Monitor Azure Firewall logs (legacy) and metrics
Tip
For an improved method to work with firewall logs, see Azure Structured Firewall Logs.
You can monitor Azure Firewall using firewall logs. You can also use activity logs to audit operations on Azure Firewall resources. Using metrics, you can view performance counters in the portal.
You can access some of these logs through the portal. Logs can be sent to Azure Monitor logs, Storage, and Event Hubs and analyzed in Azure Monitor logs or by different tools such as Excel and Power BI.
Note
This article was recently updated to use the term Azure Monitor logs instead of Log Analytics. Log data is still stored in a Log Analytics workspace and is still collected and analyzed by the same Log Analytics service. We are updating the terminology to better reflect the role of logs in Azure Monitor. See Azure Monitor terminology changes for details.
Note
We recommend that you use the Azure Az PowerShell module to interact with Azure. See Install Azure PowerShell to get started. To learn how to migrate to the Az PowerShell module, see Migrate Azure PowerShell from AzureRM to Az.
Prerequisites
Before starting, you should read Azure Firewall logs and metrics for an overview of the diagnostics logs and metrics available for Azure Firewall.
Enable diagnostic logging through the Azure portal
It can take a few minutes for the data to appear in your logs after you complete this procedure to turn on diagnostic logging. If you don't see anything at first, check again in a few more minutes.
In the Azure portal, open your firewall resource group and select the firewall.
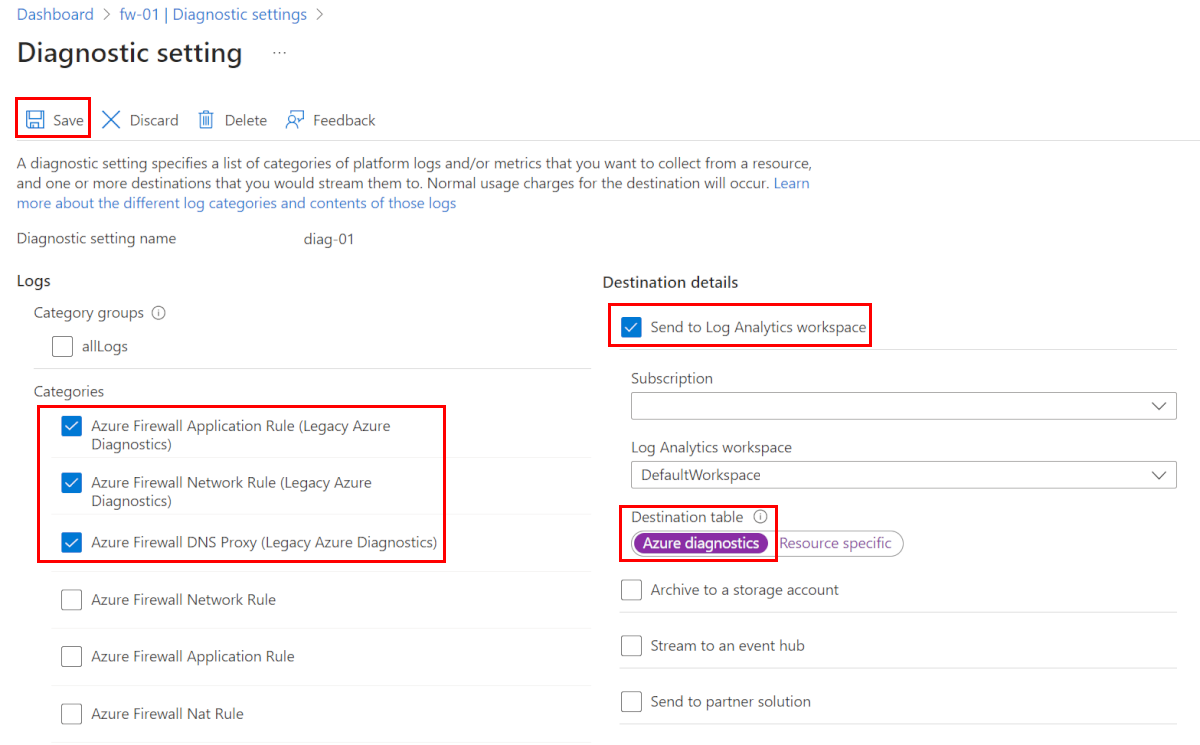
Under Monitoring, select Diagnostic settings.
For Azure Firewall, three service-specific legacy logs are available:
- Azure Firewall Application Rule (Legacy Azure Diagnostics)
- Azure Firewall Network Rule (Legacy Azure Diagnostics)
- Azure Firewall Dns Proxy (Legacy Azure Diagnostics)
Select Add diagnostic setting. The Diagnostics settings page provides the settings for the diagnostic logs.
Type a name for the diagnostic setting.
Under Logs, select Azure Firewall Application Rule (Legacy Azure Diagnostics), Azure Firewall Network Rule (Legacy Azure Diagnostics), and Azure Firewall Dns Proxy (Legacy Azure Diagnostics) to collect the logs.
Select Send to Log Analytics to configure your workspace.
Select your subscription.
For the Destination table, select Azure diagnostics.
Select Save.
Enable diagnostic logging by using PowerShell
Activity logging is automatically enabled for every Resource Manager resource. Diagnostic logging must be enabled to start collecting the data available through those logs.
To enable diagnostic logging with PowerShell, use the following steps:
Note your Log Analytics Workspace resource ID, where the log data is stored. This value is of the form:
/subscriptions/<subscriptionId>/resourceGroups/<resource group name>/providers/microsoft.operationalinsights/workspaces/<workspace name>You can use any workspace in your subscription. You can use the Azure portal to find this information. The information is located in the resource Properties page.
Note the resource ID for the firewall. This value is of the form:
/subscriptions/<subscriptionId>/resourceGroups/<resource group name>/providers/Microsoft.Network/azureFirewalls/<Firewall name>You can use the portal to find this information.
Enable diagnostic logging for all logs and metrics by using the following PowerShell cmdlet:
$diagSettings = @{ Name = 'toLogAnalytics' ResourceId = '/subscriptions/<subscriptionId>/resourceGroups/<resource group name>/providers/Microsoft.Network/azureFirewalls/<Firewall name>' WorkspaceId = '/subscriptions/<subscriptionId>/resourceGroups/<resource group name>/providers/microsoft.operationalinsights/workspaces/<workspace name>' } New-AzDiagnosticSetting @diagSettings
Enable diagnostic logging by using the Azure CLI
Activity logging is automatically enabled for every Resource Manager resource. Diagnostic logging must be enabled to start collecting the data available through those logs.
To enable diagnostic logging with Azure CLI, use the following steps:
Note your Log Analytics Workspace resource ID, where the log data is stored. This value is of the form:
/subscriptions/<subscriptionId>/resourceGroups/<resource group name>/providers/microsoft.operationalinsights/workspaces/<workspace name>You can use any workspace in your subscription. You can use the Azure portal to find this information. The information is located in the resource Properties page.
Note the resource ID for the firewall. This value is of the form:
/subscriptions/<subscriptionId>/resourceGroups/<resource group name>/providers/Microsoft.Network/azureFirewalls/<Firewall name>You can use the portal to find this information.
Enable diagnostic logging for all logs and metrics by using the following Azure CLI command:
az monitor diagnostic-settings create -n 'toLogAnalytics' --resource '/subscriptions/<subscriptionId>/resourceGroups/<resource group name>/providers/Microsoft.Network/azureFirewalls/<Firewall name>' --workspace '/subscriptions/<subscriptionId>/resourceGroups/<resource group name>/providers/microsoft.operationalinsights/workspaces/<workspace name>' --logs "[{\"category\":\"AzureFirewallApplicationRule\",\"Enabled\":true}, {\"category\":\"AzureFirewallNetworkRule\",\"Enabled\":true}, {\"category\":\"AzureFirewallDnsProxy\",\"Enabled\":true}]" --metrics "[{\"category\": \"AllMetrics\",\"enabled\": true}]"
View and analyze the activity log
You can view and analyze activity log data by using any of the following methods:
Azure tools: Retrieve information from the activity log through Azure PowerShell, the Azure CLI, the Azure REST API, or the Azure portal. Step-by-step instructions for each method are detailed in the Activity operations with Resource Manager article.
Power BI: If you don't already have a Power BI account, you can try it for free. By using the Azure Activity Logs content pack for Power BI, you can analyze your data with preconfigured dashboards that you can use as is or customize.
Microsoft Sentinel: You can connect Azure Firewall logs to Microsoft Sentinel, enabling you to view log data in workbooks, use it to create custom alerts, and incorporate it to improve your investigation. The Azure Firewall data connector in Microsoft Sentinel is currently in public preview. For more information, see Connect data from Azure Firewall.
See the following video by Mohit Kumar for an overview:
View and analyze the network and application rule logs
Azure Firewall Workbook provides a flexible canvas for Azure Firewall data analysis. You can use it to create rich visual reports within the Azure portal. You can tap into multiple Firewalls deployed across Azure, and combine them into unified interactive experiences.
You can also connect to your storage account and retrieve the JSON log entries for access and performance logs. After you download the JSON files, you can convert them to CSV and view them in Excel, Power BI, or any other data-visualization tool.
Tip
If you are familiar with Visual Studio and basic concepts of changing values for constants and variables in C#, you can use the log converter tools available from GitHub.
View metrics
Browse to an Azure Firewall. Under Monitoring, select Metrics. To view the available values, select the METRIC drop-down list.
Next steps
Now that you've configured your firewall to collect logs, you can explore Azure Monitor logs to view your data.
Feedback
Coming soon: Throughout 2024 we will be phasing out GitHub Issues as the feedback mechanism for content and replacing it with a new feedback system. For more information see: https://aka.ms/ContentUserFeedback.
Submit and view feedback for