What are the default user permissions in Microsoft Entra ID?
In Microsoft Entra ID, all users are granted a set of default permissions. A user's access consists of the type of user, their role assignments, and their ownership of individual objects.
This article describes those default permissions and compares the member and guest user defaults. The default user permissions can be changed only in user settings in Microsoft Entra ID.
Member and guest users
The set of default permissions depends on whether the user is a native member of the tenant (member user) or whether the user is brought over from another directory as a business-to-business (B2B) collaboration guest (guest user). For more information about adding guest users, see What is Microsoft Entra B2B collaboration?. Here are the capabilities of the default permissions:
Member users can register applications, manage their own profile photo and mobile phone number, change their own password, and invite B2B guests. These users can also read all directory information (with a few exceptions).
Guest users have restricted directory permissions. They can manage their own profile, change their own password, and retrieve some information about other users, groups, and apps. However, they can't read all directory information.
For example, guest users can't enumerate the list of all users, groups, and other directory objects. Guests can be added to administrator roles, which grant them full read and write permissions. Guests can also invite other guests.
Compare member and guest default permissions
| Area | Member user permissions | Default guest user permissions | Restricted guest user permissions |
|---|---|---|---|
| Users and contacts |
|
|
|
| Groups |
|
|
|
| Applications |
|
|
|
| Devices |
|
No permissions | No permissions |
| Organization |
|
|
|
| Roles and scopes |
|
No permissions | No permissions |
| Subscriptions |
|
No permissions | No permissions |
| Policies |
|
No permissions | No permissions |
Restrict member users' default permissions
It's possible to add restrictions to users' default permissions.
You can restrict default permissions for member users in the following ways:
Caution
Using the Restrict access to Microsoft Entra administration portal switch is NOT a security measure. For more information on the functionality, see the table below.
| Permission | Setting explanation |
|---|---|
| Register applications | Setting this option to No prevents users from creating application registrations. You can then grant the ability back to specific individuals, by adding them to the application developer role. |
| Allow users to connect work or school account with LinkedIn | Setting this option to No prevents users from connecting their work or school account with their LinkedIn account. For more information, see LinkedIn account connections data sharing and consent. |
| Create security groups | Setting this option to No prevents users from creating security groups. Those assigned at least the User Administrators role can still create security groups. To learn how, see Microsoft Entra cmdlets for configuring group settings. |
| Create Microsoft 365 groups | Setting this option to No prevents users from creating Microsoft 365 groups. Setting this option to Some allows a set of users to create Microsoft 365 groups. Those assigned at least the User Administrator role can still create Microsoft 365 groups. To learn how, see Microsoft Entra cmdlets for configuring group settings. |
| Restrict access to Microsoft Entra administration portal | What does this switch do? No lets non-administrators browse the Microsoft Entra administration portal. Yes Restricts non-administrators from browsing the Microsoft Entra administration portal. Non-administrators who are owners of groups or applications are unable to use the Azure portal to manage their owned resources. What does it not do? When should I use this switch? When should I not use this switch? How do I grant only a specific non-administrator users the ability to use the Microsoft Entra administration portal? Restrict access to the Microsoft Entra administration portal |
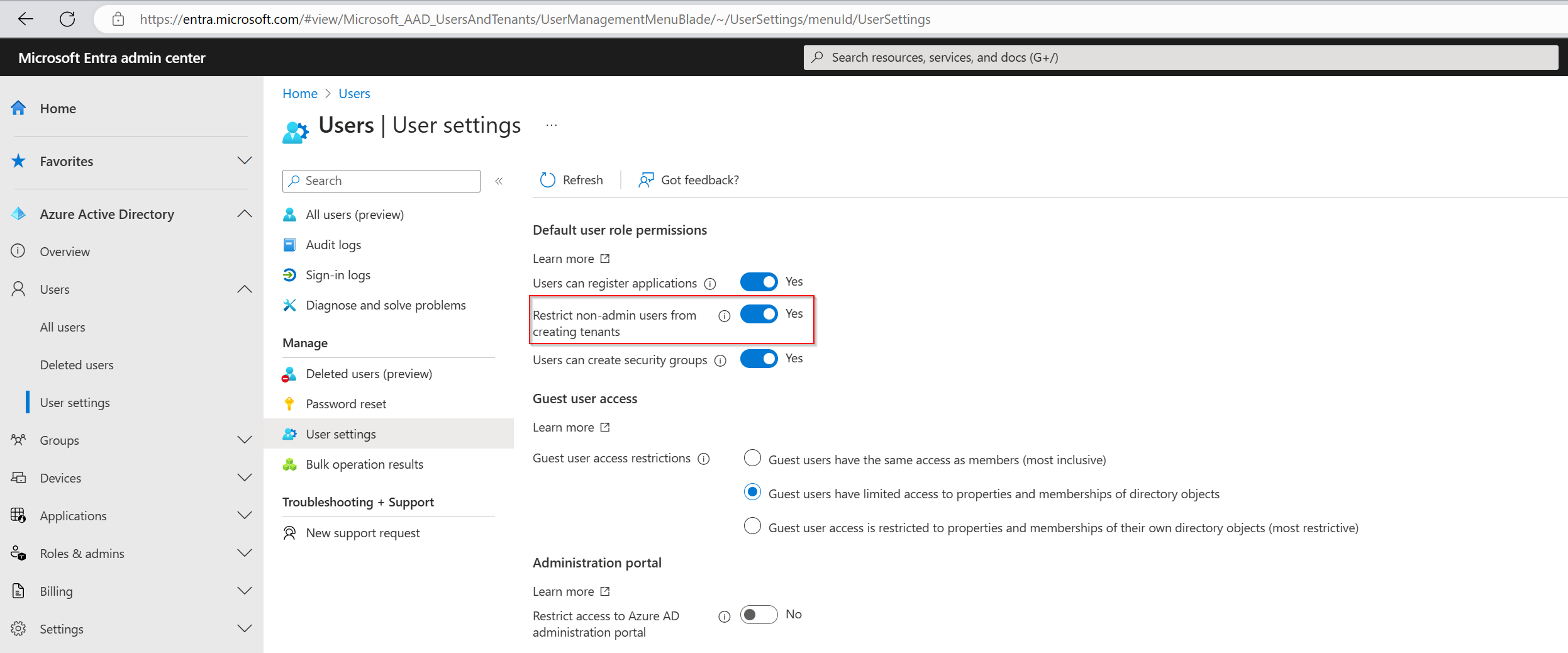
| Restrict non-admin users from creating tenants | Users can create tenants in the Microsoft Entra ID and Microsoft Entra administration portal under Manage tenant. The creation of a tenant is recorded in the Audit log as category DirectoryManagement and activity Create Company. Anyone who creates a tenant becomes the Global Administrator of that tenant. The newly created tenant doesn't inherit any settings or configurations. What does this switch do? How do I grant only a specific non-administrator users the ability to create new tenants? |
| Restrict users from recovering the BitLocker key(s) for their owned devices | This setting can be found in the Microsoft Entra admin center in the Device Settings. Setting this option to Yes restricts users from being able to self-service recover BitLocker key(s) for their owned devices. Users will have to contact their organization's helpdesk to retrieve their BitLocker keys. Setting this option to No allows users to recover their BitLocker key(s). |
| Read other users | This setting is available in Microsoft Graph and PowerShell only. Setting this flag to $false prevents all non-admins from reading user information from the directory. This flag doesn't prevent reading user information in other Microsoft services like Exchange Online.This setting is meant for special circumstances, so we don't recommend setting the flag to |
The Restrict non-admin users from creating tenants option is shown below
Restrict guest users' default permissions
You can restrict default permissions for guest users in the following ways.
Note
The Guest user access restrictions setting replaced the Guest users permissions are limited setting. For guidance on using this feature, see Restrict guest access permissions in Microsoft Entra ID.
| Permission | Setting explanation |
|---|---|
| Guest user access restrictions | Setting this option to Guest users have the same access as members grants all member user permissions to guest users by default. Setting this option to Guest user access is restricted to properties and memberships of their own directory objects restricts guest access to only their own user profile by default. Access to other users is no longer allowed, even when they're searching by user principal name, object ID, or display name. Access to group information, including groups memberships, is also no longer allowed. This setting doesn't prevent access to joined groups in some Microsoft 365 services like Microsoft Teams. To learn more, see Microsoft Teams guest access. Guest users can still be added to administrator roles regardless of this permission setting. |
| Guests can invite | Setting this option to Yes allows guests to invite other guests. To learn more, see Configure external collaboration settings. |
Object ownership
Application registration owner permissions
When a user registers an application, they're automatically added as an owner for the application. As an owner, they can manage the metadata of the application, such as the name and permissions that the app requests. They can also manage the tenant-specific configuration of the application, such as the single sign-on (SSO) configuration and user assignments.
An owner can also add or remove other owners. Unlike those assigned at least the Application Administrator role, owners can manage only the applications that they own.
Enterprise application owner permissions
When a user adds a new enterprise application, they're automatically added as an owner. As an owner, they can manage the tenant-specific configuration of the application, such as the SSO configuration, provisioning, and user assignments.
An owner can also add or remove other owners. Unlike those assigned at least the Application Administrator role, owners can manage only the applications that they own.
Group owner permissions
When a user creates a group, they're automatically added as an owner for that group. As an owner, they can manage properties of the group (such as the name) and manage group membership.
An owner can also add or remove other owners. Unlike those assigned at least the Groups Administrator role, owners can manage only the groups that they own and they can add or remove group members only if the group's membership type is Assigned.
To assign a group owner, see Managing owners for a group.
Ownership permissions
The following tables describe the specific permissions in Microsoft Entra ID that member users have over owned objects. Users have these permissions only on objects that they own.
Owned application registrations
Users can perform the following actions on owned application registrations:
| Action | Description |
|---|---|
| microsoft.directory/applications/audience/update | Update the applications.audience property in Microsoft Entra ID. |
| microsoft.directory/applications/authentication/update | Update the applications.authentication property in Microsoft Entra ID. |
| microsoft.directory/applications/basic/update | Update basic properties on applications in Microsoft Entra ID. |
| microsoft.directory/applications/credentials/update | Update the applications.credentials property in Microsoft Entra ID. |
| microsoft.directory/applications/delete | Delete applications in Microsoft Entra ID. |
| microsoft.directory/applications/owners/update | Update the applications.owners property in Microsoft Entra ID. |
| microsoft.directory/applications/permissions/update | Update the applications.permissions property in Microsoft Entra ID. |
| microsoft.directory/applications/policies/update | Update the applications.policies property in Microsoft Entra ID. |
| microsoft.directory/applications/restore | Restore applications in Microsoft Entra ID. |
Owned enterprise applications
Users can perform the following actions on owned enterprise applications. An enterprise application consists of a service principal, one or more application policies, and sometimes an application object in the same tenant as the service principal.
| Action | Description |
|---|---|
| microsoft.directory/auditLogs/allProperties/read | Read all properties (including privileged properties) on audit logs in Microsoft Entra ID. |
| microsoft.directory/policies/basic/update | Update basic properties on policies in Microsoft Entra ID. |
| microsoft.directory/policies/delete | Delete policies in Microsoft Entra ID. |
| microsoft.directory/policies/owners/update | Update the policies.owners property in Microsoft Entra ID. |
| microsoft.directory/servicePrincipals/appRoleAssignedTo/update | Update the servicePrincipals.appRoleAssignedTo property in Microsoft Entra ID. |
| microsoft.directory/servicePrincipals/appRoleAssignments/update | Update the users.appRoleAssignments property in Microsoft Entra ID. |
| microsoft.directory/servicePrincipals/audience/update | Update the servicePrincipals.audience property in Microsoft Entra ID. |
| microsoft.directory/servicePrincipals/authentication/update | Update the servicePrincipals.authentication property in Microsoft Entra ID. |
| microsoft.directory/servicePrincipals/basic/update | Update basic properties on service principals in Microsoft Entra ID. |
| microsoft.directory/servicePrincipals/credentials/update | Update the servicePrincipals.credentials property in Microsoft Entra ID. |
| microsoft.directory/servicePrincipals/delete | Delete service principals in Microsoft Entra ID. |
| microsoft.directory/servicePrincipals/owners/update | Update the servicePrincipals.owners property in Microsoft Entra ID. |
| microsoft.directory/servicePrincipals/permissions/update | Update the servicePrincipals.permissions property in Microsoft Entra ID. |
| microsoft.directory/servicePrincipals/policies/update | Update the servicePrincipals.policies property in Microsoft Entra ID. |
| microsoft.directory/signInReports/allProperties/read | Read all properties (including privileged properties) on sign-in reports in Microsoft Entra ID. |
| microsoft.directory/servicePrincipals/synchronizationCredentials/manage | Manage application provisioning secrets and credentials |
| microsoft.directory/servicePrincipals/synchronizationJobs/manage | Start, restart, and pause application provisioning synchronization jobs |
| microsoft.directory/servicePrincipals/synchronizationSchema/manage | Create and manage application provisioning synchronization jobs and schema |
| microsoft.directory/servicePrincipals/synchronization/standard/read | Read provisioning settings associated with your service principal |
Owned devices
Users can perform the following actions on owned devices:
| Action | Description |
|---|---|
| microsoft.directory/devices/bitLockerRecoveryKeys/read | Read the devices.bitLockerRecoveryKeys property in Microsoft Entra ID. |
| microsoft.directory/devices/disable | Disable devices in Microsoft Entra ID. |
Owned groups
Users can perform the following actions on owned groups.
Note
Owners of dynamic groups must have the Groups Administrator, Intune Administrator, or User Administrator role to edit group membership rules. For more information, see Create or update a dynamic group in Microsoft Entra ID.
| Action | Description |
|---|---|
| microsoft.directory/groups/appRoleAssignments/update | Update the groups.appRoleAssignments property in Microsoft Entra ID. |
| microsoft.directory/groups/basic/update | Update basic properties on groups in Microsoft Entra ID. |
| microsoft.directory/groups/delete | Delete groups in Microsoft Entra ID. |
| microsoft.directory/groups/members/update | Update the groups.members property in Microsoft Entra ID. |
| microsoft.directory/groups/owners/update | Update the groups.owners property in Microsoft Entra ID. |
| microsoft.directory/groups/restore | Restore groups in Microsoft Entra ID. |
| microsoft.directory/groups/settings/update | Update the groups.settings property in Microsoft Entra ID. |
Next steps
- To learn more about the Guest user access restrictions setting, see Restrict guest access permissions in Microsoft Entra ID.
- To learn more about how to assign Microsoft Entra administrator roles, see Assign a user to administrator roles in Microsoft Entra ID.
- To learn more about how resource access is controlled in Microsoft Azure, see Understanding resource access in Azure.
- For more information on how Microsoft Entra ID relates to your Azure subscription, see How Azure subscriptions are associated with Microsoft Entra ID.
- Manage users.
Feedback
Coming soon: Throughout 2024 we will be phasing out GitHub Issues as the feedback mechanism for content and replacing it with a new feedback system. For more information see: https://aka.ms/ContentUserFeedback.
Submit and view feedback for