Enable vulnerability scanning with the integrated Qualys scanner (deprecated)
Important
Defender for Server's vulnerability assessment solution powered by Qualys, is on a retirement path that set to complete on May 1st, 2024. If you are a currently using the built-in vulnerability assessment powered by Qualys, you should plan to transition to the Microsoft Defender Vulnerability Management vulnerability scanning solution.
For more information about our decision to unify our vulnerability assessment offering with Microsoft Defender Vulnerability Management, see this blog post.
Check out the common questions regarding the transition to Microsoft Defender Vulnerability Management.
Customers who want to continue using Qualys, can do so with the Bring Your Own License (BYOL) method.
A core component of every cyber risk and security program is the identification and analysis of vulnerabilities. Defender for Cloud regularly checks your connected machines to ensure they're running vulnerability assessment tools.
When a machine is found that doesn't have a vulnerability assessment solution deployed, Defender for Cloud generates the security recommendation: Machines should have a vulnerability assessment solution. Use this recommendation to deploy the vulnerability assessment solution to your Azure virtual machines and your Azure Arc-enabled hybrid machines.
Defender for Cloud includes vulnerability scanning for your machines. You don't need a Qualys license or even a Qualys account - everything's handled seamlessly inside Defender for Cloud. This page provides details of this scanner and instructions for how to deploy it.
Tip
The integrated vulnerability assessment solution supports both Azure virtual machines and hybrid machines. To deploy the vulnerability assessment scanner to your on-premises and multicloud machines, connect them to Azure first with Azure Arc as described in Connect your non-Azure machines to Defender for Cloud.
Defender for Cloud's integrated vulnerability assessment solution works seamlessly with Azure Arc. When you've deployed Azure Arc, your machines will appear in Defender for Cloud and no Log Analytics agent is required.
If you don't want to use the vulnerability assessment powered by Qualys, you can use Microsoft Defender Vulnerability Management or deploy a BYOL solution with your own Qualys license, Rapid7 license, or another vulnerability assessment solution.
Availability
| Aspect | Details |
|---|---|
| Release state: | General availability (GA) |
| Machine types (hybrid scenarios): | |
| Pricing: | Requires Microsoft Defender for Servers Plan 2 |
| Required roles and permissions: | Owner (resource group level) can deploy the scanner Security Reader can view findings |
| Clouds: |
Overview of the integrated vulnerability scanner
The vulnerability scanner included with Microsoft Defender for Cloud is powered by Qualys. Qualys' scanner is one of the leading tools for real-time identification of vulnerabilities. It's only available with Microsoft Defender for Servers. You don't need a Qualys license or even a Qualys account - everything's handled seamlessly inside Defender for Cloud.
How the integrated vulnerability scanner works
The vulnerability scanner extension works as follows:
Deploy - Microsoft Defender for Cloud monitors your machines and provides recommendations to deploy the Qualys extension on your selected machine/s.
Gather information - The extension collects artifacts and sends them for analysis in the Qualys cloud service in the defined region.
Analyze - Qualys' cloud service conducts the vulnerability assessment and sends its findings to Defender for Cloud.
Important
To ensure the privacy, confidentiality, and security of our customers, we don't share customer details with Qualys. Learn more about the privacy standards built into Azure.
Report - The findings are available in Defender for Cloud.
Deploy the integrated scanner to your Azure and hybrid machines
From the Azure portal, open Defender for Cloud.
From Defender for Cloud's menu, open the Recommendations page.
Select the recommendation Machines should have a vulnerability assessment solution.
Tip
The machine
server16-test, is an Azure Arc-enabled machine. To deploy the vulnerability assessment scanner to your on-premises and multicloud machines, see Connect your non-Azure machines to Defender for Cloud.Defender for Cloud works seamlessly with Azure Arc. When you've deployed Azure Arc, your machines will appear in Defender for Cloud and no Log Analytics agent is required.
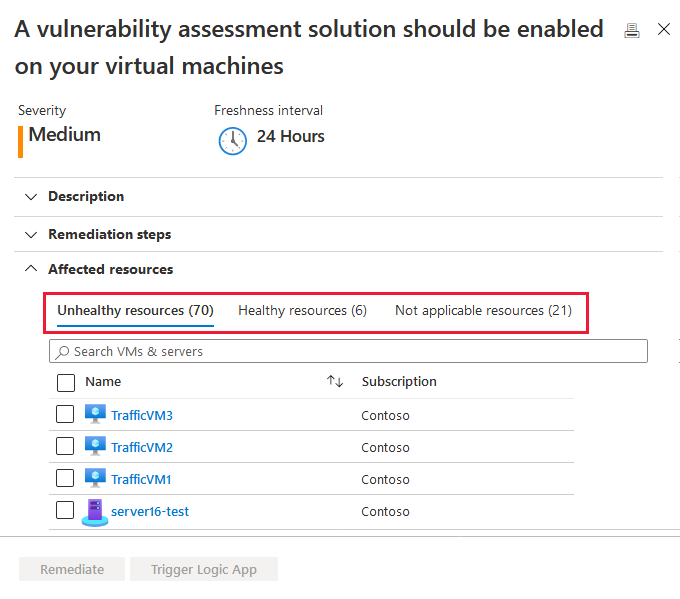
Your machines appear in one or more of the following groups:
- Healthy resources – Defender for Cloud detected a vulnerability assessment solution running on these machines.
- Unhealthy resources – A vulnerability scanner extension can be deployed to these machines.
- Not applicable resources – these machines aren't supported for the vulnerability scanner extension.
From the list of unhealthy machines, select the ones to receive a vulnerability assessment solution and select Remediate.
Important
Depending on your configuration, this list might appear differently.
- If you haven't got a third-party vulnerability scanner configured, you won't be offered the opportunity to deploy it.
- If your selected machines aren't protected by Microsoft Defender for Servers, the Defender for Cloud integrated vulnerability scanner option won't be available.
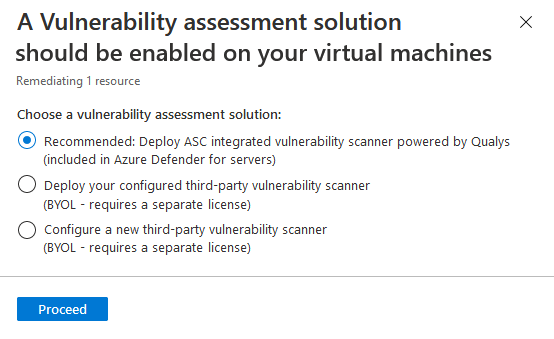
Choose the recommended option, Deploy integrated vulnerability scanner, and Proceed.
You're asked for one further confirmation. Select Remediate.
The scanner extension is installed on all of the selected machines within a few minutes.
Scanning begins automatically as soon as the extension is successfully deployed. Scans run every 12 hours. This interval isn't configurable.
Important
If the deployment fails on one or more machines, ensure the target machines can communicate with Qualys' cloud service by adding the following IPs to your allowlists (via port 443 - the default for HTTPS):
https://qagpublic.qg3.apps.qualys.com- Qualys' US data centerhttps://qagpublic.qg2.apps.qualys.eu- Qualys' European data center
If your machine is in a region in an Azure European geography (such as Europe, UK, Germany), its artifacts will be processed in Qualys' European data center. Artifacts for virtual machines located elsewhere are sent to the US data center.
Automate at-scale deployments
Note
All of the tools described in this section are available from Defender for Cloud's GitHub community repository. There, you can find scripts, automations, and other useful resources to use throughout your Defender for Cloud deployment.
Some of these tools only affect new machines connected after you enable at scale deployment. Others also deploy to existing machines. You can combine multiple approaches.
Some of the ways you can automate deployment at scale of the integrated scanner:
- Azure Resource Manager – This method is available from view recommendation logic in the Azure portal. The remediation script includes the relevant ARM template you can use for your automation:

- DeployIfNotExists policy – A custom policy for ensuring all newly created machines receive the scanner. Select Deploy to Azure and set the relevant parameters. You can assign this policy at the level of resource groups, subscriptions, or management groups.
- PowerShell Script – Use the
Update qualys-remediate-unhealthy-vms.ps1script to deploy the extension for all unhealthy virtual machines. To install on new resources, automate the script with Azure Automation. The script finds all unhealthy machines discovered by the recommendation and executes an Azure Resource Manager call. - Azure Logic Apps – Build a logic app based on the sample app. Use Defender for Cloud's workflow automation tools to trigger your logic app to deploy the scanner whenever the Machines should have a vulnerability assessment solution recommendation is generated for a resource.
- REST API – To deploy the integrated vulnerability assessment solution using the Defender for Cloud REST API, make a PUT request for the following URL and add the relevant resource ID:
https://management.azure.com/<resourceId>/providers/Microsoft.Security/serverVulnerabilityAssessments/default?api-Version=2015-06-01-preview
Trigger an on-demand scan
You can trigger an on-demand scan from the machine itself, using locally or remotely executed scripts or Group Policy Object (GPO). Alternatively, you can integrate it into your software distribution tools at the end of a patch deployment job.
The following commands trigger an on-demand scan:
- Windows machines:
REG ADD HKLM\SOFTWARE\Qualys\QualysAgent\ScanOnDemand\Vulnerability /v "ScanOnDemand" /t REG_DWORD /d "1" /f - Linux machines:
sudo /usr/local/qualys/cloud-agent/bin/cloudagentctl.sh action=demand type=vm
Next steps
Defender for Cloud also offers vulnerability analysis for your:
- SQL databases - Explore vulnerability assessment reports in the vulnerability assessment dashboard
- Azure Container Registry images - Vulnerability assessments for Azure with Microsoft Defender Vulnerability Management
Feedback
Coming soon: Throughout 2024 we will be phasing out GitHub Issues as the feedback mechanism for content and replacing it with a new feedback system. For more information see: https://aka.ms/ContentUserFeedback.
Submit and view feedback for