Tutorial: Secure user sign-in events with Microsoft Entra multifactor authentication
Multifactor authentication is a process in which a user is prompted for additional forms of identification during a sign-in event. For example, the prompt could be to enter a code on their cellphone or to provide a fingerprint scan. When you require a second form of identification, security is increased because this additional factor isn't easy for an attacker to obtain or duplicate.
Microsoft Entra multifactor authentication and Conditional Access policies give you the flexibility to require MFA from users for specific sign-in events. For an overview of MFA, we recommend watching this video: How to configure and enforce multifactor authentication in your tenant.
Important
This tutorial shows an administrator how to enable Microsoft Entra multifactor authentication. To step through the multifactor authentication as a user, see Sign in to your work or school account using your two-step verification method.
If your IT team hasn't enabled the ability to use Microsoft Entra multifactor authentication, or if you have problems during sign-in, reach out to your Help desk for additional assistance.
In this tutorial you learn how to:
- Create a Conditional Access policy to enable Microsoft Entra multifactor authentication for a group of users.
- Configure the policy conditions that prompt for MFA.
- Test configuring and using multifactor authentication as a user.
Prerequisites
To complete this tutorial, you need the following resources and privileges:
A working Microsoft Entra tenant with Microsoft Entra ID P1 or trial licenses enabled.
- If you need to, create one for free.
An account with Conditional Access Administrator, Security Administrator, or Global Administrator privileges. Some MFA settings can also be managed by an Authentication Policy Administrator. For more information, see Authentication Policy Administrator.
A non-administrator account with a password that you know. For this tutorial, we created such an account, named testuser. In this tutorial, you test the end-user experience of configuring and using Microsoft Entra multifactor authentication.
- If you need information about creating a user account, see Add or delete users using Microsoft Entra ID.
A group that the non-administrator user is a member of. For this tutorial, we created such a group, named MFA-Test-Group. In this tutorial, you enable Microsoft Entra multifactor authentication for this group.
- If you need more information about creating a group, see Create a basic group and add members using Microsoft Entra ID.
Create a Conditional Access policy
Tip
Steps in this article might vary slightly based on the portal you start from.
The recommended way to enable and use Microsoft Entra multifactor authentication is with Conditional Access policies. Conditional Access lets you create and define policies that react to sign-in events and that request additional actions before a user is granted access to an application or service.
Conditional Access policies can be applied to specific users, groups, and apps. The goal is to protect your organization while also providing the right levels of access to the users who need it.
In this tutorial, we create a basic Conditional Access policy to prompt for MFA when a user signs in. In a later tutorial in this series, we configure Microsoft Entra multifactor authentication by using a risk-based Conditional Access policy.
First, create a Conditional Access policy and assign your test group of users as follows:
Sign in to the Microsoft Entra admin center as at least a Conditional Access Administrator.
Browse to Protection > Conditional Access, select + New policy, and then select Create new policy.
Enter a name for the policy, such as MFA Pilot.
Under Assignments, select the current value under Users or workload identities.

Under What does this policy apply to?, verify that Users and groups is selected.
Under Include, choose Select users and groups, and then select Users and groups.
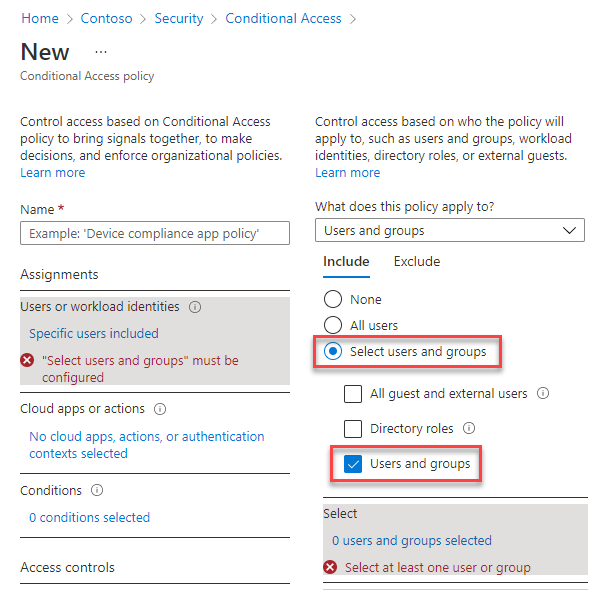
Since no one is assigned yet, the list of users and groups (shown in the next step) opens automatically.
Browse for and select your Microsoft Entra group, such as MFA-Test-Group, then choose Select.
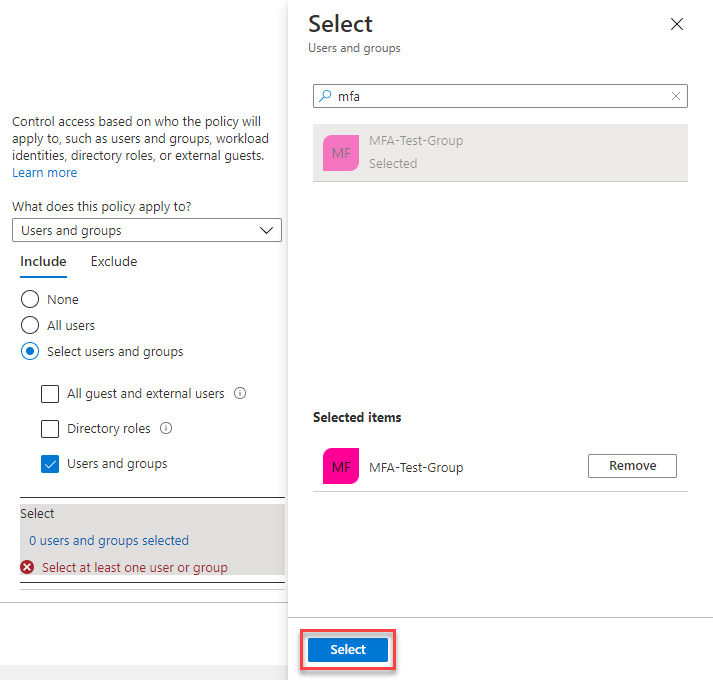
We've selected the group to apply the policy to. In the next section, we configure the conditions under which to apply the policy.
Configure the conditions for multifactor authentication
Now that the Conditional Access policy is created and a test group of users is assigned, define the cloud apps or actions that trigger the policy. These cloud apps or actions are the scenarios that you decide require additional processing, such as prompting for multifactor authentication. For example, you could decide that access to a financial application or use of management tools require an additional prompt for authentication.
Configure which apps require multifactor authentication
For this tutorial, configure the Conditional Access policy to require multifactor authentication when a user signs in.
Select the current value under Cloud apps or actions, and then under Select what this policy applies to, verify that Cloud apps is selected.
Under Include, choose Select apps.
Since no apps are yet selected, the list of apps (shown in the next step) opens automatically.
Tip
You can choose to apply the Conditional Access policy to All cloud apps or Select apps. To provide flexibility, you can also exclude certain apps from the policy.
Browse the list of available sign-in events that can be used. For this tutorial, select Windows Azure Service Management API so that the policy applies to sign-in events. Then choose Select.

Configure multifactor authentication for access
Next, we configure access controls. Access controls let you define the requirements for a user to be granted access. They might be required to use an approved client app or a device that's hybrid-joined to Microsoft Entra ID.
In this tutorial, configure the access controls to require multifactor authentication during a sign-in event.
Under Access controls, select the current value under Grant, and then select Grant access.
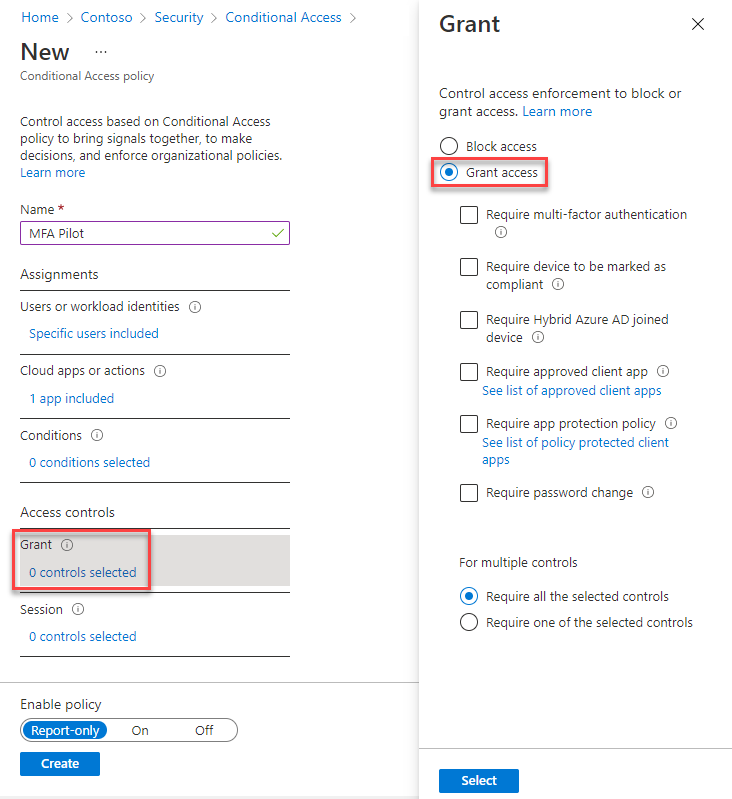
Select Require multifactor authentication, and then choose Select.

Activate the policy
Conditional Access policies can be set to Report-only if you want to see how the configuration would affect users, or Off if you don't want to the use policy right now. Because a test group of users is targeted for this tutorial, let's enable the policy, and then test Microsoft Entra multifactor authentication.
Under Enable policy, select On.
To apply the Conditional Access policy, select Create.
Test Microsoft Entra multifactor authentication
Let's see your Conditional Access policy and Microsoft Entra multifactor authentication in action.
First, sign in to a resource that doesn't require MFA:
Open a new browser window in InPrivate or incognito mode and browse to https://account.activedirectory.windowsazure.com.
Using a private mode for your browser prevents any existing credentials from affecting this sign-in event.
Sign in with your non-administrator test user, such as testuser. Be sure to include
@and the domain name for the user account.If this is the first instance of signing in with this account, you're prompted to change the password. However, there's no prompt for you to configure or use multifactor authentication.
Close the browser window.
You configured the Conditional Access policy to require additional authentication for sign in. Because of that configuration, you're prompted to use Microsoft Entra multifactor authentication or to configure a method if you haven't yet done so. Test this new requirement by signing in to the Microsoft Entra admin center:
Open a new browser window in InPrivate or incognito mode and sign in to the Microsoft Entra admin center.
Sign in with your non-administrator test user, such as testuser. Be sure to include
@and the domain name for the user account.You're required to register for and use Microsoft Entra multifactor authentication.

Select Next to begin the process.
You can choose to configure an authentication phone, an office phone, or a mobile app for authentication. Authentication phone supports text messages and phone calls, office phone supports calls to numbers that have an extension, and mobile app supports using a mobile app to receive notifications for authentication or to generate authentication codes.
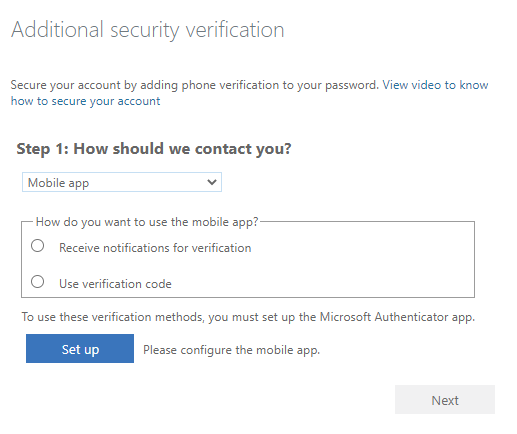
Complete the instructions on the screen to configure the method of multifactor authentication that you've selected.
Close the browser window, and sign in to the Microsoft Entra admin center again to test the authentication method that you configured. For example, if you configured a mobile app for authentication, you should see a prompt like the following.

Close the browser window.
Clean up resources
If you no longer want to use the Conditional Access policy that you configured as part of this tutorial, delete the policy by using the following steps:
Sign in to the Microsoft Entra admin center as at least a Conditional Access Administrator.
Browse to Protection > Conditional Access, and then select the policy that you created, such as MFA Pilot.
select Delete, and then confirm that you want to delete the policy.

Next steps
In this tutorial, you enabled Microsoft Entra multifactor authentication by using Conditional Access policies for a selected group of users. You learned how to:
- Create a Conditional Access policy to enable Microsoft Entra multifactor authentication for a group of Microsoft Entra users.
- Configure the policy conditions that prompt for multifactor authentication.
- Test configuring and using multifactor authentication as a user.
Feedback
Coming soon: Throughout 2024 we will be phasing out GitHub Issues as the feedback mechanism for content and replacing it with a new feedback system. For more information see: https://aka.ms/ContentUserFeedback.
Submit and view feedback for
