Create a standalone Azure Automation account
This article shows you how to create an Azure Automation account using the Azure portal. You can use the Automation account to evaluate and learn about Automation without using additional management features or integrating with Azure Monitor Logs. You can add management features or integrate with Azure Monitor Logs for advanced monitoring of runbook jobs at any point in the future.
With an Automation account, you can authenticate runbooks by managing resources in either Azure Resource Manager or the classic deployment model. One Automation Account can manage resources across all regions and subscriptions for a given tenant.
With this account created for you, you can quickly start building and deploying runbooks to support your automation needs.
Permissions required to create an Automation account
To create or update an Automation account, and to complete the tasks described in this article, you must have the following privileges and permissions:
To create an Automation account, your Microsoft Entra user account must be added to a role with permissions equivalent to the Owner role for Microsoft.Automation resources. For more information, see Role-Based Access Control in Azure Automation.
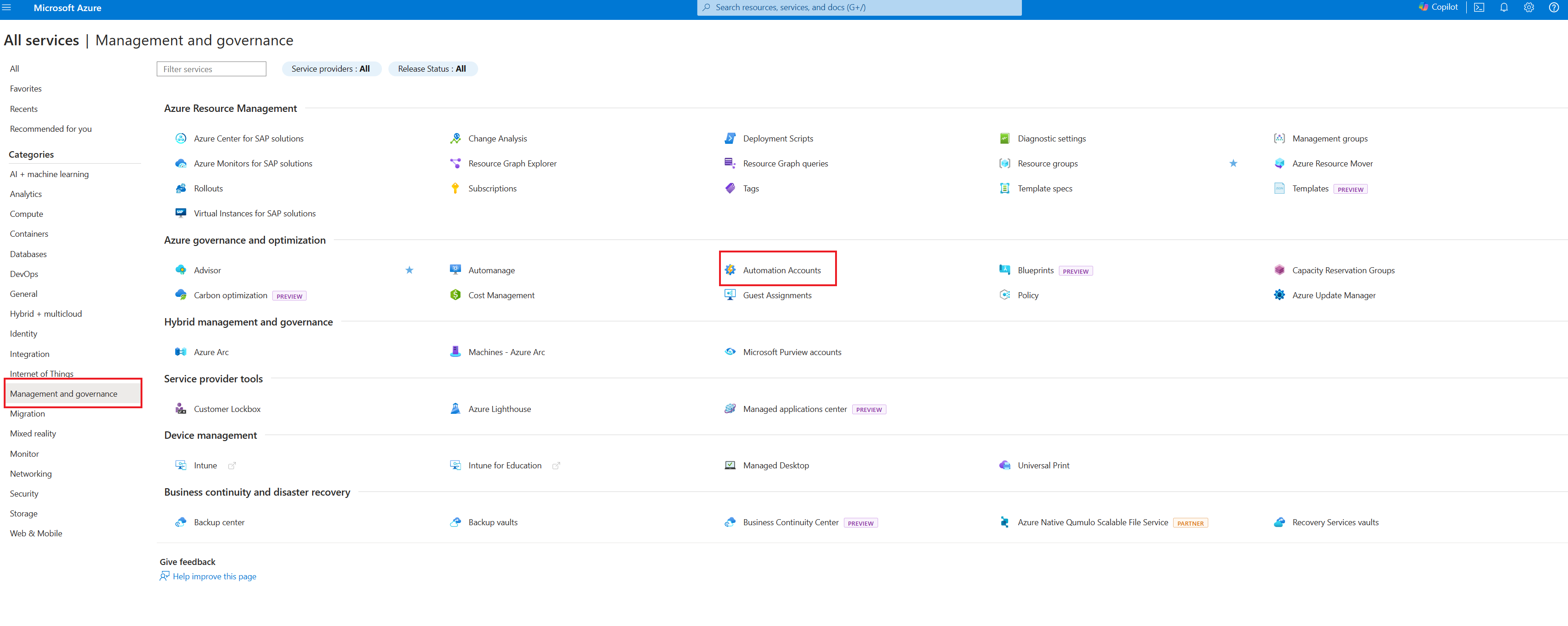
Create a new Automation account in the Azure portal
To create an Azure Automation account in the Azure portal, complete the following steps:
Sign in to the Azure portal with an account that's a member of the subscription Administrators role and a Co-Administrator of the subscription.
Select + Create a Resource.
Search for Automation. In the search results, select Automation.
Options for your new Automation account are organized into tabs in the Create an Automation Account page. The following sections describe each of the tabs and their options.
Basics
On the Basics tab, provide the essential information for your Automation account. After you complete the Basics tab, you can choose to further customize your new Automation account by setting options on the other tabs, or you can select Review + create to accept the default options and proceed to validate and create the account.
Note
By default, a system-assigned managed identity is enabled for the Automation account.
The following table describes the fields on the Basics tab.
| Field | Required or optional |
Description |
|---|---|---|
| Subscription | Required | From the drop-down list, select the Azure subscription for the account. |
| Resource group | Required | From the drop-down list, select your existing resource group, or select Create new. |
| Automation account name | Required | Enter a name unique for it's location and resource group. Names for Automation accounts that have been deleted might not be immediately available. You can't change the account name once it has been entered in the user interface. |
| Region | Required | From the drop-down list, select a region for the account. For an updated list of locations that you can deploy an Automation account to, see Products available by region. |
The following image shows a standard configuration for a new Automation account.

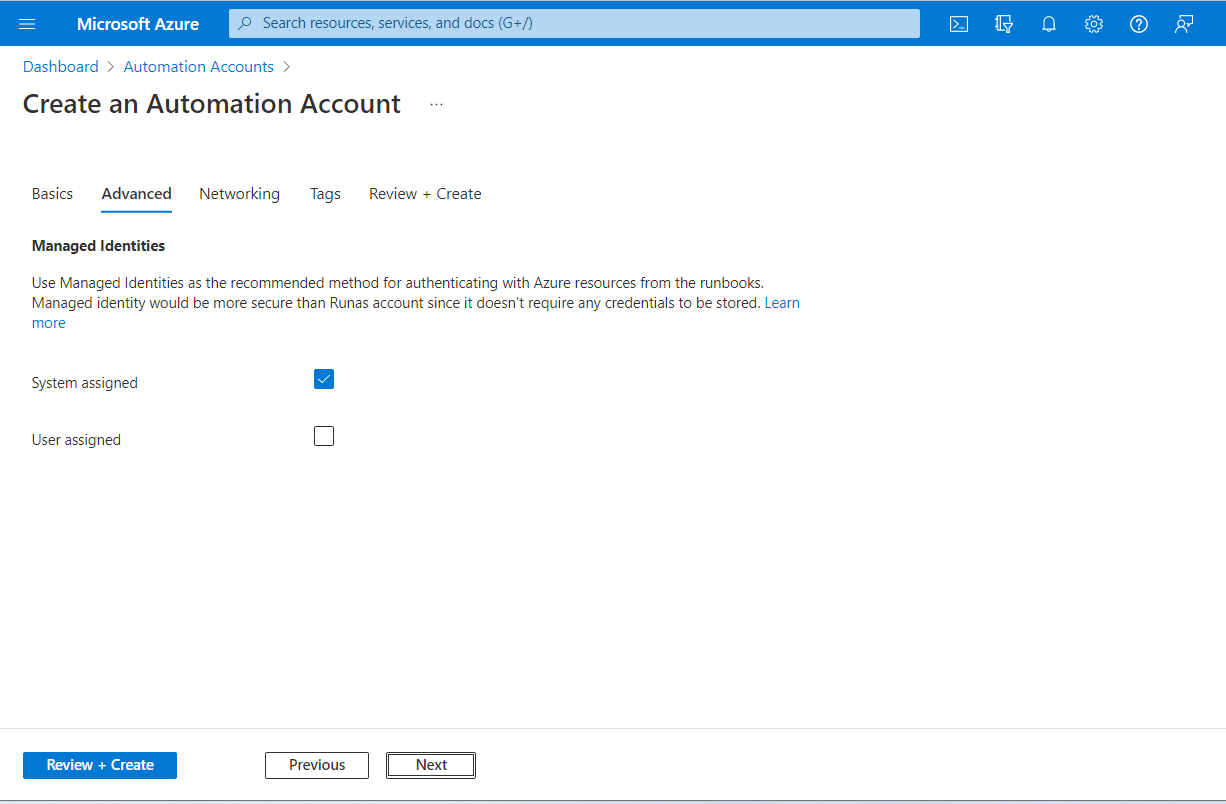
Advanced
On the Advanced tab, you can configure the managed identity option for your new Automation account. The user-assigned managed identity option can also be configured after the Automation account is created.
For instructions on how to create a user-assigned managed identity, see Create a user-assigned managed identity.
The following table describes the fields on the Advanced tab.
| Field | Required or optional |
Description |
|---|---|---|
| System-assigned | Optional | A Microsoft Entra identity that is tied to the lifecycle of the Automation account. |
| User-assigned | Optional | A managed identity represented as a standalone Azure resource that is managed separately from the resources that use it. |
You can chose to enable managed identities later, and the Automation account is created without one. To enable a managed identity after the account is created, see Enable managed identity. If you select both options, for the user-assigned identity, select the Add user assigned identities option. On the Select user assigned managed identity page, select a subscription and add one or more user-assigned identities created in that subscription to assign to the Automation account.
The following image shows a standard configuration for a new Automation account.
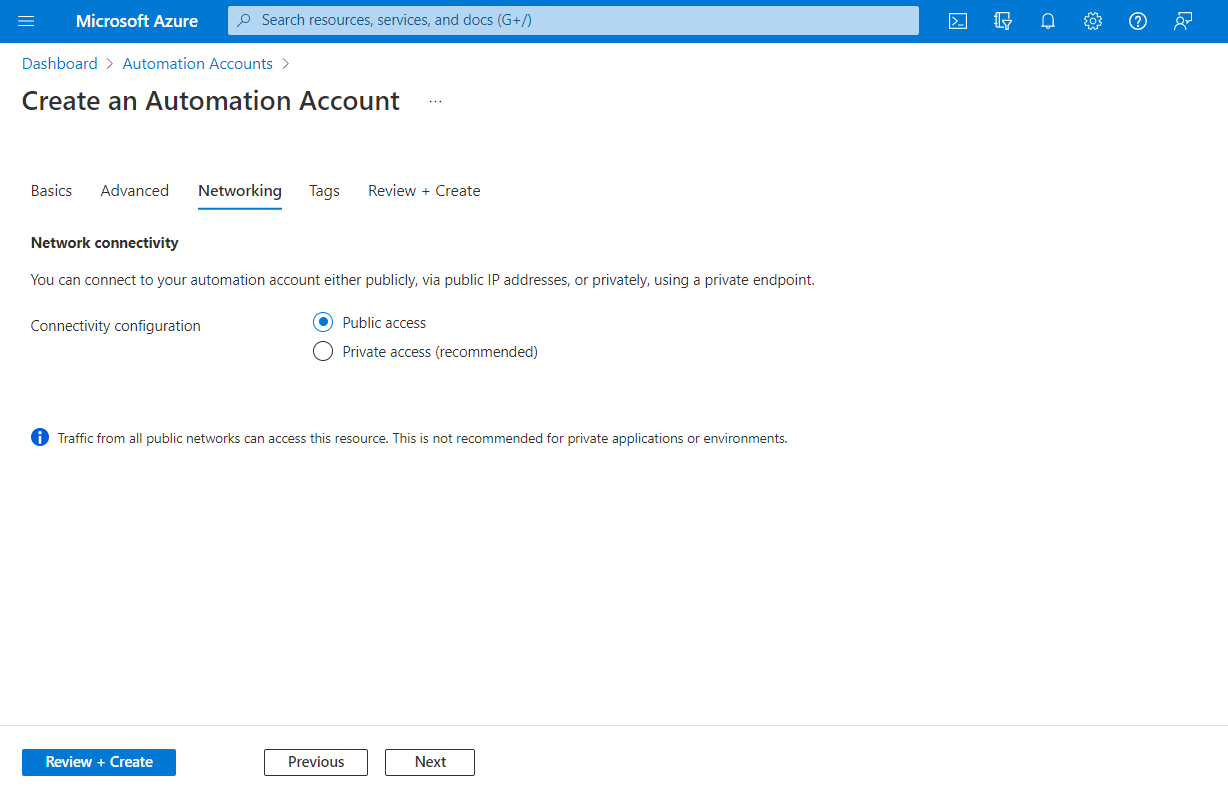
Networking
On the Networking tab, you can configure connectivity to Automation Account - either publicly via public IP addresses or privately using a Azure Automation Private Link. Azure Automation Private Link connects one or more private endpoints (and therefore the virtual networks they are contained in) to your Automation Account resource.
The following image shows a standard configuration for a new Automation account.
Tags
On the Tags tab, you can specify Resource Manager tags to help organize your Azure resources. For more information, see Tag resources, resource groups, and subscriptions for logical organization.
Review + create
When you navigate to the Review + create tab, Azure runs validation on the Automation account settings that you have chosen. If validation passes, you can proceed to create the Automation account.
If validation fails, then the portal indicates which settings need to be modified.
Review your new Automation account.
When the Automation account is successfully created, several resources are automatically created for you. After creation, these runbooks can be safely deleted if you do not wish to keep them. The managed identities can be used to authenticate to your account in a runbook, and should be left unless you create another one or do not require them. The Automation access keys are also created during Automation account creation. The following table summarizes resources for the account.
| Resource | Description |
|---|---|
| AzureAutomationTutorialWithIdentityGraphical | An example graphical runbook that demonstrates how to authenticate by using the Managed Identity. The runbook gets all Resource Manager resources. |
| AzureAutomationTutorialWithIdentity | An example PowerShell runbook that demonstrates how to authenticate by using the Managed Identity. The runbook gets all Resource Manager resources. |
Note
The tutorial runbooks have not been updated to authenticate using a managed identity. Review the Using system-assigned identity or Using user-assigned identity to learn how to grant the managed identity access to resources and configure your runbooks to authenticate using either type of managed identity.
Manage Automation account keys
When you create an Automation account, Azure generates two 512-bit automation account access keys for that account. These keys are shared access keys that are used as registration keys for registering DSC nodes as well as Windows and Linux Hybrid runbook workers. These keys are only used while registering DSC nodes and Hybrid workers. Existing machines configured as DSC nodes or hybrid workers won’t be affected after rotation of these keys.
View Automation account keys
To view and copy your Automation account access keys, follow these steps:
In the Azure portal, go to your Automation account.
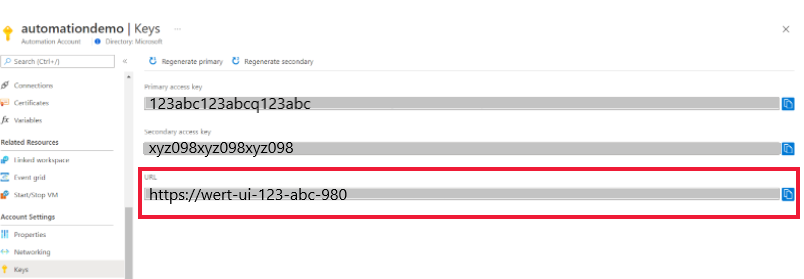
Under Account Settings, select Keys to view your Automation account's primary and secondary access keys. You can use any of the two keys to access your Automation account. However, we recommend that you use the first key and reserve the use of second key.
Manually rotate access keys
We recommend that you rotate your access keys periodically to keep the Automation account secure. As you have two access keys, you can rotate them using Azure portal or Azure PowerShell cmdlet.
Choose a client
Follow these steps:
- Go to your Automation account in the Azure portal.
- Under Account Settings, select Keys.
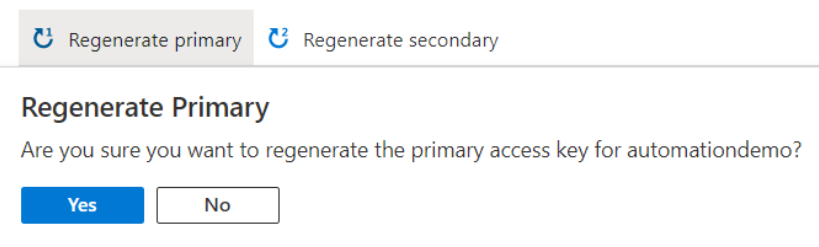
- Select Regenerate primary to regenerate the primary access key for your Automation account.
- Select the Regenerate secondary to regenerate the secondary access key.
View registration URL
The DSC node registers with the State Configuration service using the registration URL and authenticates using a registration access key along with the Automation Account access keys.
Next steps
- To get started with PowerShell runbooks, see Tutorial: Create a PowerShell runbook.
- To get started with PowerShell Workflow runbooks, see Tutorial: Create a PowerShell workflow runbook.
- To get started with Python 3 runbooks, see Tutorial: Create a Python 3 runbook.
- For a PowerShell cmdlet reference, see Az.Automation.
Feedback
Coming soon: Throughout 2024 we will be phasing out GitHub Issues as the feedback mechanism for content and replacing it with a new feedback system. For more information see: https://aka.ms/ContentUserFeedback.
Submit and view feedback for