Confusion property of symmetric block ciphers
Modern symmetric block encryption algorithms need to satisfy a number of properties to be considered strong. One such property is the property of “Confusion”.
What it means is that if an attacker is conducting an exhaustive key search, and if the key being tested is incorrect only in a few bits, the decrypted text should give no such indication. If the decrypted text does give such an indication, then the attacker can stop the brute force process, and simply change the incorrect bits in the key and get the actual key. This will take much less time relative to a full brute force attack.
To understand this better, I will demo it using the CrypTool, which is a great tool to learn about cryptography.
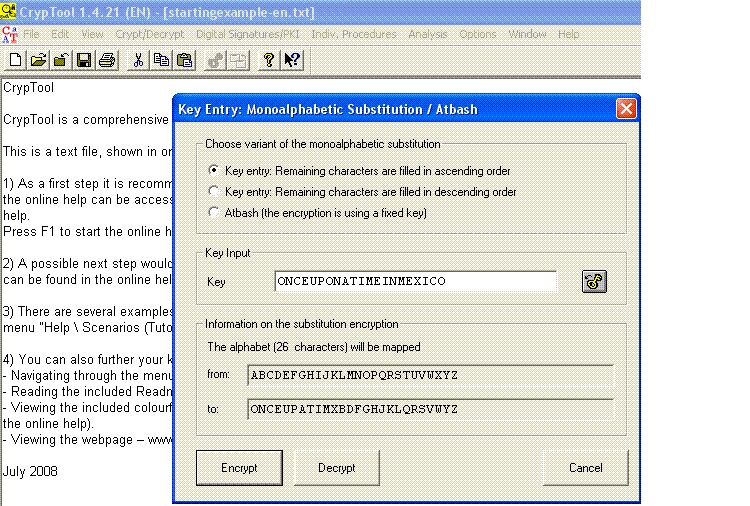
1. This will encrypt the text shown in the background using the Simple Substitution Cipher and the key “ONCEUPATIMXBDFGHJKLQRSVWYZ”.
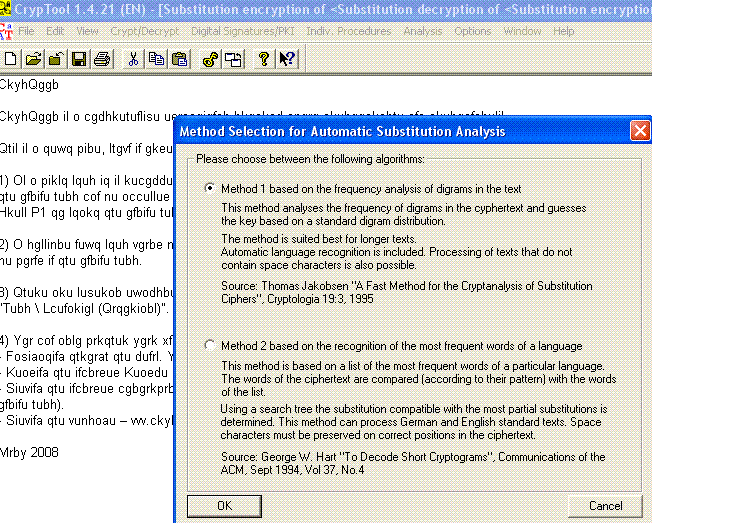
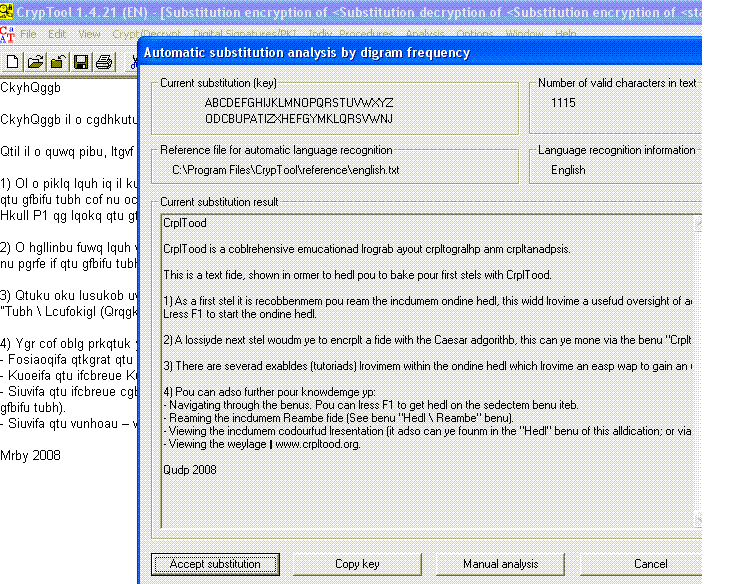
2. Text in the background has been encrypted. Using the tool, I will now perform an automatic analysis of the cipher text to try to get the key. Note: This could have been a brute force attack too.
3. Although the correct key has not been found, since the decrypted text resembles text in English to a great extent, I may be “close” to the the actual key.
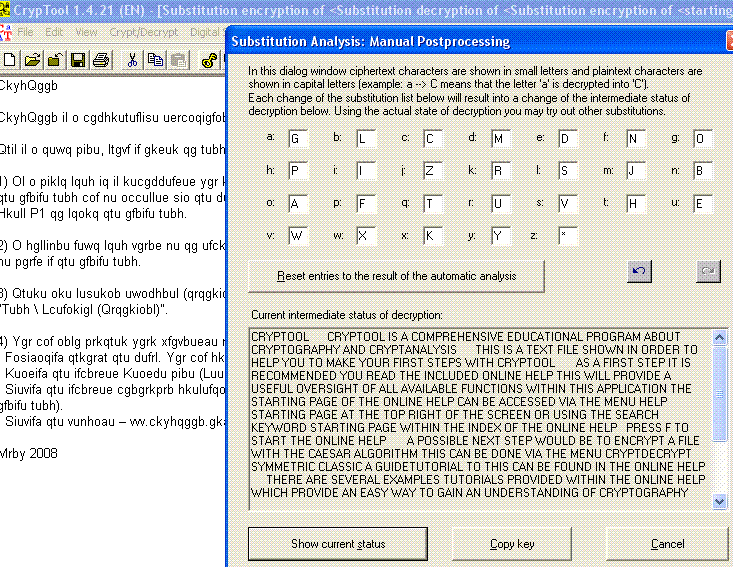
4. I will now stop the brute force process and using manual analysis , one by one substitute only those characters in the key that seem to produce incorrect plaintext, thereby getting the actual key.
Modern encryption algorithms like DES and AES have the Confusion property. Therefore if English text has been encrypted using DES or AES and during the brute force process, the key being tested differs from the actual key by only one bit, still the decrypted text does not resemble English text at all.