Determine causes of non-compliance
When an Azure resource is determined to be non-compliant to a policy rule, it's helpful to understand which portion of the rule the resource isn't compliant with. It's also useful to understand which change altered a previously compliant resource to make it non-compliant. There are two ways to find this information:
Compliance details
When a resource is non-compliant, the compliance details for that resource are available from the Policy compliance page. The compliance details pane includes the following information:
- Resource details such as name, type, location, and resource ID.
- Compliance state and timestamp of the last evaluation for the current policy assignment.
- A list of reasons for the resource non-compliance.
Important
As the compliance details for a Non-compliant resource shows the current value of properties on
that resource, the user must have read operation to the type of resource. For example, if
the Non-compliant resource is Microsoft.Compute/virtualMachines then the user must have the
Microsoft.Compute/virtualMachines/read operation. If the user doesn't have the needed
operation, an access error is displayed.
To view the compliance details, follow these steps:
Launch the Azure Policy service in the Azure portal by selecting All services, then searching for and selecting Policy.
On the Overview or Compliance page, select a policy in a compliance state that is Non-compliant.
From the Resource compliance tab of the Policy compliance page, select and hold (or right-click) or select the ellipsis of a resource in a compliance state that's Non-compliant. Then select View compliance details.
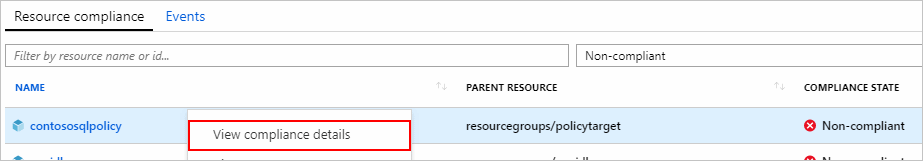
The Compliance details pane displays information from the latest evaluation of the resource to the current policy assignment. In this example, the field
Microsoft.Sql/servers/versionis found to be 12.0 while the policy definition expected 14.0. If the resource is non-compliant for multiple reasons, each is listed on this pane.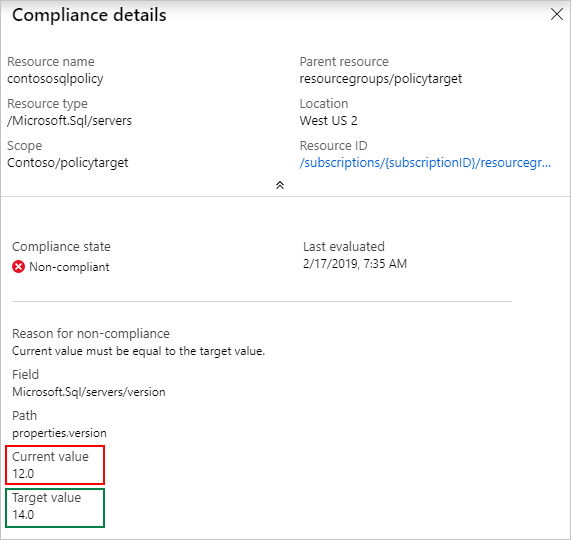
For an
auditIfNotExistsordeployIfNotExistspolicy definition, the details include the details.type property and any optional properties. For a list, see auditIfNotExists properties and deployIfNotExists properties. Last evaluated resource is a related resource from the details section of the definition.Example partial
deployIfNotExistsdefinition:{ "if": { "field": "type", "equals": "[parameters('resourceType')]" }, "then": { "effect": "deployIfNotExists", "details": { "type": "Microsoft.Insights/metricAlerts", "existenceCondition": { "field": "name", "equals": "[concat(parameters('alertNamePrefix'), '-', resourcegroup().name, '-', field('name'))]" }, "existenceScope": "subscription", "deployment": { ... } } } }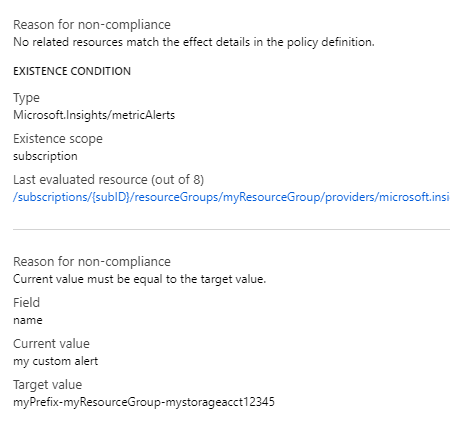
Note
To protect data, when a property value is a secret the current value displays asterisks.
These details explain why a resource is currently non-compliant, but don't show when the change was made to the resource that caused it to become non-compliant. For that information, see Change history (Preview).
Compliance reasons
Resource Manager modes and Resource Provider modes each have different reasons for non-compliance.
General Resource Manager mode compliance reasons
The following table maps each Resource Manager mode reason to the responsible condition in the policy definition:
| Reason | Condition |
|---|---|
| Current value must contain the target value as a key. | containsKey or not notContainsKey |
| Current value must contain the target value. | contains or not notContains |
| Current value must be equal to the target value. | equals or not notEquals |
| Current value must be less than the target value. | less or not greaterOrEquals |
| Current value must be greater than or equal to the target value. | greaterOrEquals or not less |
| Current value must be greater than the target value. | greater or not lessOrEquals |
| Current value must be less than or equal to the target value. | lessOrEquals or not greater |
| Current value must exist. | exists |
| Current value must be in the target value. | in or not notIn |
| Current value must be like the target value. | like or not notLike |
| Current value must be case-sensitive match the target value. | match or not notMatch |
| Current value must be case-insensitive match the target value. | matchInsensitively or not notMatchInsensitively |
| Current value must not contain the target value as a key. | notContainsKey or not containsKey |
| Current value must not contain the target value. | notContains or not contains |
| Current value must not be equal to the target value. | notEquals or not equals |
| Current value must not exist. | not exists |
| Current value must not be in the target value. | notIn or not in |
| Current value must not be like the target value. | notLike or not like |
| Current value must not be case-sensitive match the target value. | notMatch or not match |
| Current value must not be case-insensitive match the target value. | notMatchInsensitively or not matchInsensitively |
| No related resources match the effect details in the policy definition. | A resource of the type defined in then.details.type and related to the resource defined in the if portion of the policy rule doesn't exist. |
Azure Policy Resource Provider mode compliance reasons
The following table maps each Microsoft.PolicyInsights
Resource Provider mode reason code to
its corresponding explanation:
| Compliance reason code | Error message and explanation |
|---|---|
| NonModifiablePolicyAlias | NonModifiableAliasConflict: The alias '{alias}' isn't modifiable in requests using API version '{apiVersion}'. This error happens when a request using an API version where the alias doesn't support the 'modify' effect or only supports the 'modify' effect with a different token type. |
| AppendPoliciesNotApplicable | AppendPoliciesUnableToAppend: The aliases: '{ aliases }' aren't modifiable in requests using API version: '{ apiVersion }'. This can happen in requests using API versions for which the aliases don't support the 'modify' effect, or support the 'modify' effect with a different token type. |
| ConflictingAppendPolicies | ConflictingAppendPolicies: Found conflicting policy assignments that modify the '{notApplicableFields}' field. Policy identifiers: '{policy}'. Contact the subscription administrator to update the policy assignments. |
| AppendPoliciesFieldsExist | AppendPoliciesFieldsExistWithDifferentValues: Policy assignments attempted to append fields which already exist in the request with different values. Fields: '{existingFields}'. Policy identifiers: '{policy}'. Contact the subscription administrator to update the policies. |
| AppendPoliciesUndefinedFields | AppendPoliciesUndefinedFields: Found policy definition that refers to an undefined field property for API version '{apiVersion}'. Fields: '{nonExistingFields}'. Policy identifiers: '{policy}'. Contact the subscription administrator to update the policies. |
| MissingRegistrationForType | MissingRegistrationForResourceType: The subscription isn't registered for the resource type '{ResourceType}'. Check that the resource type exists and that the resource type is registered. |
| AmbiguousPolicyEvaluationPaths | The request content has one or more ambiguous paths: '{0}' required by policies: '{1}'. |
| InvalidResourceNameWildcardPosition | The policy assignment '{0}' associated with the policy definition '{1}' couldn't be evaluated. The resource name '{2}' within an ifNotExists condition contains the wildcard '?' character in an invalid position. Wildcards can only be located at the end of the name in a segment by themselves (ex. TopLevelResourceName/?). Either fix the policy or remove the policy assignment to unblock. |
| TooManyResourceNameSegments | The policy assignment '{0}' associated with the policy definition '{1}' couldn't be evaluated. The resource name '{2}' within an ifNotExists condition contains too many name segments. The number of name segments must be equal to or less than the number of type segments (excluding the resource provider namespace). Either fix the policy definition or remove the policy assignment to unblock. |
| InvalidPolicyFieldPath | The field path '{0}' within the policy definition is invalid. Field paths must contain no empty segments. They might contain only alphanumeric characters with the exception of the '.' character for splitting segments and the '[*]' character sequence to access array properties. |
AKS Resource Provider mode compliance reasons
The following table maps each Microsoft.Kubernetes.Data
Resource Provider mode reason to
the responsible state of the
constraint template
in the policy definition:
| Reason | Constraint template reason description |
|---|---|
| Constraint/TemplateCreateFailed | The resource failed to create for a policy definition with a Constraint/Template that doesn't match an existing Constraint/Template on cluster by resource metadata name. |
| Constraint/TemplateUpdateFailed | The Constraint/Template failed to update for a policy definition with a Constraint/Template that matches an existing Constraint/Template on cluster by resource metadata name. |
| Constraint/TemplateInstallFailed | The Constraint/Template failed to build and was unable to be installed on cluster for either create or update operation. |
| ConstraintTemplateConflicts | The Template has a conflict with one or more policy definitions using the same Template name with different source. |
| ConstraintStatusStale | There's an existing 'Audit' status, but Gatekeeper hasn't performed an audit within the last hour. |
| ConstraintNotProcessed | There's no status and Gatekeeper hasn't performed an audit within the last hour. |
| InvalidConstraint/Template | The resource was rejected because of one of the following reasons: invalid constraint template Rego content, invalid YAML, or a parameter type mismatch between constraint and constraint template (providing a string value when an integer was expected). |
Note
For existing policy assignments and constraint templates already on the cluster, if that Constraint/Template fails, the cluster is protected by maintaining the existing Constraint/Template. The cluster reports as non-compliant until the failure is resolved on the policy assignment or the add-on self-heals. For more information about handling conflict, see Constraint template conflicts.
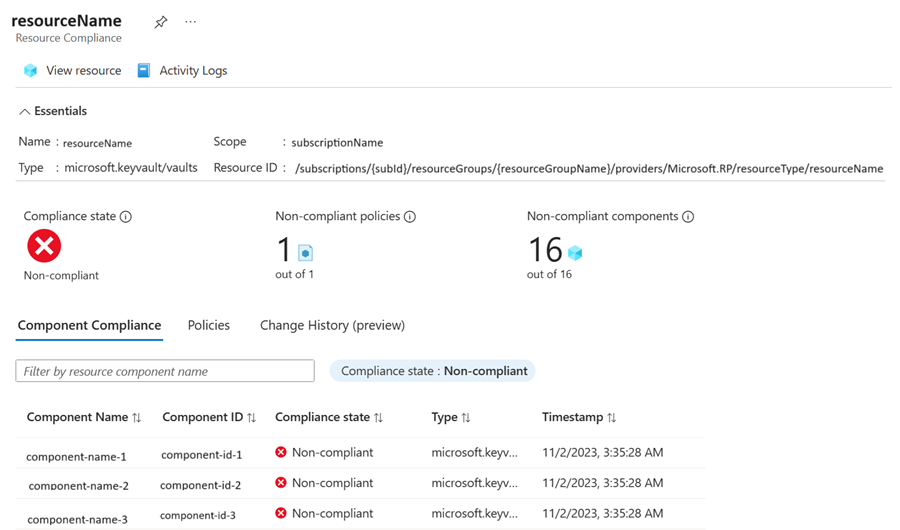
Component details for Resource Provider modes
For assignments with a Resource Provider mode, select the Non-compliant resource to view its component compliance records. The Component Compliance tab shows more information specific to the Resource Provider mode like Component Name, Component ID, and Type.
Compliance details for guest configuration
For policy definitions in the Guest Configuration category, there could be multiple settings evaluated inside the virtual machine and you need to view per-setting details. For example, if you're auditing for a list of security settings and only one of them has status Non-compliant, you need to know which specific settings are out of compliance and why.
You also might not have access to sign in to the virtual machine directly but you need to report on why the virtual machine is Non-compliant.
Azure portal
Begin by following the same steps in the Compliance details section to view policy compliance details.
In the Compliance details pane view, select the link Last evaluated resource.
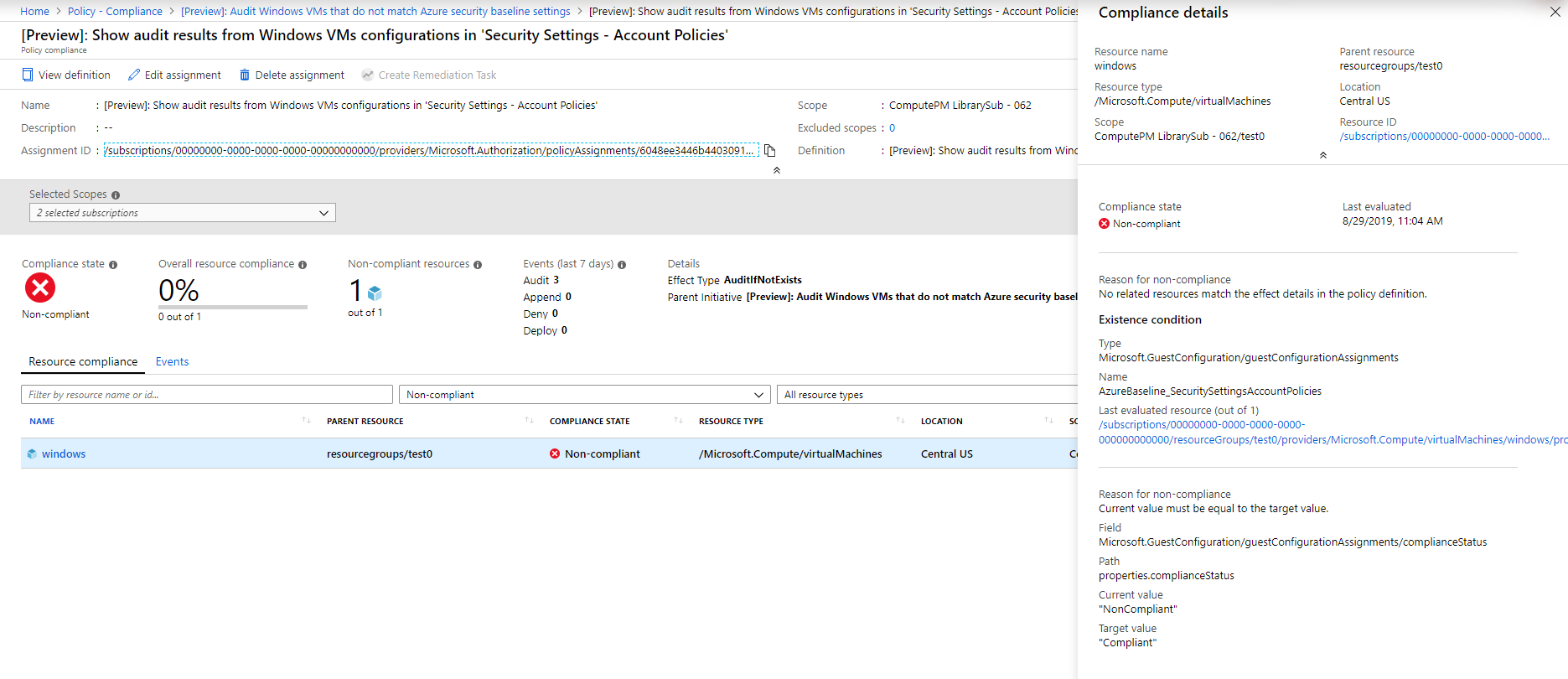
The Guest Assignment page displays all available compliance details. Each row in the view represents an evaluation that was performed inside the machine. In the Reason column, a phrase is shown describing why the Guest Assignment is Non-compliant. For example, if you're auditing password policies, the Reason column would display text including the current value for each setting.
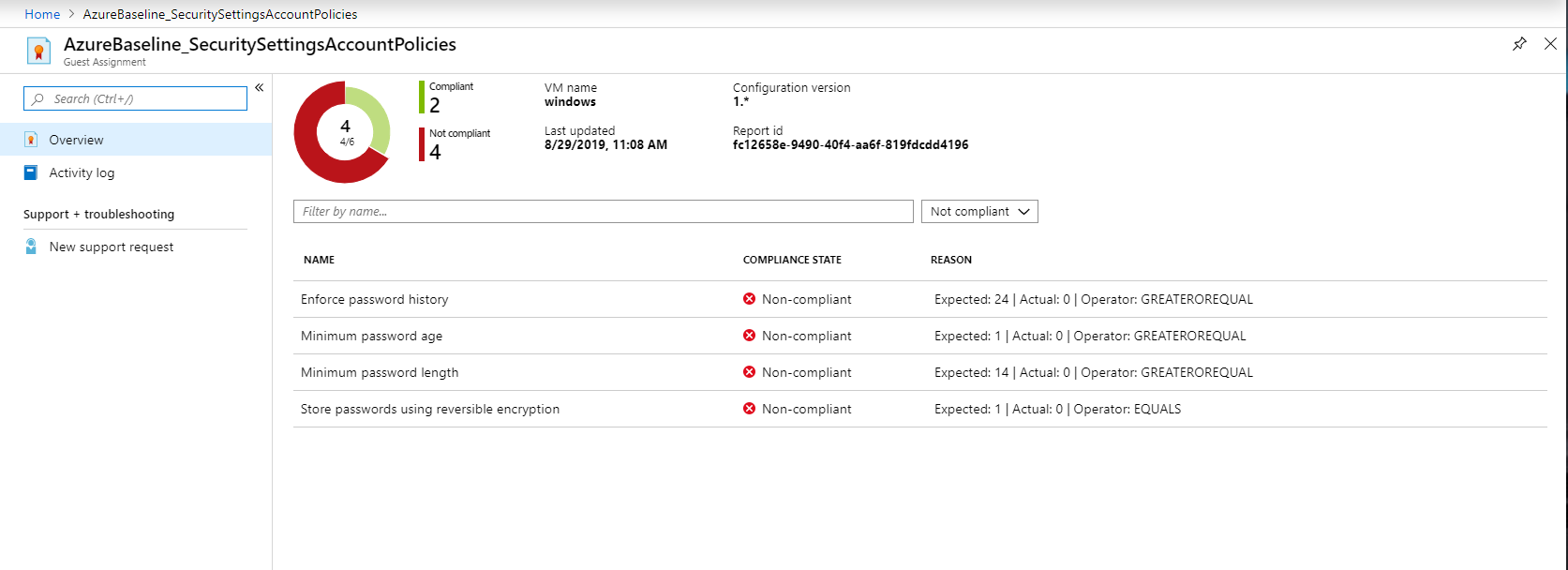
View configuration assignment details at scale
The guest configuration feature can be used outside of Azure Policy assignments. For example, Azure Automanage creates guest configuration assignments, or you might assign configurations when you deploy machines.
To view all guest configuration assignments across your tenant, from the Azure portal open the Guest Assignments page. To view detailed compliance information, select each assignment using the link in the column Name.
Change history (Preview)
As part of a new public preview, the last 14 days of change history are available for all Azure resources that support complete mode deletion. Change history provides details about when a change was detected and a visual diff for each change. A change detection is triggered when the Azure Resource Manager properties are added, removed, or altered.
Launch the Azure Policy service in the Azure portal by selecting All services, then searching for and selecting Policy.
On the Overview or Compliance page, select a policy in any compliance state.
From the Resource compliance tab of the Policy compliance page, select a resource.
Select the Change History (preview) tab on the Resource Compliance page. A list of detected changes, if any exist, are displayed.
Select one of the detected changes. The visual diff for the resource is presented on the Change history page.
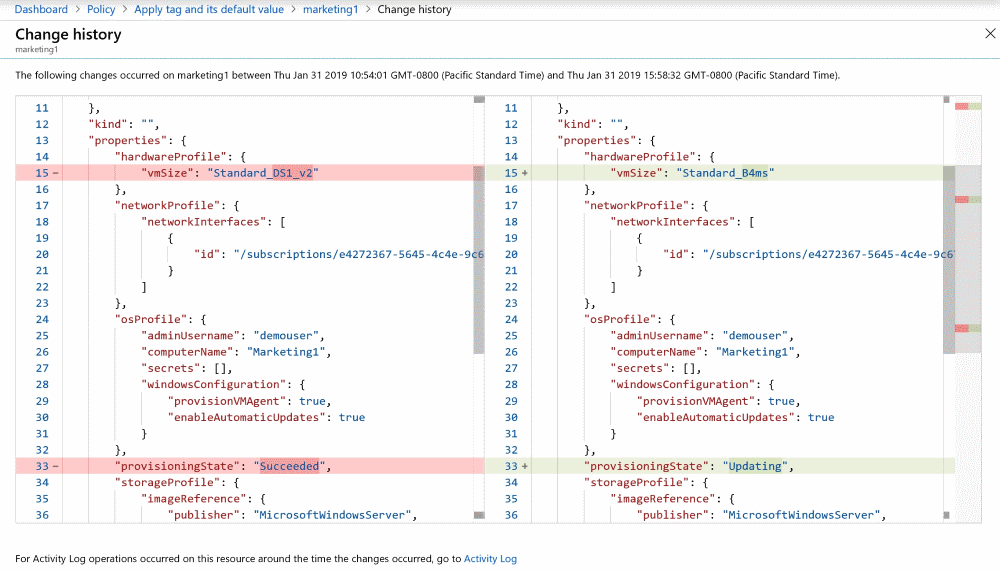
The visual diff aides in identifying changes to a resource. The changes detected might not be related to the current compliance state of the resource.
Change history data is provided by Azure Resource Graph. To query this information outside of the Azure portal, see Get resource changes.
Next steps
- Review examples at Azure Policy samples.
- Review the Azure Policy definition structure.
- Review Understanding policy effects.
- Understand how to programmatically create policies.
- Learn how to get compliance data.
- Learn how to remediate non-compliant resources.
- Review what a management group is with Organize your resources with Azure management groups.
Feedback
Coming soon: Throughout 2024 we will be phasing out GitHub Issues as the feedback mechanism for content and replacing it with a new feedback system. For more information see: https://aka.ms/ContentUserFeedback.
Submit and view feedback for