Conditional access
Azure Databricks supports Microsoft Entra ID (formerly Azure Active Directory) conditional access, which allows administrators to control where and when users are permitted to sign in to Azure Databricks. For example, conditional access policies can restrict sign-in to your corporate network or can require multi-factor authentication. For more information about conditional access, see What is Conditional Access?.
This article describes how to enable conditional access for Azure Databricks.
Requirements
- This feature requires the Premium plan.
- Conditional access is available only in Microsoft Entra ID Premium. See Microsoft Entra Plans and Pricing for details.
- You must be a Conditional Access Administrator or Global Administrator of your Microsoft Entra ID. See Microsoft Entra built-in roles for details.
Enable conditional access for Azure Databricks
In the Azure portal, click the Microsoft Entra ID service.
Click Conditional access in the SECURITY section.
Click New policy to create a new conditional access policy.
In Cloud apps, click Select apps, and then search for the application ID 2ff814a6-3304-4ab8-85cb-cd0e6f879c1d. Select AzureDatabricks.
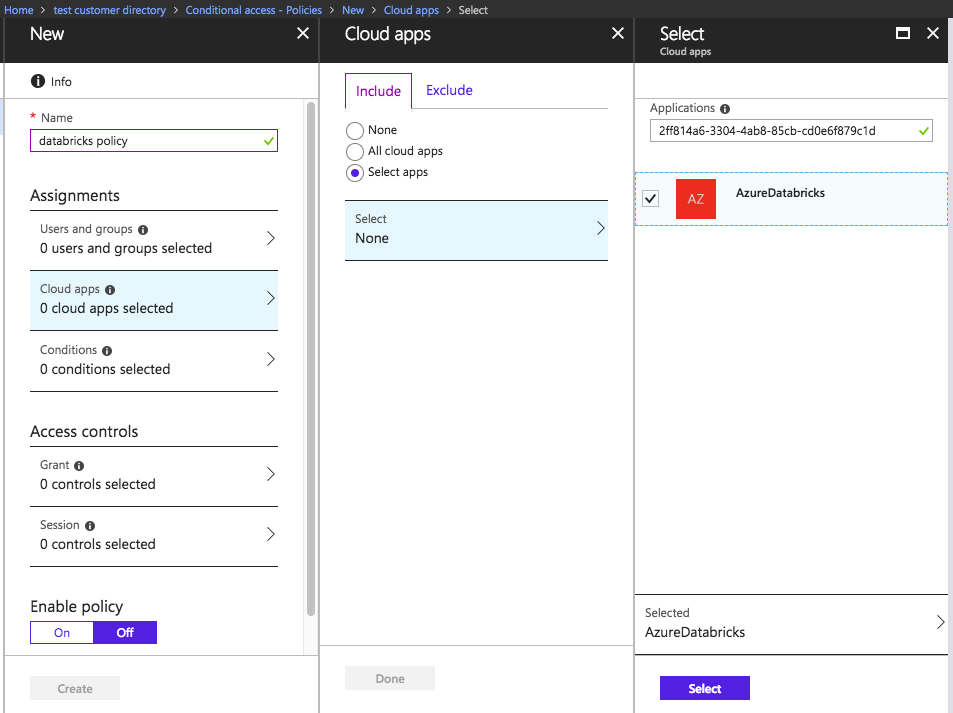
Enter the remaining settings according to your preferred conditional access configuration. See the Microsoft Entra Conditional Access documentation for tutorials and more information.
Feedback
Coming soon: Throughout 2024 we will be phasing out GitHub Issues as the feedback mechanism for content and replacing it with a new feedback system. For more information see: https://aka.ms/ContentUserFeedback.
Submit and view feedback for