如何防範網路釣魚攻擊
網路釣魚攻擊會嘗試透過電子郵件、網站、文字訊息或其他形式的電子通訊來竊取敏感性資訊。 他們嘗試看起來像來自合法公司或個人的官方通訊。
網路犯罪者通常會嘗試竊取使用者名稱、密碼、信用卡詳細數據、銀行帳戶資訊或其他認證。 他們會將遭竊的信息用於惡意用途,例如駭客入侵、身分識別竊取,或直接從銀行帳戶和信用卡竊取金錢。 這些資訊也可以在網路犯罪地區市場中銷售。
社交工程攻擊的設計目的是利用用戶在決策制定時可能的失效。 請注意,絕對不要透過電子郵件、未知網站或透過電話提供敏感性或個人資訊。 請記住,網路釣魚電子郵件的設計是要顯示為合法。
了解網路釣魚詐騙的徵兆
最佳保護是認知和教育。 請勿在未經要求的電子郵件中開啟附件或連結,即使電子郵件來自已辨識的來源。 如果電子郵件未預期,請小心開啟附件並確認URL。
企業應該教育並訓練其員工,以防有任何要求個人或財務信息的通訊。 他們也應該指示員工立即向公司的安全性作業小組報告威脅。
以下是網路釣魚詐騙的幾個徵兆:
電子郵件中提供的連結或 URL 未指向正確的位置 ,或指向與電子郵件寄件者無關的第三方網站。 例如,在下圖中提供的 URL 不符合您將前往的 URL。
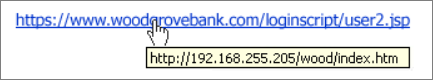
有 個人資訊的要求 ,例如社會安全號碼、銀行或財務資訊。 官方通訊通常不會以電子郵件的形式向您要求個人資訊。
電子郵件位址中的專案將會變更 ,使其類似於合法的電子郵件位址,但已新增數位或變更信件。
訊息未 預期且未經要求。 如果您突然收到來自實體或您很少處理之人員的電子郵件,請考慮此電子郵件有疑問。
訊息或附件會要求您 啟用宏、調整安全性設定,或安裝應用程式。 一般電子郵件不會要求您這麼做。
訊息包含 錯誤。 合法的公司訊息較不可能發生印刷錯誤或文法錯誤,或包含錯誤的資訊。
寄件者位址不符合訊息本身的簽章。 例如,電子郵件是來自 Contoso Corp 的 Mary,但寄件者位址是 john@example.com。
[收件者] 字段中有 多個收件者,而且這些收件者 似乎是隨機位址。 公司訊息通常會直接傳送給個別收件者。
訊息本身的問候語 不會為您個人尋址。 除了誤以為不同人員尋址的訊息之外,誤用您名稱或直接從電子郵件位址提取您名稱的問候語,通常會是惡意的。
網站看起來很熟悉,但有些 不一致或不正確。 警告符號包括過期的標誌、錯字,或要求使用者提供合法登入網站未要求的其他資訊。
開啟的頁面 不是即時頁面,而是設計成類似您所熟悉網站的影像。 可能會出現要求認證的彈出視窗。
如果不確定,請透過已知通道連絡企業,以確認是否有任何可疑的電子郵件確實合法。
組織的軟體解決方案
Microsoft Edge 和 Windows Defender 應用程式防護 使用 Microsoft 領先業界的 Hyper-V 虛擬化技術,提供保護,以防止目標攻擊的威脅日益增加。 如果流覽過的網站被視為不受信任,Hyper-V 容器會將該裝置與網路的其餘部分隔離,以防止存取您的企業數據。
Microsoft Exchange Online 保護 (EOP) 提供企業級的可靠性和防範垃圾郵件和惡意代碼的保護,同時在垃圾郵件期間和之後維持電子郵件的存取權。 使用各種層級的篩選,EOP 可以提供不同的垃圾郵件篩選控件,例如大量郵件控制與國際垃圾郵件,以改善您的保護。
使用 適用於 Office 365 的 Microsoft Defender 來協助保護您的電子郵件、檔案和在線記憶體,以防止惡意代碼。 它提供 Microsoft Teams、Word、Excel、PowerPoint、Visio、SharePoint Online 和 商務用 OneDrive 的整體保護。 藉由防範不安全的附件並擴充對惡意鏈接的保護,可補充 Exchange Online Protection的安全性功能,以提供更好的零時差保護。
如果您是網路釣魚詐騙的犧牲者,該怎麼辦
如果您認為您是網路釣魚攻擊的犧牲者:
- 如果您在工作電腦上,請連絡IT系統管理員
- 立即變更與帳戶相關聯的所有密碼
- 向您的銀行和信用卡公司回報任何詐騙活動
報告垃圾郵件
Outlook.com:如果您收到要求個人資訊的可疑電子郵件訊息,請選取 Outlook 收件匣中郵件旁邊的複選框。 選取 [ 垃圾郵件] 旁的箭號,然後選取 [網络釣魚]。
Microsoft Office Outlook:在可疑訊息中,從功能區選取 [ 報告訊 息],然後選取 [ 網络釣魚]。
Microsoft 365:使用 Microsoft 365 Defender 中的提交入口網站 ,將垃圾郵件或網路釣魚範例提交給 Microsoft 進行分析。 如需詳細資訊,請參閱 如何? 向 Microsoft 回報可疑的電子郵件或檔案?。
防網路釣魚工作組: phishing-report@us-cert.gov。 此群組會使用從傳送的電子郵件產生的報告,以對抗網路釣魚詐騙和駭客。 ISP、安全性廠商、金融機構和執法機關都牽涉到。
如果您在可疑的網站上
Microsoft Edge:當您在可疑的網站上時,請選取 [更多 (...) 圖示>說明和意見反應>報告不安全的網站。 請遵循顯示的網頁上的指示來報告網站。
Internet Explorer:當您在可疑的網站上時,請選取齒輪圖示,指向 [ 安全性],然後選取 [報告不安全的網站]。 請遵循顯示的網頁上的指示來報告網站。
網路釣魚攻擊的詳細資訊
意見反應
即將登場:在 2024 年,我們將逐步淘汰 GitHub 問題作為內容的意見反應機制,並將它取代為新的意見反應系統。 如需詳細資訊,請參閱:https://aka.ms/ContentUserFeedback。
提交並檢視相關的意見反應