Metrics Advisor service encryption of data at rest
Important
Starting on the 20th of September, 2023 you won’t be able to create new Metrics Advisor resources. The Metrics Advisor service is being retired on the 1st of October, 2026.
Metrics Advisor service automatically encrypts your data when it's persisted to the cloud. The Metrics Advisor service encryption protects your data and helps you to meet your organizational security and compliance commitments.
About Azure AI services encryption
Data is encrypted and decrypted using FIPS 140-2-compliant 256-bit AES encryption. Encryption and decryption are transparent, meaning encryption and access are managed for you. Your data is secure by default. You don't need to modify your code or applications to take advantage of encryption.
About encryption key management
By default, your subscription uses Microsoft-managed encryption keys. You can also manage your subscription with your own keys, which are called customer-managed keys. When you use customer-managed keys, you have greater flexibility in the way you create, rotate, disable, and revoke access controls. You can also audit the encryption keys that you use to protect your data. If customer-managed keys are configured for your subscription, double encryption is provided. With this second layer of protection, you can control the encryption key through your Azure Key Vault.
Metrics Advisor supports CMK and double encryption by using BYOS (bring your own storage).
Steps to create a Metrics Advisor with BYOS
Step 1. Create an Azure Database for PostgreSQL and set admin
Create an Azure Database for PostgreSQL
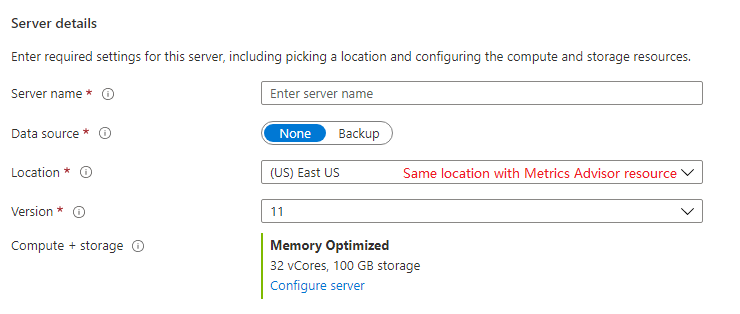
Sign in to the Azure portal and create a resource of the Azure Database for PostgreSQL. Couple of things to notice:
- Please select the 'Single Server' deployment option.
- When choosing 'Datasource', please specify as 'None'.
- For the 'Location', please make sure to create within the same location as Metrics Advisor resource.
- 'Version' should be set to 11.
- 'Compute + storage' should choose a 'Memory Optimized' SKU with at least 32 vCores.
Set Active Directory Admin for newly created PG
After successfully creating your Azure Database for PostgreSQL. Go to the resource page of the newly created Azure PG resource. Select 'Active Directory admin' tab and set yourself as the Admin.
Step 2. Create a Metrics Advisor resource and enable Managed Identity
Create a Metrics Advisor resource in the Azure portal
Go to Azure portal again and search 'Metrics Advisor'. When creating Metrics Advisor, do remember the following:
- Choose the same 'region' as your created Azure Database for PostgreSQL.
- Mark 'Bring your own storage' as 'Yes' and select the Azure Database for PostgreSQL you just created in the dropdown list.
Enable the Managed Identity for Metrics Advisor
After creating the Metrics Advisor resource, select 'Identity' and set 'Status' to 'On' to enable Managed Identity.
Get Application ID of Managed Identity
Go to Microsoft Entra ID, and select 'Enterprise applications'. Change 'Application type' to 'Managed Identity', copy resource name of Metrics Advisor, and search. Then you're able to view the 'Application ID' from the query result, copy it.
Step 3. Grant Metrics Advisor access permission to your Azure Database for PostgreSQL
Grant 'Owner' role for the Managed Identity on your Azure Database for PostgreSQL
Set firewall rules
- Set 'Allow access to Azure services' as 'Yes'.
- Add your clientIP address to sign in to Azure Database for PostgreSQL.
Get the access-token for your account with resource type 'https://ossrdbms-aad.database.windows.net'. The access token is the password you need to sign in to the Azure Database for PostgreSQL by your account. An example using
azclient:az login az account get-access-token --resource https://ossrdbms-aad.database.windows.netAfter getting the token, use it to sign in to your Azure Database for PostgreSQL. Replace the 'servername' as the one that you can find in the 'overview' of your Azure Database for PostgreSQL.
export PGPASSWORD=<access-token> psql -h <servername> -U <adminaccount@servername> -d postgresAfter sign in, execute the following commands to grant Metrics Advisor access permission to Azure Database for PostgreSQL. Replace the 'appid' with the one that you get in Step 2.
SET aad_validate_oids_in_tenant = off; CREATE ROLE metricsadvisor WITH LOGIN PASSWORD '<appid>' IN ROLE azure_ad_user; ALTER ROLE metricsadvisor CREATEDB; GRANT azure_pg_admin TO metricsadvisor;
By completing all the above steps, you've successfully created a Metrics Advisor resource with CMK supported. Wait for a couple of minutes until your Metrics Advisor is accessible.