Running Windows Server 2019. In the early morning of Sept 16, 2021 this update auto-installed and restarted the server (September 14, 2021—KB5005568). Now, the event noted below has began to appear anytime a user signs in to their computer. None of our users use Smartcards, but we do run hybrid Azure AD with Windows Hello for Business enabled. Doesn't seem to be causing any issues, but I'd still like to know what the underlying issue is and correct it.
Any ideas?
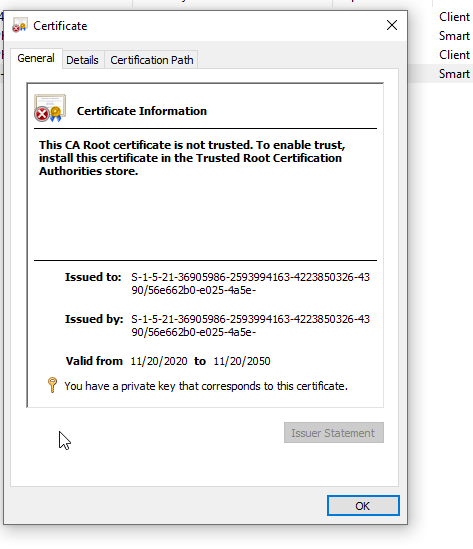
Kerberos-Key-Distribution-Center
The client certificate for the user "DOMAIN\user" is not valid, and resulted in a failed smartcard logon. Please contact the user for more information about the certificate they're attempting to use for smartcard logon. The chain status was : A certificate chain processed, but terminated in a root certificate which is not trusted by the trust provider.