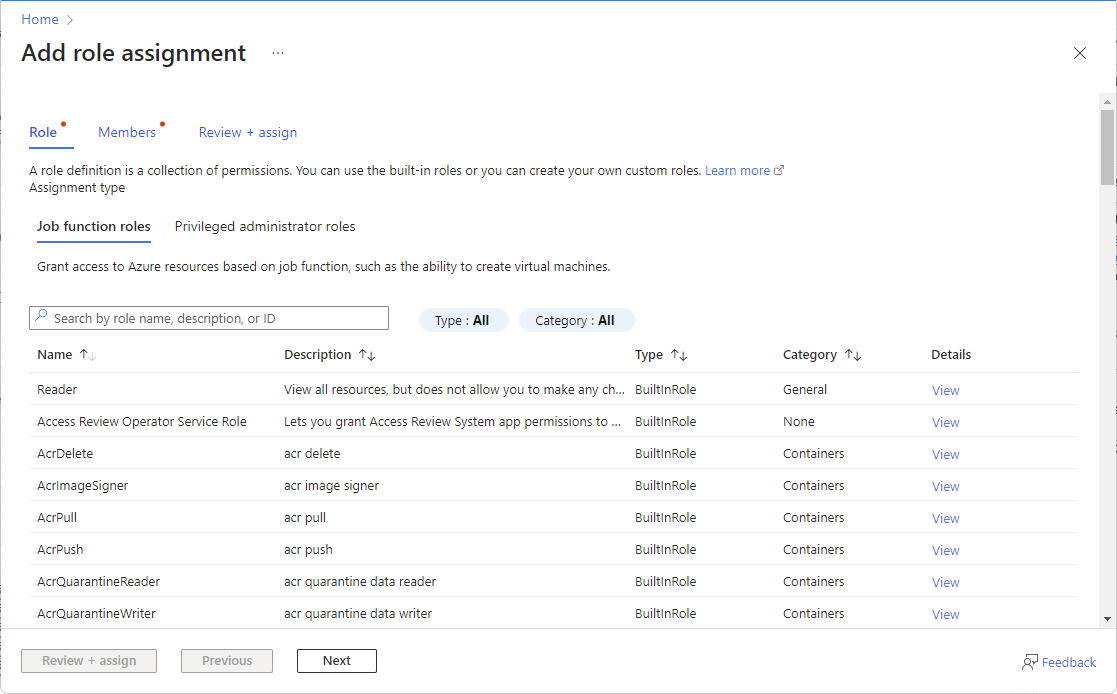
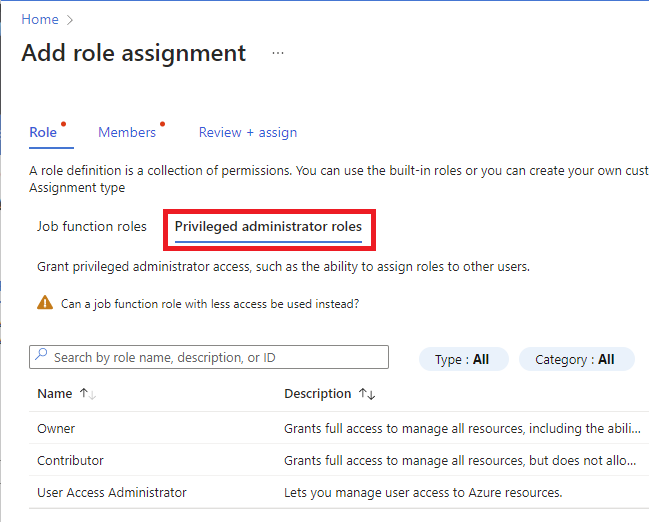
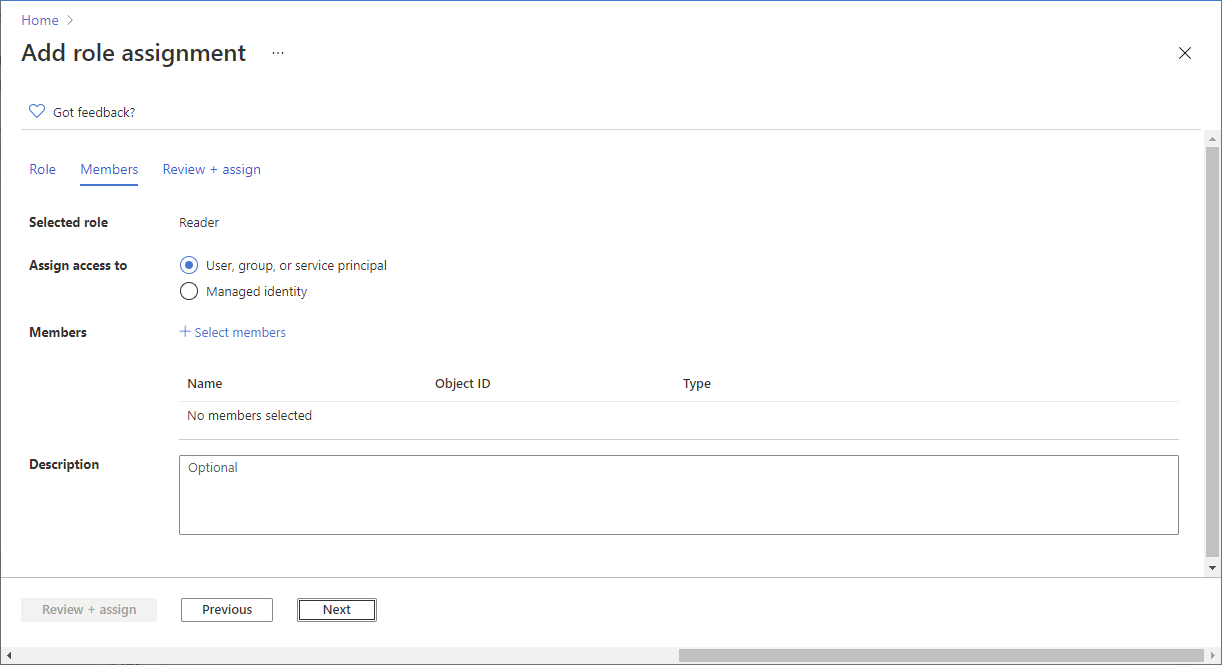
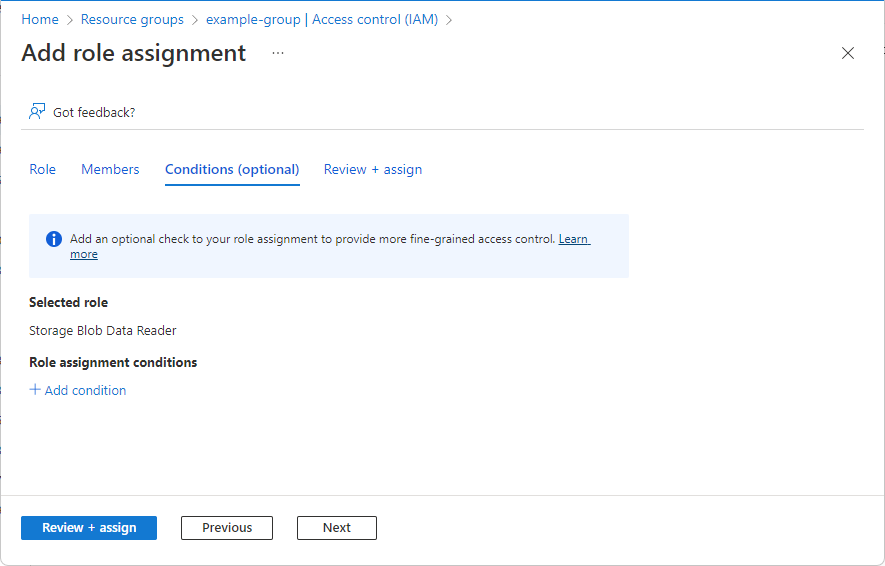
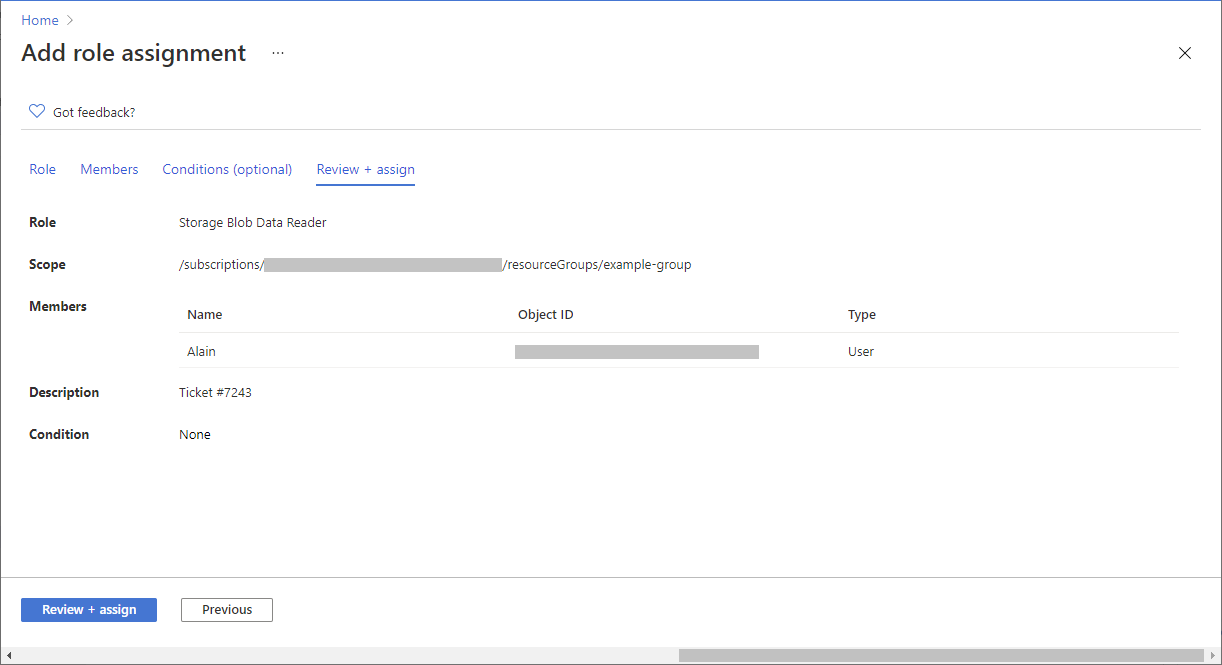
If you selected a role that supports conditions, a Conditions tab will appear and you have the option to add a condition to your role assignment. A condition is an additional check that you can optionally add to your role assignment to provide more fine-grained access control.
The Conditions tab will look different depending on the role you selected.
Delegate condition
Important
Delegating Azure role assignment management with conditions is currently in PREVIEW.
See the Supplemental Terms of Use for Microsoft Azure Previews for legal terms that apply to Azure features that are in beta, preview, or otherwise not yet released into general availability.
If you selected one of the following privileged roles, follow the steps in this section.
On the Conditions tab under What user can do, select the Allow user to only assign selected roles to selected principals (fewer privileges) option.
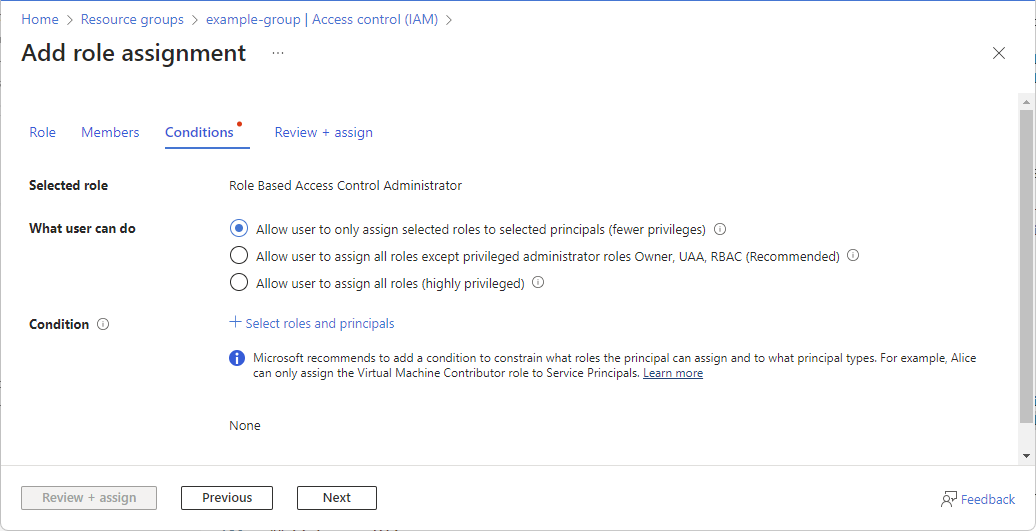
Click Select roles and principals to add a condition that constrains the roles and principals this user can assign roles to.
Follow the steps in Delegate Azure role assignment management to others with conditions.
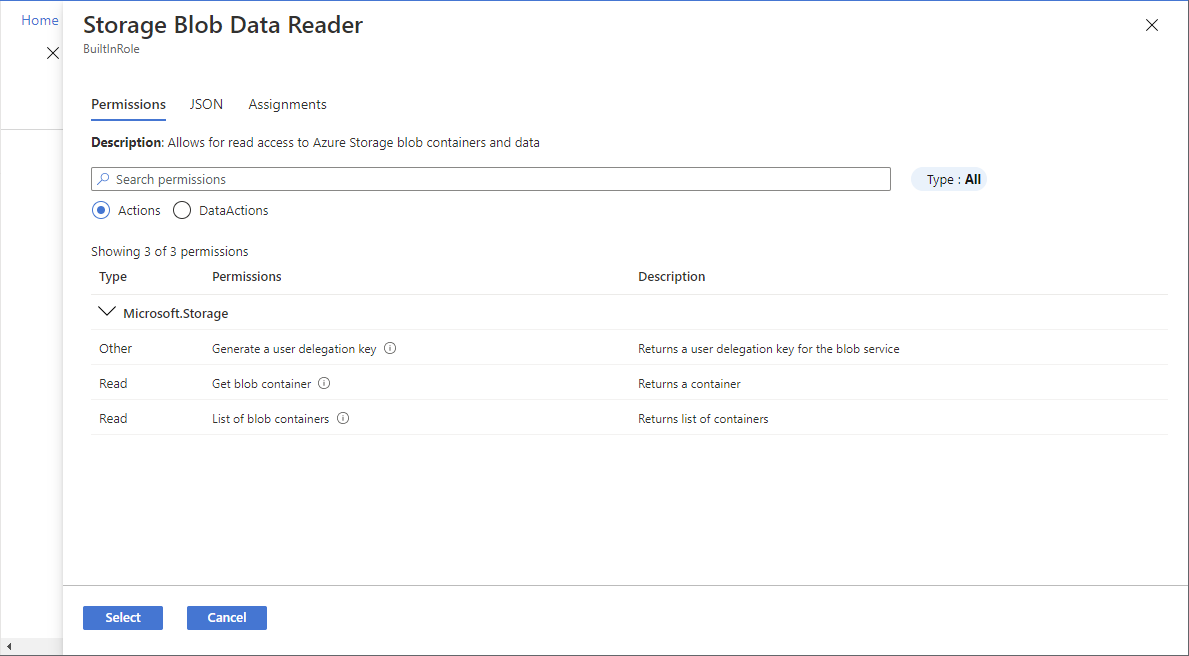
Storage condition
If you selected one of the following storage roles, follow the steps in this section.