Connectivity settings for Azure SQL Database and Azure Synapse Analytics
Applies to:
Azure SQL Database
Azure Synapse Analytics (dedicated SQL pools only)
This article introduces settings that control connectivity to the server for Azure SQL Database and dedicated SQL pool (formerly SQL DW) in Azure Synapse Analytics.
- For more information on various components that direct network traffic and connection policies, see connectivity architecture.
- This article does not apply to Azure SQL Managed Instance, instead see Connect your application to Azure SQL Managed Instance.
- This article does not apply to dedicated SQL pools in Azure Synapse Analytics workspaces. See Azure Synapse Analytics IP firewall rules for guidance on how to configure IP firewall rules for Azure Synapse Analytics with workspaces.
Networking and connectivity
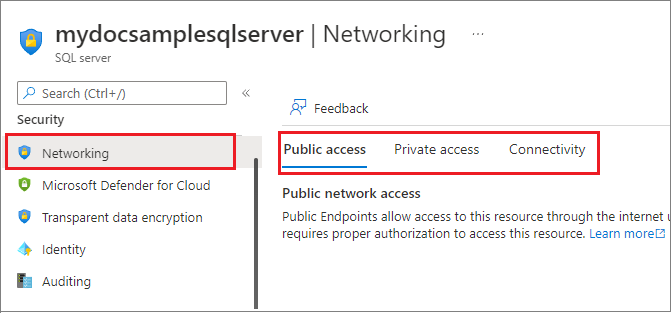
These settings apply to all SQL Database and dedicated SQL pool (formerly SQL DW) databases associated with the server. You can change these settings from the networking tab of your logical server:
Change public network access
It's possible to change the public network access via the Azure portal, Azure PowerShell, and the Azure CLI.
To enable public network access for the logical server hosting your databases, go to the Networking page in the Azure portal for your logical server in Azure, choose the Public access tab, and then set the Public network access to Select networks.
From this page, you can add a virtual network rule, as well as configure firewall rules for your public endpoint.
Choose the Private access tab to configure a private endpoint.
Note
These settings take effect immediately after they're applied. Your customers might experience connection loss if they don't meet the requirements for each setting.
Deny public network access
The default for the Public network access setting is Disable. Customers can choose to connect to a database by using either public endpoints (with IP-based server-level firewall rules or with virtual-network firewall rules), or private endpoints (by using Azure Private Link), as outlined in the network access overview.
When Public network access is set to Disable, only connections from private endpoints are allowed. All connections from public endpoints will be denied with an error message similar to:
Error 47073
An instance-specific error occurred while establishing a connection to SQL Server.
The public network interface on this server is not accessible.
To connect to this server, use the Private Endpoint from inside your virtual network.
When Public network access is set to Disable, any attempts to add, remove, or edit any firewall rules will be denied with an error message similar to:
Error 42101
Unable to create or modify firewall rules when public network interface for the server is disabled.
To manage server or database level firewall rules, please enable the public network interface.
Ensure that Public network access is set to Selected networks to be able to add, remove, or edit any firewall rules for Azure SQL Database and Azure Synapse Analytics.
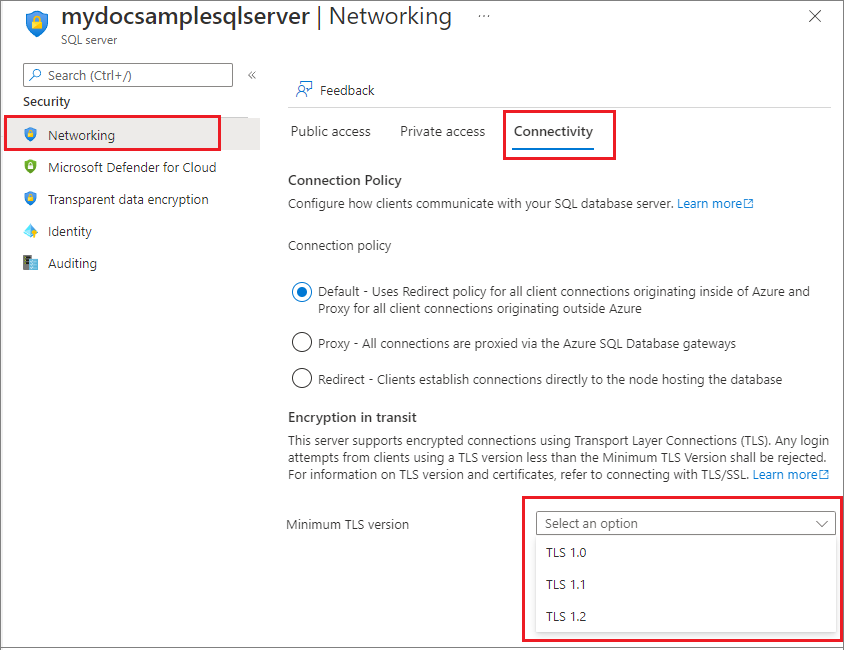
Minimal TLS version
The minimal Transport Layer Security (TLS) version setting allows customers to choose which version of TLS their SQL database uses. It's possible to change the minimum TLS version by using the Azure portal, Azure PowerShell, and the Azure CLI.
Currently, we support TLS 1.0, 1.1, and 1.2. Setting a minimal TLS version ensures that newer TLS versions are supported. For example, choosing a TLS version 1.1 means only connections with TLS 1.1 and 1.2 are accepted, and connections with TLS 1.0 are rejected. After you test to confirm that your applications support it, we recommend setting the minimal TLS version to 1.2. This version includes fixes for vulnerabilities in previous versions and is the highest version of TLS that's supported in Azure SQL Database.
Important
The default for the minimal TLS version is to allow all versions. After you enforce a version of TLS, it's not possible to revert to the default.
For customers with applications that rely on older versions of TLS, we recommend setting the minimal TLS version according to the requirements of your applications. If application requirements are unknown or workloads rely on older drivers that are no longer maintained, we recommend not setting any minimal TLS version.
For more information, see TLS considerations for SQL Database connectivity.
After you set the minimal TLS version, customers who are using a TLS version lower than the minimum TLS version of the server will fail to authenticate, with the following error:
Error 47072
Login failed with invalid TLS version
Note
When you configure a minimum TLS version, that minimum version is enforced at the application layer. Tools that attempt to determine TLS support at the protocol layer might return TLS versions in addition to the minimum required version when run directly against the SQL Database endpoint.
In the Azure portal, go to your SQL server resource. Under the Security settings, select Networking and then choose the Connectivity tab. Select the Minimum TLS Version desired for all databases associated with the server, and select Save.
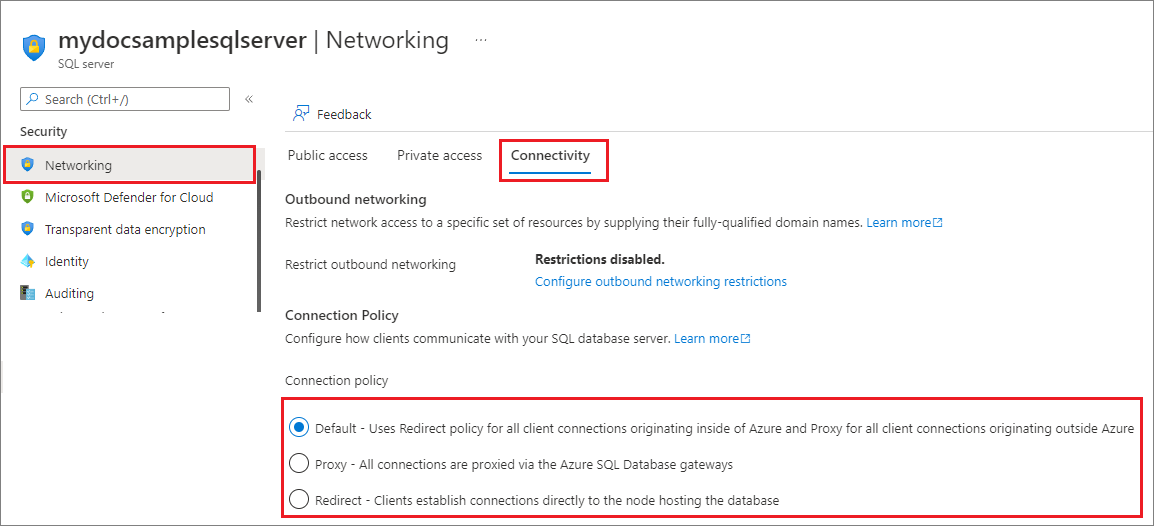
Change the connection policy
Connection policy determines how customers connect to Azure SQL Database.
We highly recommend the Redirect connection policy over the Proxy connection policy for the lowest latency and highest throughput.
It's possible to change the connection policy by using the Azure portal, Azure PowerShell, and the Azure CLI.
It's possible to change your connection policy for your logical server by using the Azure portal.
In the Azure portal, go to your SQL server resource. Under the Security settings, select Networking and then choose the Connectivity tab. Choose the desired connection policy, and select Save.
Related content
Feedback
Coming soon: Throughout 2024 we will be phasing out GitHub Issues as the feedback mechanism for content and replacing it with a new feedback system. For more information see: https://aka.ms/ContentUserFeedback.
Submit and view feedback for