Use a Linux VM system-assigned managed identity to access Azure Resource Manager
Managed identities for Azure resources is a feature of Microsoft Entra ID. Each of the Azure services that support managed identities for Azure resources are subject to their own timeline. Make sure you review the availability status of managed identities for your resource and known issues before you begin.
This quickstart shows you how to use a system-assigned managed identity as a Linux virtual machine (VM)'s identity to access the Azure Resource Manager API. Managed identities for Azure resources are automatically managed by Azure and enable you to authenticate to services that support Microsoft Entra authentication without needing to insert credentials into your code. You learn how to:
- Grant your VM access to a Resource Group in Azure Resource Manager
- Get an access token using the VM identity and use it to call Azure Resource Manager
Prerequisites
- An understanding of Managed identities. If you're not familiar with managed identities, see this overview.
- An Azure account, sign up for a free account.
- You also need a Linux Virtual machine that has system assigned managed identities enabled. If you have a VM but need to enable system assigned managed identities you can do it in the identity section of the virtual machine's properties.
- If you need to create a virtual machine for this tutorial, you can follow the article titled Create a Linux virtual machine with the Azure portal
Grant access
Tip
Steps in this article might vary slightly based on the portal you start from.
When you use managed identities for Azure resources, your code can get access tokens to authenticate to resources that support Microsoft Entra authentication. The Azure Resource Manager API supports Microsoft Entra authentication. First, we need to grant this VM's identity access to a resource in Azure Resource Manager, in this case, the Resource Group in which the VM is contained.
Sign in to the Azure portal with your administrator account.
Navigate to the tab for Resource Groups.
Select the Resource Group you want to grant the VM's managed identity access.
In the left panel, select Access control (IAM).
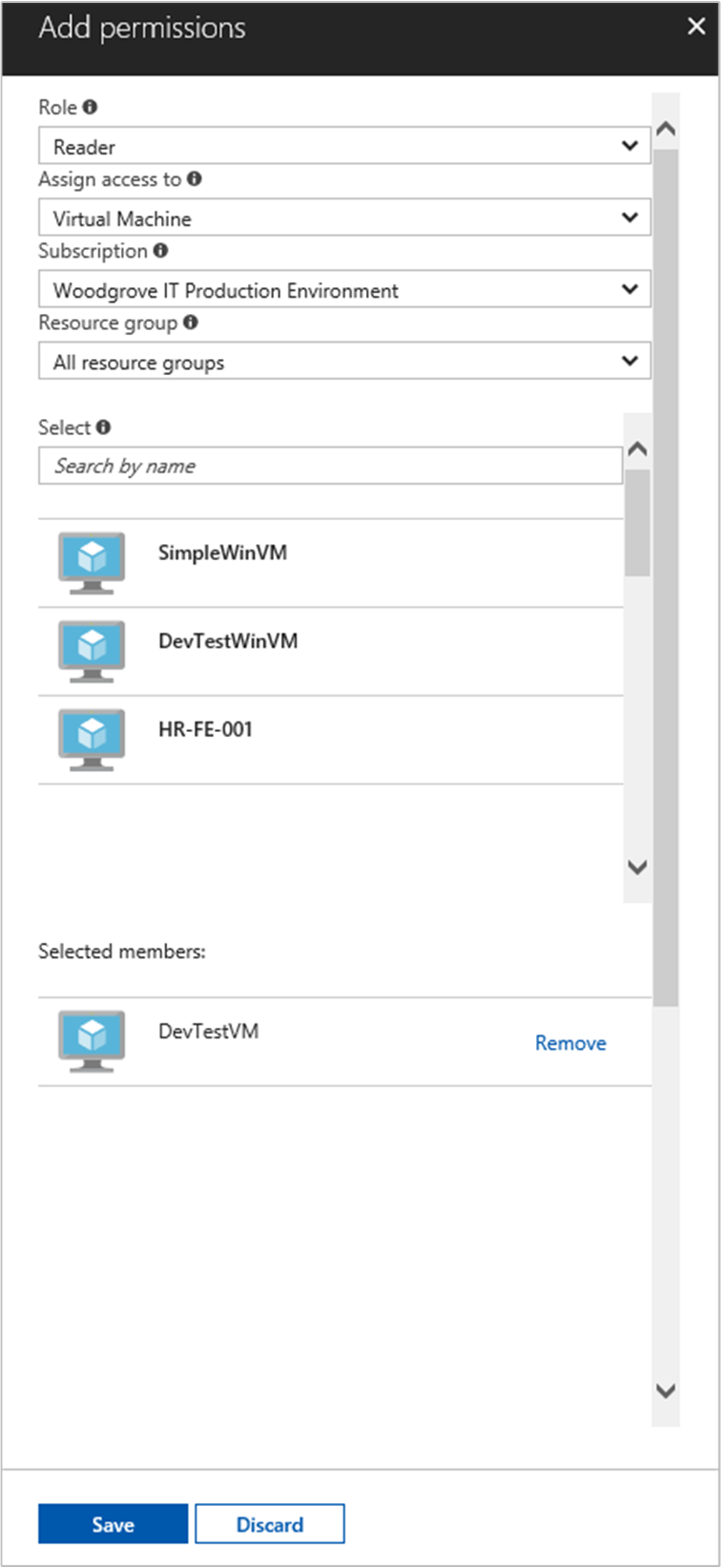
Select Add, and then select Add role assignment.
In the Role tab, select Reader. This role allows view all resources, but doesn't allow you to make any changes.
In the Members tab, for the Assign access to, select Managed identity. Then, select + Select members.
Ensure the proper subscription is listed in the Subscription dropdown. And for Resource Group, select All resource groups.
For the Manage identity dropdown, select Virtual Machine.
Finally, in Select choose your Windows Virtual Machine in the dropdown and select Save.
Get an access token using the VM's system-assigned managed identity and use it to call Resource Manager
To complete these steps, you need an SSH client. If you're using Windows, you can use the SSH client in the Windows Subsystem for Linux. If you need assistance configuring your SSH client's keys, see How to Use SSH keys with Windows on Azure, or How to create and use an SSH public and private key pair for Linux VMs in Azure.
In the portal, navigate to your Linux VM and in the Overview, select Connect.
Connect to the VM with the SSH client of your choice.
In the terminal window, using
curl, make a request to the local managed identities for Azure resources endpoint to get an access token for Azure Resource Manager. Thecurlrequest for the access token is below.
curl 'http://169.254.169.254/metadata/identity/oauth2/token?api-version=2018-02-01&resource=https://management.azure.com/' -H Metadata:true
Note
The value of the resource parameter must be an exact match for what is expected by Microsoft Entra ID. In the case of the Resource Manager resource ID, you must include the trailing slash on the URI.
The response includes the access token you need to access Azure Resource Manager.
Response:
{
"access_token":"eyJ0eXAiOi...",
"refresh_token":"",
"expires_in":"3599",
"expires_on":"1504130527",
"not_before":"1504126627",
"resource":"https://management.azure.com",
"token_type":"Bearer"
}
You can use this access token to access Azure Resource Manager, for example to read the details of the Resource Group to which you previously granted this VM access. Replace the values of <SUBSCRIPTION-ID>, <RESOURCE-GROUP>, and <ACCESS-TOKEN> with the ones you created earlier.
Note
The URL is case-sensitive, so ensure if you are using the exact same case as you used earlier when you named the Resource Group, and the uppercase “G” in “resourceGroup”.
curl https://management.azure.com/subscriptions/<SUBSCRIPTION-ID>/resourceGroups/<RESOURCE-GROUP>?api-version=2016-09-01 -H "Authorization: Bearer <ACCESS-TOKEN>"
The response back with the specific Resource Group information:
{
"id":"/subscriptions/98f51385-2edc-4b79-bed9-7718de4cb861/resourceGroups/DevTest",
"name":"DevTest",
"location":"westus",
"properties":
{
"provisioningState":"Succeeded"
}
}
Next steps
In this quickstart, you learned how to use a system-assigned managed identity to access the Azure Resource Manager API. For more information about Azure Resource Manager, see:
Feedback
Coming soon: Throughout 2024 we will be phasing out GitHub Issues as the feedback mechanism for content and replacing it with a new feedback system. For more information see: https://aka.ms/ContentUserFeedback.
Submit and view feedback for