 AD 結構描述。 必須符合下列條件:- 結構描述應該是 85 版或更新版本 - 只有 AD FS 加入的樹系才需要此條件
注意
如果您在升級到 Windows Server 2016 中的架構版本 (85 級或更高版本) 前安裝 Microsoft Entra Connect,您需要重新執行 Microsoft Entra Connect 安裝並重新整理內部部署 AD 架構,確保已配置 msDS-KeyCredentialLink 的同步規則。
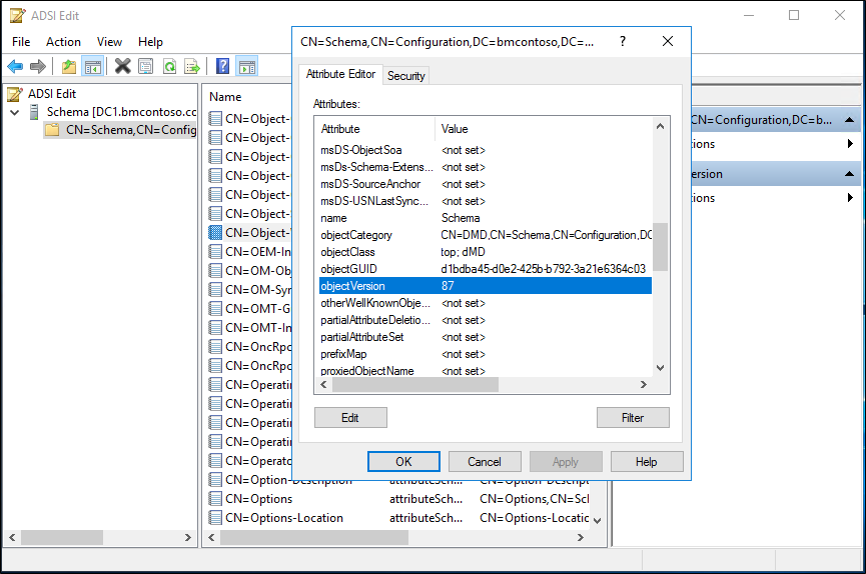
確認您的結構描述層級
若要確認結構描述層級,請執行下列動作:
- 您可以使用 ADSIEdit 或 LDP,並連線到結構描述命名內容。
- 使用 ADSIEdit,以滑鼠右鍵按一下 "CN=Schema,CN=Configuration,DC=<domain>,DC=<com> 並選取屬性。 以您的樹系資訊取代網域和 com 部分。
- 在 [屬性編輯器] 下找到 objectVersion 屬性,該屬性會告知您的版本。
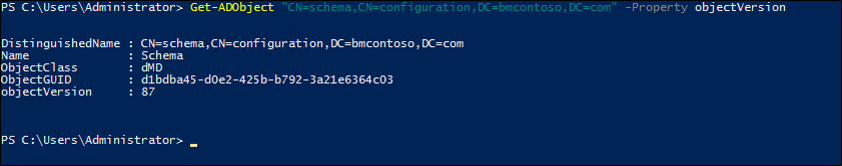
您也可以使用下列 PowerShell Cmdlet (將物件取代為您的結構描述命名內容資訊):
Get-ADObject "cn=schema,cn=configuration,dc=domain,dc=local" -Property objectVersion
如需關於升級的詳細資訊,請參閱將網域控制站升級為 Windows Server 2016。
啟用 Microsoft Entra 裝置註冊
若要配置此方案,您必須在 Microsoft Entra ID 配置裝置註冊功能。
為此,請按照設定 Microsoft Entra 加入貴公司下方的步驟
設定 AD FS
- 建立新的 AD FS 2016 伺服器陣列。
- 或者,從 AD FS 2012 R2 將伺服器陣列移轉至 AD FS 2016
- 使用自訂路徑將 AD FS 連接 Microsoft Entra ID,部署 Microsoft Entra Connect。
設定裝置回寫和裝置驗證
注意
如果您使用快速設定執行 Microsoft Entra Connect,會已為您建立正確的 AD 物件。 不過在大多數 AD FS 方案中,Microsoft Entra Connect 會以自訂設定執行配置 AD FS,因此必須執行以下步驟。
建立 AD FS 裝置驗證的 AD 物件
如果您的 AD FS 伺服器陣列尚未針對裝置驗證進行設定 (您可以在 [服務 -> 裝置註冊] 下的 [AD FS 管理] 主控台中看到此設定),請使用下列步驟來建立正確的 AD DS 物件和設定。
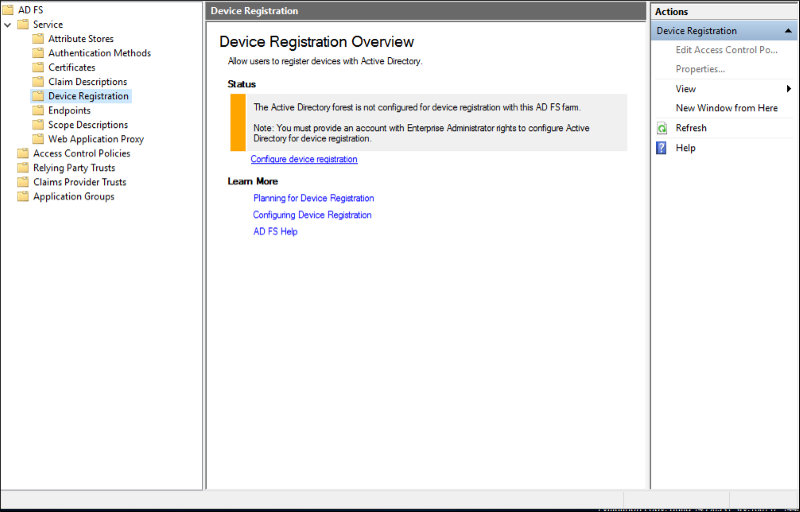
注意:下列命令需要 Active Directory 管理工具,因此若您的同盟伺服器不是網域控制站,請先使用下列步驟 1 安裝工具。 否則,您可以略過步驟 1。
- 執行新增角色 & 功能精靈並選取遠端伺服器管理工具功能 ->角色管理工具>AD DS 和 AD LDS 工具- >選擇適用 Windows PowerShell 的 Active Directory 模組和 AD DS 工具。

在您的 AD FS 主伺服器上,確定您已以 AD DS 使用者身分登入,且具有企業系統管理員 (EA) 權限,並開啟提升權限的 PowerShell 提示字元。 然後執行下列 PowerShell 命令:
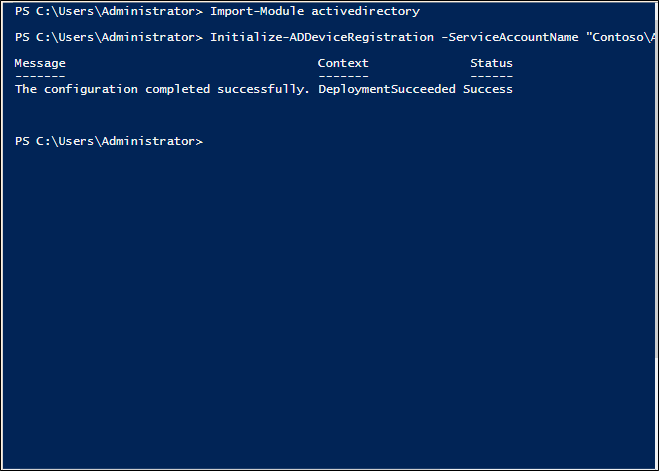
Import-module activedirectoryPS C:\> Initialize-ADDeviceRegistration -ServiceAccountName "<your service account>"在快顯視窗上,點擊 [是]。
注意:如果您的 AD FS 服務設定為使用 GMSA 帳戶,請使用「domain\accountname$」格式輸入帳戶名稱

上述 PSH 會建立下列物件:
- AD 網域分割下的 RegisteredDevices 容器
- [組態] -> [服務] --> [裝置註冊組態] 下的 [裝置註冊服務] 容器和物件
- [組態] -> [服務] --> [裝置註冊組態] 下的 [裝置註冊服務 DKM] 容器和物件
- 完成之後,您會看到成功完成訊息。
在 AD 中建立服務連接點 (SCP)
如果您計劃使用 Windows 10 網域加入 (自動註冊到 Microsoft Entra ID),如此處所言,請執行以下指令在 AD DS 建立服務連接點
開啟 Windows PowerShell 並執行下列命令:
PS C:>Import-Module -Name "C:\Program Files\Microsoft Azure Active Directory Connect\AdPrep\AdSyncPrep.psm1"
注意
必要時請從您的 Microsoft Entra Connect 伺服器複製 AdSyncPrep.psm1 檔案。 本檔案位於 Program Files\Microsoft Entra Connect\AdPrep
提供您的 Microsoft Entra Global 管理員憑證。
PS C:>$aadAdminCred = Get-Credential
執行下列 PowerShell 命令
PS C:>Initialize-ADSyncDomainJoinedComputerSync -AdConnectorAccount [AD connector account name] -AzureADCredentials $aadAdminCred
其中 [AD 連接器帳戶名稱] 是在您新增內部部署 AD DS 目錄時,在 Microsoft Entra Connect 配置的帳戶名稱。
上述指令促使使 Windows 10 客戶端藉由在 AD DS 建立 serviceConnectionpoint 物件,尋找要加入的正確 Microsoft Entra 網域。
準備 AD 以進行裝置回寫
若要確保 AD DS 物件和容器在正確狀態,以便從 Microsoft Entra ID 寫回裝置,請執行以下操作。
開啟 Windows PowerShell 並執行下列命令:
PS C:>Initialize-ADSyncDeviceWriteBack -DomainName <AD DS domain name> -AdConnectorAccount [AD connector account name]
其中 [AD 連接器帳戶名稱] 是在您以網域\帳戶名稱格式新增內部部署 AD DS 目錄時,在 Microsoft Entra Connect 配置的帳戶名稱
上述命令會在裝置回寫至 AD DS 時建立下列物件 (若這些物件尚未存在),並允許存取指定的 AD 連接器帳戶名稱
- AD 網域分割中的 RegisteredDevices 容器
- [組態] -> [服務] --> [裝置註冊組態] 下的 [裝置註冊服務] 容器和物件
在 Microsoft Entra Connect 啟用裝置寫回功能
如果您以前從未做過,請在 Microsoft Entra Connect 啟用裝置寫回功能,方法是第二次執行精靈並選取 "自訂同步選項",然後勾選裝置寫回方塊和選取您已經執行上述 cmdlet 的森林
在 AD FS 中設定裝置驗證
使用提升權限的 PowerShell 命令視窗,執行下列命令來設定 AD FS 原則
PS C:>Set-AdfsGlobalAuthenticationPolicy -DeviceAuthenticationEnabled $true -DeviceAuthenticationMethod All
檢查設定
如需參考,以下是裝置回寫和驗證運作所需 AD DS 裝置、容器和權限的完整清單
類型為 ms-DS-DeviceContainer at CN=RegisteredDevices,DC=<domain> 的物件
- AD FS 服務帳戶的讀取存取權
- 對 Microsoft Entra Connect Sync AD 連接器帳戶的讀/寫存取
Container CN=Device Registration Configuration,CN=Services,CN=Configuration,DC=<domain>
上述容器下的容器裝置註冊服務 DKM

類型為 serviceConnectionpoint at CN=<guid>, CN=Device Registration 的物件
Configuration,CN=Services,CN=Configuration,DC=<domain>
- 新物件上所指定 AD 連接器帳戶名稱的讀取/寫入存取權
類型為 msDS-DeviceRegistrationServiceContainer 的物件在 CN=裝置註冊服務、CN = 裝置註冊配置、CN = 服務、CN = 配置、DC =& ltdomain>
上述容器中類型為 Object of type msDS-DeviceRegistrationServic 的物件
查看其運作情況
若要評估新的宣告和原則,請先註冊裝置。 例如您可以使用系統 - >關於下方的設定應用程式,將 Microsoft Entra 加入 Windows 10 電腦,或者按照這裡的額外步驟設定 Windows 10 網域加入自動裝置註冊。 如需加入 Windows 10 行動裝置的相關資訊,請參閱此處的文件。
若要以最簡單的方式進行評估,請使用顯示宣告清單的測試應用程式登入 AD FS。 您將可以看到新的宣告,包括 isManaged、isCompliant 以及 trusttype。 如果您啟用 Windows Hello 企業版,您也會看到 prt 宣告。
設定其他案例
已加入網域的 Windows 10 電腦自動註冊
若要為已加入網域的 Windows 10 電腦啟用自動裝置註冊,請遵循此處的步驟 1 和 2。 這可協助您達成下列目標:
- 確定 AD DS 中的服務連接點存在,並具有適當的權限 (我們先前已建立過此物件,但再次檢查也無傷大雅)。
- 確定 AD FS 已正確設定
- 確定您的 AD FS 系統已啟用正確端點,並已設定宣告規則
- 針對已加入網域電腦的自動裝置註冊,設定所需的群組原則設定
Windows Hello 企業版
如需使用 Windows Hello 企業版啟用 Windows 10 的資訊,請參閱在組織中啟用 Windows Hello 企業版。
自動 MDM 註冊
若要啟用已註冊裝置的自動 MDM 註冊,以便您可以在存取控制原則中使用 isCompliant 宣告,請遵循此處的步驟。
疑難排解
- 如果您收到錯誤,
Initialize-ADDeviceRegistration抱怨物件已經以錯誤狀態存在,例如 "已經找到缺乏所有必要屬性的 DRS 服務物件",則您可能之前已經執行過 Microsoft Entra Connect PowerShell 指令,並在 AD DS 有部份配置。 請嘗試在 CN=Device Registration Configuration,CN=Services,CN=Configuration,DC=<domain> 下手動刪除物件,然後再試一次。 - 針對已加入網域的 Windows 10 用戶端
- 若要確認裝置驗證是否正常運作,請以測試使用者帳戶身分登入已加入網域的用戶端。 若要快速觸發佈建,請至少鎖定並解除鎖定桌面一次。
- 在 AD DS 物件上檢查 STK 金鑰認證連結的指示 (同步仍必須執行兩次嗎?)
- 如果您在嘗試註冊裝置已註冊的 Windows 電腦時收到錯誤,但無法或已經取消註冊裝置,則登錄中可能有裝置註冊設定片段。 若要調查並移除此錯誤,請使用下列步驟:
- 在 Windows 電腦上,開啟 Regedit 並瀏覽至 HKLM\Software\Microsoft\Enrollments
- 在此機碼下,GUID 表單中將會有許多子機碼。 導航到含有 ~17 個值且 "EnrollmentType" 為 "6" [已加入 MDM] 或 "13" (已加入 Microsoft Entra) 的子索引鍵
- 將 EnrollmentType 修改為 0
- 再次嘗試裝置註冊或登錄