Tutorial: Microsoft Entra single sign-on (SSO) integration with Alibaba Cloud Service (Role-based SSO)
In this tutorial, you'll learn how to integrate Alibaba Cloud Service (Role-based SSO) with Microsoft Entra ID. When you integrate Alibaba Cloud Service (Role-based SSO) with Microsoft Entra ID, you can:
- Control in Microsoft Entra ID who has access to Alibaba Cloud Service (Role-based SSO).
- Enable your users to be automatically signed-in to Alibaba Cloud Service (Role-based SSO) with their Microsoft Entra accounts.
- Manage your accounts in one central location.
Prerequisites
To get started, you need the following items:
- A Microsoft Entra subscription. If you don't have a subscription, you can get a free account.
- Alibaba Cloud Service (Role-based SSO) single sign-on (SSO) enabled subscription.
Scenario description
In this tutorial, you configure and test Microsoft Entra SSO in a test environment.
- Alibaba Cloud Service (Role-based SSO) supports IDP initiated SSO
Adding Alibaba Cloud Service (Role-based SSO) from the gallery
To configure the integration of Alibaba Cloud Service (Role-based SSO) into Microsoft Entra ID, you need to add Alibaba Cloud Service (Role-based SSO) from the gallery to your list of managed SaaS apps.
Sign in to the Microsoft Entra admin center as at least a Cloud Application Administrator.
Browse to Identity > Applications > Enterprise applications > New application.
In the Add from the gallery section, type Alibaba Cloud Service (Role-based SSO) in the search box.
Select Alibaba Cloud Service (Role-based SSO) from results panel and then add the app. Wait a few seconds while the app is added to your tenant.
On the Alibaba Cloud Service (Role-based SSO) page, click Properties in the left-side navigation pane, and copy the object ID and save it on your computer for subsequent use.

Alternatively, you can also use the Enterprise App Configuration Wizard. In this wizard, you can add an application to your tenant, add users/groups to the app, assign roles, as well as walk through the SSO configuration as well. Learn more about Microsoft 365 wizards.
Configure and test Microsoft Entra SSO for Alibaba Cloud Service (Role-based SSO)
Configure and test Microsoft Entra SSO with Alibaba Cloud Service (Role-based SSO) using a test user called B.Simon. For SSO to work, you need to establish a link relationship between a Microsoft Entra user and the related user in Alibaba Cloud Service (Role-based SSO).
To configure and test Microsoft Entra SSO with Alibaba Cloud Service (Role-based SSO), perform the following steps:
- Configure Microsoft Entra SSO - to enable your users to use this feature.
- Create a Microsoft Entra test user - to test Microsoft Entra single sign-on with Britta Simon.
- Assign the Microsoft Entra test user - to enable Britta Simon to use Microsoft Entra single sign-on.
- Configure Role-Based Single Sign-On in Alibaba Cloud Service - to enable your users to use this feature.
- Configure Alibaba Cloud Service (Role-based SSO) SSO - to configure the Single Sign-On settings on application side.
- Create Alibaba Cloud Service (Role-based SSO) test user - to have a counterpart of Britta Simon in Alibaba Cloud Service (Role-based SSO) that is linked to the Microsoft Entra representation of user.
- Test SSO - to verify whether the configuration works.
Configure Microsoft Entra SSO
Follow these steps to enable Microsoft Entra SSO.
Sign in to the Microsoft Entra admin center as at least a Cloud Application Administrator.
Browse to Identity > Applications > Enterprise applications > Alibaba Cloud Service (Role-based SSO) > Single sign-on.
On the Select a single sign-on method page, select SAML.
On the Set up single sign-on with SAML page, click the edit/pen icon for Basic SAML Configuration to edit the settings.
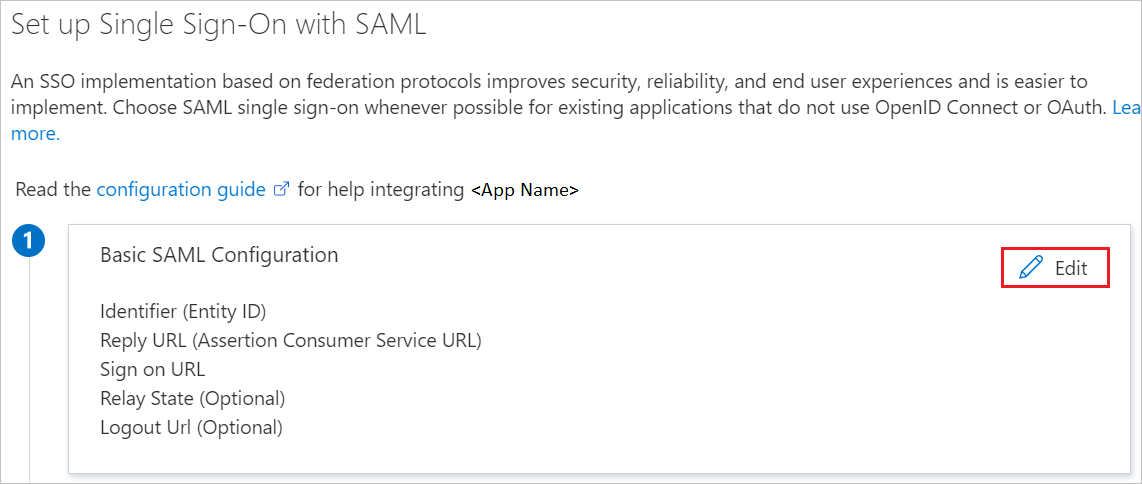
On the Basic SAML Configuration section, if you have Service Provider metadata file, perform the following steps:
a. Click Upload metadata file.
b. Click on folder logo to select the metadata file and click Upload.
Note
c. Once the metadata file is successfully uploaded, the Identifier and Reply URL values get auto populated in Alibaba Cloud Service (Role-based SSO) section textbox:
Note
If the Identifier and Reply URL values do not get auto populated, then fill in the values manually according to your requirement.
Alibaba Cloud Service (Role-based SSO) require roles to be configured in Microsoft Entra ID. The role claim is pre-configured so you don't have to configure it but you still need to create them in Microsoft Entra ID using this article.
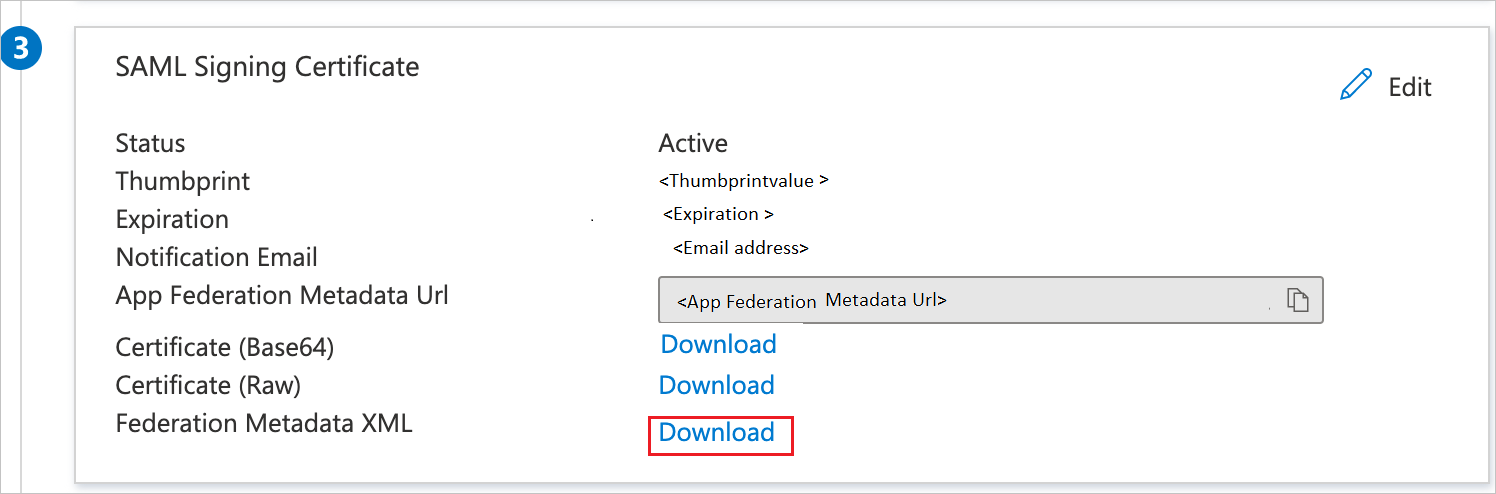
On the Set up single sign-on with SAML page, in the SAML Signing Certificate section, find Federation Metadata XML and select Download to download the certificate and save it on your computer.
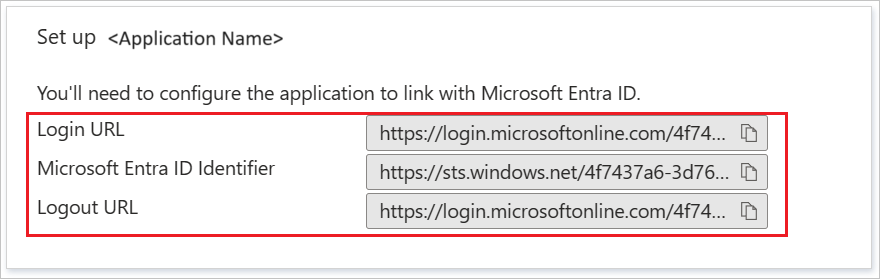
On the Set up Alibaba Cloud Service (Role-based SSO) section, copy the appropriate URL(s) based on your requirement.
Create a Microsoft Entra test user
In this section, you'll create a test user called B.Simon.
- Sign in to the Microsoft Entra admin center as at least a User Administrator.
- Browse to Identity > Users > All users.
- Select New user > Create new user, at the top of the screen.
- In the User properties, follow these steps:
- In the Display name field, enter
B.Simon. - In the User principal name field, enter the username@companydomain.extension. For example,
B.Simon@contoso.com. - Select the Show password check box, and then write down the value that's displayed in the Password box.
- Select Review + create.
- In the Display name field, enter
- Select Create.
Assign the Microsoft Entra test user
In this section, you'll enable B.Simon to use single sign-on by granting access to Alibaba Cloud Service (Role-based SSO).
Sign in to the Microsoft Entra admin center as at least a Cloud Application Administrator.
Browse to Identity > Applications > Enterprise applications > Alibaba Cloud Service (Role-based SSO).
In the app's overview page, find the Manage section and select Users and groups.
Select Add user, then select Users and groups in the Add Assignment dialog.
On the Users and groups tab, select u2 from the user list, and click Select. Then, click Assign.
View the assigned role and test Alibaba Cloud Service (Role-based SSO).
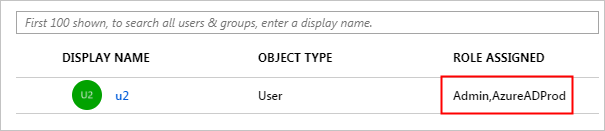
Note
After you assign the user (u2), the created role is automatically attached to the user. If you have created multiple roles, you need to attach the appropriate role to the user as needed. If you want to implement role-based SSO from Microsoft Entra ID to multiple Alibaba Cloud accounts, repeat the preceding steps.
Configure Role-Based Single Sign-On in Alibaba Cloud Service
Sign in to the Alibaba Cloud RAM console by using Account1.
In the left-side navigation pane, select SSO.
On the Role-based SSO tab, click Create IdP.
On the displayed page, enter
AADin the IdP Name field, enter a description in the Note field, click Upload to upload the federation metadata file you downloaded before, and click OK.After the IdP is successfully created, click Create RAM Role.
In the RAM Role Name field enter
AADrole, selectAADfrom the Select IdP drop-down list and click OK.Note
You can grant permission to the role as needed. After creating the IdP and the corresponding role, we recommend that you save the ARNs of the IdP and the role for subsequent use. You can obtain the ARNs on the IdP information page and the role information page.
Associate the Alibaba Cloud RAM role (AADrole) with the Microsoft Entra user (u2):
To associate the RAM role with the Microsoft Entra user, you must create a role in Microsoft Entra ID by following these steps:
Sign in to the Microsoft Graph Explorer.
Click modify permissions to obtain required permissions for creating a role.
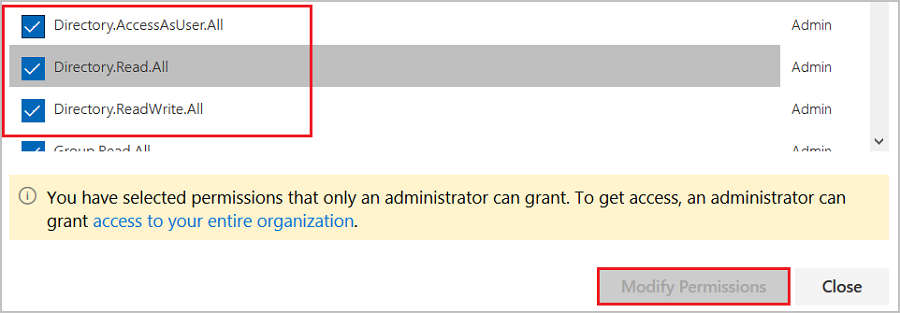
Select the following permissions from the list and click Modify Permissions, as shown in the following figure.
Note
After permissions are granted, sign in to the Graph Explorer again.
On the Graph Explorer page, select GET from the first drop-down list and beta from the second drop-down list. Then enter
https://graph.microsoft.com/beta/servicePrincipalsin the field next to the drop-down lists, and click Run Query.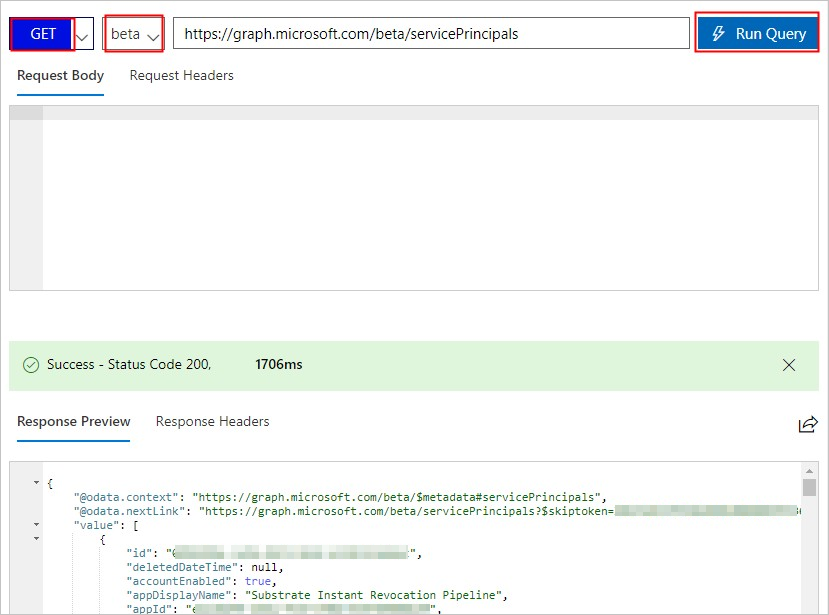
Note
If you are using multiple directories, you can enter
https://graph.microsoft.com/beta/contoso.com/servicePrincipalsin the field of the query.In the Response Preview section, extract the appRoles property from the 'Service Principal' for subsequent use.

Note
You can locate the appRoles property by entering
https://graph.microsoft.com/beta/servicePrincipals/<objectID>in the field of the query. Note that theobjectIDis the object ID you have copied from the Microsoft Entra ID Properties page.Go back to the Graph Explorer, change the method from GET to PATCH, paste the following content into the Request Body section, and click Run Query:
{ "appRoles": [ { "allowedMemberTypes": [ "User" ], "description": "msiam_access", "displayName": "msiam_access", "id": "41be2db8-48d9-4277-8e86-f6d22d35****", "isEnabled": true, "origin": "Application", "value": null }, { "allowedMemberTypes": [ "User" ], "description": "Admin,AzureADProd", "displayName": "Admin,AzureADProd", "id": "68adae10-8b6b-47e6-9142-6476078cdbce", "isEnabled": true, "origin": "ServicePrincipal", "value": "acs:ram::187125022722****:role/aadrole,acs:ram::187125022722****:saml-provider/AAD" } ] }Note
The
valueis the ARNs of the IdP and the role you created in the RAM console. Here, you can add multiple roles as needed. Microsoft Entra ID will send the value of these roles as the claim value in SAML response. However, you can only add new roles after themsiam_accesspart for the patch operation. To smooth the creation process, we recommend that you use an ID generator, such as GUID Generator, to generate IDs in real time.After the 'Service Principal' is patched with the required role, attach the role with the Microsoft Entra user (u2) by following the steps of Assign the Microsoft Entra test user section of the tutorial.
Configure Alibaba Cloud Service (Role-based SSO) SSO
To configure single sign-on on Alibaba Cloud Service (Role-based SSO) side, you need to send the downloaded Federation Metadata XML and appropriate copied URLs from the application configuration to Alibaba Cloud Service (Role-based SSO) support team. They set this setting to have the SAML SSO connection set properly on both sides.
Create Alibaba Cloud Service (Role-based SSO) test user
In this section, you create a user called Britta Simon in Alibaba Cloud Service (Role-based SSO). Work with Alibaba Cloud Service (Role-based SSO) support team to add the users in the Alibaba Cloud Service (Role-based SSO) platform. Users must be created and activated before you use single sign-on.
Test SSO
After the preceding configurations are completed, test Alibaba Cloud Service (Role-based SSO) by following these steps:
Sign in to the Microsoft Entra admin center as at least a Cloud Application Administrator.
Browse to Identity > Applications > Enterprise applications > Alibaba Cloud Service (Role-based SSO).
Select Single sign-on, and click Test.
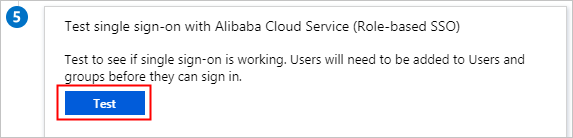
Click Sign in as current user.

On the account selection page, select u2.

The following page is displayed, indicating that role-based SSO is successful.
Next steps
Once you configure Alibaba Cloud Service (Role-based SSO) you can enforce session control, which protects exfiltration and infiltration of your organization’s sensitive data in real time. Session control extends from Conditional Access. Learn how to enforce session control with Microsoft Defender for Cloud Apps.
Feedback
Coming soon: Throughout 2024 we will be phasing out GitHub Issues as the feedback mechanism for content and replacing it with a new feedback system. For more information see: https://aka.ms/ContentUserFeedback.
Submit and view feedback for