Enable Microsoft Defender for open-source relational databases and respond to alerts
Microsoft Defender for Cloud detects anomalous activities indicating unusual and potentially harmful attempts to access or exploit databases for the following services:
To get alerts from the Microsoft Defender plan you'll first need to enable it as shown below.
Learn more about this Microsoft Defender plan in Overview of Microsoft Defender for open-source relational databases.
Enable enhanced security
From the Azure portal, open the configuration page of the database server you want to protect.
From the security menu on the left, select Microsoft Defender for Cloud.
If enhanced security isn't enabled, you'll see a button as shown in the following screenshot. Select Enable Microsoft Defender for [Database type] (for example, "Microsoft Defender for MySQL") and select Save.
Tip
This page in the portal will be the same regardless of the database type (PostgreSQL, MySQL, or MariaDB).
Respond to security alerts
When Microsoft Defender for Cloud is enabled on your database, it detects anomalous activities and generates alerts. These alerts are available from multiple locations, including:
- In the Azure portal:
- Microsoft Defender for Cloud's security alerts page - Shows alerts for all resources protected by Defender for Cloud in the subscriptions you've got permissions to view.
- The resource's Microsoft Defender for Cloud page - Shows alerts and recommendations for one specific resource, as shown above in Enable enhanced security.
- In the inbox of whoever in your organization has been designated to receive email alerts.
Tip
A live tile on Microsoft Defender for Cloud's overview dashboard tracks the status of active threats to all your resources including databases. Select the security alerts tile to go to the Defender for Cloud security alerts page and get an overview of active threats detected on your databases.
For detailed steps and the recommended method to respond to security alerts, see Respond to a security alert.
Respond to email notifications of security alerts
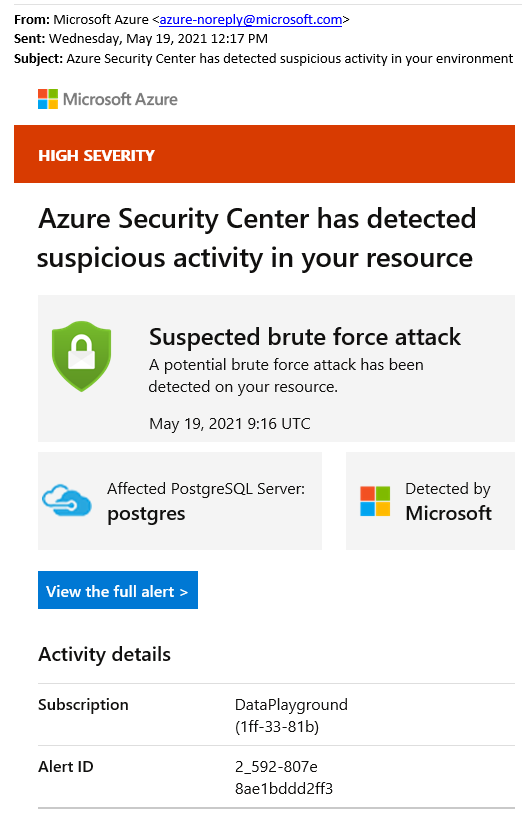
Defender for Cloud sends email notifications when it detects anomalous database activities. The email includes details of the suspicious security event such as the nature of the anomalous activities, database name, server name, application name, and event time. The email also provides information on possible causes and recommended actions to investigate and mitigate any potential threats to the database.
From the email, select the View the full alert link to launch the Azure portal and show the security alerts page, which provides an overview of active threats detected on the database.
View active threats at the subscription level from within the Defender for Cloud portal pages:
For additional details and recommended actions for investigating the current threat and remediating future threats, select a specific alert.
Tip
For a detailed tutorial on how to handle your alerts, see Manage and respond to alerts.
Next step
Feedback
Coming soon: Throughout 2024 we will be phasing out GitHub Issues as the feedback mechanism for content and replacing it with a new feedback system. For more information see: https://aka.ms/ContentUserFeedback.
Submit and view feedback for


