Configure how users consent to applications
In this article, you'll learn how to configure the way users consent to applications and how to disable all future user consent operations to applications.
Before an application can access your organization's data, a user must grant the application permissions to do so. Different permissions allow different levels of access. By default, all users are allowed to consent to applications for permissions that don't require administrator consent. For example, by default, a user can consent to allow an app to access their mailbox but can't consent to allow an app unfettered access to read and write to all files in your organization.
To reduce the risk of malicious applications attempting to trick users into granting them access to your organization's data, we recommend that you allow user consent only for applications that have been published by a verified publisher.
Prerequisites
To configure user consent, you need:
- A user account. If you don't already have one, you can create an account for free.
- A Global Administrator role.
Configure user consent settings
Tip
Steps in this article might vary slightly based on the portal you start from.
To configure user consent settings through the Microsoft Entra admin center:
Sign in to the Microsoft Entra admin center as a Global Administrator.
Browse to Identity > Applications > Enterprise applications > Consent and permissions > User consent settings.
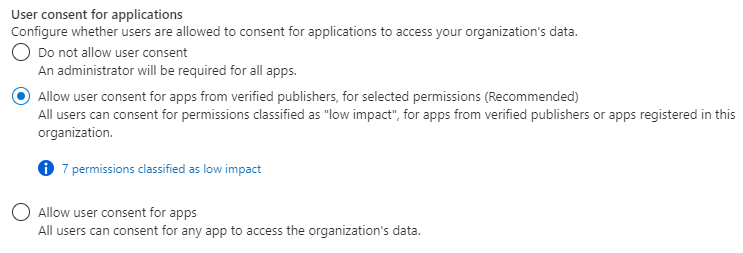
Under User consent for applications, select which consent setting you want to configure for all users.
Select Save to save your settings.
To choose which app consent policy governs user consent for applications, you can use the Microsoft Graph PowerShell module. The cmdlets used here are included in the Microsoft.Graph.Identity.SignIns module.
Connect to Microsoft Graph PowerShell
Connect to Microsoft Graph PowerShell using the least-privilege permission needed. For reading the current user consent settings, use Policy.Read.All. For reading and changing the user consent settings, use Policy.ReadWrite.Authorization. You need to sign in as a Global Administrator.
Connect-MgGraph -Scopes "Policy.ReadWrite.Authorization"
Disable user consent
To disable user consent, ensure that the consent policies (PermissionGrantPoliciesAssigned) include other current ManagePermissionGrantsForOwnedResource.* policies if any while updating the collection. This way, you can maintain your current configuration for user consent settings and other resource consent settings.
# only exclude user consent policy
$body = @{
"permissionGrantPolicyIdsAssignedToDefaultUserRole" = @(
"managePermissionGrantsForOwnedResource.{other-current-policies}"
)
}
Update-MgPolicyAuthorizationPolicy -AuthorizationPolicyId authorizationPolicy -BodyParameter $body
Allow user consent subject to an app consent policy using PowerShell
To allow user consent, choose which app consent policy should govern users' authorization to grant consent to apps. Ensure that the consent policies (PermissionGrantPoliciesAssigned) include other current ManagePermissionGrantsForOwnedResource.* policies if any while updating the collection. This way, you can maintain your current configuration for user consent settings and other resource consent settings.
$body = @{
"permissionGrantPolicyIdsAssignedToDefaultUserRole" = @(
"managePermissionGrantsForSelf.{consent-policy-id}",
"managePermissionGrantsForOwnedResource.{other-current-policies}"
)
}
Update-MgPolicyAuthorizationPolicy -AuthorizationPolicyId authorizationPolicy -BodyParameter $body
Replace {consent-policy-id} with the ID of the policy you want to apply. You can choose a custom app consent policy that you've created, or you can choose from the following built-in policies:
| ID | Description |
|---|---|
| microsoft-user-default-low | Allow user consent for apps from verified publishers, for selected permissions Allow limited user consent only for apps from verified publishers and apps that are registered in your tenant, and only for permissions that you classify as low impact. (Remember to classify permissions to select which permissions users are allowed to consent to.) |
| microsoft-user-default-legacy | Allow user consent for apps This option allows all users to consent to any permission that doesn't require admin consent, for any application |
For example, to enable user consent subject to the built-in policy microsoft-user-default-low, run the following commands:
$body = @{
"permissionGrantPolicyIdsAssignedToDefaultUserRole" = @(
"managePermissionGrantsForSelf.managePermissionGrantsForSelf.microsoft-user-default-low",
"managePermissionGrantsForOwnedResource.{other-current-policies}"
)
}
Use the Graph Explorer to choose which app consent policy governs user consent for applications. You need to sign in as a Global Administrator.
To disable user consent, ensure that the consent policies (PermissionGrantPoliciesAssigned) include other current ManagePermissionGrantsForOwnedResource.* policies if any while updating the collection. This way, you can maintain your current configuration for user consent settings and other resource consent settings.
PATCH https://graph.microsoft.com/v1.0/policies/authorizationPolicy
{
"defaultUserRolePermissions": {
"permissionGrantPoliciesAssigned": [
"managePermissionGrantsForOwnedResource.{other-current-policies}"
]
}
}
Allow user consent subject to an app consent policy using Microsoft Graph
To allow user consent, choose which app consent policy should govern users' authorization to grant consent to apps. Ensure that the consent policies (PermissionGrantPoliciesAssigned) include other current ManagePermissionGrantsForOwnedResource.* policies if any while updating the collection. This way, you can maintain your current configuration for user consent settings and other resource consent settings.
PATCH https://graph.microsoft.com/v1.0/policies/authorizationPolicy
{
"defaultUserRolePermissions": {
"managePermissionGrantsForSelf.{consent-policy-id}",
"managePermissionGrantsForOwnedResource.{other-current-policies}"
}
}
Replace {consent-policy-id} with the ID of the policy you want to apply. You can choose a custom app consent policy that you've created, or you can choose from the following built-in policies:
| ID | Description |
|---|---|
| microsoft-user-default-low | Allow user consent for apps from verified publishers, for selected permissions Allow limited user consent only for apps from verified publishers and apps that are registered in your tenant, and only for permissions that you classify as low impact. (Remember to classify permissions to select which permissions users are allowed to consent to.) |
| microsoft-user-default-legacy | Allow user consent for apps This option allows all users to consent to any permission that doesn't require admin consent, for any application |
For example, to enable user consent subject to the built-in policy microsoft-user-default-low, use the following PATCH command:
PATCH https://graph.microsoft.com/v1.0/policies/authorizationPolicy
{
"defaultUserRolePermissions": {
"permissionGrantPoliciesAssigned": [
"managePermissionGrantsForSelf.microsoft-user-default-low",
"managePermissionGrantsForOwnedResource.{other-current-policies}"
]
}
}
Tip
To allow users to request an administrator's review and approval of an application that the user isn't allowed to consent to, enable the admin consent workflow. For example, you might do this when user consent has been disabled or when an application is requesting permissions that the user isn't allowed to grant.
Next steps
Feedback
Coming soon: Throughout 2024 we will be phasing out GitHub Issues as the feedback mechanism for content and replacing it with a new feedback system. For more information see: https://aka.ms/ContentUserFeedback.
Submit and view feedback for