Confirmed, no joy, still seeing errors. I still think it's related to Secure Hardware Key which we don't use.
"The client certificate for the user "DOMAIN\user" is not valid, and resulted in a failed smartcard logon" after KB5005568 update.
Running Windows Server 2019. In the early morning of Sept 16, 2021 this update auto-installed and restarted the server (September 14, 2021—KB5005568). Now, the event noted below has began to appear anytime a user signs in to their computer. None of our users use Smartcards, but we do run hybrid Azure AD with Windows Hello for Business enabled. Doesn't seem to be causing any issues, but I'd still like to know what the underlying issue is and correct it.
Any ideas?
Kerberos-Key-Distribution-Center
The client certificate for the user "DOMAIN\user" is not valid, and resulted in a failed smartcard logon. Please contact the user for more information about the certificate they're attempting to use for smartcard logon. The chain status was : A certificate chain processed, but terminated in a root certificate which is not trusted by the trust provider.
17 answers
Sort by: Most helpful
-
-
Doug Tran 6 Reputation points
2021-11-18T19:35:43.167+00:00 For users seeing this issue:
- Do you have Password-less FIDO2 Security enabled?
- If you do, do you see this error if you logged in with a Security Key vs a Password?
- Do you see this error if you log into a Windows Servers vs Windows 10?
If so, look at this these two pages:
For myself, I enabled FIDO2 back in Feburary 2021. I do not see this event when logging in with a Security Key. I do not see this event when logging into a Windows Server via password.
-Doug
-
Anonymous
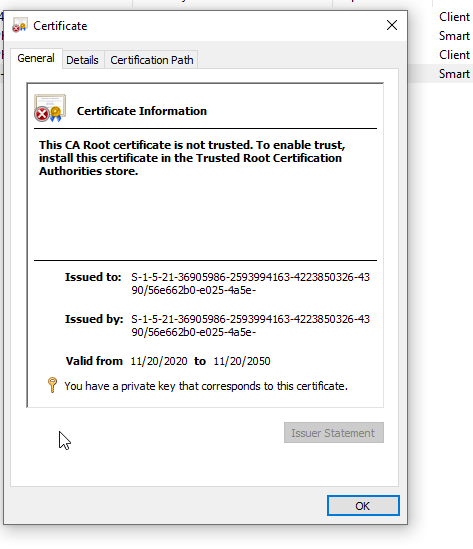
2021-11-24T14:31:49.68+00:00 Hey everyone, I have the same issue but we use AADJ devices. Furthermore we see in CAPI2 log:
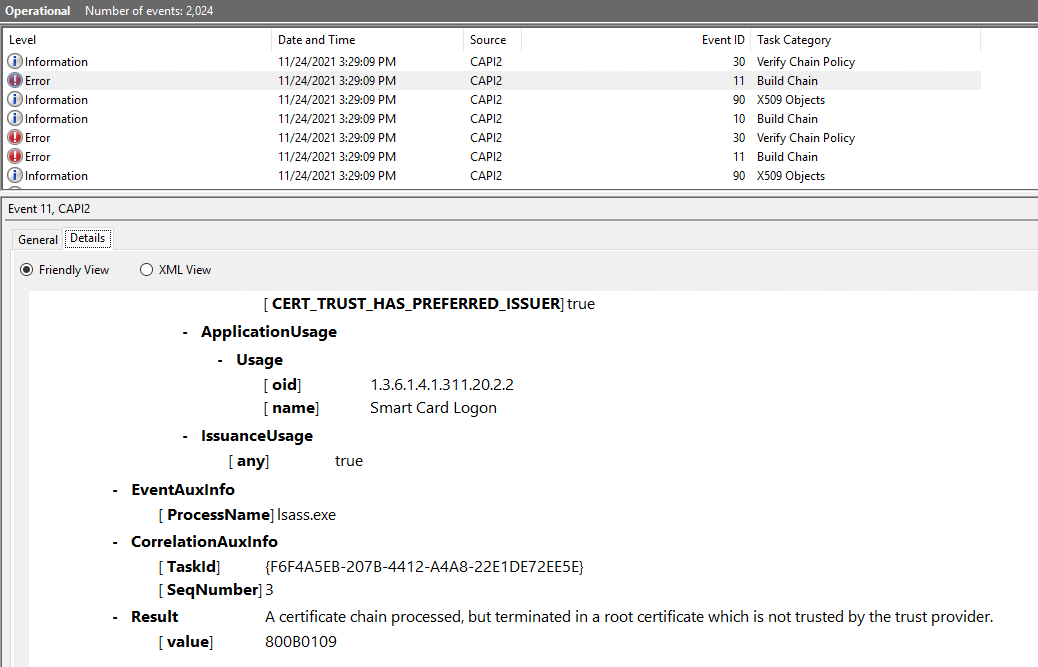
Subject name is:

Do you have an idea what is wrong?
Best regards
-
Shaunm001 301 Reputation points
2022-01-11T15:26:06.457+00:00 It's definitely Windows Hello for Business related, we started seeing these error messages as soon as we began implementing WHfB (Hybrid Azure AD Key-Trust deployment) a couple months ago. It does seem to drop this self-signed certificate onto every machine where a user has enabled WHfB. WHfB is functioning normally for everyone, not sure if this is just one of those "by-design" errors you can safely ignore or if we botched the rollout at some point.
I tried deleting the cert and rebooting and was still able to sign in using my WHfB PIN. I checked certificates again after logging back in and saw that a new self-signed cert had been added back in. I next tried moving the cert into the Trusted Root store, rebooted and signed back in. When I checked certificates again, it had once more added the self-signed cert back into the personal store. This time it didnt show any errors about being untrusted, but I still got a Kerberos KDC event 21 error on the domain controller for that sign in. Not sure what to do at this point, other than ignore these errors...?
-
Mads Brodersen Toustrup 1 Reputation point
2022-04-12T12:34:47.003+00:00 Did anyone find a solution for this, or did you choose to ignore the warning messages?
I can confirm that everything works fine - but as more and more users start using WHfB this will flood the logs ... :-)