Azure networking monitoring solutions in Azure Monitor
Note
We recommend that you use the Azure Az PowerShell module to interact with Azure. See Install Azure PowerShell to get started. To learn how to migrate to the Az PowerShell module, see Migrate Azure PowerShell from AzureRM to Az.
Azure Monitor offers the following solutions for monitoring your networks:
- Network Performance Monitor to:
- Monitor the health of your network.
- Azure Application Gateway analytics to review:
- Application Gateway logs.
- Application Gateway metrics.
- Solutions to monitor and audit network activity on your cloud network:
Network Performance Monitor
The Network Performance Monitor management solution is a network monitoring solution that monitors the health, availability, and reachability of networks. It's used to monitor connectivity between:
- Public cloud and on-premises.
- Datacenters and user locations like branch offices.
- Subnets that host various tiers of a multi-tiered application.
For more information, see Network Performance Monitor.
Application Gateway analytics
- Enable diagnostics to direct the diagnostics to a Log Analytics workspace in Azure Monitor.
- Consume the detailed summary for your resource by using the workbook template for Application Gateway.
If diagnostic logs aren't enabled for Application Gateway, only the default metric data would be populated within the workbook.
Review Azure networking data collection details
The Application Gateway analytics and the network security group analytics management solutions collect diagnostics logs directly from Application Gateway and network security groups. It isn't necessary to write the logs to Azure Blob Storage, and no agent is required for data collection.
The following table shows data collection methods and other details about how data is collected for Application Gateway analytics and the network security group analytics.
| Platform | Direct agent | Systems Center Operations Manager agent | Azure | Operations Manager required? | Operations Manager agent data sent via management group | Collection frequency |
|---|---|---|---|---|---|---|
| Azure | • | When logged |
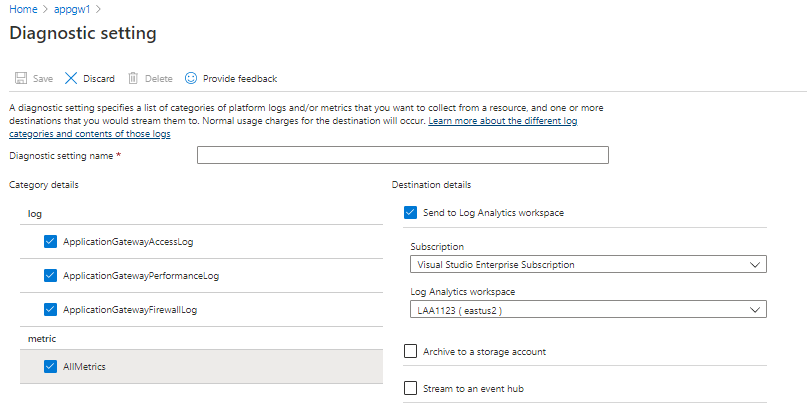
Enable Application Gateway diagnostics in the portal
In the Azure portal, go to the Application Gateway resource to monitor.
Select Diagnostic settings to open the following page.
Select the Send to Log Analytics workspace checkbox.
Select an existing Log Analytics workspace or create a workspace.
Select the checkbox under log for each of the log types to collect.
Select Save to enable the logging of diagnostics to Azure Monitor.
Enable Azure network diagnostics by using PowerShell
The following PowerShell script provides an example of how to enable resource logging for application gateways:
$workspaceId = "/subscriptions/d2e37fee-1234-40b2-5678-0b2199de3b50/resourcegroups/oi-default-east-us/providers/microsoft.operationalinsights/workspaces/rollingbaskets"
$gateway = Get-AzApplicationGateway -Name 'ContosoGateway'
Set-AzDiagnosticSetting -ResourceId $gateway.ResourceId -WorkspaceId $workspaceId -Enabled $true
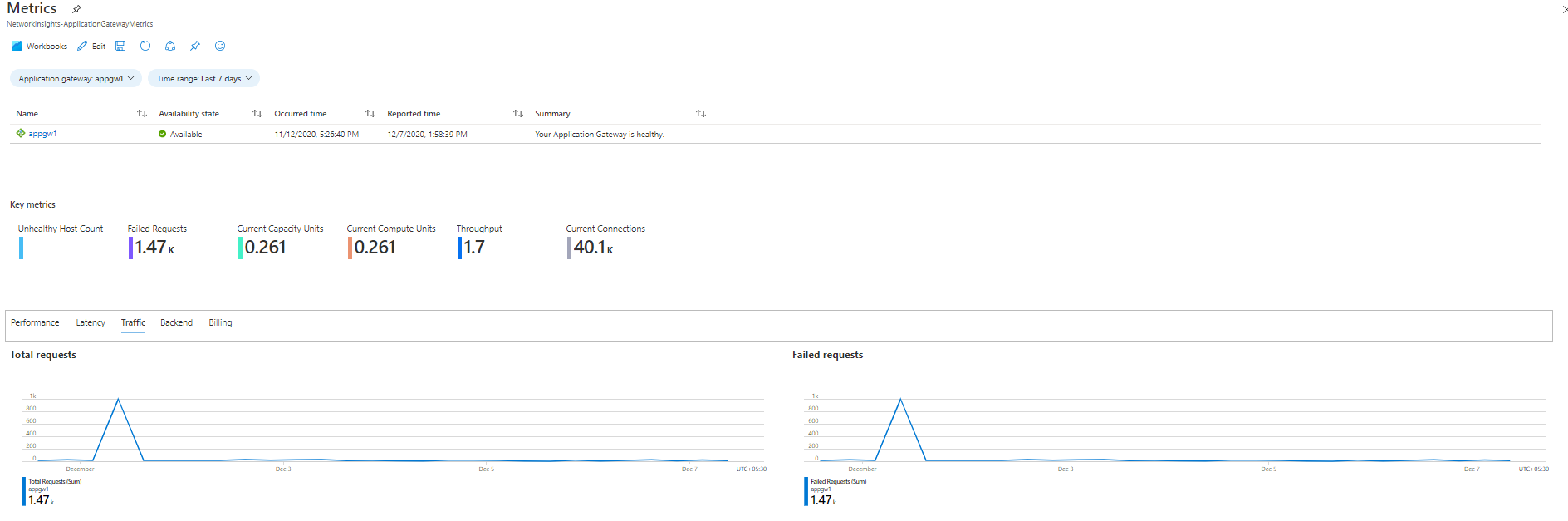
Access Application Gateway analytics via Azure Monitor Network Insights
Application insights can be accessed via the Insights tab in your Application Gateway resource.
The View detailed metrics tab opens the pre-populated workbook that summarizes the data from your Application Gateway resource.
New capabilities with an Azure Monitor Network Insights workbook
Note
No other costs are associated with an Azure Monitor Network Insights workbook. The Log Analytics workspace will continue to be billed per usage.
The Network Insights workbook allows you to take advantage of the latest capabilities of Azure Monitor and Log Analytics, including:
- Centralized console for monitoring and troubleshooting with both metric and log data.
- Flexible canvas to support creation of custom-rich visualizations.
- Ability to consume and share workbook templates with a wider community.
For more information about the capabilities of the new workbook solution, see Workbooks overview.
Migrate from the Azure Gateway analytics solution to Azure Monitor workbooks
Note
We recommend the Azure Monitor Network Insights workbook solution for accessing metric and log analytics for your Application Gateway resources.
Ensure that diagnostics settings are enabled to store logs in a Log Analytics workspace. If it's already configured, the Azure Monitor Network Insights workbook will be able to consume data from the same location. No more changes are required.
Note
All past data is already available within the workbook from the point when diagnostic settings were originally enabled. No data transfer is required.
Access the default insights workbook for your Application Gateway resource. All existing insights supported by the Application Gateway analytics solution will be already present in the workbook. You can add custom visualizations based on metric and log data.
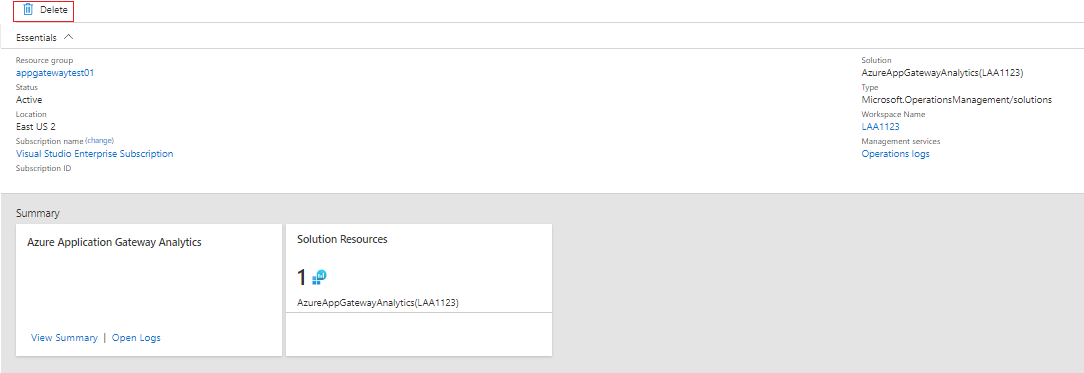
After you see all your metric and log insights, to clean up the Azure Gateway analytics solution from your workspace, delete the solution from the Solution Resources pane.
Troubleshooting
Follow the steps here to troubleshoot Azure Diagnostics.
Troubleshoot Azure Diagnostics
If you receive the following error message, the Microsoft.Insights resource provider isn't registered:
Failed to update diagnostics for 'resource'. {"code":"Forbidden","message":"Please register the subscription 'subscription id' with Microsoft.Insights."}
To register the resource provider, perform the following steps in the Azure portal:
- In the navigation pane on the left, select Subscriptions.
- Select the subscription identified in the error message.
- Select Resource providers.
- Find the microsoft.insights provider.
- Select the Register link.
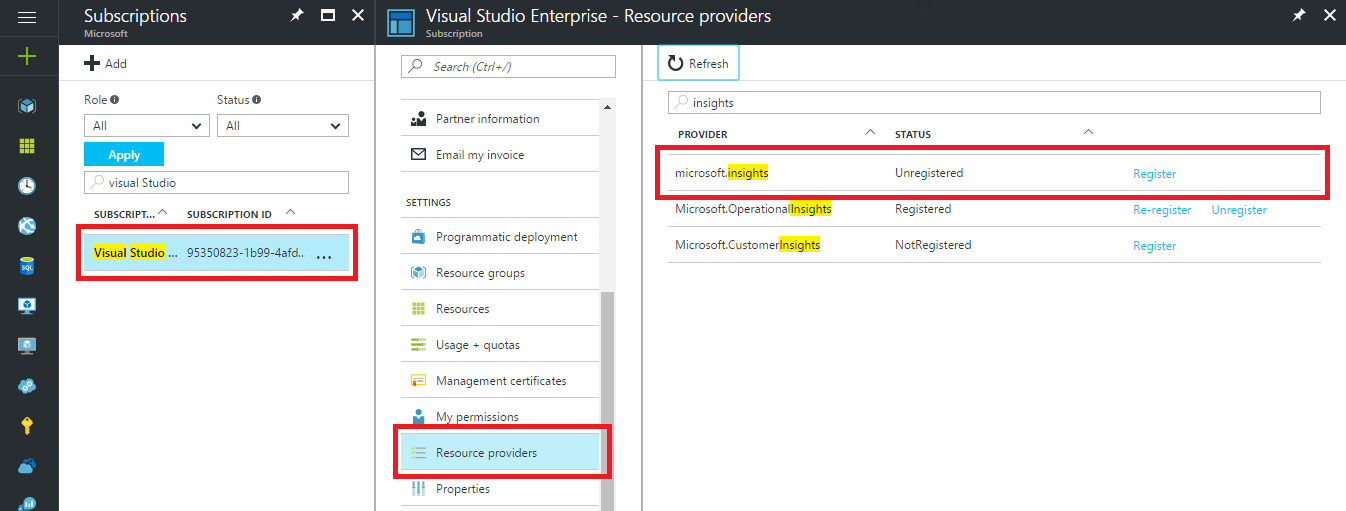
After the Microsoft.Insights resource provider is registered, retry configuring the diagnostics.
In PowerShell, if you receive the following error message, you must update your version of PowerShell:
Set-AzDiagnosticSetting : A parameter cannot be found that matches parameter name 'WorkspaceId'.
To update your version of Azure PowerShell, follow the instructions in Install Azure PowerShell.
Next steps
Use log queries in Azure Monitor to view detailed Azure Diagnostics data.