What is Azure Firewall?
Azure Firewall is a cloud-native and intelligent network firewall security service that provides the best of breed threat protection for your cloud workloads running in Azure. It's a fully stateful firewall as a service with built-in high availability and unrestricted cloud scalability. It provides both east-west and north-south traffic inspection. To learn what's east-west and north-south traffic, see East-west and north-south traffic.
Azure Firewall is offered in three SKUs: Standard, Premium, and Basic.
Azure Firewall Standard
Azure Firewall Standard provides L3-L7 filtering and threat intelligence feeds directly from Microsoft Cyber Security. Threat intelligence-based filtering can alert and deny traffic from/to known malicious IP addresses and domains that are updated in real time to protect against new and emerging attacks.
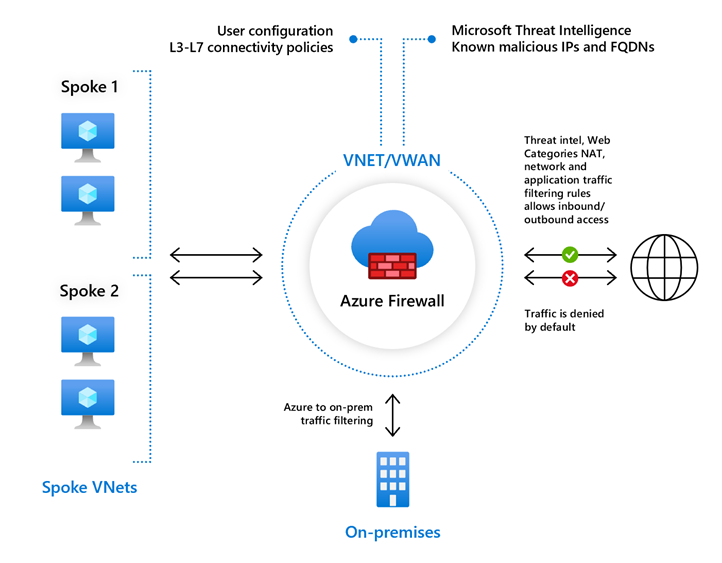
To learn about Firewall Standard features, see Azure Firewall Standard features.
Azure Firewall Premium
Azure Firewall Premium provides advanced capabilities include signature based IDPS to allow rapid detection of attacks by looking for specific patterns. These patterns can include byte sequences in network traffic or known malicious instruction sequences used by malware. There are more than 67,000 signatures in over 50 categories that are updated in real time to protect against new and emerging exploits. The exploit categories include malware, phishing, coin mining, and Trojan attacks.
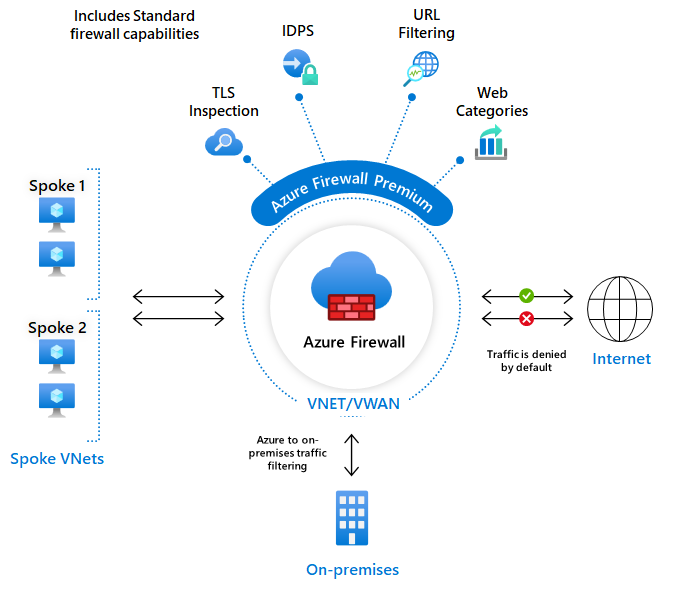
To learn about Firewall Premium features, see Azure Firewall Premium features.
Azure Firewall Basic
Azure Firewall Basic is intended for small and medium size (SMB) customers to secure their Azure cloud environments. It provides the essential protection SMB customers need at an affordable price point.
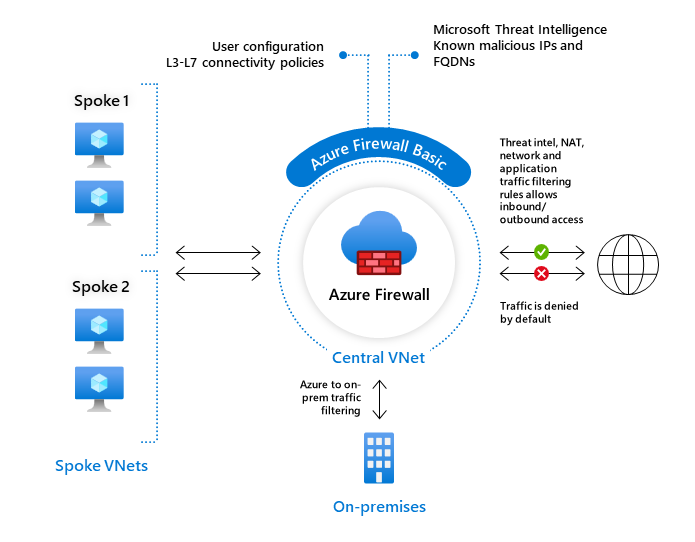
Azure Firewall Basic is like Firewall Standard, but has the following main limitations:
- Supports Threat Intel alert mode only
- Fixed scale unit to run the service on two virtual machine backend instances
- Recommended for environments with an estimated throughput of 250 Mbps
To learn more about Azure Firewall Basic, see Azure Firewall Basic features.
Feature comparison
To compare the all Firewall SKU features, see Choose the right Azure Firewall SKU to meet your needs.
Azure Firewall Manager
You can use Azure Firewall Manager to centrally manage Azure Firewalls across multiple subscriptions. Firewall Manager uses firewall policy to apply a common set of network/application rules and configuration to the firewalls in your tenant.
Firewall Manager supports firewalls in both virtual network and Virtual WANs (Secure Virtual Hub) environments. Secure Virtual Hubs use the Virtual WAN route automation solution to simplify routing traffic to the firewall with just a few steps.
To learn more about Azure Firewall Manager, see Azure Firewall Manager.
Pricing and SLA
For Azure Firewall pricing information, see Azure Firewall pricing.
For Azure Firewall SLA information, see Azure Firewall SLA.
Supported regions
For the supported regions for Azure Firewall, see Azure products available by region.
What's new
To learn what's new with Azure Firewall, see Azure updates.
Known issues
For Azure Firewall known issues, see Azure Firewall known issues.
Next steps
- Quickstart: Create an Azure Firewall and a firewall policy - ARM template
- Quickstart: Deploy Azure Firewall with Availability Zones - ARM template
- Tutorial: Deploy and configure Azure Firewall using the Azure portal
- Learn module: Introduction to Azure Firewall
- Learn more about Azure network security
Feedback
Coming soon: Throughout 2024 we will be phasing out GitHub Issues as the feedback mechanism for content and replacing it with a new feedback system. For more information see: https://aka.ms/ContentUserFeedback.
Submit and view feedback for