System Center 2012 R2 Explained: App Controller as a Single Pane of Glass for Cloud Management, A Primer
As IT architectures, methodologies, solutions, and cloud computing are rapidly converging, system management plays an increasingly critical role and has become a focal point of any cloud initiative. A system management solution now must identify and manage not only physical and virtualized resources, but those deployed as services to private cloud, public cloud, and in hybrid deployment scenarios. An integrated operating environment with secure access, self-servicing mechanism, and a consistent user experience is essential to be efficient in daily IT routines.
App Controller as a Single Pane of Glass
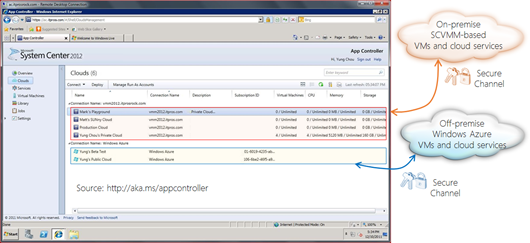
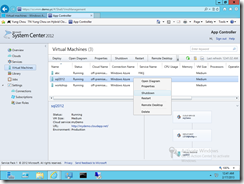
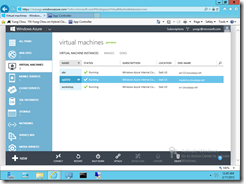
App Controller is a component and part of the self-service portal solution in System Center 2012 R2. By connecting to System Center Virtual Machine Manager (SCVMM) servers, Microsoft Azure subscriptions, and 3rd-party host services, App Controller offers a vehicle that enables an authorized user to administer resources deployed to private cloud, public cloud, and those in between without the need to understand the underlined fabric and physical complexities. It is a single pane of glass to manage multiple clouds and deployments in a modern datacenter where a private cloud may securely extend it boundary into Microsoft Azure, or a trusted hosting environment. The user experience and operations are consistent with those in Windows desktop and Internet Explorer. The following is a snapshot showing App Controller securely connected to both on-premise SCVMM-based private cloud and cloud services deployed to Microsoft Azure.
Delegation of Cloud Management
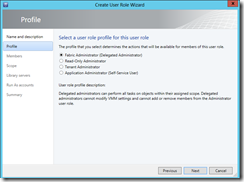
A key delivery of App Controller is the ability to delegate authority by allowing a user to connect to multiple resources based on user’s authorities, while hiding the underlying technical complexities.
An user can then manage those authorized resources by logging in App Controller and authorized by an associated user role, i.e. profile. In App Controller, a user neither sees, nor needs to know the existence of cloud fabric, i.e. under the hood how infrastructure, storage virtualization, network virtualization, and various servers and server virtualization hosts are placed, configured, and glued together.
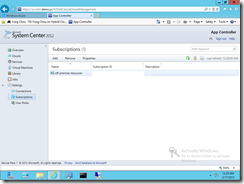
When first logging into App Controller, a user needs to connect with authorized datacenter resources including SCVMM servers, Microsoft Azure Subscriptions, and 3rd party host services.
Connecting with SCVMM Server
The user experience of App Controller is much the same with that of operating a Windows desktop. Connecting App Controller with a service provider on the other hand is per the provider’s instructions. However the process will be very similar with that of connecting with a Microsoft Azure subscription.
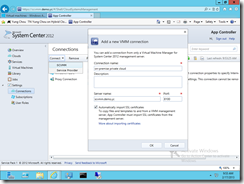
Connecting with Microsoft Azure Subscriptions
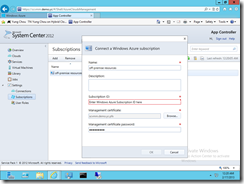
Connecting App Controller with Microsoft Azure on the other hands requires certificates and information of Microsoft Azure subscription id. This routine although may initially appear complex, it is actually quite simple and logical.
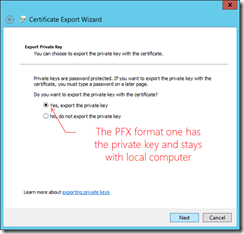
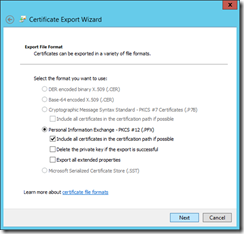
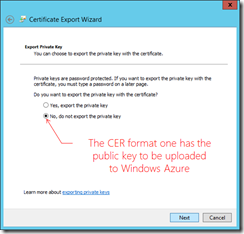
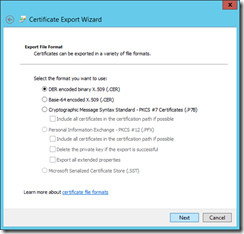
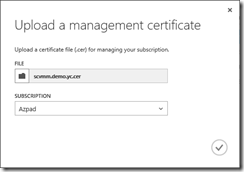
Establishing a secure channel for connecting App Controller with a Microsoft Azure subscription requires a private key/public key pair. App Controller employs a private key by installing the associated Personal Information Exchange (PFX) format of a chosen digital certificate, and the paired public key is in the binary format (.CER) of the digital certificate and uploaded to an intended Microsoft Azure subscription account. The following walks through the process.
Step 1 Acquire certificates
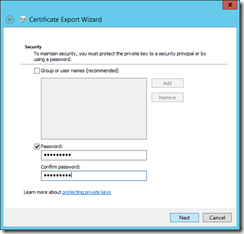
For those who are familiar with PKI, use Microsoft Management Console, or MMC, to directly export a digital certificate in PFX and CER formats from local computer certificate store. Those relatively new to certificate management should first take a look into what certificates IIS are employing first to better understand which certificate to use.
Optionally Review IIS Server Certificates
Since App Controller is installed with IIS, acquiring a certificate is quite simple to do. When installing App Controller with IIS, a self-signed certificate is put in place for accessing App Controller web UI with SSL.
 |
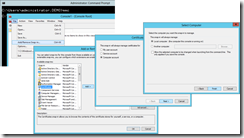
In IIS console, Server Certificate will list out all certificates visible to IIS. As needed, new certificates can be requested or created easily from the Actions pane of IIS Server Certificates UI, which is described elsewhere |
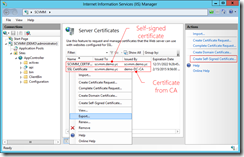 |
Here, there are two certificates listed. The self-signed certificate is created by installing App Controller, while the SSL certificate is later manually added. From Server Certificates, identify a target certificate to be used for connecting Microsoft Azure. Then use MMC to export certificates from the local computer certificate store. |
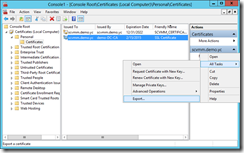
Use MMC with Certificate Snap-In to Expert Certificates
The certificate store of an OS instance can be accessed with MMC.
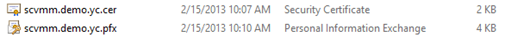
The two export processes, for example, created two certificates for connecting App Controller with Microsoft Azure as the following.
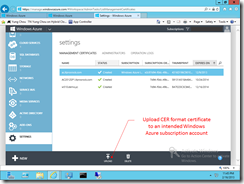
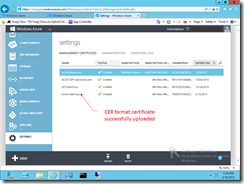
Step 2 Upload CER format certificate to Microsoft Azure
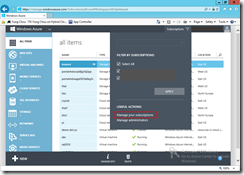
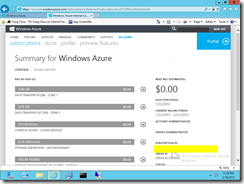
Step 3 Record Microsoft Azure subscription ID
Step 4 Connect App Controller with Microsoft Azure
Closing Thoughts
Upon connecting to on-premise and off-premise datacenter resources, App Controller is a secure vehicle enabling a user to manage authorized resources in a self-servicing manner. Not only the technologies are fascinating, but this is about shortening go-to-market while maximizing efficiency by allocating and deploying resources based on a user’s needs. This is a key step in realizing of IT as a Service.
Additional information:
- System Center 2012 R2 Explained: Managing Hybrid Cloud with App Controller
- System Center 2012 R2 Explained: Storing VM
- System Center 2012 R2 Explained: Using App Controller to COPY VM from On-Premise SCVMM-Based Private Cloud to Off-Premise Service Provider’s Facilities like Microsoft Azure
- System Center 2012 R2 Explained: App Controller for VM and Cloud Service Deployment
- System Center 2012 R2 Explained: Creating Private Clouds and Deploying Services with System Center 2012 R2 Virtual Machine Manager