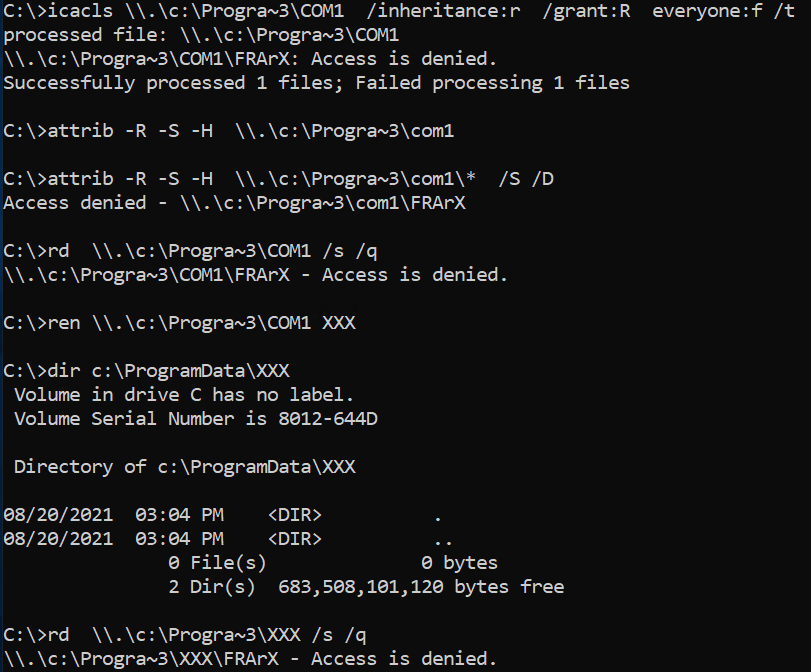
Hackers attacked a Windows Server 2019, and in the process put a folder called COM1 on Drive C. I have made a number of attempts to delete this folder. Unfortunately, COM1 is a reserved name. Here is what I have tried and have failed.
I took ownership of the folder back to the Administrators group, which I was able to do. However, it did not allow the folder removal process through File Explorer.
Then I tried removing the directory from a DOS prompt.
rmdir \?\<x>:\<path_to_folder>\<COM1>
Result: "Access denied".
Then i tried renaming the folder.
ren "\.\C:\<path to folder>\COM1 TEMP
Result: "Access denied".
File Explorer shows the folder is shared, but if go to Advanced Options, it does not show up as a Share. It also does not show up
as a shared folder in Computer Management.
I tried running the attrib command from a DOS prompt. It will display the attributes of the folder, (only Archive shows). Trying to set attributes results in,
Path not found - \.\com1\
I am running out of ideas. Any help would be appreciated.