無線存取部署
適用於:Windows Server 2022、Windows Server 2019、Windows Server 2016
請遵循下列步驟來部署無線存取:
部署和設定無線 AP
請遵循下列步驟來部署和設定無線 AP:
注意
本指南的程序不包含開啟 [使用者帳戶控制] 對話方塊來要求權限以繼續執行的說明。 如果執行本指南的程序時此對話方塊開啟,或此對話方塊因回應您的動作而開啟,請按一下 [繼續]。
指定無線 AP 頻道頻率
當您在單一地理站點部署多個無線 AP 時,您必須為訊號重疊的無線 AP 進行設定,讓其均使用唯一的頻道頻率以減少無線 AP 之間的干擾。
您可以使用下列指導方針來協助您選擇不會與無線網路所在地理位置的其他無線網路衝突的頻道頻率。
如果附近有其他組織的辦公室或其辦公室與貴組織的辦公室位於同一棟大樓內,請識別環境內是否有這些組織所擁有的任何無線網路。 請了解其無線 AP 的所在位置和指派的頻道頻率,因為您需要為您的 AP 指派不同的頻道頻率,而且您需要判斷您 AP 的最佳安裝位置。
請識別貴組織內相鄰樓層的重疊無線訊號。 在識別組織內外的重疊訊號涵蓋範圍後,請為您的無線 AP 指派頻道頻率,並確保您有為任何兩個訊號涵蓋範圍重疊的無線 AP 指派不同的頻道頻率。
設定無線 AP
使用下列資訊以及無線 AP 製造商所提供的產品文件來設定無線 AP。
此程序會列舉無線 AP 上常會設定的項目。 項目名稱可能會因品牌和型號而有所不同,而且可能會與下列清單中的名稱不同。 如需特定詳細資料,請參閱無線 AP 的文件。
設定無線 AP
SSID。 指定無線網路的名稱 (例如 ExampleWLAN)。 這是會向無線用戶端公告的名稱。
加密。 請根據無線用戶端電腦網路介面卡支援的版本,指定 WPA2-Enterprise (慣用) 或 WPA-Enterprise 以及 AES (慣用) 或 TKIP 加密。
無線 AP IP 位址 (靜態)。 在每個 AP 上設定落在子網路 DHCP 範圍排除範圍內的唯一靜態 IP 位址。 使用從 DHCP 所指派的位址範圍中排除的位址,可防止 DHCP 伺服器將相同的 IP 位址指派給電腦或其他裝置。
子網路遮罩。 請將此項目設定為符合無線 AP 所連線 LAN 的子網路遮罩設定。
DNS 名稱。 您可以使用 DNS 名稱來設定某些無線 AP。 網路上的 DNS 服務可以將 DNS 名稱解析為 IP 位址。 請在每個支援此功能的無線 AP 上,輸入用於 DNS 解析的唯一名稱。
DHCP 服務。 如果無線 AP 內建 DHCP 服務,請加以停用。
RADIUS 共用密碼。 除非您打算依群組將 AP 設定為 NPS 中的 RADIUS 用戶端,否則請為每個無線 AP 使用唯一的 RADIUS 共用密碼。 如果您打算在 NPS 中依群組設定 AP,則群組的每個成員必須使用相同的共用密碼。 此外,您使用的每個共用密碼都應該是至少 22 個字元、混合大寫和小寫字母、數字和標點符號的隨機順序。 為確保隨機性,您可以使用隨機字元產生器 (例如在 NPS 的設定 802.1X 精靈中找到的隨機字元產生器) 建立共用密碼。
提示
記錄每個無線 AP 的共用密碼,並將其存放在安全的地方,例如辦公室的保險箱。 在 NPS 中設定 RADIUS 用戶端時,必須知道每個無線 AP 的共用密碼。
RADIUS 伺服器 IP 位址。 輸入執行 NPS 之伺服器的 IP 位址。
UDP 連接埠。 NPS 預設會使用 UDP 連接埠 1812 和 1645 來傳送驗證訊息,並使用 UDP 連接埠 1813 和 1646 來傳送帳戶處理訊息。 建議您在 AP 上使用上述的相同 UDP 連接埠,但如果您有使用不同連接埠的合理理由,請確定您不僅有使用新的連接埠號碼來設定 AP,還有重新設定所有 NPS 以使用與 AP 相同的連接埠號碼。 如果未使用相同的 UDP 連接埠設定 AP 和 NPS,NPS 就無法接收或處理來自 AP 的連線要求,而且網路上的所有無線連線嘗試都會失敗。
VSA。 某些無線 AP 需要廠商特定屬性 (VSA) 才能提供完整的無線 AP 功能。 VSA 會新增到 NPS 網路原則中。
DHCP 篩選。 請依無線 AP 製造商所述來設定無線 AP,讓無線用戶端無法將 IP 封包從 UDP 連接埠 68 傳送至網路。
DNS 篩選。 請依無線 AP 製造商所述來設定無線 AP,讓無線用戶端無法將 IP 封包從 TCP 或 UDP 連接埠 53 傳送至網路。
建立無線使用者的安全性群組
請遵循下列步驟建立一或多個無線使用者安全性群組,然後將使用者新增至適當的無線使用者安全性群組:
建立無線使用者安全性群組
您可以使用此程序在 Active Directory 使用者和電腦 Microsoft Management Console (MMC) 嵌入式管理單元中建立無線安全性群組。
若要執行此程序,至少需要 Domain Admins 的成員資格或同等權限。
建立無線使用者安全性群組
依序按一下 [開始]、[系統管理工具] 及 [Active Directory 使用者和電腦]。 Active Directory 使用者和電腦嵌入式管理單元便會開啟。 如果尚未選取,請按一下您的網域節點。 例如,如果您的網域是 example.com,請按一下 [example.com]。
在 [詳細資料] 窗格中,以滑鼠右鍵按一下您要在其中新增群組的資料夾 (例如,以滑鼠右鍵按一下 [使用者])、指向 [新增],然後按一下 [群組]。
在 [新增物件 - 群組] 的 [群組名稱] 中,輸入新群組的名稱。 例如,輸入無線群組。
在 [群組範圍] 中,選取下列其中一個選項:
網域本機
全球
萬用
在 [群組類型] 中,選取 [安全性]。
按一下 [確定]。
如果您需要多個無線使用者安全性群組,請重複上述步驟以建立額外的無線使用者群組。 稍後,您可以在 NPS 中建立個別的網路原則,以向每個群組套用不同的條件和條件約束,為其提供不同的存取權限和連線規則。
將使用者新增至無線使用者安全性群組
您可以使用此程序,在 Active Directory 使用者和電腦 Microsoft Management Console (MMC) 嵌入式管理單元中將使用者、電腦或群組新增至無線安全性群組。
若要執行此程序,至少需要 Domain Admins 的成員資格或同等權限。
將使用者新增至無線安全性群組
依序按一下 [開始]、[系統管理工具] 及 [Active Directory 使用者和電腦]。 這樣會開啟 [Active Directory 使用者和電腦] MMC。 如果尚未選取,請按一下您的網域節點。 例如,如果您的網域是 example.com,請按一下 [example.com]。
在 [詳細資料] 窗格中,按兩下包含無線安全性群組的資料夾。
在 [詳細資料] 窗格中,以滑鼠右鍵按一下該無線安全性群組,然後按一下 [屬性]。 安全性群組的 [屬性] 對話方塊便會開啟。
在 [成員] 索引標籤上,按一下 [新增],然後完成下列其中一個程序以新增電腦或新增使用者或群組。
新增使用者或群組
在 [輸入要選取的物件名稱] 中,輸入您要新增的使用者或群組的名稱,然後按一下 [確定]。
若要將群組成員資格指派給其他使用者或群組,請重複此程序的步驟 1。
若要新增電腦
按一下 [物件類型]。 [物件類型] 對話方塊便會開啟。
在 [物件類型] 中,選取 [電腦],然後按一下 [確定]。
在 [輸入要選取的物件名稱] 中,輸入您要新增的電腦所具有的名稱,然後按一下 [確定]。
若要將群組成員資格指派給其他電腦,請重複此程序的步驟 1-3。
設定無線網路 (IEEE 802.11) 原則
請遵循下列步驟來設定無線網路 (IEEE 802.11) 原則的群組原則延伸:
開啟或新增並開啟群組原則物件
根據預設,在已安裝 Active Directory Domain Services (AD DS) 伺服器角色且伺服器設定為網域控制站時,執行 Windows Server 2016 的電腦上會安裝群組原則管理功能。 下列程序會說明如何在網域控制站上開啟群組原則管理主控台 (GPMC)。 此程序接著會說明如何開啟現有的網域層級群組原則物件 (GPO) 以供編輯,或建立新的網域 GPO 並加以開啟以供編輯。
若要執行此程序,至少需要 Domain Admins 的成員資格或同等權限。
開啟或新增並開啟群組原則物件
在網域控制站上,依序按一下 [開始]、[Windows 系統管理工具] 和 [群組原則管理]。 此時會開啟群組原則管理主控台。
在左窗格中,按兩下您的樹系。 例如,按兩下 [樹系:example.com]。
在左窗格中按兩下 [網域],然後按兩下您要管理其群組原則物件的網域。 例如,按兩下 example.com。
執行下列其中一個動作:
若要開啟現有的網域層級 GPO 以供編輯,請按兩下您要管理的群組原則物件所屬的網域,以滑鼠右鍵按一下您要管理的網域原則 (例如 [預設網域原則]),然後按一下 [編輯]。 [群組原則管理編輯器] 便會開啟。
若要建立新的群組原則物件並加以開啟以供編輯,請以滑鼠右鍵按一下要建立新群組原則物件的網域,然後按一下 [在這個網域中建立 GPO 並連結到這裡]。
在 [新增 GPO] 的 [名稱] 中,輸入新群組原則物件的名稱,然後按一下 [確定]。
以滑鼠右鍵按一下新的群組原則物件,然後按一下 [編輯]。 [群組原則管理編輯器] 便會開啟。
在下一節中,您會使用群組原則管理編輯器來建立無線原則。
啟用預設無線網路 (IEEE 802.11) 原則
此程序會說明如何使用群組原則管理編輯器 (GPME) 來啟用預設無線網路 (IEEE 802.11) 原則。
注意
在啟用 Windows Vista 和更新版本的無線網路 (IEEE 802.11) 原則或 Windows XP 版本後,當您以滑鼠右鍵按一下 [無線網路 (IEEE 802.11) 原則] 時,選項清單中會自動移除版本選項。 這是因為在選取原則版本後,當您選取 [無線網路 (IEEE 802.11) 原則] 節點時,GPME 的 [詳細資料] 窗格中便會新增該原則。 此狀態會維持不變,除非您刪除無線原則,此時無線原則版本就會回到 GPME 中 [無線網路 (IEEE 802.11) 原則] 的右鍵功能表內。 此外,只有在選取 [無線網路 (IEEE 802.11) 原則] 節點時,GPME 的 [詳細資料] 窗格中才會列出無線原則。
若要執行此程序,至少需要 Domain Admins 的成員資格或同等權限。
啟用預設無線網路 (IEEE 802.11) 原則
遵循先前的程序開啟或新增並開啟群組原則物件以開啟 GPME。
在 GPME 的左窗格中,依序按兩下 [電腦設定]、[原則]、[Windows 設定] 和 [安全性設定]。
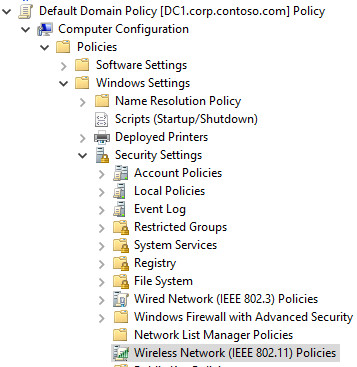
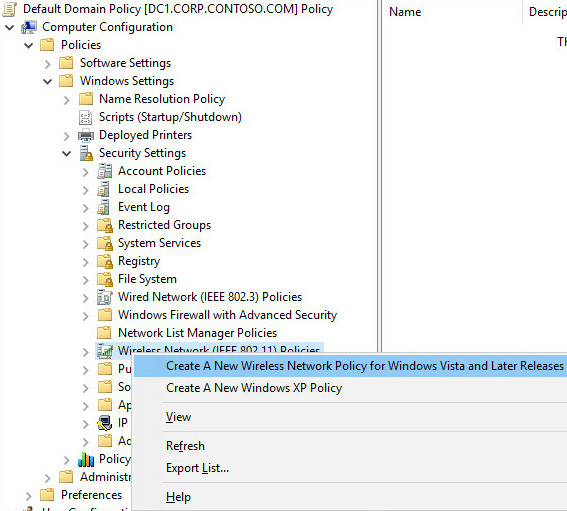
- 在 [安全性設定] 中,以滑鼠右鍵按一下[無線網路 (IEEE 802.11) 原則],然後按一下 [為 Windows Vista 和更新版本建立新的無線原則]。
- [新增無線網路原則屬性] 對話方塊便會開啟。 在 [原則名稱] 中,為原則輸入新名稱,或保留預設名稱。 按一下 [確定] 以儲存原則。 預設原則便會啟用並列在 GPME 的 [詳細資料] 窗格中,且具有您提供的新名稱或預設名稱 (新的無線網路原則)。
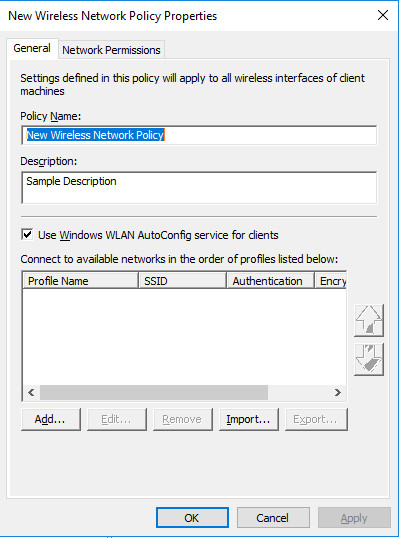
- 在 [詳細資料] 窗格中,按兩下 [新的無線網路原則] 來加以開啟。
在下一節中,您可以執行原則設定、原則處理喜好設定順序和網路權限。
設定新的無線網路原則
您可以使用本節中的程序來設定無線網路 (IEEE 802.11) 原則。 此原則可讓您設定安全性與驗證設定、管理無線設定檔,並為沒有設定成慣用網路的無線網路指定權限。
設定 PEAP-MS-CHAP v2 的無線連線設定檔
此程序提供設定 PEAP-MS-CHAP v2 無線設定檔所需的步驟。
至少要有 Domain Admins 的成員資格或是對等成員資格,才能完成此程序。
設定 PEAP-MS-CHAP v2 的無線連線設定檔
在 GPME 中,於您剛建立之原則的 [無線網路屬性] 對話方塊中,請於 [一般] 索引標籤和 [描述] 中輸入原則的簡短描述。
若要指定使用 WLAN 自動設定來設定無線網路介面卡設定,請確定您已選取 [針對用戶端使用 Windows WLAN 自動設定服務]。
在 [按照以下列出的設定檔順序連線到可用網路上] 中,按一下 [新增],然後選取 [基礎結構]。 [新增設定檔屬性] 對話方塊便會開啟。
在 [新增設定檔屬性] 對話方塊的 [連線] 索引標籤中,於 [設定檔名稱] 欄位為設定檔輸入新名稱。 例如,輸入 Windows 10 的 Example.com WLAN 設定檔。
在 [網路名稱 (SSID)] 中,輸入對應到無線 AP 上所設定 SSID 的 SSID,然後按一下 [新增]。
如果您的部署使用多個 SSID,且每個無線 AP 都使用相同的無線安全性設定,請重複此步驟來為您要套用此設定檔的每個無線 AP 新增 SSID。
如果您的部署使用多個 SSID,但每個 SSID 的安全性設定不相符,請為使用相同安全性設定的每個 SSID 群組設定個別的設定檔。 例如,如果您有一組無線 AP 設定為使用 WPA2-Enterprise 與 AES,而另一組無線 AP 設定為使用 WPA-Enterprise 與 TKIP,請為每一組無線 AP 設定設定檔。
如果有預設文字 NEWSSID,請加以選取,然後按一下 [移除]。
如果您部署設定為抑制廣播指標的無線存取點,請選取 [即使網路未廣播,還是進行連線]。
注意
啟用此選項可能造成安全性風險,因為無線用戶端將探測並嘗試連線到任何無線網路。 預設不會啟用此設定。
按一下 [安全性] 索引標籤,按一下 [進階],然後設定下列設定:
若要設定進階 802.1X 設定,請在 [IEEE 802.1X] 中選取 [強制執行進階 802.1X 設定]。
強制執行進階 802.1X 設定時,[EAPOL-Start 訊息的上限數]、[保留週期]、[開始週期] 以及 [驗證期間] 的預設值,已足夠完成典型的無線部署。 因此,除非有特定原因,否則不需要變更預設值。
若要啟用「單一登入」,請選取 [對此網路啟用單一登入]。
[單一登入] 中其餘的預設值足以用於一般的無線部署。
如果您的無線 AP 是設定為預先驗證,請在 [快速漫遊] 中選取 [此網路使用預先驗證]。
若要指定無線通訊符合 FIPS 140-2 標準,請選取 [以 FIPS 140-2 認證的模式執行密碼編譯]。
按一下 [確定] 以返回 [安全性] 索引標籤。如果無線 AP 與無線用戶端網路介面卡支援 WPA2-Enterprise,請在 [對此網路選取安全性方法] 的 [驗證] 中,選取 [WPA2-Enterprise]。 否則,選取 [WPA-Enterprise]。
如果您的無線 AP 和無線用戶端網路介面卡可支援,請在 [加密] 中選取 [AES-CCMP]。 如果您使用支援 802.11ac 的存取點和無線網路介面卡,請選取 [AES-GCMP]。 否則,選取 [TKIP]。
注意
[驗證] 與 [加密] 的設定必須符合在無線 AP 所設定的設定。 [驗證模式]、[驗證失敗的數目上限] 以及 [快取使用者資訊以供此網路的後續連線使用] 的預設設定都足以用於一般的無線部署。
在 [選取網路驗證方法] 中,選取 [受保護的 EAP (PEAP)],然後按一下 [內容]。 [受保護的 EAP 屬性] 對話方塊便會開啟。
在 [受保護的 EAP 屬性] 中,確認您已選取 [透過驗證憑證來確認伺服器身分識別]。
在 [受信任的根憑證授權單位] 中,選取受信任的根憑證授權單位 (CA),此憑證授權單位發行伺服器憑證給 NPS。
注意
此設定會將用戶端信任的根 CA 範圍限制為只限選取的 CA。 若未選取受信任的根 CA,用戶端將會信任其受信任的根憑證授權單位憑證存放區中所列的所有根 CA。
在 [選擇驗證方法] 清單中,選取 [安全護的密碼 (EAP-MSCHAP v2)]。
按一下 [設定] 。 在 [EAP MSCHAPv2 屬性] 對話方塊中,確認您已選取 [自動使用我的 Windows 登入名稱及密碼 (及網域,如果有的話)],然後按一下 [確定]。
若要啟用 [PEAP 快速重新連線],請確定已選取 [啟用快速重新連線]。
若要在嘗試連線時要求伺服器密碼編譯繫結 TLV,請選取 [如果伺服器未出示密碼編譯繫結 TLV 就中斷連線]。
若要指定驗證的第一個階段要為使用者身分識別產生遮罩,請選取 [啟用身分識別隱私權],然後在文字方塊中輸入匿名的身分識別名稱,或讓文字方塊保持空白。
[!NOTES]
- 您必須使用 NPS 連線要求原則來建立 802.1X 無線的 NPS 原則。 如果使用 NPS 網路原則來建立 NPS 原則,則身分識別隱私權不會運作。
- EAP 身分識別隱私權是由某些 EAP 方法所提供,這些方法會傳送空白或匿名的身分識別 (不同於實際的身分識別) 以回應 EAP 身分識別要求。 PEAP 會在驗證期間傳送身分識別兩次。 在第一個階段,身分識別會以純文字形式傳送,而且此身分識別會用於路由用途,而非用於用戶端驗證。 用於驗證的實際身分識別則會在驗證的第二個階段,於第一個階段所建立的安全通道內進行傳送。 如果選取 [啟用身分識別隱私權] 核取方塊,則系統會將使用者名稱取代為文字方塊中指定的項目。 例如,假設您已選取 [啟用身分識別隱私權],並在文字方塊中指定身分識別隱私權別名為 [匿名]。 對於實際身分識別別名為 jdoe@example.com 的使用者,在驗證的第一個階段中傳送的身分識別會變更為 anonymous@example.com。 第 1 階段身分識別的領域部分不會有所修改,因為其用於路由用途。
按一下 [確定] 以關閉 [受保護的 EAP 屬性] 對話方塊。
按一下 [確定] 以關閉 [安全性] 索引標籤。
如果您想要建立其他設定檔,請按一下 [新增],然後重複上述步驟,針對您要套用設定檔的無線用戶端和網路進行不同選擇以自訂每個設定檔。 當您新增完設定檔時,請按一下 [確定] 以關閉 [無線網路原則屬性] 對話方塊。
在下一節中,您可以為原則設定檔排序以獲得最佳安全性。
設定無線連線設定檔的喜好設定順序
如果您已在無線網路原則中建立多個無線設定檔,而且想要為設定檔排序以獲得最佳效果和安全性,則可以使用此程序。
為確保無線用戶端會以其所能支援的最高階安全性進行連線,請將最嚴格的原則放在清單頂端。
例如,如果您有兩個設定檔,一個用於支援 WPA2 的用戶端,另一個用於支援 WPA 的用戶端,則請將 WPA2 設定檔放在清單上較前面的位置。 這可確保支援 WPA2 的用戶端會使用該方法來連線,而非使用較不安全的 WPA。
此程序所提供的步驟,可指定要以何種順序使用無線連線設定檔,以將網域成員無線用戶端連線到無線網路的順序。
至少要有 Domain Admins 的成員資格或是對等成員資格,才能完成此程序。
設定無線連線設定檔的喜好設定順序
在 GPME 中,於剛才所設定原則的 [無線網路屬性] 對話方塊中,按一下 [一般] 索引標籤。
在 [一般] 索引標籤的 [按照以下列出的設定檔順序連線到可用網路上] 中,選取要移入清單的設定檔,然後按一下 [向上箭號] 按鈕或 [向下箭號] 按鈕,以將設定檔移至您想要的清單位置。
針對要移入清單的每個設定檔重複步驟 2。
按一下 [確定] 以儲存所有變更。
在下一節中,您可以定義無線原則的網路權限。
定義網路權限
您可以在 [網路權限] 索引標籤上針對套用無線網路 (IEEE 802.11) 原則的網域成員進行設定。
您只能針對未設定於 [無線網路原則屬性] 頁面的 [一般] 索引標籤上的無線網路套用下列設定:
針對以網路類型和服務組識別元 (SSID) 指定的特定無線網路,允許或拒絕與該無線網路的連線
允許或拒絕與臨機操作網路的連線
允許或拒絕與基礎結構網路的連線
允許或拒絕使用者檢視系統拒絕其存取的網路類型 (臨機操作或基礎結構)
允許或拒絕使用者建立套用至所有使用者的設定檔
使用者只能使用群組原則設定檔連線到允許的網路
至少要有 Domain Admins 的成員資格或是對等成員資格,才能完成這些程序。
允許或拒絕與特定無線網路的連線
在 GPME 的 [無線網路屬性] 對話方塊中,按一下 [網路權限] 索引標籤。
在 [網路權限] 索引標籤上,按一下 [新增]。 [新增權限項目] 對話方塊便會開啟。
在 [新增權限項目] 對話方塊的 [網路名稱 (SSID)] 欄位中,針對要定義權限的網路輸入其網路 SSID。
在 [網路類型] 中,選取 [基礎結構] 或 [臨機操作]。
注意
如果您不確定廣播網路是基礎結構網路還是臨機操作網路,則可以設定兩個網路權限項目,每種網路類型都設定一個。
在 [權限] 中,選取 [允許] 或 [拒絕]。
按一下 [確定] 以返回 [網路權限] 索引標籤。
指定其他網路權限 (選擇性)
在 [網路權限] 索引標籤上,設定下列任一項或所有項目:
若要拒絕網域成員存取臨機操作網路,請選取 [防止連線至臨機操作網路]。
若要拒絕網域成員存取基礎結構網路,請選取 [防止連線至基礎結構網路]。
若要允許網域成員檢視系統拒絕其存取的網路類型 (臨機操作或基礎結構),請選取 [允許使用者檢視拒絕的網路]。
若要允許使用者建立會套用至所有使用者的設定檔,請選取 [允許任何人建立所有使用者設定檔]。
若要指定使用者只能使用群組原則設定檔連線到允許的網路,請選取 [僅針對允許的網路使用群組原則設定檔]。
設定 NPS
請遵循下列步驟來設定 NPS 以執行無線存取的 802.1X 驗證:
在 Active Directory Domain Services 中註冊 NPS
您可以使用此程序,在 NPS 所屬網域的 Active Directory Domain Services (AD DS) 中註冊執行網路原則伺服器 (NPS) 的伺服器。 若要在授權程序進行期間向 NPS 授與讀取使用者帳戶撥入屬性的權限,則必須在 AD DS 中註冊每個 NPS。 註冊 NPS 會將伺服器新增至 AD DS 中的 RAS 和 IAS 伺服器安全性群組。
注意
您可以將 NPS 安裝到網域控制站或專用伺服器上。 如果您尚未安裝 NPS,請執行下列 Windows PowerShell 命令來加以安裝:
Install-WindowsFeature NPAS -IncludeManagementTools
至少要有 Domain Admins 的成員資格或是對等成員資格,才能完成此程序。
在其預設網域中註冊 NPS
在您 NPS 的 [伺服器管理員] 中,按一下 [工具],然後按一下 [網路原則伺服器]。 NPS 嵌入式管理單元便會開啟。
在 [NPS (本機)] 上按一下滑鼠右鍵,然後按一下 [在 Active Directory 中註冊伺服器]。 [網路原則伺服器] 對話方塊便會開啟。
在 [網路原則伺服器] 中,按一下 [確定],然後再按一次 [確定]。
將無線 AP 設定為 NPS RADIUS 用戶端
您可以使用此程序,透過 NPS 嵌入式管理單元,將 AP (也稱為網路存取伺服器 (NAS)) 設定為遠端驗證撥入使用者服務 (RADIUS) 用戶端。
重要
用戶端電腦 (例如無線可攜式電腦及其他執行用戶端作業系統的電腦) 並非 RADIUS 用戶端。 RADIUS 用戶端是網路存取伺服器 (例如無線存取點、支援 802.1X 的交換器、虛擬私人網路 (VPN) 伺服器和撥號伺服器),因為其會使用 RADIUS 通訊協定與 NPS 之類的 RADIUS 伺服器進行通訊。
至少要有 Domain Admins 的成員資格或是對等成員資格,才能完成此程序。
將網路存取伺服器新增為 NPS 中的 RADIUS 用戶端
在您 NPS 的 [伺服器管理員] 中,按一下 [工具],然後按一下 [網路原則伺服器]。 NPS 嵌入式管理單元便會開啟。
在 NPS 嵌入式管理單元中,按兩下 [RADIUS 用戶端和伺服器]。 以滑鼠右鍵按一下 [RADIUS 用戶端],然後按一下 [新增]。
在 [新增 RADIUS 用戶端] 中,確認您已選取 [啟用此 RADIUS 用戶端] 核取方塊。
在 [新增 RADIUS 用戶端] 的 [自訂名稱] 中,輸入無線存取點的顯示名稱。
例如,如果您想要新增名為 AP-01 的無線存取點 (AP),請輸入 AP-01。
在 [位址 (IP 或 DNS)] 中,輸入 NAS 的 IP 位址或完整網域名稱 (FQDN)。
如果您輸入 FQDN,為確認名稱正確且對應至有效的 IP 位址,請按一下 [確認],然後在 [確認位址] 的 [位址] 欄位中,按一下 [解析]。 如果 FQDN 名稱對應至有效的 IP 位址,該 NAS 的 IP 位址會自動出現在 [IP 位址] 中。 如果 FQDN 無法解析為 IP 位址,則您會收到訊息,內容指出沒有這類已知主機。 如果發生這種情況,請確認 AP 名稱正確無誤,且 AP 已開啟電源並連線到網路。
按一下 [確定] 以關閉 [確認位址]。
在 [新增 RADIUS 用戶端] 的 [共用密碼] 中,執行下列其中一個動作:
若要手動設定 RADIUS 共用密碼,請選取 [手動],然後在 [共用密碼] 中輸入也在 NAS 上輸入的強式密碼。 在 [確認共用密碼] 中重新輸入共用密碼。
若要自動產生共用密碼,請選取 [產生] 核取方塊,然後按一下 [產生] 按鈕。 儲存所產生的共用密碼,然後使用該值來設定 NAS,使其可與 NPS 通訊。
重要
您在 NPS 中針對虛擬 AP 輸入的 RADIUS 共用密碼必須完全符合您在實際的無線 AP 上設定的 RADIUS 共用密碼。 如果您使用 NPS 選項來產生 RADIUS 共用密碼,則必須使用 NPS 所產生的 RADIUS 共用密碼來設定相符的實際無線 AP。
在 [新增 RADIUS 用戶端] 的 [進階] 索引標籤上,於 [廠商名稱] 中指定 NAS 製造商名稱。 如果您不確定 NAS 製造商名稱,請選取 [RADIUS 標準]。
在 [其他選項] 中,如果您使用 EAP 和 PEAP 以外的任何驗證方法,而且您的 NAS 支援使用訊息驗證者屬性,請選取 [存取要求訊息必須包含 Message-Authenticator 屬性]。
按一下 [確定]。 NAS 便會出現在 NPS 上所設定的 RADIUS 用戶端清單中。
使用精靈建立 802.1X 無線的 NPS 原則
您可以使用此程序,建立要將支援 802.1X 的無線存取點以遠端驗證撥入使用者服務 (RADIUS) 用戶端的形式部署至執行網路原則伺服器 (NPS) 的 RADIUS 伺服器所需的連線要求原則和網路原則。 在執行精靈之後,會建立下列原則:
一個連線要求原則
一個網路原則
注意
您可以在每次需要建立 802.1X 驗證存取的新原則時,執行 [新增 IEEE 802.1X 的安全有線及無線連線] 精靈。
至少要有 Domain Admins 的成員資格或是對等成員資格,才能完成此程序。
使用精靈建立 802.1X 驗證無線的原則
開啟 NPS 嵌入式管理單元。 如果尚未選取,請按一下 [NPS (本機)]。 如果您正在執行 NPS MMC 嵌入式管理單元,並要在遠端 NPS 上建立原則,請選取此伺服器。
在 [使用者入門] 的 [標準設定] 中,選取 [802.1X 無線或有線連線的 RADIUS 伺服器]。 此文字下方的文字與連結會變更,以反映您所做的選擇。
按一下 [設定 802.1X]。 [設定 802.1X] 精靈便會開啟。
在 [選取 802.1X 連線類型] 精靈頁面上,於 [802.1X 連線的類型] 中,選取 [安全的無線連線],然後在 [名稱] 中輸入原則的名稱,或保留預設名稱 [安全的無線連線]。 按一下 [下一步] 。
[指定 802.1X 交換器] 精靈頁面上的 [RADIUS 用戶端] 中會顯示您在 NPS 嵌入式管理單元中新增為 RADIUS 用戶端的所有 802.1X 交換器和無線存取點。 執行下列其中一個步驟:
若要在 [RADIUS 用戶端] 中新增無線 AP 等其他網路存取伺服器 (NAS),請按一下 [新增],然後在 [新增 RADIUS 用戶端] 中輸入下列資訊:[自訂名稱]、[位址 (IP 或 DNS)] 和 [共用密碼]。
若要修改任何 NAS 的設定,請在 [RADIUS 用戶端] 中,選取要修改設定的 AP,然後按一下 [編輯]。 視需要修改設定。
若要從清單中移除 NAS,請在 [RADIUS 用戶端] 中選取 NAS,然後按一下 [移除]。
警告
從 [設定 802.1X] 精靈內移除 RADIUS 用戶端時,系統會從 NPS 設定中刪除該用戶端。 您在 [設定 802.1X] 精靈中對 RADIUS 用戶端所做的所有新增、修改和刪除,都會反映在 NPS 嵌入式管理單元的 [NPS / RADIUS 用戶端和伺服器] 下的 [RADIUS 用戶端] 節點中。 例如,如果您使用精靈移除 802.1X 交換器,則系統也會從 NPS 嵌入式管理單元中移除該交換器。
按一下 [下一步] 。 在 [設定驗證方法] 精靈頁面上的 [類型 (根據存取方法和網路設定)] 中,選取 [Microsoft:受保護的 EAP (PEAP)],然後按一下 [設定]。
提示
如果您收到錯誤訊息,內容指出找不到可與驗證方法搭配使用的憑證,而且您已將 Active Directory 憑證服務設定為自動向網路上的 RAS 和 IAS 伺服器發出憑證,則請先確定您已遵循「在 Active Directory Domain Services 中註冊 NPS」的步驟,然後使用下列步驟來更新群組原則:依序按一下 [開始]、[Windows 系統] 和 [執行],並在 [開啟] 中輸入 gpupdate,然後按 ENTER 鍵。 當命令傳回的結果指出系統已成功更新使用者和電腦群組原則時,請再次選取 [Microsoft:受保護的 EAP (PEAP)],然後按一下 [設定]。
如果在重新整理群組原則後,仍持續收到錯誤訊息指出找不到可與驗證方法搭配使用的憑證,則系統不會顯示該憑證,因為其不符合《核心網路附屬指南》:部署 802.1 X 有線和無線部署的伺服器憑證中所述的最低伺服器憑證需求。 如果發生這種情況,您必須先中止 NPS 設定、撤銷發給 NPS 的憑證,然後再遵循指示,使用伺服器憑證部署指南來設定新的憑證。
在 [編輯受保護的 EAP 屬性] 精靈頁面上,於 [已發出憑證] 中,確定您已選取正確的 NPS 憑證,然後執行下列動作:
注意
請確認 [簽發者] 中的值對於 [已發出憑證] 中所選取的憑證來說是正確的。 例如,在網域 contoso.com 中,執行 Active Directory 憑證服務 (AD CS) 且名為 corp\DC1 的 CA 所發出憑證的預期簽發者是 corp-DC1-CA。
若要允許使用者使用其無線電腦漫遊於存取點之間,而不需要在每次與新的 AP 關聯時重新驗證,請選取 [啟用快速重新連線]。
若要指定如果 RADIUS 伺服器未出示密碼編譯繫結的 Type-Length-Value (TLV),進行連線的無線用戶端就結束網路驗證程序,請選取 [將沒有密碼編譯繫結的用戶端中斷連線]。
若要修改 EAP 類型的原則設定,請在 [EAP 類型] 中,按一下 [編輯],在 [EAP MSCHAPv2 屬性] 中視需要修改設定,然後按一下 [確定]。
按一下 [確定]。 [編輯受保護的 EAP 屬性] 對話方塊便會關閉,且您會回到 [設定 802.1X] 精靈。 按一下 [下一步] 。
在 [指定使用者群組] 中,按一下 [新增],然後在 Active Directory 使用者和電腦嵌入式管理單元中輸入您為無線用戶端設定的安全性群組名稱。 例如,如果您將無線安全性群組命名為「無線群組」,則請輸入無線群組。 按一下 [下一步] 。
按一下 [設定] 以視需要以及如您無線 AP 硬體廠商所提供的文件所指定,設定虛擬 LAN (VLAN) 的 RADIUS 標準屬性和廠商特定屬性。 按一下 [下一步] 。
檢閱設定摘要詳細資料,然後按一下 [完成]。
NPS 原則現已建立好,您可以繼續將無線電腦加入網域。
將新的無線電腦加入網域
要將新的無線電腦加入網域,最簡單的方法就是先以實體方式將電腦連結到有線 LAN 的區段 (亦即不是由 802.1X 交換器控制的區段),再將電腦加入網域。 這個方法最簡單,因為系統會自動套用無線群組原則設定,而且如果您已部署自己的 PKI,電腦就會收到 CA 憑證,並將其放在受信任的根憑證授權單位憑證存放區中,讓無線用戶端能夠信任具有 CA 所發出伺服器憑證的 NPS。
同樣地,在新的無線電腦加入網域後,使用者用來登入網域的較佳方法是使用有線的網路連線來執行登入。
其他加入網域的方法
如果實務上無法使用有線乙太網路連線將電腦加入網域,或者如果使用者無法使用有線連線來進行首次的網域登入,則必須使用替代方法。
- IT 人員電腦設定。 IT 人員的成員會將無線電腦加入網域,並設定單一登入啟動程序無線設定檔。 使用此方法時,IT 系統管理員會將無線電腦連線到有線的乙太網路,並將電腦加入網域。 然後,系統管理員再將電腦分配給使用者。 當使用者在未使用有線連線的情況下啟動電腦時,電腦會使用系統管理員以手動方式指定用於使用者登入的網域認證,來與無線網路連線以及登入該網域。
如需詳細資訊,請參閱使用 IT 人員電腦設定方法加入網域並登入一節
- 使用者啟動程序無線設定檔設定。 使用者根據 IT 系統管理員所提供的指示,使用啟動程序無線設定檔手動設定無線電腦並加入網域。 啟動程序無線設定檔可讓使用者建立無線連線,然後加入網域。 將電腦加入網域並重新啟動電腦後,使用者便可以使用無線連線及其網域帳戶的認證來登入網域。
如需詳細資訊,請參閱使用使用者啟動程序無線設定檔設定來加入網域並登入一節。
使用 IT 人員電腦設定方法加入網域並登入
其無線用戶端電腦已加入網域的網域成員使用者可以使用暫時的無線設定檔來連線到 802.1X 驗證無線網路,而不需要先連線到有線 LAN。 這個暫時的無線設定檔稱為啟動程序無線設定檔。
啟動程序無線設定檔會要求使用者手動指定其網域使用者帳戶認證,而且不會驗證執行網路原則伺服器 (NPS) 之遠端驗證撥入使用者服務 (RADIUS) 伺服器的憑證。
無線連線建立好之後,無線用戶端電腦便會套用群組原則,且系統會自動發出新的無線設定檔。 新原則會使用電腦和使用者帳戶的認證進行用戶端驗證。
此外,在使用新設定檔 (而非啟動程序設定檔) 進行 PEAP-MS-CHAP v2 相互驗證時,用戶端會驗證 RADIUS 伺服器的認證。
在將電腦加入網域後,請先使用此程序設定單一登入啟動程序無線設定檔,再將無線電腦分配給網域成員使用者。
設定單一登入啟動程序無線設定檔
使用這個名為設定 PEAP-MS-CHAP v2 的無線連線設定檔的指南中的程序建立啟動程序設定檔,並使用下列設定:
PEAP-MS-CHAP v2 驗證
驗證 RADIUS 伺服器憑證已停用
單一登入已啟用
在新啟動程序設定檔建立所在無線網路原則的屬性中,於 [一般] 索引標籤上選取啟動程序設定檔,然後按一下 [匯出] 將設定檔匯出至網路共用、USB 快閃磁碟機或其他方便存取的地方。 設定檔會以 *.xml 檔案的形式儲存到指定的地方。
將新的無線電腦加入網域 (例如,透過不需要 IEEE 802.1X 驗證的乙太網路連線),並使用 netsh wlan add profile 命令將啟動程序無線設定檔新增至電腦。
注意
如需詳細資訊,請參閱 http://technet.microsoft.com/library/dd744890.aspx 上的「用於無線區域網路 (WLAN) 的 Netsh 命令」。
透過「使用執行 Windows 10 的電腦登入網域」的程序,將新的無線電腦分配給使用者。
當使用者啟動電腦時,Windows 會提示使用者輸入其網域使用者帳戶名稱和密碼。 因為單一登入已啟用,電腦會使用網域使用者帳戶的認證,先與無線網路連線再登入網域。
使用執行 Windows 10 的電腦登入網域
登出電腦,或重新啟動電腦。
按下鍵盤上的任意按鍵,或按一下桌面。 隨即會出現登入畫面,其中會顯示本機使用者帳戶名稱,名稱下方則有密碼的輸入欄位。 請勿使用本機使用者帳戶來登入。
在畫面左下角,按一下 [其他使用者]。 隨即會出現有兩個欄位的 [其他使用者] 登入畫面,一個欄位用於使用者名稱,另一個欄位用於密碼。 密碼欄位下方是 [登入:] 文字,然後是電腦所加入網域的名稱。 例如,如果網域的名稱是 example.com,則文字會是 [登入: EXAMPLE]。
在 [使用者名稱] 中,輸入網域的使用者名稱。
在 [密碼] 中,輸入網域密碼,然後按方向鍵或按 ENTER。
注意
如果 [其他使用者] 畫面未包含 [登入:] 文字和網域名稱,則請以「domain\user」的格式輸入使用者名稱。 例如,若要使用名為 User-01 的帳戶登入 example.com 網域,請輸入 example\User-01。
使用使用者啟動程序無線設定檔設定來加入網域並登入
使用此方法時,您會先完成<一般步驟>區段中的步驟,然後向網域成員使用者提供有關如何使用啟動程序無線設定檔手動設定無線電腦的指示。 啟動程序無線設定檔可讓使用者建立無線連線,然後加入網域。 電腦加入網域並重新啟動後,使用者便能透過無線連線登入網域。
一般步驟
在 [控制台] 中,為使用者設定本機電腦系統管理員帳戶。
重要
若要將電腦加入網域,使用者必須使用本機系統管理員帳戶登入電腦。 或者,使用者必須在將電腦加入網域的過程中,提供本機系統管理員帳戶的認證。 此外,使用者也必須在其想要在其中加入電腦的網域中擁有使用者帳戶。 在將電腦加入網域的過程中,系統會提示使用者輸入網域帳戶認證 (使用者名稱與密碼)。
向網域使用者提供用於設定啟動程序無線設定檔的指示,如下列程序設定啟動程序無線設定檔所述。
此外,向使用者同時提供本機電腦認證 (使用者名稱和密碼) 以及「DomainName\UserName」形式的網域認證 (網域使用者帳戶名稱和密碼),以及用來「將電腦加入網域」和用來「登入網域」的程序,如 Windows Server 2016 核心網路指南所述。
設定啟動程序無線設定檔
使用網路系統管理員或 IT 支援專業人員所提供的認證,透過本機電腦的系統管理員帳戶登入電腦。
以滑鼠右鍵按一下桌面上的 [網路] 圖示,然後按一下 [開啟網路和共用中心]。 [網路和共用中心] 便會開啟。 在 [變更網路設定] 中,按一下 [設定新的連線或網路]。 [設定連線或網路] 對話方塊便會開啟。
按一下 [手動連線到無線網路],然後按 [下一步]。
在 [手動連線到無線網路] 的 [網路名稱] 中,輸入 AP 的 SSID 名稱。
在 [安全性類型] 中,選取系統管理員所提供的設定。
在 [加密類型] 和 [安全性金鑰] 中,選取或輸入系統管理員所提供的設定。
選取 [自動啟動此連線],然後按 [下一步]。
在 [已成功新增您的網路 SSID] 中,按一下 [變更連線設定]。
按一下 [變更連線設定]。 [您的網路 SSID 無線網路] 屬性對話方塊便會開啟。
按一下 [安全性] 索引標籤,然後在 [選擇網路驗證方法] 中,選取 [受保護的 EAP (PEAP)]。
按一下 [設定] 。 [受保護的 EAP (PEAP) 屬性] 頁面便會出現。
在 [受保護的 EAP (PEAP) 屬性] 頁面中,確定您並未選取 [驗證伺服器憑證],按 [確定] 兩次,然後按一下 [關閉]。
Windows 接著會嘗試連線到無線網路。 啟動程序無線設定檔的設定會指定您必須提供網域認證。 當 Windows 提示您輸入帳戶名稱和密碼時,請輸入您的網域帳戶認證,如下所示:「網域名稱\使用者名稱」、「網域密碼」。
將電腦加入網域
使用本機 Administrator 帳戶登入電腦。
在搜尋文字方塊中,輸入 PowerShell。 在搜尋結果中,以滑鼠右鍵按一下 [Windows PowerShell],然後按一下 [以系統管理員身分執行]。 Windows PowerShell 便會開啟,並出現提升權限的提示。
在 Windows PowerShell 中輸入下列指令,然後按 ENTER 鍵。 確實地將變數 DomainName 取代為您要加入的網域名稱。
Add-Computer DomainName
出現提示時,輸入您的網域使用者名稱和密碼,然後按一下 [確定]。
重新啟動電腦。
遵循上一節使用執行 Windows 10 的電腦登入網域中的指示來進行。