L2TP/IPsec Client Access VPN with Pre-shared key is not working in TMG
Recently I worked on an issue where the L2TP/IPSec Client Access VPN was not working through TMG. The TMG was configured to use Pre-Shared key for the IPsec policy but the VPN clients were unable to establish the session with the TMG server.
In the Event viewer we, got the below error
The following error occurred in the Point to Point Protocol module on port: VPN2-220, UserName: testuser@xxx.com. The connection was prevented because of a policy configured on your RAS/VPN server. Specifically, the authentication method used by the server to verify your username and password may not match the authentication method configured in your connection profile. Please contact the Administrator of the RAS server and notify them of this error.
We verified all the configuration on the TMG and client machines but couldn’t find anything wrong. Then we collected the ikee traces from the TMG server and found the below interesting entry in the log.
5020 Auth methods: 1
5021 -- 0 --
5022 Type: Certificate
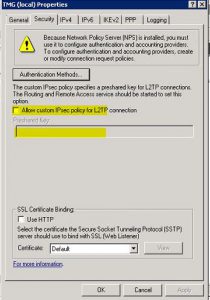
The Type was showing as Certificate instead of Pre-Shared key. Further checking in the RRAS settings, we found that the TMG was unable to save the Pre-Shared key in the RRAS configuration. In RRAS settings, the Pre-shared key was not even showing as enabled.
So we investigated further by collecting various trace logs and finally figured out the TMG server had the below registry key enabled.
HKLM\System\CurrentControlSet\services\RasMan\Parameters\DisableSavePassword
The value for the DisableSavePassword was set to 1 and this was preventing TMG from saving the Pre-shared key. After disabling this registry setting, the TMG was able to configure the Pre-shared key in the RRAS and VPN clients were able to connect successfully.
Author:
ANIL GEORGE
Microsoft Security Support Escalation Engineer
Reviewer:
KARTHIK DIVAKARAN
Microsoft Windows Escalation Engineer