Hello,
Thank you so much for your feedback.
So glad to hear that the advanced audit settings started working when they were shifted to Default Domain Policy. If we did the settings on a separate GPO, it would still be applied. Below is my test, and we could kindly have a check.
1, Created the OU (such as OU for computers) and added the computers into this OU.
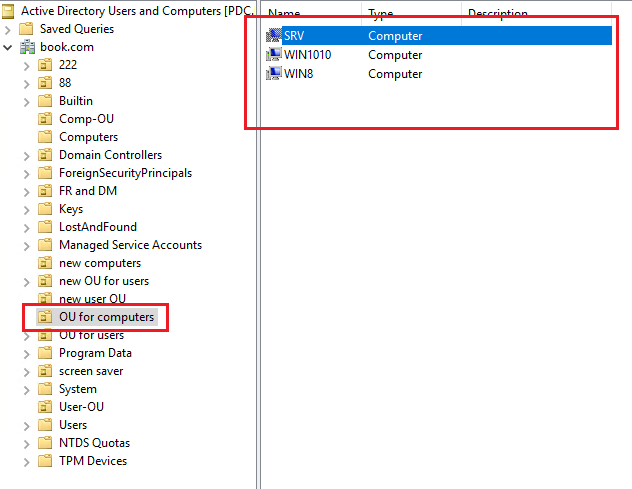
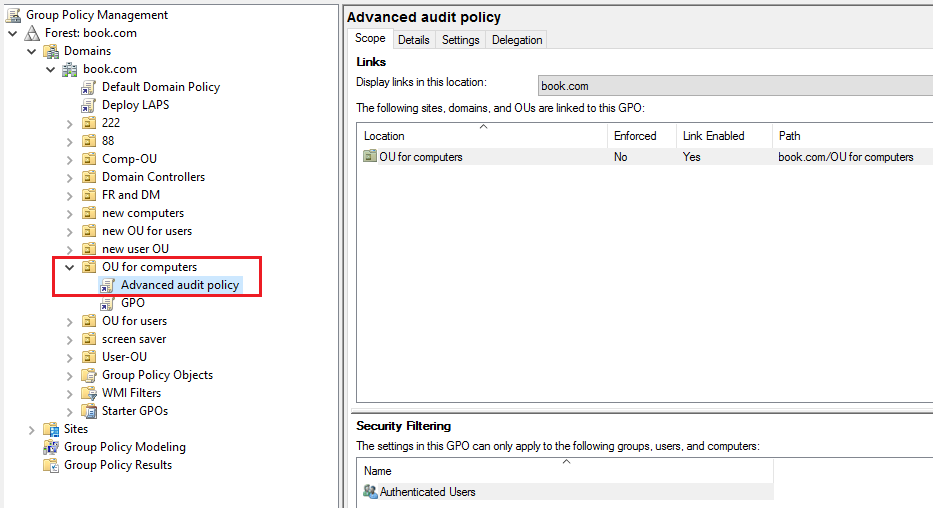
2, Created a GPO and linked to the above OU (The GPO was named Advanced audit policy).
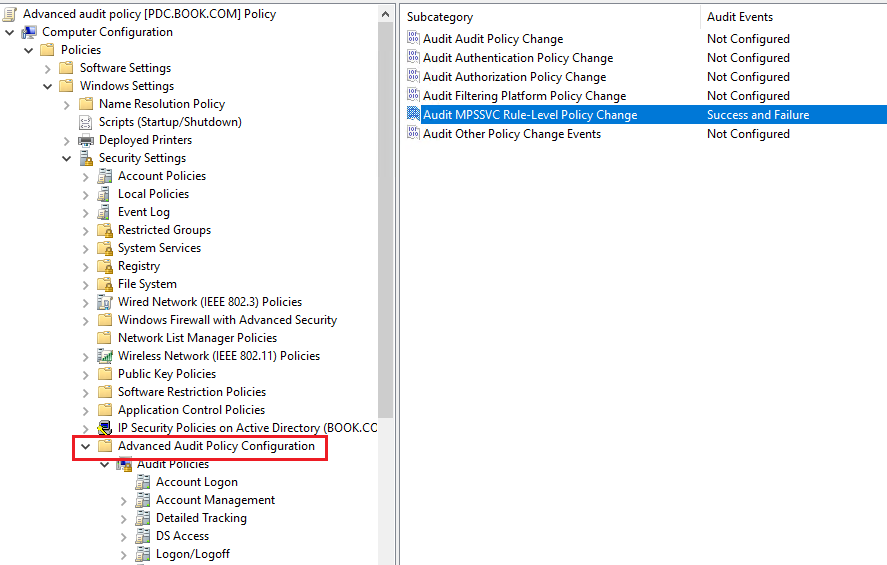
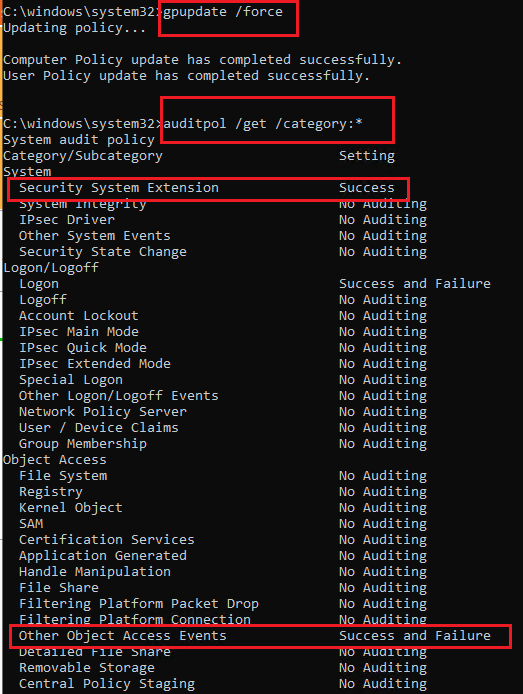
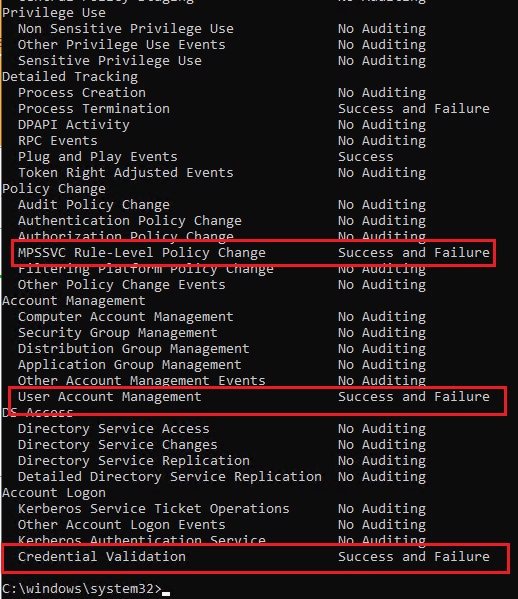
3, Edited the GPO and configured the settings, such as Audit Credential Validation set to Success and Failure, Audit Security System Extension set to success.
4, Logged on to the computer and refresh the group policy via command gpupdate /force.
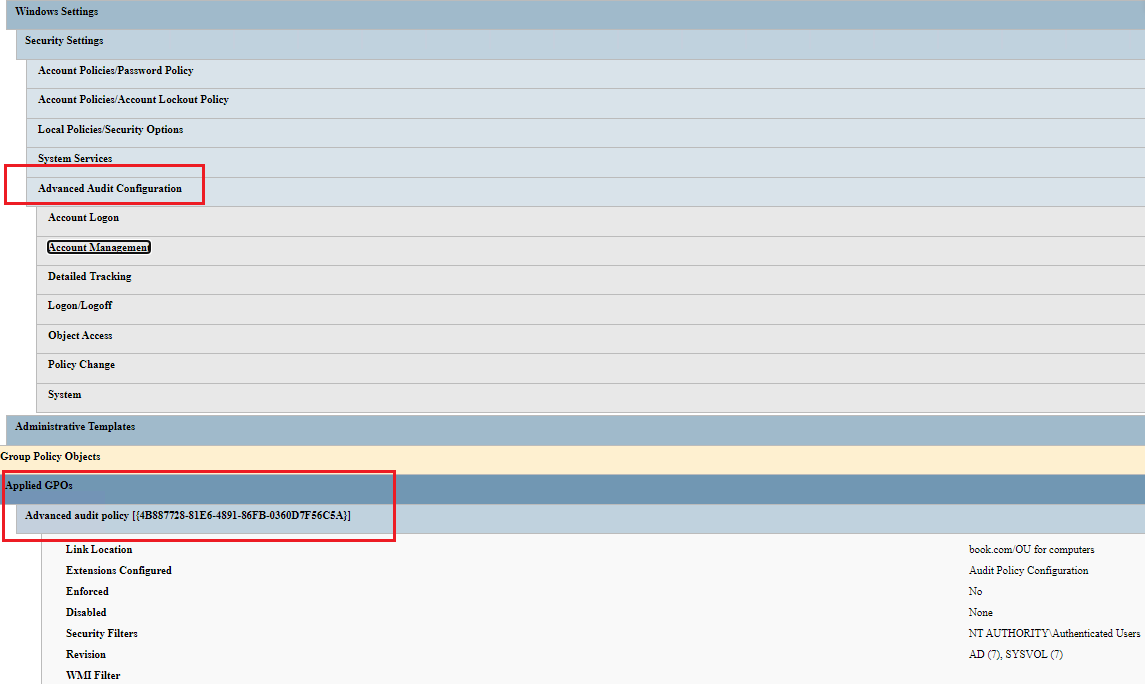
5, Checked the gpresult that the GPO was applied successfully.
6, Then check the audit policy via command auditpol /get /category:* and we could see that the settings were applied.
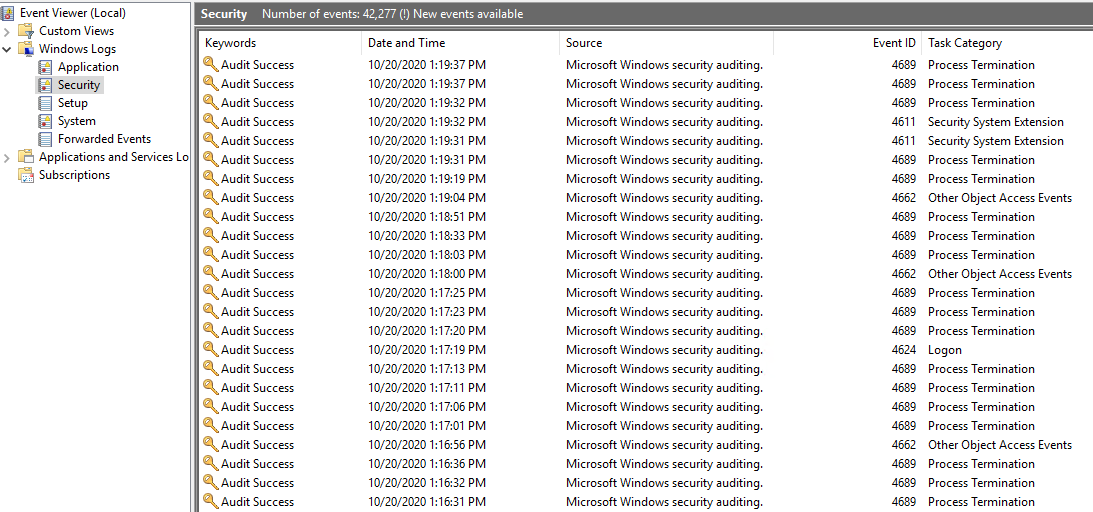
7, Last check the Event Viewer, and we could see that some events were logged.
Hope the information is helpful. Thank you so much for your time.
Best regards,
Hannah Xiong







