核心 DMA 保護
核心直接記憶體存取 (DMA) 保護是一項 Windows 安全性功能,可防止外部周邊取得未經授權的記憶體存取權。
PcIe Hot plug devices such such as Peripheralbolt, USB4, and CFexpress allow users to attach classes of external peripherals, including graphics card, to their devices with the plug-and play ease of USB. 這些裝置具備 DMA 功能,而且可以存取系統記憶體並執行讀取和寫入作業,而不需要系統處理器的介入。 這項功能是PCI裝置卓越效能背後的原因,但也讓它們容易受到 DMA 驅動攻擊。
「由 DMA 驅動」攻擊是在系統擁有者不存在時發生的攻擊,通常只需要幾分鐘的時間,使用簡單到中度的攻擊工具 (經濟實惠、現成的硬體和軟體) ,而不需要裝置的反組譯碼。 例如,攻擊者可以在裝置擁有者處於中斷狀態時插入類似 USB 的裝置,並離開電腦上的所有秘密,或插入惡意代碼,讓他們在略過鎖定畫面時從遠端完全控制裝置。
注意
核心 DMA 保護功能無法透過 1394/FireWire、PCMCIA、CardBus 或 ExpressCard 來防範 DMA 攻擊。
Windows 如何防範 DMA 磁碟驅動器式攻擊
Windows 會使用系統 輸入/輸出記憶體管理單元 (IOMMU) 來封鎖外部周邊啟動和執行 DMA,除非這些周邊的驅動程式支援記憶體隔離 (例如 DMA 重新對應) 。 具有 DMA 重新對應相容驅動 程式的周邊將會自動列舉、啟動,並允許對其指派的記憶體區域執行 DMA。
根據預設,具有 DMA 重新對應不相容驅動程式的週邊設備將無法啟動和執行 DMA,直到授權的使用者登入系統或解除鎖定畫面為止。 IT 系統管理員可以使用 MDM 或組策略,修改套用至具有 DMA 重新對應不相容驅動程式之裝置的預設行為。
使用者體驗
開啟核心 DMA 保護時:
- 將自動列舉和啟動具有 DMA 重新對應相容設備驅動器的周邊
- 如果在授權的使用者登入之前插入周邊,或螢幕鎖定時,將封鎖具有 DMA 重新對應不相容驅動程式的周邊啟動。 一旦系統解除鎖定,操作系統就會啟動周邊驅動程式,而介面設備會繼續正常運作,直到系統重新啟動,或將周邊解除封鎖為止。 如果使用者鎖定螢幕或註銷系統,周邊會繼續正常運作。
Windows 版本和授權需求
下表列出支援核心直接記憶體存取 (DMA) 保護的 Windows 版本:
| Windows 專業版 | Windows 企業版 | Windows 專業教育版/SE | Windows 教育版 |
|---|---|---|---|
| 是 | 是 | 是 | 是 |
核心直接記憶體存取 (DMA) 保護授權權利由下列授權授與:
| Windows 專業版/專業教育版/SE | Windows 企業版 E3 | Windows 企業版 E5 | Windows 教育版 A3 | Windows 教育版 A5 |
|---|---|---|---|---|
| 是 | 是 | 是 | 是 | 是 |
如需 Windows 授權的詳細資訊,請參閱 Windows 授權概觀。
系統相容性
核心 DMA 保護需要 UEFI 韌體支援,不需要虛擬化型安全性 (VBS) 。
核心 DMA 保護與其他 BitLocker DMA 攻擊的因應措施不相容。 如果系統支援核心 DMA 保護,建議您停用 BitLocker DMA 攻擊的因應措施。 核心 DMA 保護可讓系統透過 BitLocker DMA 攻擊因應措施提供更高的安全性列,同時維持外部外圍設備的可用性。
注意
使用WDDM 3.0 驅動程式模型在 Windows 11 中新增了圖形裝置的 DMA 重新對應支援;Windows 10 不支援此功能。
檢查核心 DMA 保護是否已啟用
支援 Kernel DMA Protection 的系統會自動啟用此功能,而不需要使用者或 IT 系統管理員設定。
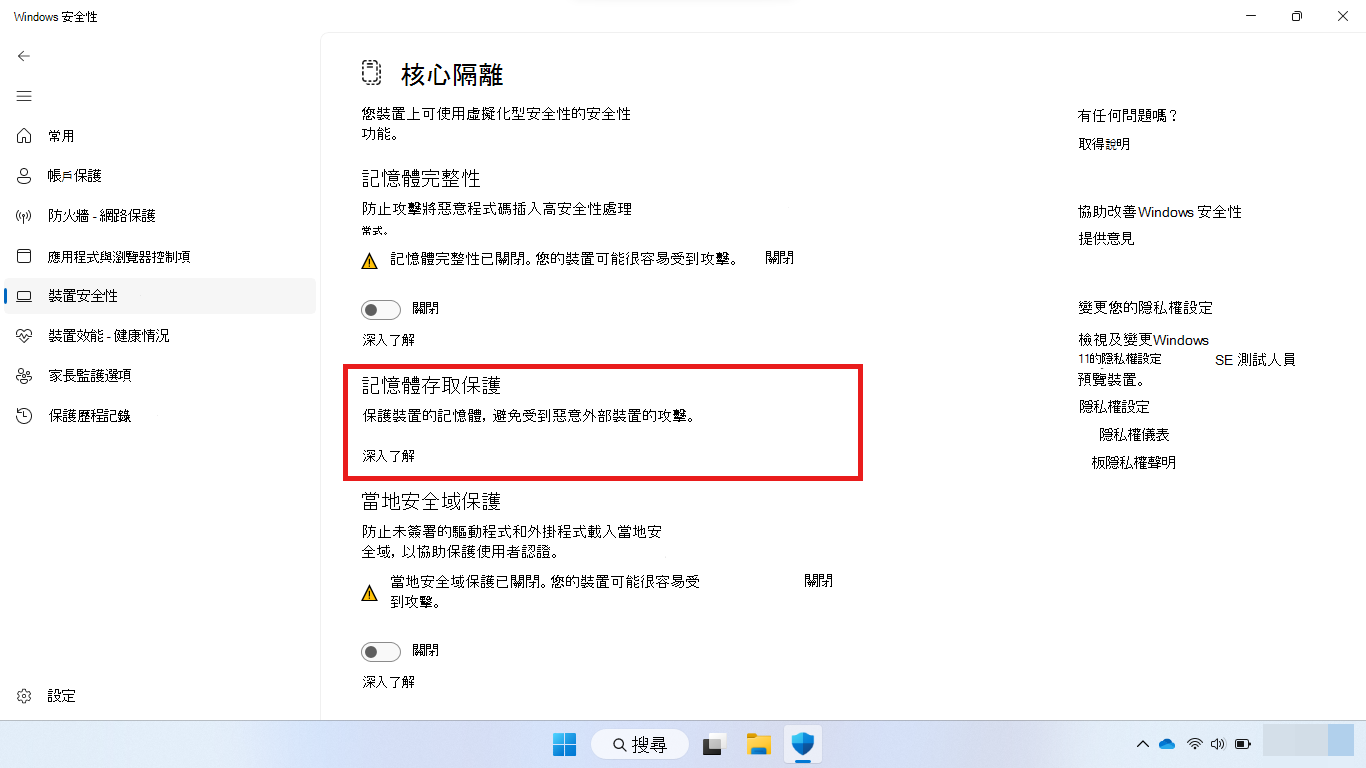
您可以使用 Windows 安全性 設定來檢查是否已啟用 Kernel DMA Protection:
開啟 Windows 安全性。
選 取裝置安全 > 性核心隔離詳細數據 > 記憶體存取保護
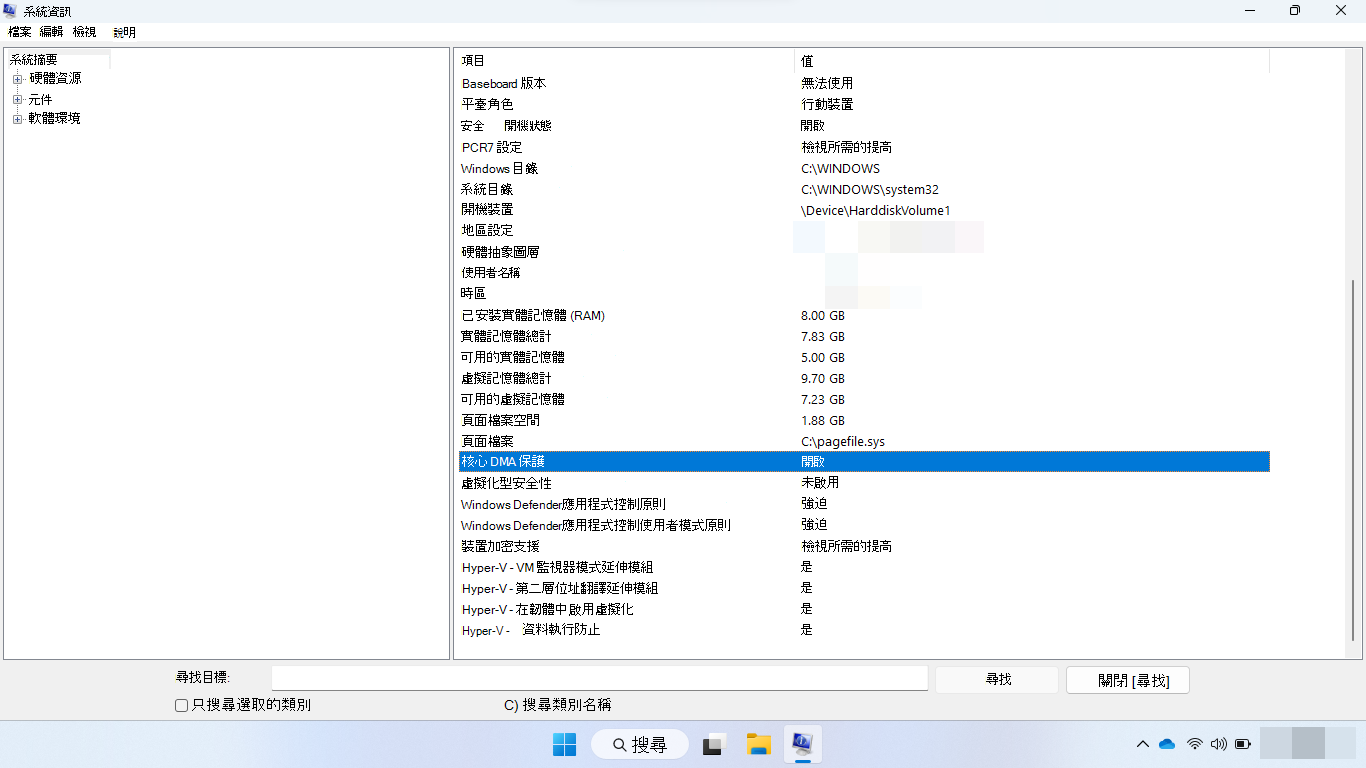
或者,您可以使用系統資訊桌面應用程式 (
msinfo32.exe) 。 如果系統支援 Kernel DMA Protection, 則 Kernel DMA Protection 值會設定為 ON。如果 Kernel DMA Protection 的目前狀態為 OFF ,且 [Hyper-V - 在韌體中啟用虛擬化 ] 為 [否]:
- 重新啟動至 UEFI 設定
- 開啟 Intel 虛擬化技術
- 開啟 Intel Virtualization Technology for I/O (VT-d)
- 將系統重新啟動至 Windows
注意
如果已啟用 Hyper-V Windows 功能,則會隱藏所有 Hyper-V 相關功能,並 偵測到 Hypervisor。Hyper-V 所需的功能將不會顯示 在清單底部。 這表示 [韌體中啟用的 Hyper-V - 虛擬化 ] 設定為 [ 是]。
需要在韌體 (IOMMU) 中啟用 Hyper-V 虛擬化,才能啟用核心 DMA 保護,即使韌體具有 KERnel DMA Protection (適用於 OEM 的記憶體存取保護) 中所述的 ACPI 核心 DMA 保護指標旗標。
如果 Kernel DMA Protection 的狀態維持為 [關閉],則系統不支援 Kernel DMA Protection。
如需不支援核心 DMA 保護的系統,請參閱 BitLocker 因應 措施或 Microsoft Windows 操作系統上的安全性 ,以取得其他 DMA 保護方法。
常見問題集
核心 DMA 保護是否可防止開機期間的磁碟驅動器式 DMA 攻擊?
否,內核 DMA 保護只會在載入作業系統之後,防止受到磁碟驅動器的 DMA 攻擊。 系統韌體/BIOS 負責在開機期間透過Boltbolt 3 埠防範攻擊。
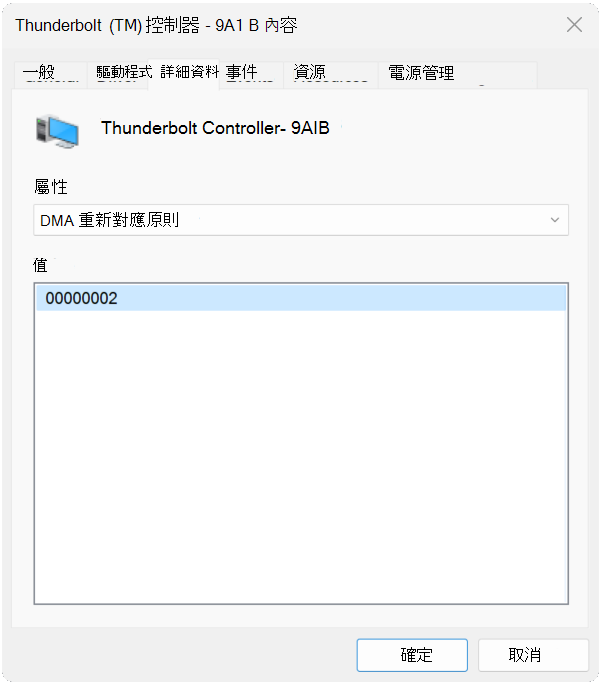
如何檢查特定驅動程式是否支援 DMA 重新對應?
並非所有裝置和驅動程式都支援 DMA 重新對應。 若要檢查特定驅動程式是否選擇加入 DMA 重新對應,請在 裝置管理員*中裝置的 [詳細數據] 索引標籤中,檢查對應至 [DMA 重新對應原則] 屬性的值。 值為 0 或 1 表示裝置驅動器不支援 DMA 重新對應。 值 為 2 表示設備驅動器支援 DMA 重新對應。 如果屬性無法使用,則設備驅動器不支援 DMA 重新對應。 檢查您要測試之裝置的驅動程序實例。 某些驅動程式可能會有不同的值,視裝置在內部與外部) (的位置而定。
當 PCI 或 Bolt 3 週邊設備的驅動程式不支援 DMA 重新對應時?
可用時,請針對周邊使用 Windows 提供的驅動程式。 如果 Windows 未為您的周邊提供任何類別驅動程式,請連絡周邊廠商/驅動程式廠商以更新驅動程式以支援 DMA 重新對應。
我的系統核心 DMA 保護已關閉。 是否可以開啟特定裝置的 DMA 重新對應?
是。 特定裝置的 DMA 重新對應可以與 Kernel DMA Protection 獨立開啟。 例如,如果驅動程式選擇加入,且已開啟適用於導向 I/O) 的 VT-d (Virtualization Technology,則即使已關閉 Kernel DMA Protection,仍會為裝置驅動程式啟用 DMA 重新對應。
核心 DMA 保護是一項原則,可根據裝置的重新對應狀態和功能,允許或封鎖裝置執行 DMA。
Microsoft 驅動程式是否支援 DMA 重新對應?
適用於 USB XHCI (3.x) 控制器、記憶體 AHCI/SATA 控制器和記憶體 NVMe 控制器的 Microsoft 收件匣驅動程式支援 DMA 重新對應。
非 PCI 裝置的驅動程式是否需要與 DMA 重新對應相容?
否。 非 PCI 周邊裝置,例如 USB 裝置,不會執行 DMA,因此不需要讓驅動程式與 DMA 重新對應相容。
企業如何啟用外部裝置列舉原則?
外部裝置列舉原則會控制是否要列舉與 DMA 重新對應不相容的外部周邊。 一律會列舉與 DMA 重新對應相容的周邊。 只有在使用者登入 (預設) 之後,才可以封鎖、允許或允許的介面設備。
您可以使用下列方式來啟用原則:
- 群組原則:外部裝置的系統管理範本\系統\核心 DMA 保護\列舉原則與核心 DMA 保護不相容
- 行動 裝置管理 (MDM) :DmaGuard 原則
意見反應
即將登場:在 2024 年,我們將逐步淘汰 GitHub 問題作為內容的意見反應機制,並將它取代為新的意見反應系統。 如需詳細資訊,請參閱:https://aka.ms/ContentUserFeedback。
提交並檢視相關的意見反應