Deliver events using private link service
Pull delivery supports consuming events using private links. Pull delivery is a feature of Event Grid namespaces. Once you have added a private endpoint connection to a namespace, your consumer application can connect to Event Grid on a private endpoint to receive events. For more information, see configure private endpoints for namespaces and pull delivery overview.
With push delivery isn't possible to deliver events using private endpoints. That is, with push delivery, either in Event Grid basic or Event Grid namespaces, your application can't receive events over private IP space. However, there's a secure alternative using managed identities with public endpoints.
Use managed identity
If you're using Event Grid basic and your requirements call for a secure way to send events using an encrypted channel and a known identity of the sender (in this case, Event Grid) using public IP space, you could deliver events to Event Hubs, Service Bus, or Azure Storage service using an Azure Event Grid custom topic or a domain with system-assigned or user-assigned managed identity. For details about delivering events using managed identity, see Event delivery using a managed identity.
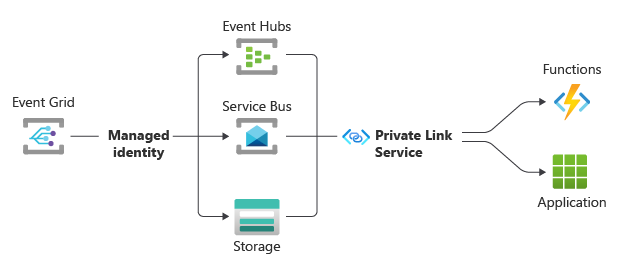
Under this configuration, the secured traffic from Event Grid to Event Hubs, Service Bus, or Azure Storage, stays on the Microsoft backbone and a managed identity of Event Grid is used. Configuring your Azure Function or webhook from within your virtual network to use an Event Hubs, Service Bus, or Azure Storage via private link ensures the traffic between those services and your function or webhook stays within your virtual network perimeter.
Deliver events to Event Hubs using managed identity
To deliver events to event hubs in your Event Hubs namespace using managed identity, follow these steps:
- Enable system-assigned or user-assigned managed identity: system topics, custom topics, and domains.
- Add the identity to the Azure Event Hubs Data Sender role on the Event Hubs namespace.
- Enable the Allow trusted Microsoft services to bypass this firewall setting on your Event Hubs namespace.
- Configure the event subscription that uses an event hub as an endpoint to use the system-assigned or user-assigned managed identity.
Deliver events to Service Bus using managed identity
To deliver events to Service Bus queues or topics in your Service Bus namespace using managed identity, follow these steps:
- Enable system-assigned or user-assigned managed identity: system topics, custom topics, and domains.
- Add the identity to the Azure Service Bus Data Sender role on the Service Bus namespace
- Enable the Allow trusted Microsoft services to bypass this firewall setting on your Service Bus namespace.
- Configure the event subscription that uses a Service Bus queue or topic as an endpoint to use the system-assigned or user-assigned managed identity.
Deliver events to Storage using managed identity
To deliver events to Storage queues using managed identity, follow these steps:
- Enable system-assigned or user-assigned managed identity: system topics, custom topics, and domains.
- Add the identity to the Storage Queue Data Message Sender role on Azure Storage queue.
- Configure the event subscription that uses a Storage queue as an endpoint to use the system-assigned or user-assigned managed identity.
Firewall and virtual network rules
If there's no firewall or virtual network rules configured for the destination Storage account, Event Hubs namespace, or Service Bus namespace, you can use both user-assigned and system-assigned identities to deliver events.
If a firewall or virtual network rule is configured for the destination Storage account, Event Hubs namespace, or Service Bus namespace, you can use only the system-assigned managed identity if Allow Azure services on the trusted service list to access the storage account is also enabled on the destinations. You can't use user-assigned managed identity whether this option is enabled or not.
Next steps
For more information about delivering events using a managed identity, see Event delivery using a managed identity.
Feedback
Coming soon: Throughout 2024 we will be phasing out GitHub Issues as the feedback mechanism for content and replacing it with a new feedback system. For more information see: https://aka.ms/ContentUserFeedback.
Submit and view feedback for