Opt-in to receive notifications related to personal access tokens found in a GitHub public repository
Currently, when we discover a personal access token checked into a GitHub public repository, we send a detailed email notification to the token owner and log an event to your Azure DevOps Organization’s Audit Log. With this update, we've added the option for project collection administrators to opt-in to get notifications when a personal access token for a user that belongs to their organization is found in a GitHub public repository. This will help project collection administrators to know when there are leaked tokens that can compromise their Azure DevOps accounts and data.
Check out the release notes for details.
General
- Project Collection Administrators can opt-in for notifications related to personal access tokens found in a GitHub public repository
- Enforcing security validation for all Azure DevOps requests
Azure Boards
Azure Pipelines
- Support Group Managed Service Accounts as agent service account
- Informational runs
- Build Definition REST API
retentionRulesproperty is obsolete
General
Project Collection Administrators can opt-in for notifications related to personal access tokens found in a GitHub public repository
Project Collection Administrators can now opt-in to receive notifications when a personal access token (PAT) belonging to a user in their organization is found in a GitHub public repository.
As a reminder, the Azure DevOps security team, in collaboration with our partners at GitHub, scan for Azure DevOps PATs checked into public repositories on GitHub and sends an email notification to the owner of the token, if one is found in a GitHub public repository. This is also logged in the Azure DevOps organization's Audit Log.
Project Collection Administrators can subscribe to these notifications by navigating to User Settings -> Notifications -> New Subscription
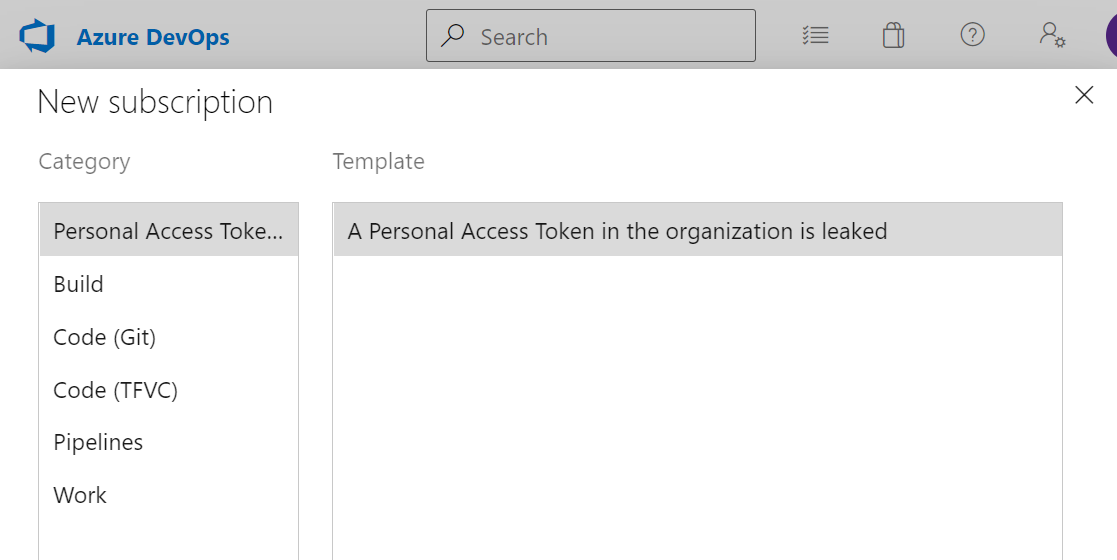
Enforcing security validation for all Azure DevOps requests
Azure DevOps will be closing a prior vulnerability that allowed certain users to bypass some security validation when using the X-TFS-FedAuthRedirect header to make calls to Azure DevOps resources. Now, all users who use this X-TFS-FedAuthRedirect header must always be in compliance with any Azure Active Directory policies set by their tenant and regularly sign in to their Azure DevOps accounts to ensure they always have an active user session.
If you have been using this header and are considered non-compliant, you may experience 401s when making calls with X-TFS-FedAuthRedirect. The recommended action for those using this header would be to ensure that your account meets all required admin policies, sign in again to Azure DevOps to get a new user session, and continue signing into to Azure DevOps at least once every 90 days, or the duration of any sign-in frequency checks set by your tenant admins.
This may also apply to users of Visual Studio, as the product may also make calls using the X-TFS-FedAuthRedirect header behind-the-scenes. If you come across 401s in the Visual Studio product (i.e. any banners or error messages blocking access to Azure DevOps resources), the same advice above applies. Please ensure that your account meets admin policies, sign in to Azure DevOps again, and continue doing so on a regular cadence to avoid interruptions.
Azure Boards
Assigned To children in Kanban cards
We have added the Assigned To avatar to all child items on the Kanban board cards. This now makes it easier to understand what items have been assigned and to whom. You can also use the context menu to quickly assign the work item.
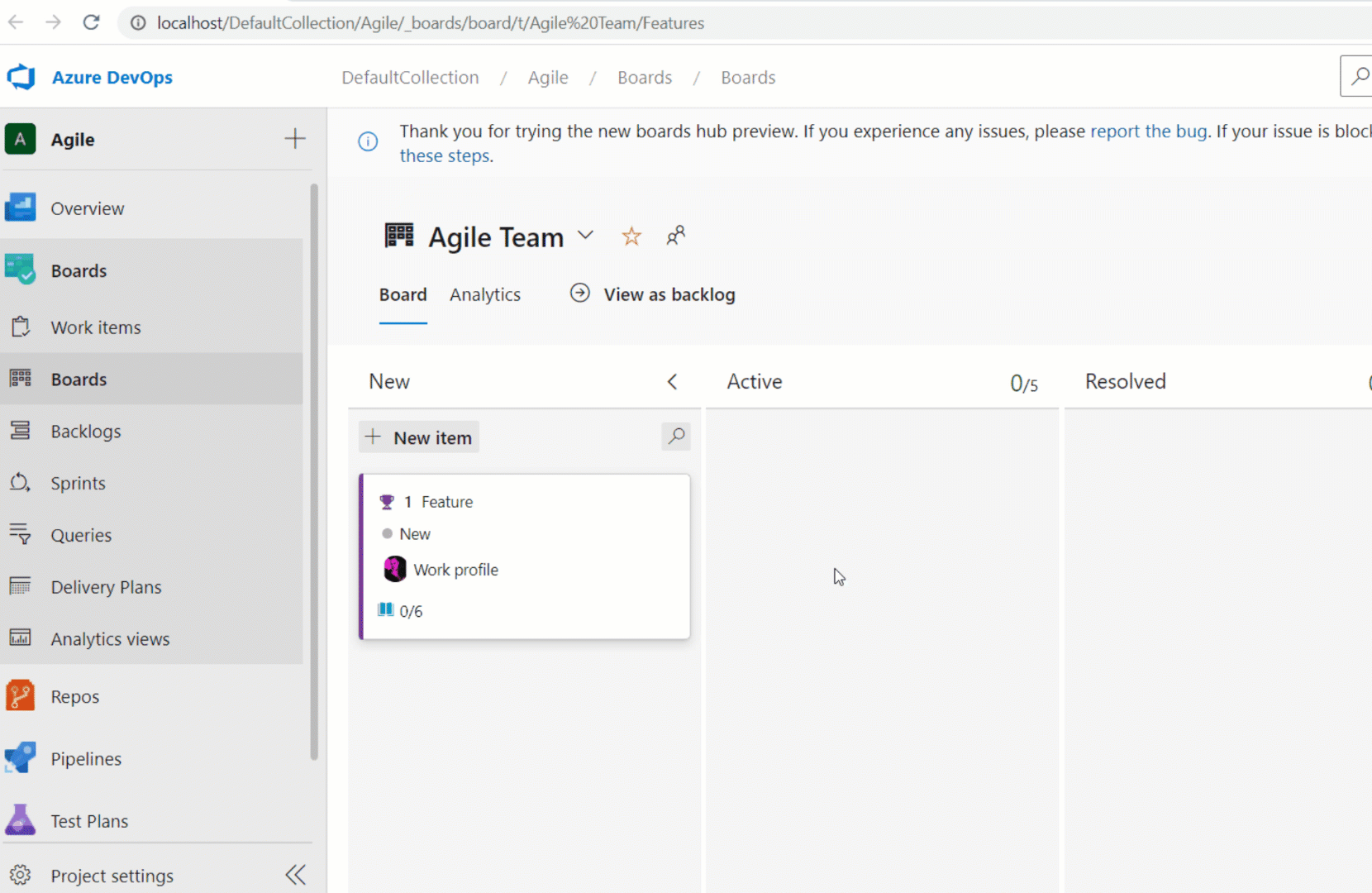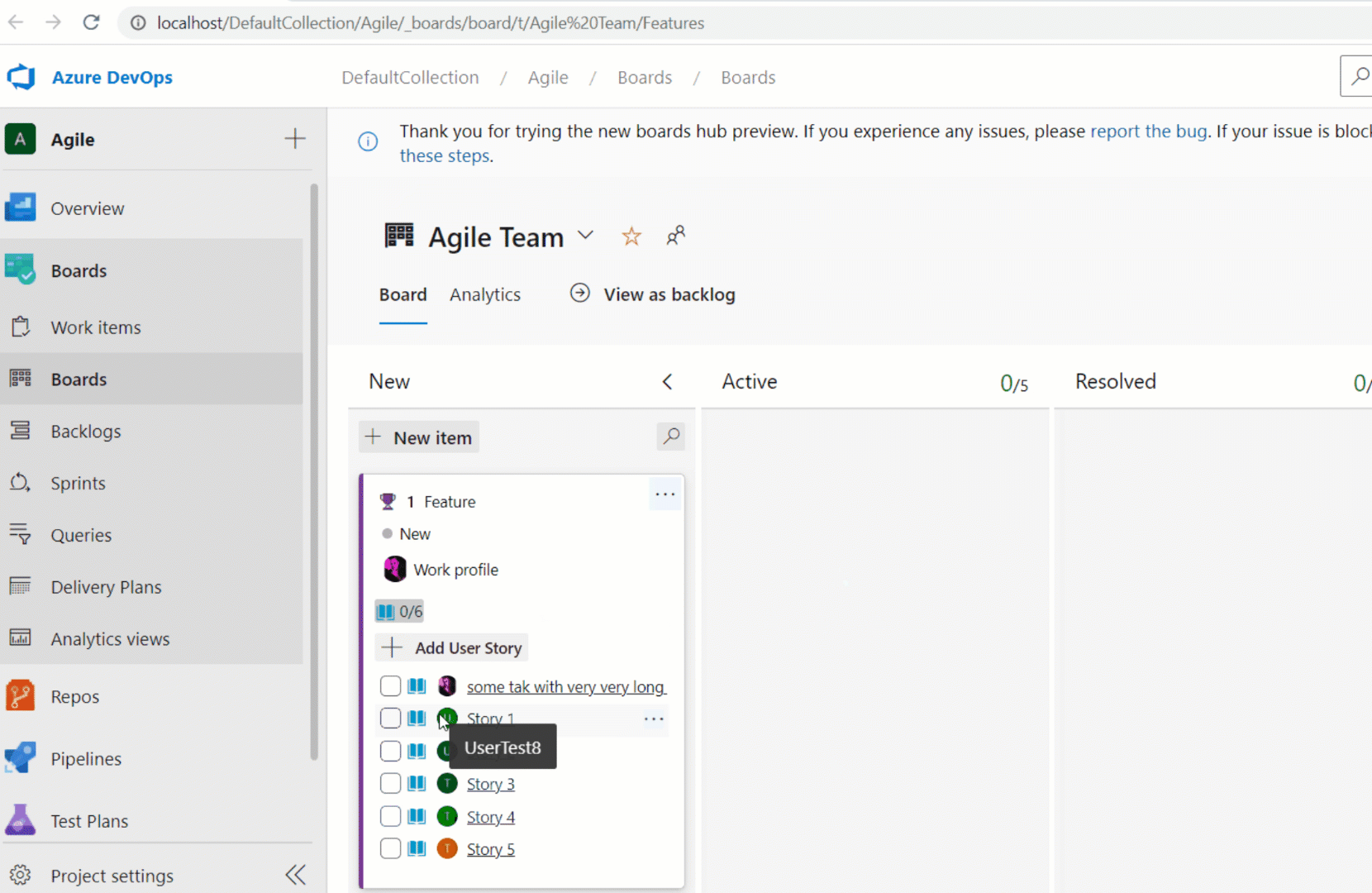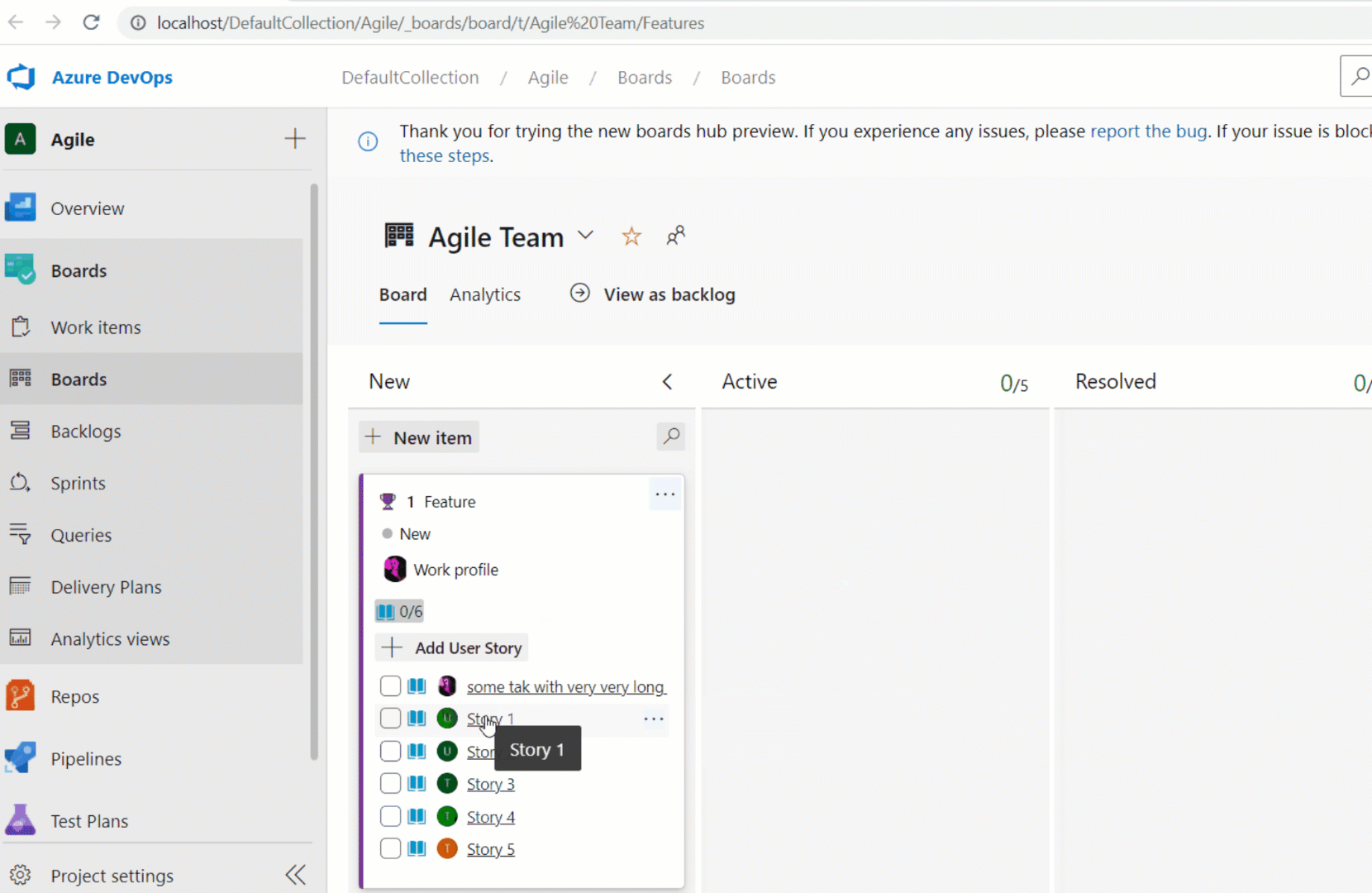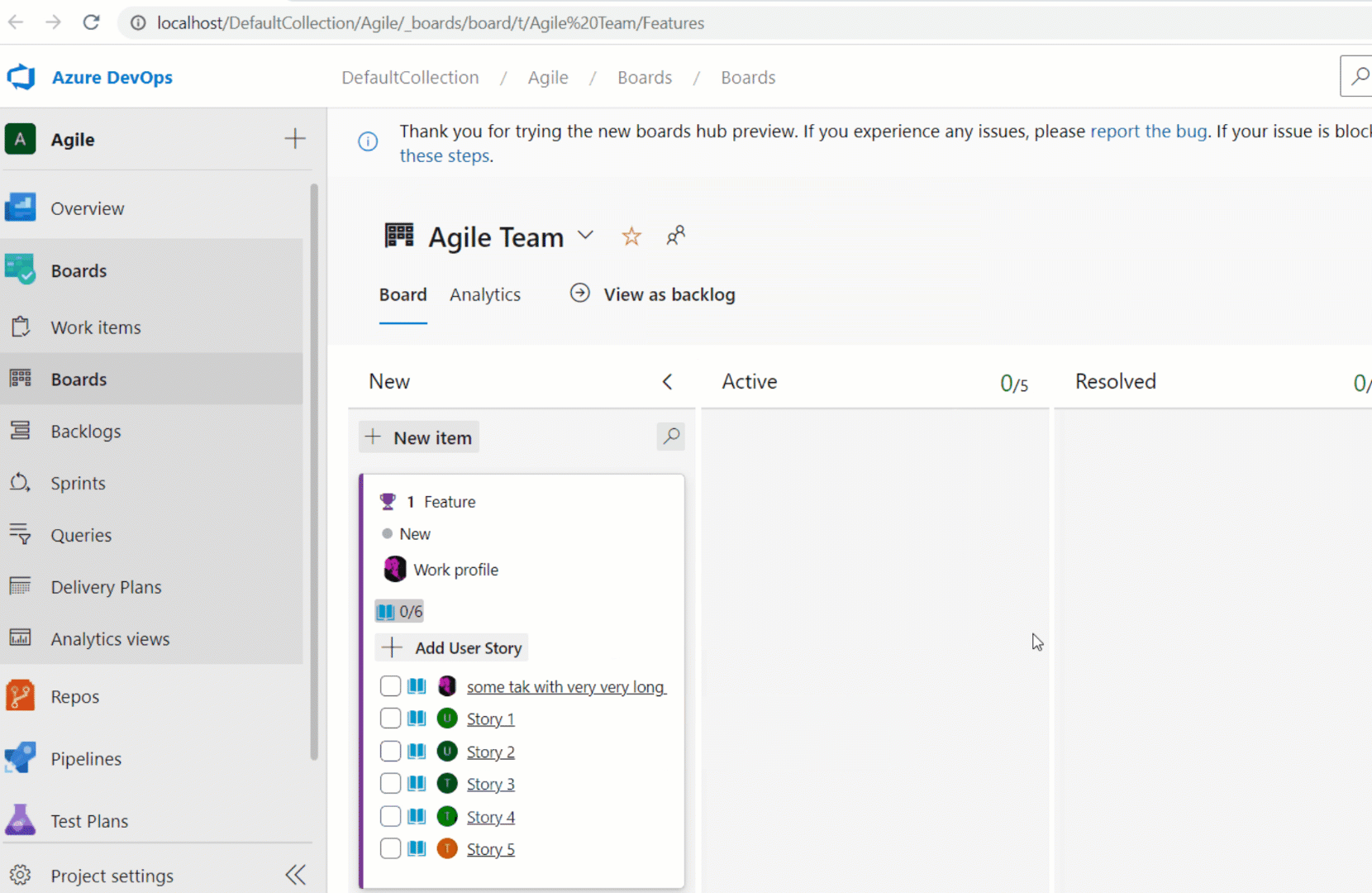
Note
This feature is available with the New Boards Hubs preview.
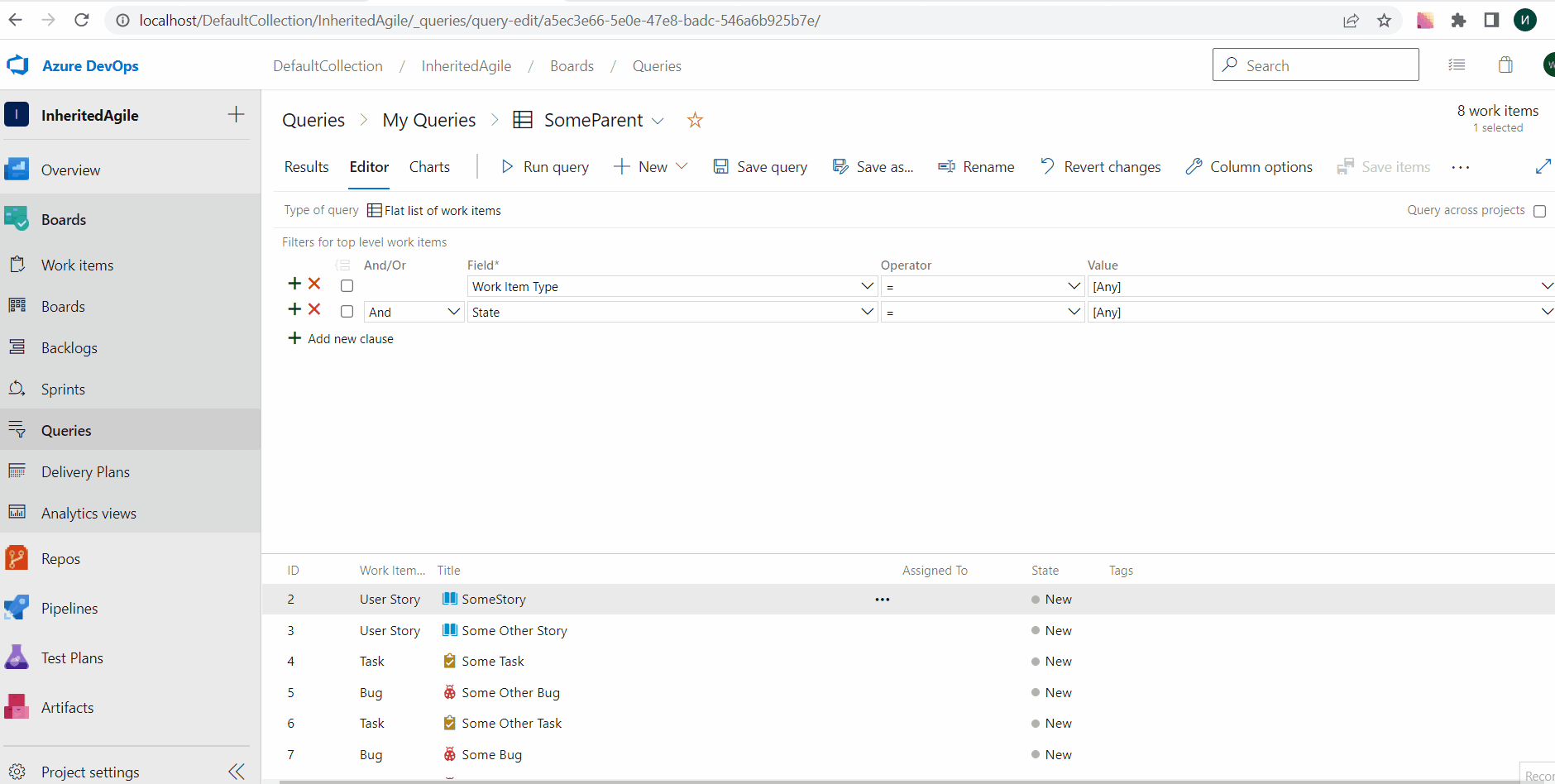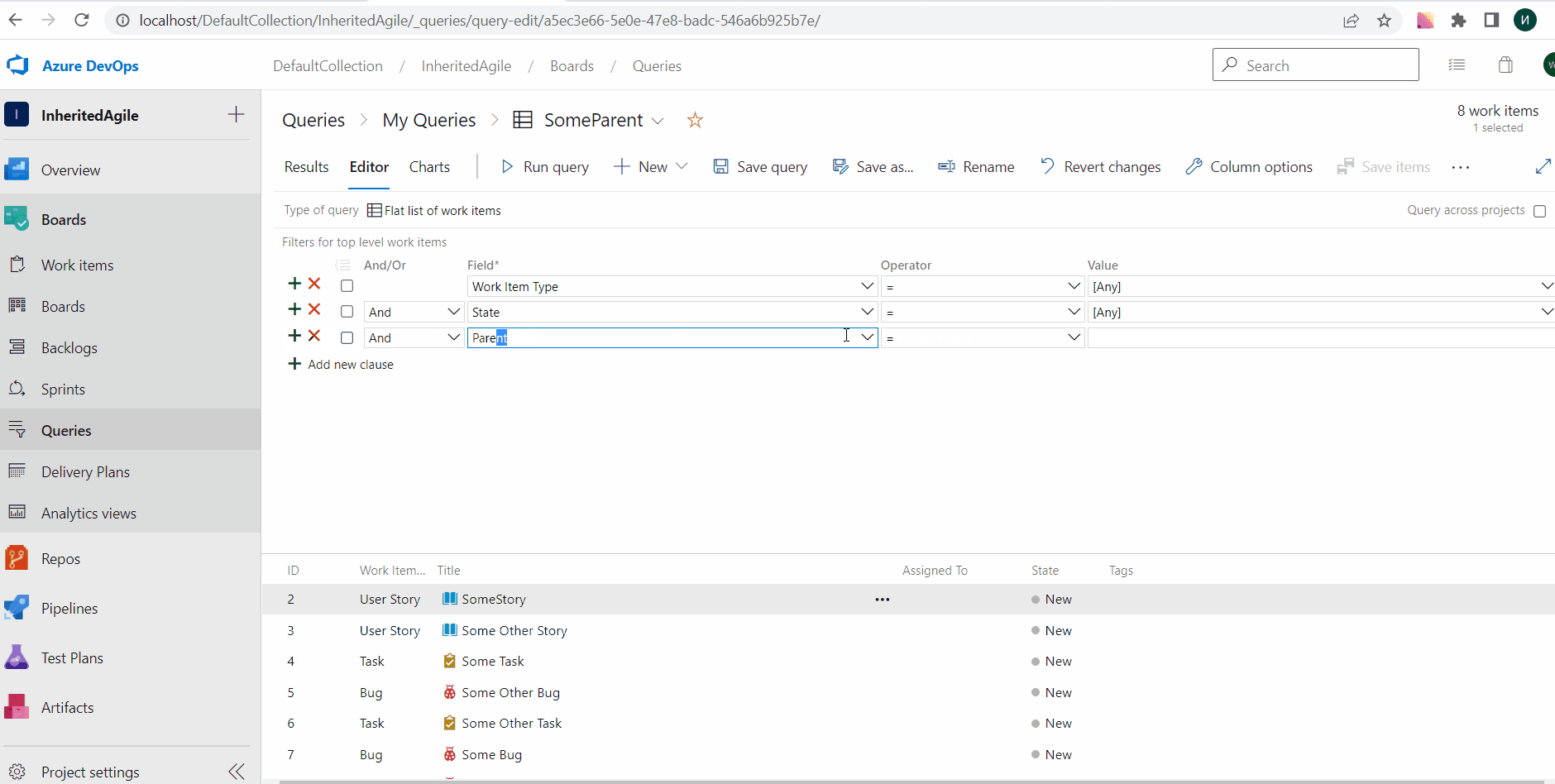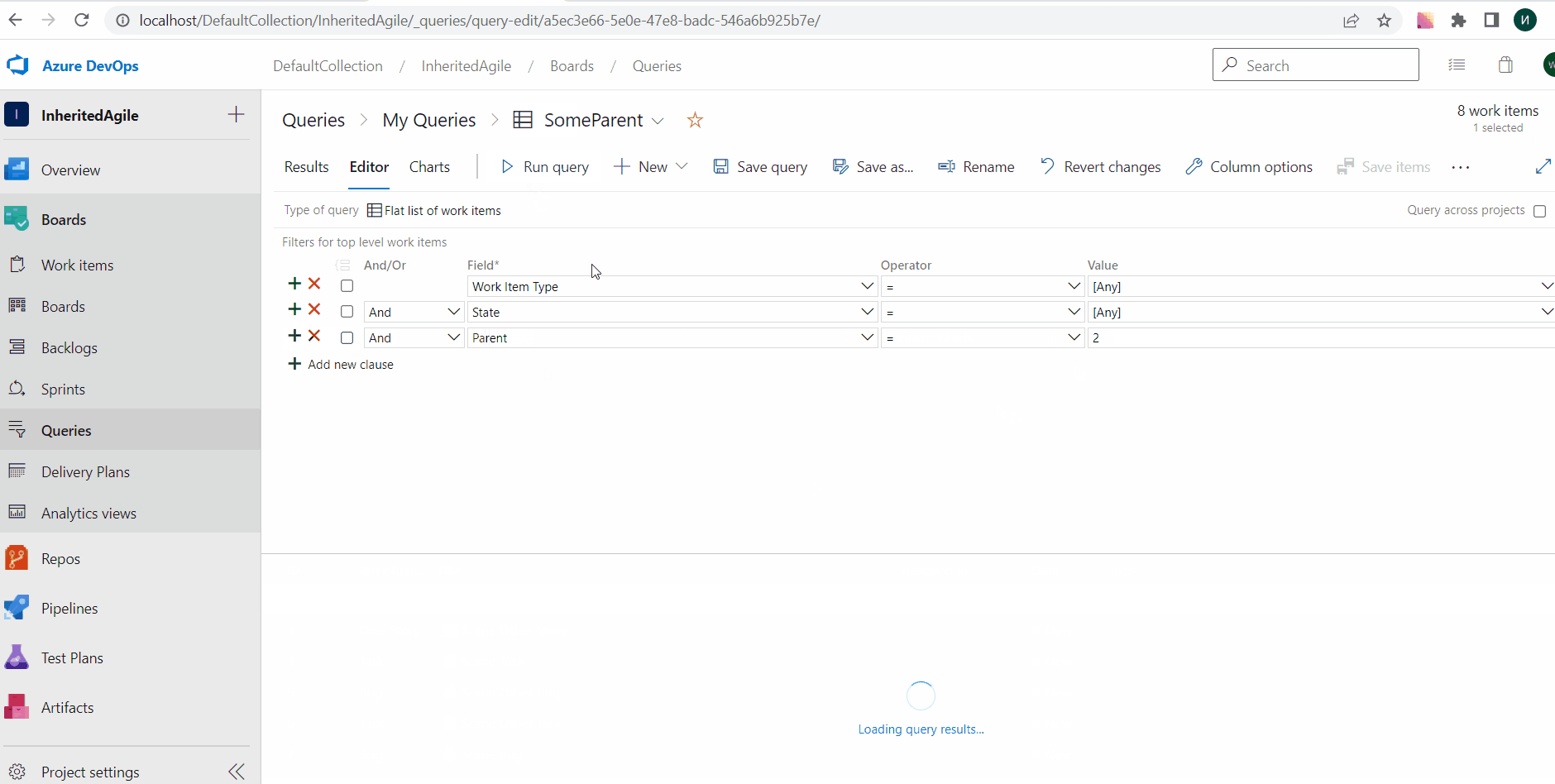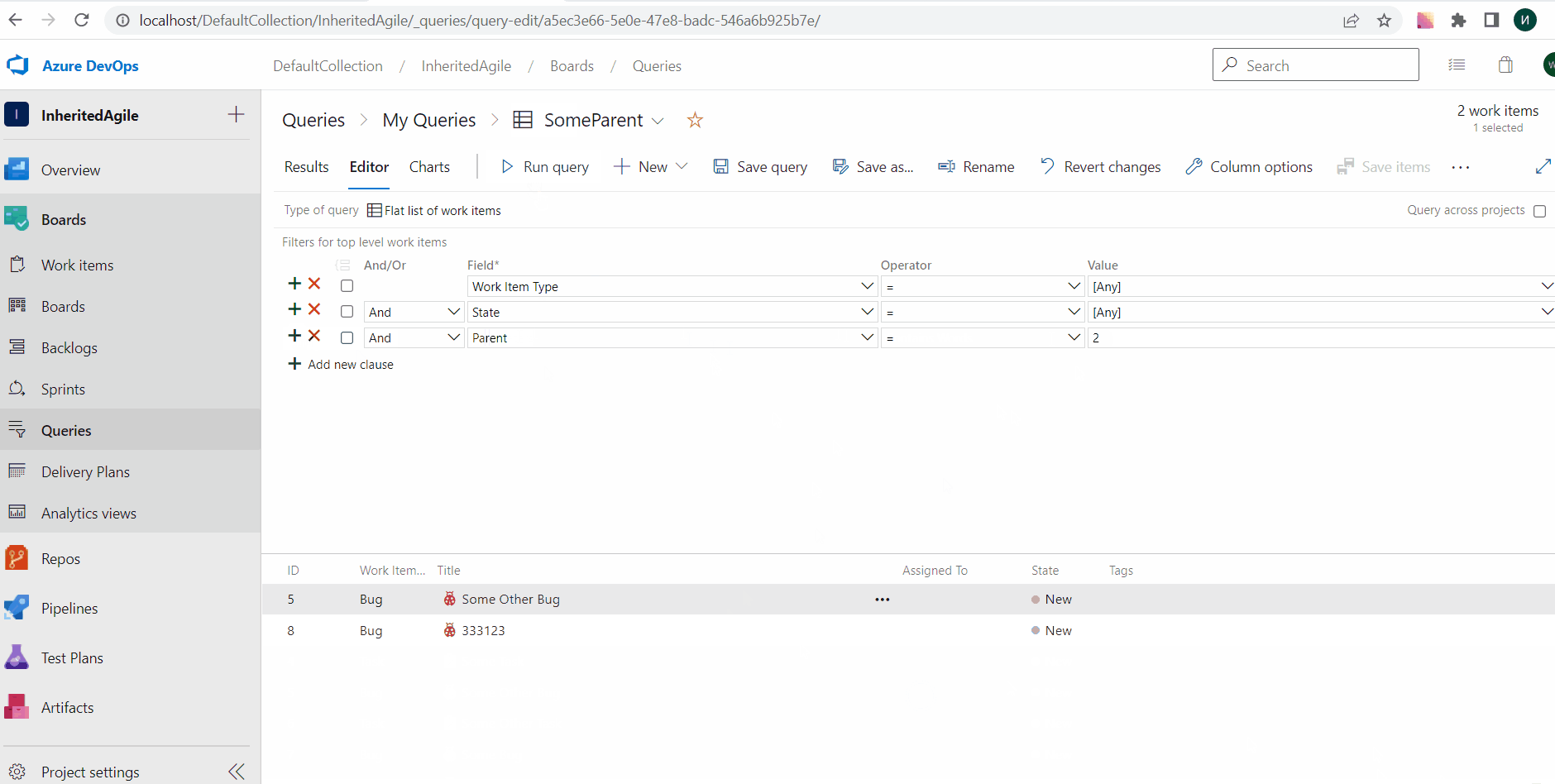
General availability of Query by Parent Id
With this update, we are generally releasing the ability to query work items by Parent Id. This is a great feature if you are looking for ways to get a flat list of children based on the parent.
Azure Pipelines
Support Group Managed Service Accounts as agent service account
The Azure Pipelines agent now supports Group Managed Service Accounts on Self-hosted agents on Windows.
Group Managed Service Accounts (gSMAs) provide centralized password management for domain accounts that act as service accounts. The Azure Pipelines Agent can recognize this type of account so a password is not required during configuration:
.\config.cmd --url https://dev.azure.com/<Organization> `
--auth pat --token <PAT> `
--pool <AgentPool> `
--agent <AgentName> --replace `
--runAsService `
--windowsLogonAccount <DOMAIN>\<gMSA>
Informational runs
An informational run tells you Azure DevOps failed to retrieve a YAML pipeline's source code. Such a run looks like the following.
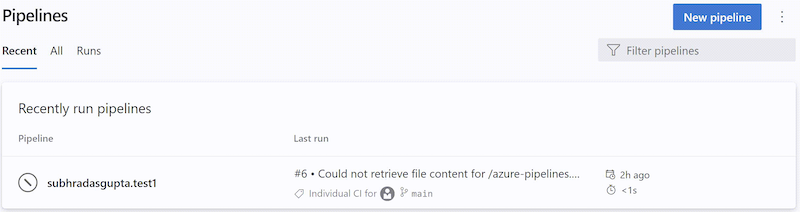
Azure DevOps retrieves a YAML pipeline's source code in response to external events, for example, a pushed commit, or in response to internal triggers, for example, to check if there are code changes and start a scheduled run or not. When this step fails, the system creates an informational run. These runs are created only if the pipeline's code is in a GitHub or BitBucket repository.
Retrieving a pipeline's YAML code can fail due to:
- Repository provider experiencing an outage
- Request throttling
- Authentication issues
- Unable to retrieve the content of the pipeline's .yml file
Read more about Informational runs.
Build Definition REST API retentionRules property is obsolete
In the Build Definition REST API's BuildDefinition response type, the retentionRules property is now marked as obsolete, as this property always returns an empty set.
Next steps
Note
These features will roll out over the next two to three weeks.
Head over to Azure DevOps and take a look.
How to provide feedback
We would love to hear what you think about these features. Use the help menu to report a problem or provide a suggestion.
You can also get advice and your questions answered by the community on Stack Overflow.
Thanks,
Aaron Hallberg
Feedback
Coming soon: Throughout 2024 we will be phasing out GitHub Issues as the feedback mechanism for content and replacing it with a new feedback system. For more information see: https://aka.ms/ContentUserFeedback.
Submit and view feedback for