Exercise - Enable JIT VM access
You need to have the enhanced security features of Microsoft Defender for Cloud to use this feature. After you activate a trial or enable enhanced security on your subscription, you can enable Just-in-time (JIT) virtual machine (VM) access for selected Azure virtual machines (VMs) in the subscription. If you don't want to start a trial now, you can read through the following instructions to see the required steps.
Create a new VM
Let's start by creating a virtual machine using Azure Cloud Shell.
Note
This exercise can't be performed in the Azure Sandbox. Make sure to select a subscription that has enhanced security features enabled for Defender for Cloud.
Sign in to the Azure portal.
Select the Cloud Shell icon from the top right of the Azure portal toolbar. Cloud Shell appears at the bottom of the portal.
Start by setting some default values, so you don't have to enter them multiple times.
Set a default location. Here, we use eastus, but feel free to change that to a location closer to you.
az configure --defaults location=eastusTip
You can use the Copy button to copy commands to the clipboard. To paste, right-click on a new line in the Cloud Shell terminal and select Paste, or use the Shift+Insert keyboard shortcut (⌘+V on macOS).
Next, create a new Azure resource group to hold your VM resources. We used the name
mslearnDeleteMehere to remind ourselves to delete this group when we're finished.az group create --name mslearnDeleteMe --location eastusGo ahead and set
mslearnDeleteMeas the default resource group.az configure --defaults group="mslearnDeleteMe"Next, run the following command to create a new Windows-based VM. Make sure to replace the
<your-password-here>value with your own valid password.az vm create \ --name SRVDC01 \ --image win2019datacenter \ --resource-group mslearnDeleteMe \ --admin-username azureuser \ --admin-password <your-password-here>It takes a few minutes to create the VM and supporting resources. You should get a response similar to the following example.
{ "fqdns": "", "id": "/subscriptions/abcd/resourceGroups/mslearnDeleteMe/providers/Microsoft.Compute/virtualMachines/SRVDC01", "location": "eastus", "macAddress": "00-00-00-00-00-00", "powerState": "VM running", "privateIpAddress": "10.1.0.4", "publicIpAddress": "52.123.123.123", "resourceGroup": "mslearnDeleteMe", "zones": "" }To connect to the VM using Remote Desktop (RDP), use the public IP address in the response. Windows has a built-in RDP client. If you use a different client system, there are clients available for macOS and Linux.
You can connect and administer the VM. Let's add JIT for security!
Enable JIT VM access in Defender for Cloud
On the home page of the Azure portal in the top search bar, search for and select Microsoft Defender for Cloud. The Overview pane for Microsoft Defender for Cloud appears.
In the left menu pane, under Cloud Security, select Workload protections. The Workload protections pane displays.
In the main window, scroll down to Advanced protection. select Just-in-time VM access. The Just-in-time VM access pane appears.
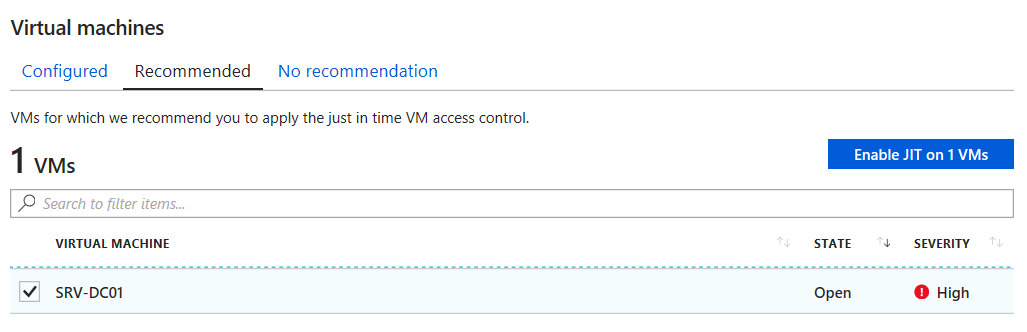
Under Virtual machines, select the Not Configured tab.
Select the virtual machine from the resource group, MSLEARNDELETEME.
Select Enable JIT on 1 VM with your selected VM, as shown in the following screenshot.
The JIT VM access configuration pane appears for your VM. After you enable the JIT rules, you can examine the Network Security Group for the VM. It has a new set of rules applied to block remote management access, as shown in the following image.

Notice that the rules are applied to the internal address, and all management ports are included - both Remote Desktop Protocol (3389) and SSH (22).
On the top menu bar, select Save. The Just-in-time VM access pane reappears.
Request Remote Desktop Access
If you try to RDP into the Windows VM at this point, access is blocked. When your admin needs access, they can come into Defender for Cloud to request access.
Under Virtual machines, select the Configured tab.
Select your VM, and then select Request access to open up the management ports.

The Request access pane appears for SRVD01.
Select the ports you want to open; in this case, the Remote Desktop port (3389).

Select Open ports to finalize the request. You can set the number of hours to keep the port open from this pane as well. After the time expires, the port is closed, and access is denied.
Now, your Remote Desktop client can connect successfully - at least for the time period that you allotted through Defender for Cloud.