Replicate a DNS outage by using the NSG fault
The network security group (NSG) fault enables you to modify your existing NSG rules as part of a chaos experiment in Azure Chaos Studio. By using this fault, you can block network traffic to your Azure resources and simulate a loss of connectivity or outages of dependent resources.
This article walks you through creating a chaos experiment that blocks all traffic to external (internet) DNS servers for 15 minutes. You can validate that resources connected to the Azure virtual network associated with the target NSG don't have a dependency on external DNS servers. In this way, you can validate one of the risk-threat model requirements.
Prerequisites
- An NSG that's associated with the Azure resource you want to target in your experiment.
- Use the Bash environment in Azure Cloud Shell.
Create the NSG fault provider
First, you register a fault provider on the subscription where your NSG is hosted for Chaos Studio to interact with it.
Create a file named AzureNetworkSecurityGroupChaos.json with the following contents and save it to your local machine:
{ "properties": { "enabled": true, "providerConfiguration": { "type": "AzureNetworkSecurityGroupChaos" } } }Open an instance of Cloud Shell.
Replace
$SUBSCRIPTION_IDwith the Azure subscription ID that contains the NSG you want to use in your experiment. Run the following command to ensure that the provider is registered on the correct subscription:az account set --subscription $SUBSCRIPTION_IDDrag and drop AzureNetworkSecurityGroupChaos.json into the Cloud Shell window to upload the file.
Replace
$SUBSCRIPTION_IDused in the prior step and execute the following command to register theAzureNetworkSecurityGroupChaosfault provider:az rest --method put --url "https://management.azure.com/subscriptions/$SUBSCRIPTION_ID/providers/microsoft.chaos/chaosProviderConfigurations/AzureNetworkSecurityGroupChaos?api-version=2023-11-01" --body @AzureNetworkSecurityGroupChaos.json --resource "https://management.azure.com"(Optional) Delete the AzureNetworkSecurityGroupChaos.json file you previously created because it's no longer required. Close Cloud Shell.
Create a chaos experiment
After the NSG fault provider is created, you can start to create experiments in Chaos Studio.
Open the Azure portal with the Chaos Studio feature flag:
- If you're using an @microsoft.com account, go to this website.
- If you're using an external account, go to this website.
Select Add an experiment.
Enter the name you want to give the experiment and select the Subscription, Resource group, and Location (region) where you want to create the experiment.
Select Next: Experiment designer.

Select Add fault.
Select Network Security Group Fault from the Faults dropdown list.

Populate the following parameters.
Parameter Value Duration 15Name block_internet_dnsSource Address Prefix *Destination Address Prefix InternetAccess DenySource Port Range *Destination Port Range 53Priority 1001Direction Outbound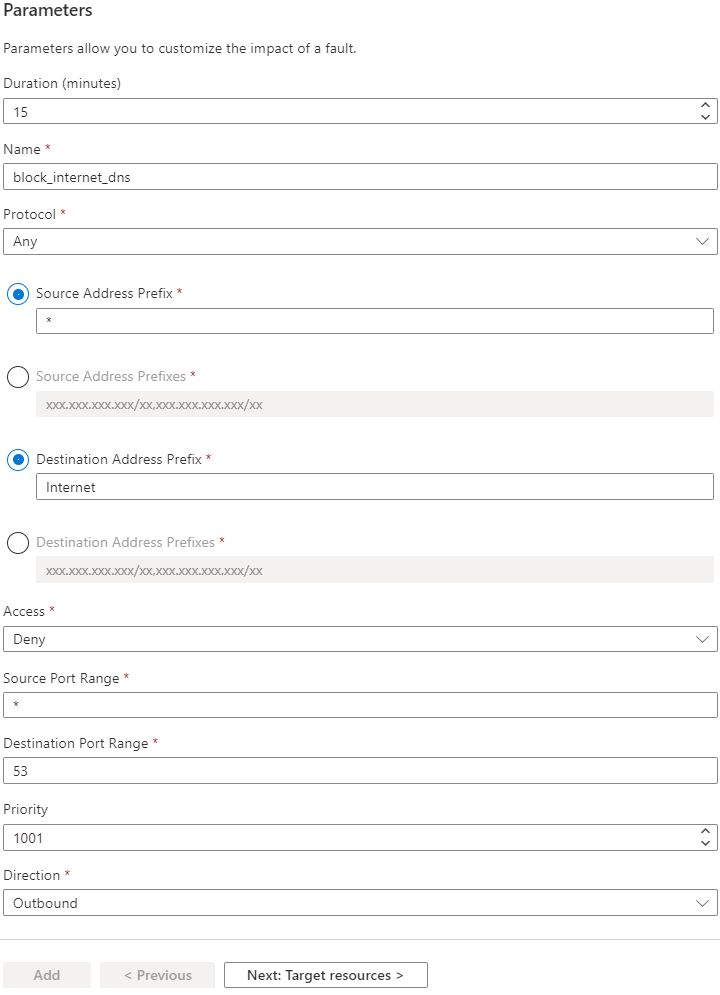
The Name and Priority fields might need to be adjusted if either one already exists in a preexisting rule on the target NSG.
Note
The priority might need to be lowered if there are any rules that explicitly allow port 53 traffic to the internet.
Select Next: Target resources.
Select the NSGs to be targeted by this experiment.
Select Add.

Select Review + Create.

Select Create.
Grant the chaos experiment access to the network security group
As a safety precaution, all chaos experiments must be granted access to the Azure resources targeted in the experiment.
Go to the resources targeted in the experiment.
Select Access Control (IAM).
Select Add.
Select Add role assignment.
In Role, select
Network Contributor.
In Select, enter the name of the chaos experiment and then select it.
Select Save.

Run the chaos experiment
Open the Azure portal with the Chaos Studio feature flag:
- If you're using an @microsoft.com account, go to this website.
- If you're using an external account, go to this website.
Select the checkbox next to the experiment name and select Start Experiment.

Select Yes to confirm you want to start the chaos experiment.

(Optional) Select the experiment name to see a detailed view of the execution status of the experiment.
After the experiment starts, you can use your existing monitoring, telemetry, or logging tools to confirm what effect the execution chaos experiment has had on your service.
Clean up resources
If you're not going to continue to use this experiment and want to delete it:
Open the Azure portal with the Chaos Studio feature flag:
- If you're using an @microsoft.com account, go to this website.
- If you're using an external account, go to this website.
Select the checkbox next to the experiment name and select Delete.
Select Yes to confirm that you want to delete the experiment.
If you're not going to continue using any faults related to NSGs:
Open an instance of Cloud Shell.
Replace $SUBSCRIPTION_ID with the Azure subscription ID where the NSG fault provider was provisioned. Run the following command:
az rest --method delete --url "https://management.azure.com/subscriptions/$SUBSCRIPTION_ID/providers/microsoft.chaos/chaosProviderConfigurations/AzureNetworkSecurityGroupChaos?api-version=2023-11-01" --resource "https://management.azure.com"
Feedback
Coming soon: Throughout 2024 we will be phasing out GitHub Issues as the feedback mechanism for content and replacing it with a new feedback system. For more information see: https://aka.ms/ContentUserFeedback.
Submit and view feedback for