傳輸層安全性 (TLS) 登錄設定
適用於:Windows Server 2022、Windows Server 2019、Windows Server 2016、Windows 11、Windows 10 及之前的版本
本文說明透過 SChannel Security Support Provider (SSP) 實現 Transport Layer Security (TLS) 協定和 Secure Sockets Layer (SSL) 協定 Windows 支援的登錄檔設定資訊。 本文中介紹的登錄子機碼和項目可以幫助您管理 SChannel SSP 並排除問題,具體地說,是 TLS 和 SSL 協定。
警告
這項資訊供您在進行疑難排解或確認必要的設定是否套用時做為參考之用。 建議您不要直接編輯登錄,除非已沒有其他替代方案。 登錄的修改在套用之前,登錄編輯程式或 Windows 作業系統並不會加以驗證。 因此可能會儲存不正確的值,而這將導致系統發生無法復原的錯誤。 盡可能使用 Group Policy 或其他 Windows 工具,例如 Microsoft Management Console (MMC),而不直接編輯登錄檔。 如果您必須編輯登錄,必須非常小心。
Schannel 記錄
SChannel 事件有八個記錄層級儲存在系統事件記錄檔中,並可使用事件檢視器檢視。 此登錄檔路徑儲存在 HKLM\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL 的 EventLogging 機碼下,且 DWORD 值設定為 1。
| 十進位或十六進位 | SChannel 記錄事件 |
|---|---|
| 0 | 沒有任何事件 |
| 1 | 錯誤事件 |
| 2 | 警告事件 |
| 3 | 錯誤和警告事件 |
| 4 | 資訊與成功事件 |
| 5 | 錯誤、資訊和成功事件 |
| 6 | 警告、資訊和成功事件 |
| 7 | 錯誤、警告、資訊和成功事件 |
注意
在變更 SChannel 記錄等級之後,您必須重新啟動您的裝置。
CertificateMappingMethods
當伺服器應用程式需要使用者端驗證時,SChannel 會自動嘗試將使用者端電腦提供的憑證對應到使用者帳戶。 您可以建立對應,將憑證資訊與 Windows 使用者帳戶建立關係,來驗證使用用戶端憑證登入的使用者。
建立並啟用憑證對應之後,每當用戶端出示用戶端憑證時,您的伺服器應用程式便會自動將該名使用者與適當的 Windows 使用者帳戶產生關聯。
在大部分情況下,憑證會透過兩種方式之一對應至使用者帳戶:
- 單一憑證對應至單一使用者帳戶 (一對一對應)。
- 多個憑證對應至一個使用者帳戶 (多對一對應)。
SChannel 提供者使用四 (4) 種憑證對應方法:
- Kerberos 使用者服務 (S4U) 對應 (預設為啟用)
- 使用者主體名稱對應
- 一對一對應 (也稱為主體/簽發者對應)
- 多對一對應
登錄檔路徑:HKLM SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL
| 項目名稱 | 下載 | 預設為啟用 |
|---|---|---|
| 主旨/簽發者 | 0x000000001 | No |
| Issuer | 0x000000002 | No |
| UPN | 0x000000004 | No |
| S4U2Self | 0x000000008 | Yes |
| S4U2Self Explicit | 0x000000010 | Yes |
適用版本:如本文開頭的 Applies To 清單中所指定。
加密
TLS/SSL 密碼應該透過設定密碼套件順序來控制。 有關詳細資訊,請參閱配置 TLS Cipher Suite Order。
如需有關 SChannel SSP 使用的預設密碼套件順序的資訊,請參閱 TLS/SSL中的 Cipher Suites (SChannel SSP)。
CipherSuites
設定 TLS/SSL 密碼套件應該使用群組原則、MDM 或 PowerShell 完成,如需詳細資訊,請參閱設定 TLS Cipher Suite Order。
如需有關 SChannel SSP 使用的預設密碼套件順序的資訊,請參閱 TLS/SSL中的 Cipher Suites (SChannel SSP)。
ClientCacheTime
此項目指定使用者端 TLS 工作階段快取項目留存期 (以毫秒為單位)。 從 Windows Server 2008 和 Windows Vista 開始,預設值為 10 小時。 值 0,將關閉客戶端上的 TLS 會話快取。
當客戶端第一次透過 SChannel SSP 連線到伺服器時,會執行完整的 TLS/SSL 握手。 此動作完成時,主要密碼、加密套件和憑證會分別儲存在用戶端和伺服器的工作階段快取中。
登錄檔路徑:HKLM SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL
EnableOcspStaplingForSni
Online Certificate Status Protocol (OCSP) 裝訂可讓 網路伺服器 (例如 Internet Information Services (IIS)) 在 TLS 握手期間傳送伺服器憑證至使用者端時,提供伺服器憑證的目前撤銷狀態。 此功能可減輕 OCSP 伺服器的負載,因為網路伺服器可以快取伺服器憑證的目前 OCSP 狀態,並將其傳送至多個網路使用者端。 若沒有這項功能,每個網路使用者端都會嘗試從 OCSP 伺服器擷取伺服器憑證的目前 OCSP 狀態。 這會在 OCSP 伺服器上產生高負載。
除了 IIS 之外,透過 http.sys 的網路服務也可以從這項設定中獲益,包括 Active Directory Federation Services (AD FS) 和 Web Application Proxy (WAP)。
依預設,具有簡單安全 (SSL/TLS) 繫結的 IIS 網站會啟用 OCSP 支援。 但是,如果 IIS 網站正在使用下列其中一種型別的 SSL/TLS 繫結,則預設不會啟用這項支援:
- 需要 Servier Name Indication
- 使用集中式憑證存放區
在這種情況下,預設情況為 TLS 握手期間的伺服器問候響應將不包括 OCSP 裝訂狀態。 此行為可改善效能:Windows OCSP 裝訂實作可擴充至數百個伺服器憑證。 但是,Server Name Indication (SNI) 和 Central Certificate Store (CCS) 使 IIS 能夠擴展到可能具有數千個伺服器證書的數千個網站,因此為 CCS 繫結啟用 OCSP 裝訂可能會導致效能問題。
適用版本:所有以 Windows Server 2012 和 Windows 8 開頭的版本。
登錄檔路徑:HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL
新增下列機碼:
"EnableOcspStaplingForSni"=dword:00000001
若要停用,請將 DWORD 值設為0:
"EnableOcspStaplingForSni"=dword:00000000
注意
啟用此登錄檔機碼可能對效能有影響。
雜湊
TLS/SSL 雜湊演算法應該透過設定密碼套件順序來控制。 如需詳細資訊,請參閱設定 TLS Cipher Suite Order。
IssuerCacheSize
此項目控制簽發者快取的大小,並且用於簽發者對應。 SChannel SSP 嘗試對應客戶憑證鏈中的所有發行者,而不只是客戶憑證的直接簽發者。 通常情況下,當簽發者沒有對應到某個帳戶時,伺服器可能會嘗試重複對應同一簽發者名稱,每秒數百次。
為防止這種情況,伺服器具有負快取,因此如果簽發者名稱沒有對應到某個帳戶,該名稱將新增到快取中,在快取項目過期之前,SChannel SSP 不會再次嘗試對應簽發者名稱。 此登錄項目會指定快取大小。 預設情況下,登錄檔中不存在此項目。 預設值是 100。
適用版本:所有以 Windows Server 2008 和 Windows Vista 開頭的版本。
登錄檔路徑:HKLM SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL
IssuerCacheTime
此項目會控制快取逾時間隔的長度 (以毫秒為單位)。 SChannel SSP 嘗試對應客戶憑證鏈中的所有發行者,而不只是客戶憑證的直接簽發者。 如果簽發者沒有對應到一個帳戶 (這是典型情況),伺服器可能會嘗試重複對應相同的簽發者名稱,每秒數百次。
為防止這種情況,伺服器具有負快取,因此如果簽發者名稱沒有對應到某個帳戶,該名稱將新增到快取中,在快取項目過期之前,SChannel SSP 不會再次嘗試對應簽發者名稱。 由於效能原因,保留此快取,因此系統不會繼續嘗試對應相同的簽發者。 預設情況下,此項目不存在登錄檔中。 預設值為 10 分鐘。
適用版本:所有以 Windows Server 2008 和 Windows Vista 開頭的版本。
登錄檔路徑:HKLM SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL
KeyExchangeAlgorithm 機碼大小
依預設,下列項目可能不存在登錄檔中,必須手動建立。 機碼交換演算法的使用應該透過配置密碼套件順序來控制。
新增至 Windows 10、1507 版及 Windows Server 2016。
登錄檔路徑:HKLM\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\KeyExchangeAlgorithms\Diffie-Hellman
若要為 TLS 使用者端指定支援的最小 Diffie-Hellman 機碼位元長度範圍,請建立 ClientMinKeyBitLength 項目。 建立項目之後,請將 DWORD 值變更為所需的位元長度。 如果未設定,則最少需要 1024 位元。
若要指定 TLS 使用者端支援的 Diffie-Hellman 機碼位元長度最大範圍,請建立 ClientMaxKeyBitLength 項目。 建立項目之後,請將 DWORD 值變更為所需的位元長度。
若要指定 TLS 伺服器預設的 Diffie-Hellman 機碼位元長度,請建立 ServerMinKeyBitLength 專案。 建立項目之後,請將 DWORD 值變更為所需的位元長度。 如果未設定,則預設為 2048 位元。
注意
配置的橢圓曲線決定 ECDHE 金鑰交換的加密強度。 請參閱 Manage Transport Layer Security (TLS),了解詳細資訊。
若要深入瞭解 TLS/SSL Cipher Suite 加密演算法,請參閱:
- TLS/SSL 中的 Cipher Suites (SChannel SSP)
- SChannel 揭密 (blog)
MaximumCacheSize
此項目控制快取 TLS 會話的最大數量。 將 MaximumCacheSize 設定為 0,會停用伺服器端工作階段快取,以防止工作階段恢復。 將 MaximumCacheSize 增加至預設值以上,會導致 Lsass.exe 耗用更多記憶體。 每個工作階段快取元素通常需要 2 KB 到 4 KB 的記憶體。 預設情況下,此項目不存在登錄檔中。 預設值為 20,000 個元素。
適用版本:所有以 Windows Server 2008 和 Windows Vista 開頭的版本。
登錄檔路徑:HKLM SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL
訊息 — 片段語法分析
此項目控制將接受 TLS 握手訊息的大小上限。 系統不會接受超過允許大小的訊息,且 TLS 握手將會失敗。 依預設,這些項目不在登錄檔中。
將該值設定為 0x0,則不處理片段訊息,並將導致 TLS 握手失敗。 這使得目前電腦上的 TLS 客戶端或伺服器與 TLS RFC 不相容。
允許的大小上限可以增加到 2^16 個位元組。 允許客戶端或伺服器從網路中讀取和儲存大量未經驗證的資料不是好主意,而且每個安全語境會消耗額外的記憶體。
在 Windows 7 和 Windows Server 2008 R2 中新增:提供可讓 Windows XP、Windows Vista 或 Windows Server 2008 中的 Internet Explorer 解析片段的 TLS/SSL 握手訊息更新。
登錄檔路徑:HKLM\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Messaging
若要指定 TLS 使用者端將接受的分段 TLS 握手訊息允許的大小上限,請建立 MessageLimitClient。 建立項目之後,請將 DWORD 值變更為所需的位元長度。 若未設定,預設值為 0x8000 位元組。
若要指定當沒有使用者端驗證時,TLS 伺服器會接受的片段 TLS 握手訊息允許的大小上限,請建立 MessageLimitServer。 建立項目之後,請將 DWORD 值變更為所需的位元長度。 若未設定,預設值為 0x4000 位元組。
若要指定 TLS 伺服器在有使用者端驗證時會接受的片段 TLS 握手訊息最大允許大小,請建立 MessageLimitServerClientAuth 專案。 建立項目之後,請將 DWORD 值變更為所需的位元長度。 若未設定,預設值為 0x8000 位元組。
SendTrustedIssuerList
TLS 伺服器可以在請求客戶端身份驗證時傳送可接受的憑證機構分辨名稱清單。 這可以幫助 TLS 客戶端選擇適當的 TLS 客戶端憑證。 預設情況下,基於 SChannel 的 TLS 伺服器不會傳送此受信任簽發者清單,因為會向被動觀察者公開伺服器受信任的憑證機構,並且還增加在 TLS 握手過程中交換的資料量。 將此值設定為 1,會導致 SChannel 伺服器傳送其受信任的簽發者清單。
當客戶要求客戶憑證時,不傳送受信任簽發者清單可能會影響客戶傳送的內容。 例如,當 Internet Explorer 收到用戶端驗證的要求時,它只會顯示鏈結至伺服器所傳送的其中一個憑證授權單位的用戶端憑證。 如果伺服器未傳送清單,Internet Explorer 會顯示安裝在使用者端上的所有使用者端憑證。
此行為可能不妥當。 例如,當 PKI 環境中包含交叉憑證時,使用者端和伺服器憑證將不會有相同的根 CA;因此,Internet Explorer 無法選擇鏈結至其中一個伺服器 CA 的憑證。 TLS 客戶端可以在伺服器未傳送受信任簽發者清單時提供任何可用的客戶端憑證。 預設情況下,此項目不存在登錄檔中。
Default Send Trusted Issuer List behavior
| Windows 版本 | 預設行為 |
|---|---|
| Windows Server 2012、Windows 8 及更新版本 | FALSE |
| Windows Server 2008 R2、Windows 7 及更早版本 | TRUE |
適用版本:所有以 Windows Server 2008 和 Windows Vista 開頭的版本。
登錄檔路徑:HKLM SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL
ServerCacheTime
此專案指定伺服器 TLS 工作階段快取項目留存期 (以毫秒為單位)。 預設為 10 小時。 值 0,將關閉伺服器上的 TLS 會話快取,並防止會話恢復。 將 ServerCacheTime 增加至預設值以上,會導致 Lsass.exe 耗用更多記憶體。 每個工作階段快取元素通常需要 2 KB 至 4 KB 的記憶體。 預設情況下,此項目不存在登錄檔中。
適用版本:所有以 Windows Server 2008 和 Windows Vista 開頭的版本。
登錄檔路徑:HKLM SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL
預設伺服器快取時間:10 小時
TLS、DTLS 和 SSL 協定版本設定
SChannel SSP 實作 TLS、DTLS 和 SSL 協定的版本。 不同的 Windows 版本支援不同的協定版本。 SSPI 呼叫者可在 AcquireCredentialsHandle 呼叫中指定 SCH_CREDENTIALS 結構,以限制 (但無法展開) 全系統可用的 (D)TLS 和 SSL 版本集。 建議 SSPI 呼叫者使用系統預設值,而不是強制使用協定版本限制。
支援的 (D)TLS 或 SSL 協定版本可以存在於下列其中一種狀態:
- 啟用:除非 SSPI 呼叫者使用 SCH_CREDENTIALS 結構明確停用此協定版本,否則 SChannel SSP 可能會與支援的對等端協商此協定版本。
- 停用:SChannel SSP 將不會協商此協定版本,不論 SSPI 呼叫者可能指定的設定為何。
這些登入值分別針對協定使用者端和伺服器角色,在命名為登錄子機碼下,使用下列格式進行設定:
<SSL/TLS/DTLS >主要版本<號碼.次>要版本<號><碼 >Client\Server
您可以在下列登錄檔路徑下建立這些版本特定的子機碼:
HKLM SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols
例如,以下是一些具有版本特定子機碼的有效登錄檔路徑:
HKLM SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 3.0\Client
HKLM SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Server
HKLM SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\DTLS 1.2\Client
若要覆寫系統預設值,並將支援的 (D)TLS 或 SSL 協定版本設定為 Enabled 狀態,請在對應的版本特定子機碼下,建立名為 Enabled 且輸入值為 1 的 DWORD 登入值。
下列範例顯示 TLS 1.0 使用者端設定為 Enabled 狀態:
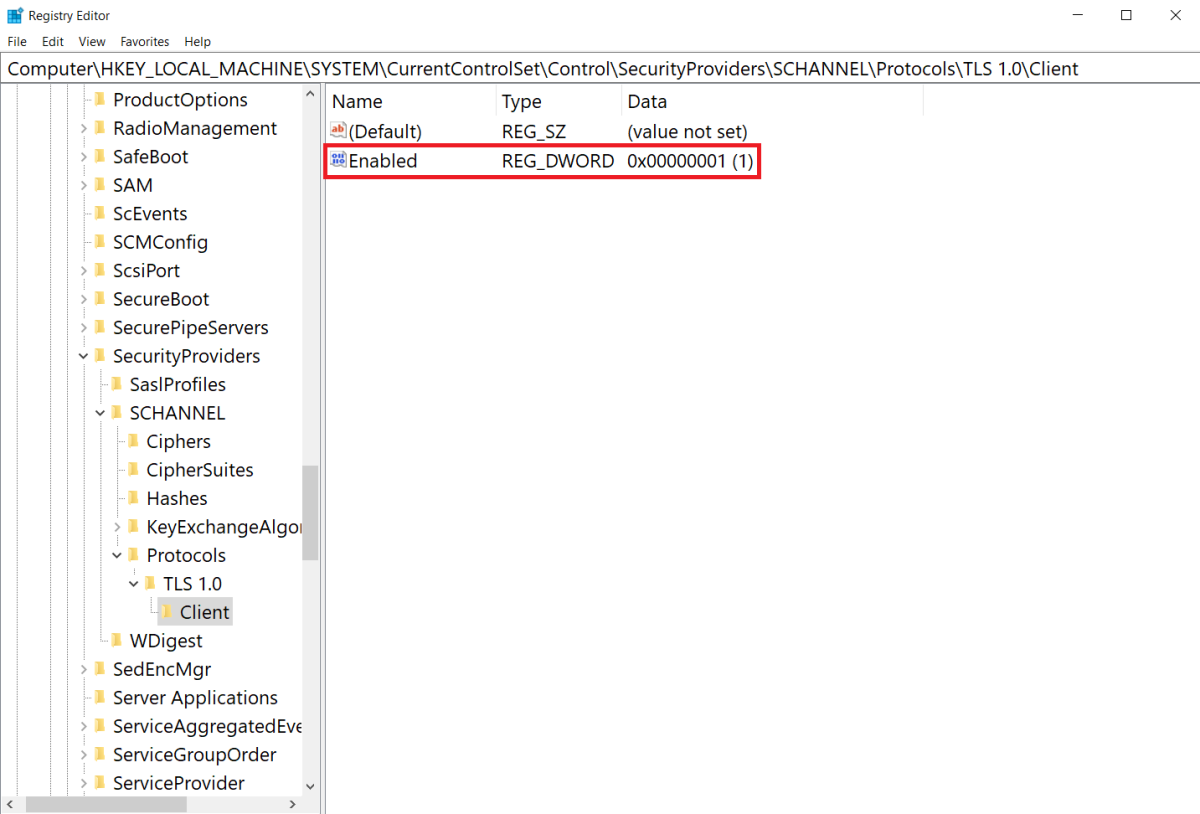
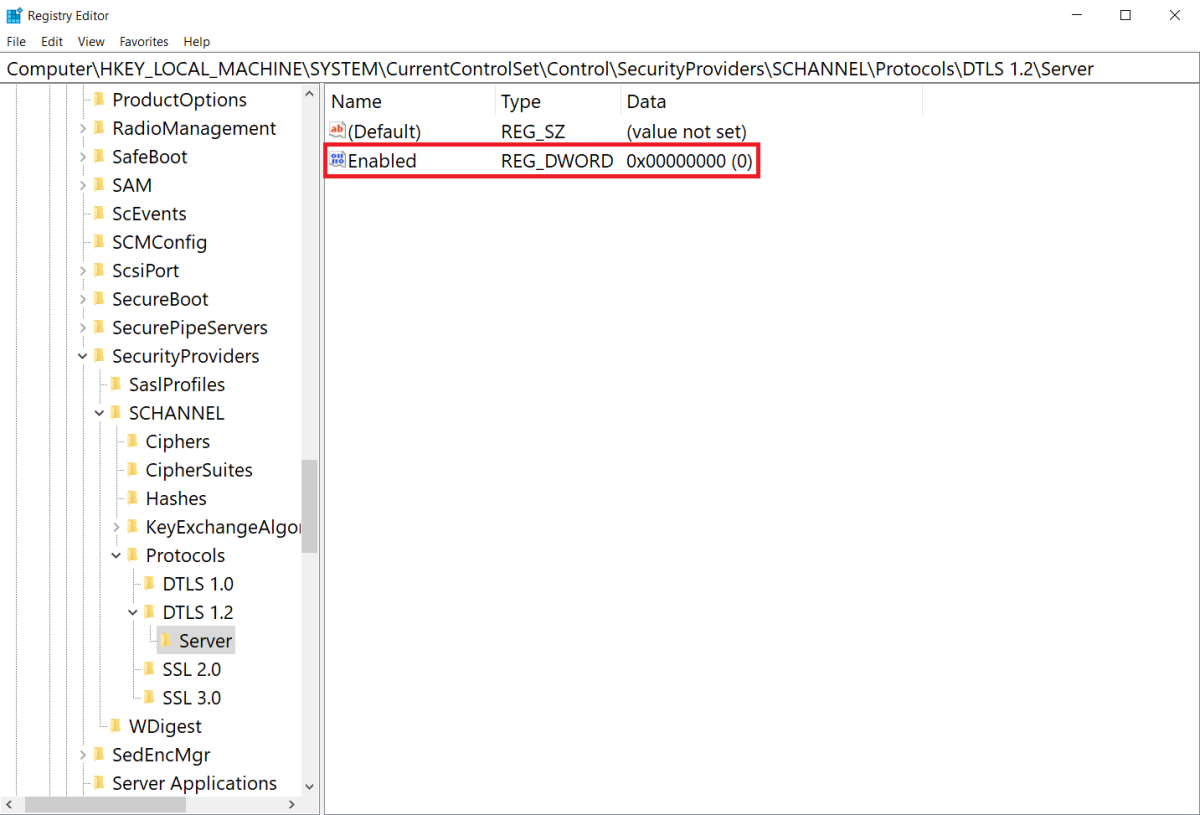
若要覆寫系統預設值,並將支援的 (D)TLS 或 SSL 協定版本設定為 Disabled 狀態,請在對應的版本特定子機碼下,將 DWORD 登錄檔值 Enabled 變更為 0。
下列範例顯示在登錄檔中停用的 DTLS 1.2:
將 (D)TLS 或 SSL 協定版本切換為 Disabled 狀態可能會導致 AcquireCredentialsHandle 呼叫失敗,因為缺少在整個系統範圍內啟用的協定版本以及特定 SSPI 呼叫方允許的同時啟用協定版本。 此外,減少 Enabled (D)TLS 和 SSL 版本集可能會破壞與遠端對等方的互操作性。
修改 (D)TLS 或 SSL 協定版本設定後,將對使用後續 AcquireCredentialsHandle 呼叫開啟的驗證把手建立的連線生效。 (D)TLS 和 SSL 客戶和伺服器應用程式和服務傾向於為多個連線重複使用驗證把手,這是出於效能上的考慮。 為了讓這些應用程式重新取得驗證把手,可能需要重新啟動應用程式或服務。
這些登錄檔設定僅適用於 SChannel SSP,不會影響系統上可能安裝的任何第三方 (D)TLS 和 SSL 實現。