AD FS 和憑證 KeySpec 內容資訊
金鑰規格 (“KeySpec”) 是與憑證和金鑰相關聯的屬性。 其可指定與憑證相關聯的私密金鑰是否可用於簽署、加密或兩者。
不正確的 KeySpec 值可能會導致 AD FS 和 Web 應用程式 Proxy 錯誤,例如:
- 無法建立與 AD FS 或 Web 應用程式 Proxy 的 SSL/TLS 連線,且未記錄任何 AD FS 事件 (雖然可記錄 SChannel 36888 和 36874 事件)
- 無法登入 AD FS 或 WAP 表單型驗證頁面,且頁面上未顯示任何錯誤訊息。
您可能會在事件記錄檔中看到下列事件:
Log Name: AD FS Tracing/Debug
Source: AD FS Tracing
Date: 2/12/2015 9:03:08 AM
Event ID: 67
Task Category: None
Level: Error
Keywords: ADFSProtocol
User: S-1-5-21-3723329422-3858836549-556620232-1580884
Computer: ADFS1.contoso.com
Description:
Ignore corrupted SSO cookie.
造成問題的原因
KeySpec 屬性可識別如何使用透過 Microsoft 舊版密碼編譯儲存提供者 (CSP) 的 Microsoft CryptoAPI (CAPI) 產生或擷取的金鑰。
KeySpec 值 1 或 AT_KEYEXCHANGE 可用於簽署和加密。 值 2或 AT_SIGNATURE 只會用於簽署。
最常見的 KeySpec 錯誤設定是針對權杖簽署憑證以外的憑證使用值 2。
對於使用新一代密碼編譯 (CNG) 提供者產生金鑰的憑證,沒有金鑰規格的概念,且 KeySpec 值一律為零。
了解如何在本文的下一節中檢查有效的 KeySpec 值。
範例
舊版 CSP 的範例是 Microsoft 增強式密碼編譯提供者。
Microsoft RSA CSP 金鑰 Blob 格式包含演算法識別碼 (CALG_RSA_KEYX 或 CALG_RSA_SIGN),分別為 AT_KEYEXCHANGE 或 AT_SIGNATURE 金鑰的要求提供服務。
RSA 金鑰演算法識別碼會對應至 KeySpec 值,如下所示:
| 提供者支援的演算法 | CAPI 呼叫的金鑰規格值 |
|---|---|
CALG_RSA_KEYX:可用於簽署和解密的 RSA 金鑰 |
AT_KEYEXCHANGE (或 KeySpec=1) |
CALG_RSA_SIGN:僅限 RSA 簽章金鑰 |
AT_SIGNATURE (或 KeySpec=2) |
KeySpec 值和相關意義
以下是各種 KeySpec 值的意義:
| Keyspec 值 | 方法 | 建議的 AD FS 用法 |
|---|---|---|
0 |
憑證是 CNG 憑證 | 僅限 SSL 憑證 |
1 |
針對舊版 CAPI (非 CNG) 憑證,金鑰可用於簽署和解密 | SSL、權杖簽署、權杖解密、服務通訊憑證 |
2 |
針對舊版 CAPI (非 CNG) 憑證,金鑰只能用於簽署 | 不建議 |
如何檢查憑證/金鑰的 KeySpec 值
若要查看憑證的值,您可使用 certutil 命令列工具。
以下是一個範例:certutil –v –store my。 此命令會將憑證資訊傾印到畫面。
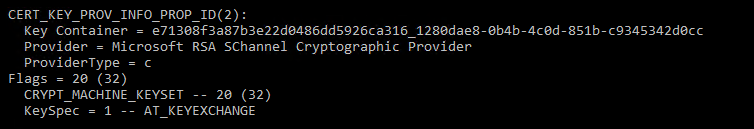
在 CERT_KEY_PROV_INFO_PROP_ID 之下尋找兩件事:
ProviderType:這表示憑證是使用舊版密碼編譯儲存提供者 (CSP),還是使用以較新的新一代憑證 (CNG) API 為基礎的金鑰儲存提供者。 非零值表示舊版提供者。
KeySpec:下表顯示 AD FS 憑證的有效
KeySpec值:舊版 CSP 提供者 (ProviderType 不等於 0):
AD FS 憑證用途 有效的 Keyspec 值 服務通訊 1 權杖解密 1 權杖簽署 1 和 2 SSL 1 CNG 提供者 (ProviderType = 0):
AD FS 憑證用途 有效的 Keyspec 值 SSL 0
如何將憑證的 keyspec 變更為支援的值
變更 KeySpec 值不需要重新產生或重新發出憑證。 使用下列步驟,將 PFX 檔案中的完整憑證和私密金鑰重新匯入憑證存放區,即可變更 KeySpec。
- 檢查並記錄現有憑證的私密金鑰權限,以便在重新匯入之後視需要重新設定這些權限。
- 將包含私密金鑰的憑證匯出至 PFX 檔案。
- 針對每個 AD FS 和 WAP 伺服器執行下列步驟。
- 刪除憑證 (從 AD FS / WAP 伺服器)。
- 開啟已提高權限的 PowerShell 命令提示字元。
- 使用下列語法,在每個 AD FS 和 WAP 伺服器上匯入 PFX 檔案,並指定
AT_KEYEXCHANGE值 (適用於所有 AD FS 憑證用途):certutil –importpfx certfile.pfx AT_KEYEXCHANGE- 輸入 PFX 密碼。
- 上述程序完成之後,請執行下列動作:
- 檢查私密金鑰權限。
- 重新啟動 AD FS 或 WAP 服務。