Microsoft Entra ID Protection and B2B users
Microsoft Entra ID Protection detects compromised credentials for Microsoft Entra users. If your credential is detected as compromised, it means that someone else might have your password and be using it illegitimately. To prevent further risk to your account, it's important to securely reset your password so that the bad actor can no longer use your compromised password. ID Protection marks accounts that might be compromised as "at risk."
You can use your organizational credentials to sign-in to another organization as a guest. This process is referred to business-to-business or B2B collaboration. Organizations can configure policies to block users from signing-in if their credentials are considered at risk. If your account is at risk and you're blocked from signing-in to another organization as a guest, you might be able to self-remediate your account using the following steps. If your organization didn't enable self-service password reset, your administrator needs to manually remediate your account.
How to unblock your account
If you're attempting to sign-in to another organization as a guest and are blocked due to risk, you see the following block message: "Your account is blocked. We've detected suspicious activity on your account."
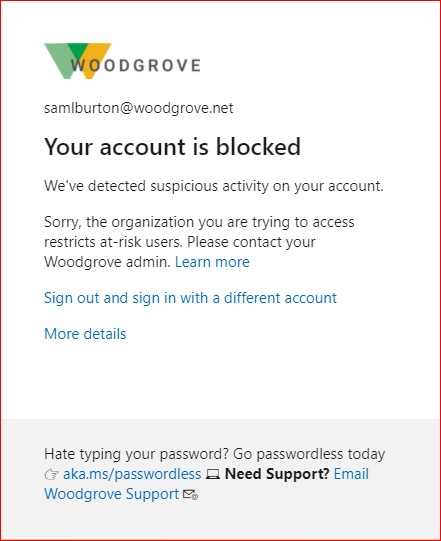
If your organization enables it, you can use self-service password reset unblock your account and get your credentials back to a safe state.
- Go to the Password reset portal and initiate the password reset. If self-service password reset isn't enabled for your account and you can't proceed, reach out to your IT administrator with the following information.
- If self-service password reset is enabled for your account, you're prompted to verify your identity using security methods prior to changing your password. For assistance, see the Reset your work or school password article.
- Once you have successfully and securely reset your password, your user risk is remediated. You can now try again to sign-in as a guest user.
If after resetting your password you're still blocked as a guest due to risk, reach out to your organization's IT administrator.
How to remediate a user's risk as an administrator
ID Protection automatically detects risky users for Microsoft Entra tenants. If you haven't checked the ID Protection reports before, there might be a large number of users with risk. Since resource tenants can apply user risk policies to guest users, your users can be blocked due to risk even if they were previously unaware of their risky state. If your user reports they're blocked as a guest user in another tenant due to risk, it's important to remediate the user to protect their account and enable collaboration.
Reset the user's password
From the Risky users report in the Microsoft Entra Security menu, search for the impacted user using the 'User' filter. Select the impacted user in the report and select "Reset password" in the top toolbar. The user will be assigned a temporary password that must be changed on the next sign-in. This process remediates their user risk and brings their credentials back to a safe state.
Manually dismiss user's risk
If password reset isn't an option for you, you can choose to manually dismiss user risk. Dismissing user risk doesn't have any impact on the user's existing password, but this process will change the user's Risk State from At Risk to Dismissed. It's important that you change the user's password using whatever means are available to you in order to bring the identity back to a safe state.
To dismiss user risk, go to the Risky users report in the Microsoft Entra Security menu. Search for the impacted user using the 'User' filter and select the user. Select the "dismiss user risk" option from the top toolbar. This action might take a few minutes to complete and update the user risk state in the report.
To learn more about Microsoft Entra ID Protection, see What is Identity Protection.
How does ID Protection work for B2B users?
The user risk for B2B collaboration users is evaluated at their home directory. The real-time sign-in risk for these users is evaluated at the resource directory when they try to access the resource. With Microsoft Entra B2B collaboration, organizations can enforce risk-based policies for B2B users using ID Protection. These policies be configured in two ways:
- Administrators can configure their Conditional Access policies, using sign-in risk as a condition, and includes guest users.
- Administrators can configure the built-in ID Protection risk-based policies, that apply to all apps, and include guest users.
Limitations of ID Protection for B2B collaboration users
There are limitations in the implementation of ID Protection for B2B collaboration users in a resource directory, due to their identity existing in their home directory. The main limitations are as follows:
- If a guest user triggers the ID Protection user risk policy to force password reset, they will be blocked. This block is due to the inability to reset passwords in the resource directory.
- Guest users do not appear in the risky users report. This limitation is due to the risk evaluation occurring in the B2B user's home directory.
- Administrators cannot dismiss or remediate a risky B2B collaboration user in their resource directory. This limitation is due to administrators in the resource directory not having access to the B2B user's home directory.
Why can't I remediate risky B2B collaboration users in my directory?
The risk evaluation and remediation for B2B users occurs in their home directory. Due to this fact, the guest users don't appear in the risky users report in the resource directory and admins in the resource directory can't force a secure password reset for these users.
What do I do if a B2B collaboration user was blocked due to a risk-based policy in my organization?
If a risky B2B user in your directory is blocked by your risk-based policy, the user needs to remediate that risk in their home directory. Users can remediate their risk by performing a secure password reset in their home directory as outlined previously. If they don't have self-service password reset enabled in their home directory, they need to contact their own organization's IT Staff to have an administrator manually dismiss their risk or reset their password.
How do I prevent B2B collaboration users from being impacted by risk-based policies?
Excluding B2B users from your organization's risk-based Conditional Access policies prevents B2B users from being impacted by risk evaluation. To exclude these B2B users, create a group in Microsoft Entra ID that contains all of your organization's guest users. Then, add this group as an exclusion for your built-in ID Protection user risk and sign-in risk policies, and any Conditional Access policies that use sign-in risk as a condition.
Next steps
See the following articles on Microsoft Entra B2B collaboration:
Feedback
Coming soon: Throughout 2024 we will be phasing out GitHub Issues as the feedback mechanism for content and replacing it with a new feedback system. For more information see: https://aka.ms/ContentUserFeedback.
Submit and view feedback for