憑證簡介
本文討論通用 Windows 平台 (UWP) 應用程式中憑證的使用。 數位憑證用於公開金鑰密碼編譯,將公開金鑰繫結至人員、電腦或組織。 繫結身分識別最常用來對一個實體驗證另一個實體。 例如,憑證經常用來對使用者驗證網頁伺服器以及對網頁伺服器驗證使用者。 您可以建立憑證要求,並安裝或匯入發行的憑證。 您也可以在憑證階層中註冊憑證。
共用憑證儲存
UWP 應用程式使用 Windows 8 中引入的新隔離應用程式模型。 在此模型中,應用程式在稱為應用程式容器的低階作業系統建構中執行,該構造禁止應用程式存取自身外部的資源或文件,除非明確允許這樣做。 以下部分描述了這對公鑰基礎設施 (PKI) 的影響。
每個應用程式容器的憑證儲存
打算在特定應用程式容器中使用的憑證儲存在每個使用者、每個應用程式容器位置。 在應用程式容器中執行的應用程式僅具有對其自己的憑證儲存的寫入存取權。 如果應用程式將憑證新增至其任何儲存體中,則其他應用程式無法讀取這些憑證。 如果卸載應用程式,則特定於該應用程式的任何憑證也會被刪除。 應用程式還具有對 MY 和 REQUEST 儲存之外的本機電腦憑證儲存的讀取存取權限。
Cache
每個應用程式容器都有一個獨立的緩存,可在其中儲存驗證所需的頒發者憑證、憑證撤銷清單 (CRL) 和線上憑證狀態協定 (OCSP) 回應。
共用憑證和金鑰
當智慧卡插入讀卡機時,卡上包含的憑證和金鑰將傳播到使用者的「我的」儲存,使用者正在執行的任何完全信任的應用程式都可以共用它們。 但是,預設情況下,應用程式容器無權存取每個使用者的「我的商店」。
為了解決此問題,並使主體組能夠存取資源組,應用程式容器隔離模型支援功能概念。 此功能允許應用程式容器程序存取特定資源。 SharedUserCertificates 功能可授予應用程式容器對使用者「我的」儲存和智慧卡可信任根儲存中包含的憑證和金鑰的讀取存取權。 此功能不會授予對使用者 REQUEST 儲存的讀取存取權限。
您可以在清單中指定sharedUserCertificates 功能,如下例所示。
<Capabilities>
<Capability Name="sharedUserCertificates" />
</Capabilities>
憑證欄位
X.509 公鑰憑證標準隨著時間的推移進行了修訂。 資料結構的每個後續版本都保留了先前版本中存在的欄位,並新增了更多欄位,如下圖所示。
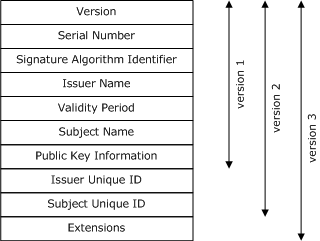
當您使用 CertificateRequestProperties 類別建立憑證要求時,可以直接指定這些欄位和延伸模組。 大多數不能。 這些欄位可以由發行機構填寫,也可以留空。 關於欄位的更多資訊,請參閱以下部分:
版本 1 欄位
| 欄位 | 描述 |
|---|---|
| 版本 | 指定編碼憑證的版本編號。 目前,該欄位的可能值為 0、1 或 2。 |
| 序號 | 包含由憑證授權單位 (CA) 指派給憑證的唯一正整數。 |
| 簽章演算法 | 包含指定 CA 用於簽署憑證的演算法的物件識別碼 (OID)。 例如,1.2.840.113549.1.1.5 指定 SHA-1 雜湊演算法與 RSA 實驗室的 RSA 加密演算法結合。 |
| Issuer | 包含建立並簽署憑證的 CA 的 X.500 可分辨名稱 (DN)。 |
| 有效期 | 指定憑證有效的時間間隔。 截至 2049 年底的日期使用協調世界時 (格林威治標準時間) 格式 (yymmddhhmmssz)。 從 2050 年 1 月 1 日開始的日期使用通用時間格式 (yyyymmddhhmmssz)。 |
| 主旨 | 包含與憑證中包含的公鑰關聯的實體的 X.500 可分辨名稱。 |
| 公開金鑰 | 包含公鑰和相關演算法資訊。 |
版本 2 欄位
X.509 版本 2 憑證包含版本 1 中定義的基本欄位,並新增下列欄位。
| 欄位 | 描述 |
|---|---|
| 發行人唯一識別碼 | 包含一個唯一值,可用於使 CA 的 X.500 名稱在被不同實體隨時間重複使用時明確。 |
| 主題唯一識別碼 | 包含一個唯一值,可用於使憑證主體的 X.500 名稱在被不同實體隨時間重複使用時明確。 |
版本 3 擴充
X.509 版本 3 憑證包含版本 1 和版本 2 中定義的欄位,並新增憑證擴充功能。
| 欄位 | 描述 |
|---|---|
| 授權單位金鑰識別元 | 標識與用於簽署憑證的 CA 私鑰相對應的憑證授權單位 (CA) 公鑰。 |
| 基本限制 | 指定該實體是否可以用作 CA,如果可以,則指定憑證鏈中該實體下方可以存在的從屬 CA 的數量。 |
| 憑證原則 | 指定頒發憑證所依據的策略及其使用目的。 |
| CRL 發佈點 | 包含基礎憑證撤銷清單 (CRL) 的 URI。 |
| 增強金鑰使用方法 | 指定憑證中包含的公鑰的使用方式。 |
| 發行人替代名稱 | 為憑證要求的發行者指定一種或多種備用名稱形式。 |
| 金鑰使用方法 | 指定對憑證中包含的公鑰可以執行的操作的限制。 |
| 名稱限制 | 指定憑證層次結構中的所有使用者名稱必須位於的命名空間。 該副檔名僅在 CA 憑證中使用。 |
| 政策限制 | 透過禁止策略對應或要求層次結構中的每個憑證都包含可接受的策略標識符來限制路徑驗證。 該副檔名僅在 CA 憑證中使用。 |
| 原則對應 | 指定從屬 CA 中與頒發 CA 中的策略相對應的原則。 |
| 私鑰使用期限 | 為私鑰指定與私鑰關聯的憑證不同的有效期限。 |
| 主體別名 | 為憑證要求的主題指定一種或多種替代名稱形式。 範例替代形式包括電子郵件地址、DNS 名稱、IP 位址和 URI。 |
| 主題目錄屬性 | 傳達身分屬性,例如憑證主體的國籍。 擴展值是一系列 OID 值對。 |
| 主體金鑰識別碼 | 區分憑證主體持有的多個公鑰。 擴充值通常是金鑰的 SHA-1 雜湊值。 |
意見反應
即將登場:在 2024 年,我們將逐步淘汰 GitHub 問題作為內容的意見反應機制,並將它取代為新的意見反應系統。 如需詳細資訊,請參閱:https://aka.ms/ContentUserFeedback。
提交並檢視相關的意見反應