Analytics and central reporting for Azure Information Protection
Note
Are you looking for Microsoft Information Protection? The Azure Information Protection unified labeling client is currently in maintenance mode. We recommend enabling Microsoft Information Protection's built-in labeling for your Office 365 applications. Learn more.
This article describes how to use the auditing solution from Microsoft Purview to view audit events generated from the Azure Information Protection Unified Labeling client. Audit events emitted to the Microsoft 365 unified audit log for central reporting are viewable in the Activity explorer, which can help you track the adoption of your labels that classify and protect your organization's data.
Audit enables you to do perform the following steps:
- Aggregate data from your Azure Information Protection clients, Azure Information Protection scanners and Microsoft Defender for Cloud Apps.
- View audit events in the Microsoft 365 unified audit log and Office 365 activity log for your organization.
- Query, view and detect audit events in Activity explorer with a graphical interface in the compliance portal.
Audit events from the Microsoft 365 unified audit log
The AIP Unified Labeling client includes the Add-in for Office, the Scanner, the Viewer for Windows, the client PowerShell, and the Classify-and-Protect shell extension for Windows. All these components generate audit events that show up in the Office 365 activity logs and can be queried using the Office 365 Management Activity API.
Audit events enable an administrator to:
- Monitor labeled and protected documents and emails across your organization.
- Monitor user access to labeled documents and emails, and track document classification changes.
Microsoft 365 unified audit log event schema
The five events (also called “AuditLogRecordType”) specific to AIP listed below, and more details about each can be found within the API reference.
| Value | Member name | Description |
|---|---|---|
| 93 | AipDiscover | Azure Information Protection (AIP) scanner events. |
| 94 | AipSensitivityLabelAction | AIP sensitivity label events. |
| 95 | AipProtectionAction | AIP protection events. |
| 96 | AipFileDeleted | AIP file deletion events. |
| 97 | AipHeartBeat | AIP heartbeat events. |
This information is accessible in the Microsoft 365 unified audit log for your organization and can be viewed in the Activity explorer.
Query Audit Events in Activity Explorer
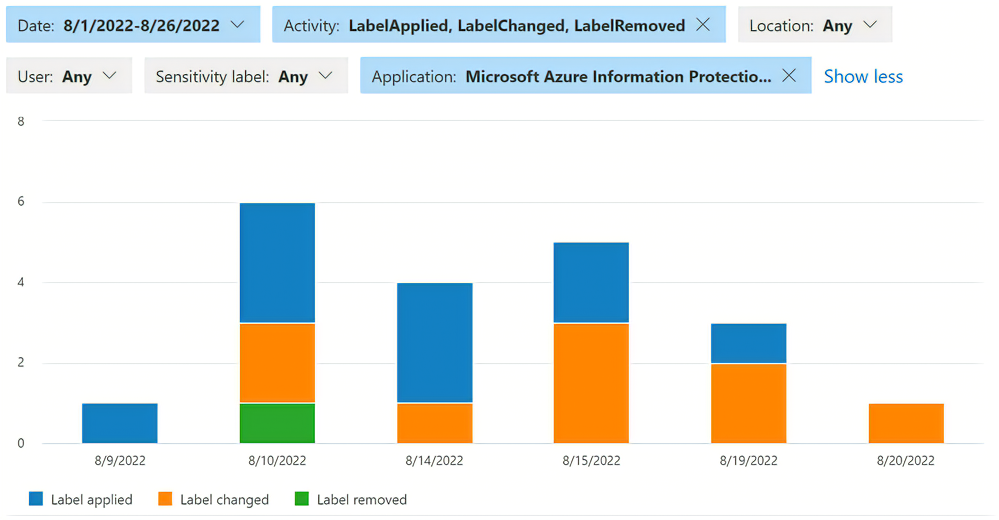
The Activity explorer in the Microsoft Purview compliance portal is a graphical interface to view audit events emitted to the Microsoft 365 unified audit log. An administrator of the tenant can use built-in queries to determine whether the policies and controls implemented by your organization is effective. With up to 30 days of data available, an administrator can set filters and clearly see when and how sensitive data is handled within your organization.
To see AIP-specific activity, an administrator can begin with the following filters:
- Activity type:
- Label applied
- Label changed
- Label removed
- Label file read
- Application:
- Microsoft Azure Information Protection Word add-in
- Microsoft Azure Information Protection Excel add-in
- Microsoft Azure Information Protection PowerPoint add-in
- Microsoft Azure Information Protection Outlook add-in
An administrator might not see all the options in the filter, or may see more; the filter values depend on what activities are captured for your tenant. For more information about the Activity explorer, see:
Information collected and sent to Microsoft Purview from the AIP Unified Labeling client
To generate these reports, endpoints send the following types of information to the Microsoft 365 unified audit log:
The label action. For example, set a label, change a label, add or remove protection, automatic and recommended labels.
The label name before and after the label action.
Your organization's tenant ID.
The user ID (email address or UPN).
The name of the user's device.
The IP address of the user's device.
The relevant process name, such as outlook or msip.app.
The name of the application that performed the labeling, such as Outlook or File Explorer
For documents: The file path and file name of documents that are labeled.
For emails: The email subject and email sender for emails that are labeled.
The sensitive information types (predefined and custom) that were detected in content.
The Azure Information Protection client version.
The client operating system version.
Prevent the AIP clients from sending auditing data
To prevent the Azure Information Protection unified labeling client from sending auditing data, configure a label policy advanced setting.
Content matches for deeper analysis
Azure Information Protection lets you collect and store the actual data that's identified as being a sensitive information type (predefined or custom). For example, this can include credit card numbers that are found, as well as social security numbers, passport numbers, and bank account numbers. The content matches are displayed when you select an entry from Activity logs, and view the Activity Details.
By default, Azure Information Protection clients don't send content matches. To change this behavior so that content matches are sent, configure an advanced setting in a label policy.
Prerequisites
Audit events are enabled by default for your organization. To view audit events in Microsoft Purview, review the licensing requirements for basic and Audit (Premium) solutions.
Next steps
After reviewing the information in the reports, you may want to learn more about how to configure Microsoft Purview's auditing solution for your organization.
- Learn how to export audit events from the Microsoft 365 unified audit log to an Azure log analytics workspace with AIP Audit Export on GitHub.
- Read the Admin guide to auditing and reporting for the AIP Unified Labeling client for a deep dive into Microsoft Purview's auditing solution.
- Review the protection usage logs documentation for file access and denied events generated from the Rights Management Service. These events are handled separately from events generated from the Azure Information Protection Unified Labeling client.
- Refer to the Microsoft 365 documentation about sensitivity labels to learn how to make changes to your labeling policy in the compliance portal.
Feedback
Coming soon: Throughout 2024 we will be phasing out GitHub Issues as the feedback mechanism for content and replacing it with a new feedback system. For more information see: https://aka.ms/ContentUserFeedback.
Submit and view feedback for