Hi @LouisWaweru ,
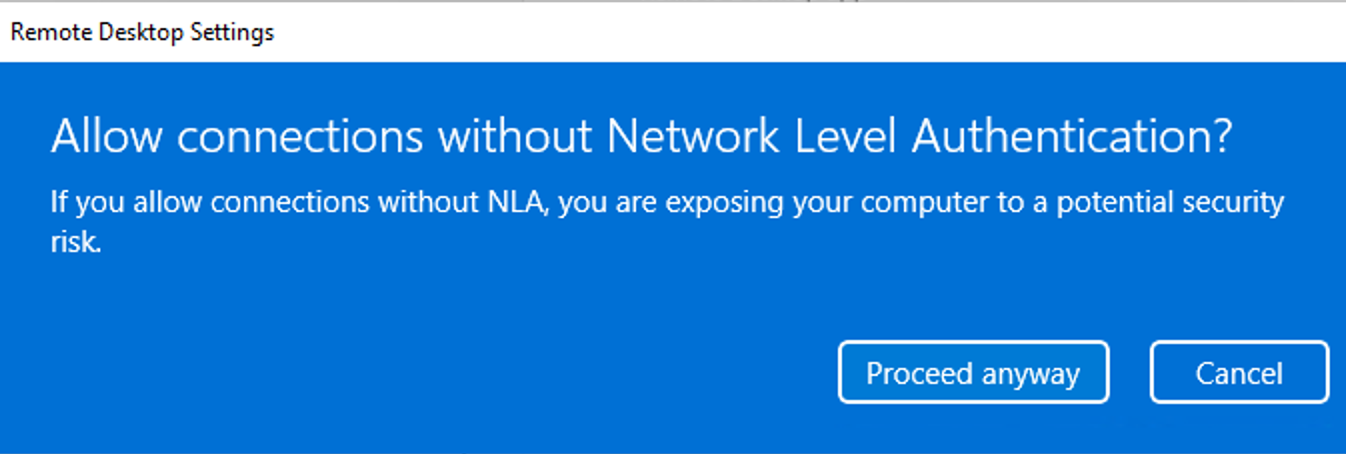
We do support NLA to RDP into AAD joined machines. We recommend to turning off the Remote Credential Guard to make sure this works.
Since the machine is domain joined, please ensure that PKU2U is enabled (the default is "disabled") with NLA.
NLA basically authenticates against the DC before authorizing to the local machine so if there is no communication between the VMs and the DC--whether they are not domain joined, the DC is down, or there is no network connectivity--it will throw an NLA error.
You can temporarily disable NLA using the run command option automatically from the Azure portal > run command > disable NLA. Then attempt to RDP using local admin credentials and investigate further. Check domain join > check DNS > ping DC > etc. Then you can re-enable NLA when you are done:
You can also run Diagnostics to get the exact error message for the user:
$activities = Get-RdsDiagnosticActivities -TenantName <tenantName> -ActivityType Connection -Outcome Failure -Detailed
(See related.)
If you've configured Password Hash Sync then your users should already have their password hashes stored in the right format. But I'll also note that the password hashes need to be stored in a format that is suitable for NTLM, and if the passwords are not stored in that format, you need to let those users change their passwords in order to force the right password hash format.
Let me know if these steps help.
-
If this answer was helpful to you, please remember to "mark as answer" so that others in the community with similar questions can more easily find a solution.