Blocking executable content in Office 365 for more aggressive anti-malware protection
Sometimes, spammers and malware writers create malware that passes through our service and arrives in customer inboxes. This is new or unknown malware. The anti-malware engines that we use have not yet created signatures for them, and sometimes the spam rules do not catch them because the small amount of content has nothing for the spam rules to detect without causing false positives.
One solution to block this is to use an Exchange Transport Rule to block executable content. This will catch malware that uses commonly used malware mechanisms – content that executes automatically.
To do this using the Exchange Admin Center:
Login to the Exchange Admin Center and navigate to Admin –> Exchange –> mailflow –> rules.
-
Create a new Transport rule using the instructions below
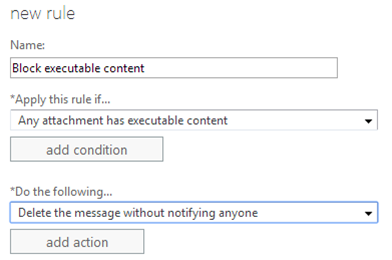
Create a new rule entitled “Block executable content”
* Apply this rule if… Any attachment has executable content
* Do the following… Delete the message without notifying anyoneThis will ensure that any message with executable content will not make it to the end user similar to how malware is treated today in the service (i.e., it is deleted).
Alternatively, if you don’t want to delete the message because you may receive false positives:
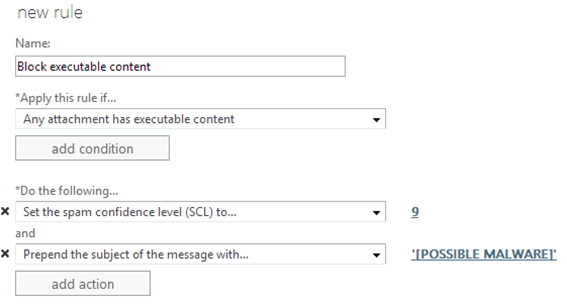
Create a new rule entitled “Block executable content”
* Apply this rule if… Any attachment has executable content
* Do the following… Set the Spam Confidence Level to 9 and Prepend the subject of the message with [POSSIBLE MALWARE](The red text is added by me for emphasis in this blog post)
This will route messages using the High Confidence Spam Action your organization has selected (Spam Quarantine, x-header modification, or move to Junk Mail Folder). However, it will also modify the message subject to give a visual indicator to users that it may contain possible malware so if they go through their Junk Folder or Spam Quarantine, they will see why the message was sent there.
Both of these options do not reject or bounce the message back to the sender. You should not pick this option because if the sender is spoofed, they will receive your rejection notice even though they did not send it.
To do this using Powershell instead:
a) Connect to Exchange Online using Powershell
https://technet.microsoft.com/en-us/library/jj984289(v=exchg.150).aspx
Or, connect to Exchange Online Protection using Powershell
https://technet.microsoft.com/en-us/library/dn621036(v=exchg.150).aspx
b) To delete the message without notifying anyone:
New-TransportRule -Name "Block executable content" -AttachmentHasExecutableContent $true -DeleteMessage $true
To set the SCL to 9 and modify the message subject:
New-TransportRule -Name "Block executable content" -SetSCL 9 -PrependSubject "[POSSIBLE MALWARE]"
The following table lists how executable content is determined:
Extension Description .rar Self-extracting archive file created with the WinRAR archiver .dll 32-bit Windows executable file with dynamic link library extension .exe Self-extracting executable program file .jar Java archive file exe Un-installation executable file .exe Program shortcut file .obj Compiled source code file or 3D object file or sequence file .exe 32-bit Windows executable file .vxd Microsoft Vizio XML drawing file .os2 OS/2 operating system file .w16 16-bit Windows executable file .dos Disk-operating system file .com European Institute for Computer Antivirus Research standard anti-virus test file .pif Windows program information file .exe Windows executable program file The transport engine does not rely solely upon the extension to detect if it is an executable. Instead, it scans the content to determine what type of file it is.
Submit malware to Microsoft through the reporting portal
Microsoft has a web portal to submit missed spam. If you are an Office 365 customer and the message with the attachment lands in your inbox, please submit it here:
https://www.microsoft.com/security/portal/submission/submit.aspx
Microsoft and Office 365 use these samples to update our anti-malware engines.
The above instructions will help catch zero-day malware. However, they should not be considered the definitive solution:
1.
Keep your local antivirus software up-to-date
Malware can be, and is, delivered in other formats other than the above.
Ensure the other software you are running is up-to-date
It is important to run the latest version of all your software (e.g., Windows OS, Internet browser, etc.). For Internet browsers, you can use https://browsercheck.qualys.com to ensure your browser plugins are running the latest version.
You may get false positives
To send files that require you have the above extensions:
Use a zip program to package files before you attach them to your e-mail message and password-protect it. In the message, you can include instructions that explain how to extract the files from the zipped package. Some email clients will block these, however.
Post the files to a secure network share. Most Internet service providers (ISPs) offer paying subscribers a space where they can post files, e.g., OneDrive. Give your recipients access to them and in your message to the recipients, you can include a link to the share.
Related Articles