Multiple Active Directory forest support in IPAM
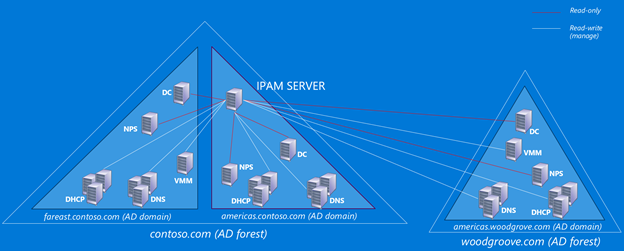
In Windows Server 2016, IPAM will support multiple AD forest deployments. You will now be able to manage DNS and DHCP servers spanning across different Active Directory forests through a single instance of IPAM, provided they have 2-way trust relationship with the AD forest the IPAM server belongs to. IPAM provides the same set of management features for these servers irrespective of the AD forest they belong to. This will enable admins to view and manage their DDI (DNS, DHCP, IP address) infrastructure across the AD forests through a single console.
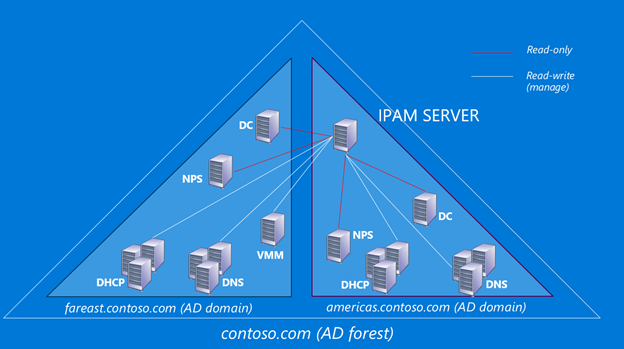
In Windows Server 2102 R2, IPAM was able to manage the DNS, DHCP and DC servers of the forest IPAM was part of. In a typical IPAM deployment, it is able to manage DNS and DHCP servers belonging to different domains of the same AD forest. It is also able to get domain information from the Domain Controllers and user audit data from NPS servers. In virtualized environments, IPAM is also able to sync with the SCVMM servers to get virtualized network data.
In Windows Server 2016, IPAM’s management boundary will be expanded to the servers which are part of a different AD forest that has 2-way trust relationship with the forest IPAM server is part of. It will be able to communicate with DNS, DHCP, NPS, DC and SCVMM servers in the same way as if they belonged to the same forest.
How it works:
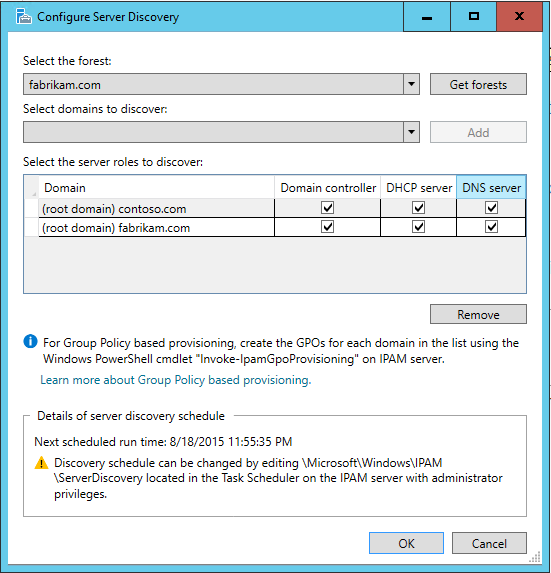
To begin discovering servers from different AD forest, click Configure server discovery in the IPAM client console and click Get forests. It will launch a background task which will fetch the list of trusted forests from the DC hosting the local forest. For each discovered forest, IPAM then queries to get list of domains presents in the forest.
Once the task is finished, reopen the Configure server discovery dialog again and you will be able to see the list of trusted forests in Select the forest drop-down. Select the appropriate forest and then choose the domains you want to manage from the drop-down list and then click Add.
In each domain chosen, specify the type of servers to discover. By default, Domain Controllers, DHCP servers, and DNS servers are discovered. In the following example, IPAM server is in contoso.com forest, but we are able to add root domain of fabrikam.com forest and configure that domain controllers, DHCP servers, and DNS servers in that domain are to be discovered.
Once this is done, administrator can run server discovery workflow to discover these servers. To manage them, administrator needs to run the GPO invoking cmdlet for the domain. The GPO script will add IPAM user group to DNS admins, DHCP administrators and Event log readers groups for the domain. For non-DC DNS servers, the IPAM user group will be added as an administrator of the DNS server. This is the same procedure as for managing the domains belonging to the same AD forest as IPAM.
This new feature provides the administrators with the following capabilities:
Ability to get an aggregated view of the namespace as all the DNS servers can be managed using the same console
Ability to get an aggregated view of the IP addressing infrastructure as all the DHCP servers can be managed using the same console
Since all the DHCP and DNS servers can be managed together, administrators need not move from console to console and can do multi-server management from a single instance of IPAM
Reduction in cost as administrators need not maintain separate instances of IPAM for each AD forest
Using role based access control, administrators can still delegate permissions on different servers to different users. Hence, you can still have separate administrator for different forests.
We request you to try the new version of IPAM in your environment and let us know your feedback in the comments below.